 Microsoft’s lawyers this week engineered a pair of important takedowns, one laudable and the other highly-charged. The software giant orchestrated a legal sneak attack against the Web servers controlling the Waledac botnet, a major distributor of junk e-mail. In an unrelated and more controversial move, Redmond convinced an ISP to shutter a popular whistleblower Web site for hosting a Microsoft surveillance compliance document.
Microsoft’s lawyers this week engineered a pair of important takedowns, one laudable and the other highly-charged. The software giant orchestrated a legal sneak attack against the Web servers controlling the Waledac botnet, a major distributor of junk e-mail. In an unrelated and more controversial move, Redmond convinced an ISP to shutter a popular whistleblower Web site for hosting a Microsoft surveillance compliance document.
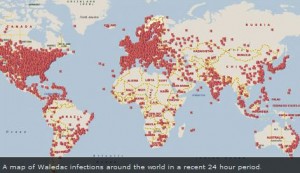
On Feb. 22, a federal judge in Virginia granted a request quietly filed by Microsoft to disconnect 277 Internet domains believed to be responsible for directing the daily activities of the Waledac botnet, estimated to be one of the ten-largest spam botnets in existence today and responsible for sending 1.5 billion junk e-mails per day. Microsoft said it found that between December 3-21, 2009, approximately 651 million spam emails attributable to Waledac were directed to Hotmail accounts alone, including offers and scams related to online pharmacies, imitation goods, jobs, penny stocks and more.
The takedown, which Microsoft dubbed “Operation b49,” has “quickly and effectively cut off traffic to Waledac at the ‘.com’ or domain registry level, severing the connection between the command and control centers of the botnet and most of its thousands of zombie computers around the world,” the company said. From the official Microsoft blog:
“Three days into the effort, Operation b49 has effectively shut down connections to the vast majority of Waledac-infected computers, and our goal is to make that disruption permanent. But the operation hasn’t cleaned the infected computers and is not a silver bullet for undoing all the damage we believe Waledac has caused. Although the zombies are now largely out of the bot-herders’ control, they are still infected with the original malware.”
What praise and adulation the IT industry might heap on Microsoft for this effort, however, may be drowned out by the growing chorus of criticism over Microsoft’s legal victory against a popular whistleblower Web site. Alleging copyright infringement, Microsoft went after Cryptome.org curator John Young on Tuesday after he posted a Microsoft compliance document that the company gives to law enforcement agents seeking information on Microsoft users.
On Wednesday, Cryptome was shut down by its hosting provider, Network Solutions. As wired.com’s Ryan Singel writes, the takedown shuttered “a site that thumbed its nose at the government since 1996 — posting thousands of documents that the feds would prefer never saw the light of day.”
Predictably, the document has since shown up on numerous other Web sites, including Wikileaks.org, and Wired.com. It includes information about the various types of customer information available to law enforcement across Microsoft’s properties, such as Xbox Live. The document, titled “Global Criminal Compliance Handbook,” is worth a read for anyone curious about the types of identifying user information that Microsoft may make available to law enforcement upon request
“On the botnet stuff, Microsoft deserves credit for its strategy and the court deserves kudos for understanding the importance of the case,” former Justice Department prosecutor Mark Rasch said. “The other takedown, though, is unwinable for Microsoft, because it’s a little like wrestling with a pig: You’re just going to make the pig mad.”
Update, 1:19 p.m. ET: ReadWriteWeb is reporting that Microsoft has decided to withdraw the copyright complaint against Cryptome, and that the site is expected to be back online today.




How many times are corporations going to have to relearn the Streisand Effect?
What was the name of that site again? 🙂
Kudos to Microsoft for its actions on the Botnet.
Shame on Microsoft for its actions on the GCCH document.
Like wiredog said, if they would have said nothing, it would have faded away. The document is 2 years old (march 2008), and I don’t fault Microsoft storing the data. If you aren’t doing anything wrong what do you have to worry about.
Just my 2 cents worth
I would like to point out, I’m not a Microsoft basher, I use (and pay for) their products. I also use Linux. Both have their pluses and minuses.
I wonder just how much IPv4 and in the future v6 will be able to withstand the “flotsamand jetsam” of the internets which take years to accumulate. How many of the IP blocks are tainted or tagged as spammers, zombies / bots, hosting porn, etc in various blacklists and are not ever expunged.
Why a court order? This is a huge waste of legal resources for a problem which ought not to need a legal CYA. Contacting the registrars and ISPs and enforcing the existing business contracts which should supposedly be in place ought to have been enough to disconnect the botnet.
Yet no one is yet asking for class action suits to Microsoft or other software vendors for the massive outbreaks of bots which is enabled by the lax security models of certain vendors who only respond with reactive not pro-active measures. That fact MS still hasn’t rolled out Kernel patch protection for 32bit is like Toyota saying fixing the brakes isn’t something to be done till the next vehicle is sold to them (post crash). DEP has been a bit forgotten as well
Luckily Waledac (as reported so far) didn’t have built in poison unlike ZeuS. Bot writers will now just nuke the victim’s server/pc if the deadman switch is not “held” for say 3 weeks or some other time period. This would cause a “fresh” environment that would be ripe for re-infection with a new bot net strain. Statistically the way the software model is configured in a SOHO; a high percentage of devices would be reloaded machines ie from old images that are vulnerable having already proven to be missing patches or be misconfigured. If bare metal reload these are always vulnerable as the Service Packs & patches are DL’d from MS and vendors with a live internet connection (not a WSUS or other homebrew off the internet till secured best practice )
Really throwing on secunia OSI as the 2nd thing after the antivirus and running it as the system is reloaded till acceptably clean is a huge pain in the ass. How many apps, plugins etc are security stale out of the archive!
I congratulate Microsoft for helping clean up the world. Now, how about cleaning up their own backyard?
http://rss.uribl.com/hosters/spaces_live_com.html
…over 900 new spammed sites were registered since this morning. Compared to Waledec, this should be a piece of cake.
I am not a MSFT-basher; I help support them by using their software, and, for the most part, liking it. Why they can’t deal with this? Please?
On the cited blog, MSFT says, “Microsoft has since been taking additional technical countermeasures to downgrade much of the remaining peer-to-peer command and control communication within the botnet,”
Sounds like a legally-authorized hack. This is a pioneering step in civil law enforcement (as distinguished from criminal law enforcement) on the Internet. –Ben
What caused Microsoft to change course and withdraw the copyright complaint against Cryptome? Just curious.
I had difficulty posting this article on my FaceBook account. I wonder if Brain knows they are trying to say
FaceBook members are supposedly reporting his link as too controversial!! Can you believe that BS!!
I smell a rat! Of course FB is probably infested with rats; but I have to use it for my work!
Re: Microsoft’s withdrawal of suit: The prosecutor’s words ring true. When the document started to show up @ multiple sites, Redmond realized the battle was over and ran up the white flag. Their learning curve improves.
Re Network Solutions: Can medical science advance far enough to graft a spine on to NS? Time will tell. (-;
>Can medical science advance far enough to graft a >spine on to NS?
No.
If the Devil himself and a Verisign salesman both showed up holding contracts and I had to sign one of them, I’d tell the Verisign salesman to go pound sand.
The aim of cloud computing is to revoke our freedom. Once the content of everything is in the cloud, what personal content is ours?
#dark cloud computing
As much as I agree with you, your comment has absolutely nothing to do with the subject of this article.
“It includes information about the various types of customer information available to law enforcement across Microsoft’s properties, such as Xbox Live. The document, titled “Global Criminal Compliance Handbook,” is worth a read for anyone curious about the types of identifying user information that Microsoft may make available to law enforcement upon request.”
Yet, all I ever read about is how “EVIL” Google is for hording all of my search data (for God knows how long). Given the fact that I’ve used Microsoft properties for over 20 years, I’m sure Microsoft is a far bigger threat to my privacy than Google.
Well … Microsoft sure knows how to get favourable publicity. I’ll give them that, but Microsoft’s attempt to position themselves as botnet busters goes too far. Way too far.
Why? Simply because about 100% of all botnet machines are running Microsoft Windows.
Now why is that? Because MS Windows is so widespread? Or because MS Windows is deployed so much by people who haven’t the foggiest notion of how to secure their machine (or simply don’t care)? Or because MS Windows’ architecture and default setting guarantee that it’s is so insecure?
Just consider this: about 60% of all web servers aren’t running MS Windows. They’re running Linux. And those machines certainly aren’t compromised more often than MS Windows machines. Quite the contrary in fact. So it’s unlikely that Microsoft’s near 100% market share in compromised machines is due to its market share.
There is a very legitimate point of view that says that Microsoft are solely responsible for the rise of botnets because they purvey operating systems that are so easy to compromise. One may or may not agree with this viewpoint, but to portray Microsoft as anti-botnet champion smacks too much of chutzpa to my taste.
And then the way in which Microsoft achieved this. If there ever was a case of legal sandbagging, this is it. Microsoft sneakily ensured that it appeared alone in front of the court to argue its case and to move for the suspension of a number of domains. Is that a precedent we would wish to see followed? That a big corporation can institute a secret trial against anonymous internet participants and get an injunction kicking them off the net?
Now I’m as happy as the next computer user to see a botnet being taken down, but this price is too steep for me. Far too steep.
And last but not least, according to Spamhaus this was a fairly small fish, accounting for about 1% of all spam. So could we save the self-congratulary press releases for when there is something substantial to report?
Comparing Linux web servers, with presumably professional sysadmins configuring most of them, with the home machines that form the bulk of bot-nets is an apple and oranges comparison.
Most sysadmins at least are cognizant about security even if they forget something, get lazy, or get too busy to get to it. When they do, Linux boxes get rooted.
Most homeowners know and want to know as much about computers as their car. They just want it to run, and most drivers would be hard pressed to find a dipstick never mind such trivially easy tasks as changing oil, rotating tires, and replacing brake pads they’ll usually either pay a mechanic to do it, or won’t pay and don’t care to learn how so the car just rots for lack of care.
The legal power the judge assumed here borders on a separation of powers Constitutional violation. The judge essentially gave Microsoft the authority to declare war on these computers. There are also some striking similarities to the law enforcement process of obtaining a search warrant, except Microsoft isn’t a police force! I won’t go into detail, but if you are interested in a more detailed legal analysis, check out the link below:
http://www.modernbandit.com/2010/02/microsoft-cyber-army-judicial-power-to.html
all the patch in the world can never completely eradicate this problem as long there are an abundant supply of bad codes from hastily-made products. take for instance the bunch of live NASA server exploits listed at pinoysecurity. the list just goes on…
One of the main problems is the disinformation, hype and downright dangerous propaganda campaign going on over the word “privacy”.
I hope Microsoft will keep records on every single word I ever write so I can and other people can search for and find it. If laws are passed by Congress, Microsoft or anyone else has to follow them. The truth of the matter is there is a dangerous, life threatening, organized criminal element, which can find out anything they want to about anyone else. It’s called the Advertising Agencies.
Did you know that Advertising Agencies can, entirely without regulation, access your medical devices over the networks? Did you know that nearly all programming in any medium is paid for by Advertisers? Did you know that Advertising Agencies are the largest lobby of Congress? Did you know that Advertising Agencies are the arm of big business and also Mossad, the Israeli Spy Agency? Did you know they can stop your pacemaker?
I support Microsoft’s efforts, especially their campaign with Microsoft.dna, which has done more for the FBI to catch and imprison child molesters, child pornography rings, and rapists/kidnappers/murderers/torturers of children than any other software in history. They are taking down the criminal gangs, not trying to read your emails.
The whole debate about “privacy” is a misnomer. What is needed desperately is a way to definitively establish and maintain your identity in all communications media and have a way to measure re-routing, filtering and the deadly, search and replace functions. These put people onto terrorism watch lists and create files of disinformation on people. They have no recourse to defend themselves against any accusation, because they are anonymous victims with no way to obtain records and redress grievances. “In the future, we will all die from hearsay”.
For a great article on the need for establishing identity, see: Privacy Issues: Avoiding Becoming A Victim Of Online Crime
ScienceDaily (Dec. 8, 2008) by the International Journal of Property Management on ScienceDaily.com (sorry, link broken!)
All of your phone calls are being re-routed through Israel and over 10% of the world was attacked by the Chinese military and is now behind their firewall. Sony infected almost every computer there is with spyware, for which they were convicted in a Texas Court, before Cheney decided they would make a good business partner and classified it. Wiley Rein, the attorneys for Trust e sold proprietary information and “one on one access” to advertising agencies and the pedophile, Howard Stern as part of their so-called work for the “Government Spy Program”, obtained immunity, then refused to turn over records for their client AT&T, while lobbying congress with billions to oppose Net Neutrality.
It is not Microsoft or Google, both of which had to ask for help from the NSA, but the ISP’s who are, with the telcos, re-routing, stealing and selling your information to Advertising Agencies and others, without your permission. They claim they are protecting your privacy, however this is blatantly false.
For a real wake up call into the tidal wave of neuromarketing coming soon to your brain with no “off switch” by Advertising Agencies, see this:
http://www.sciencedaily.com/releases/2010/06/100609102028.htm
Excellent post. Thanks for the links!