The very first entry I posted at Krebs on Security, Virus Scanners for Virus Authors, introduced readers to two services that let virus writers upload their creations to see how well they are detected by numerous commercial anti-virus scanners. In this follow-up post, I take you inside of a pair of similar services that allow customers to periodically scan a malware sample and receive alerts via instant message or e-mail when a new anti-virus product begins to detect the submission as malicious.
 While there are free services like VirusTotal and Jotti that will let visitors upload a suspicious file and scan it against dozens of commercial anti-virus tools, the reports produced by the scans are shared with all of the participating anti-virus makers so that those vendors can incorporate detection for newly discovered malware into their products. While virus writers probably would love to use such services to fine-tune the stealth of their malware, they may not want their unique malware samples broadly shared among the anti-virus community before the malware has even had a chance to infect PCs.
While there are free services like VirusTotal and Jotti that will let visitors upload a suspicious file and scan it against dozens of commercial anti-virus tools, the reports produced by the scans are shared with all of the participating anti-virus makers so that those vendors can incorporate detection for newly discovered malware into their products. While virus writers probably would love to use such services to fine-tune the stealth of their malware, they may not want their unique malware samples broadly shared among the anti-virus community before the malware has even had a chance to infect PCs.
So it’s not hard to see why some malware authors and purveyors choose to avoid these free services in favor of subscription products that scan submitted files with multiple anti-virus engines, yet prevent those results from being shared with the anti-virus vendors. Such is the business model behind scan4you.net, a service that charges 15 cents for each file checked. Scan4you will scan your malware against 30 anti-virus products, but promises it will bar those products from snarfing up a copy of the malware:
“This service is about to help you in anonymous check of different anti-virus system. This check will be made by numbers of anti-virus system and no reports will be send to developers of this anti-virus system. You can be fully sure that your files will not be send to anti-virus databases. All reporting system in our version of anti-virus engines was disabled MicrosoftSpyNet, ESET ThreatSense.Net Early Warning System etc.”
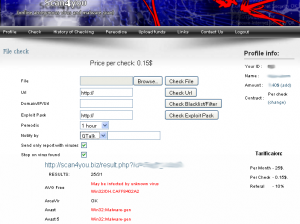
For 15 cents, you can scan your file to see if any potential victim’s anti-virus program will detect it. Or maybe you’re more interested in seeing how well your drive-by download site is flagged by anti-virus products as malicious? Perhaps you want to see whether your site is listed on any of the major spam and anti-malware blacklists? All these checks can be had for $0.15 each.
 So your malware is invisible by to all anti-virus products? Yay for you, but it won’t stay that way: Sooner or later, the malware author is going to need to tweak his creation or replace it with a newer version, or risk having the invader detected and killed by anti-virus software on the victim’s PC. Probably the most innovative feature of scan4you.net is a service that lets you choose the interval time to have your file re-scanned, and then receive alerts whenever an anti-virus product starts shipping detection for your malware. Customers can select anywhere from a 1-24 hour rescan interval, and receive update alerts via e-mail, ICQ, Gmail chat, or Jabber (see screen shot above).
So your malware is invisible by to all anti-virus products? Yay for you, but it won’t stay that way: Sooner or later, the malware author is going to need to tweak his creation or replace it with a newer version, or risk having the invader detected and killed by anti-virus software on the victim’s PC. Probably the most innovative feature of scan4you.net is a service that lets you choose the interval time to have your file re-scanned, and then receive alerts whenever an anti-virus product starts shipping detection for your malware. Customers can select anywhere from a 1-24 hour rescan interval, and receive update alerts via e-mail, ICQ, Gmail chat, or Jabber (see screen shot above).
Another service, avcheck.ru, does essentially the same thing — allowing users to scan their creations and receive periodic updates about future detection — but with fewer anti-virus products and fewer instant alert options.




AV….blacklisting is worthless. Why do we put so much money in this crap. There needs to be more broad development for users to use “simplified” versions of application whitelisting and sandboxed browsers (hi chrome) from IE/FF.
05
Apr 10
Virus Scanners for Virus Authors, Part II
April 10?
The bigger (font size) numbers are the day. That 10 is the year (2010).
DD
MMM YY
Right. Well. I’ll just go hang my head in shame for missing the obvious here.
I blame the coffee. Not enough caffeine in it. Yeah. That’s what it is.
When you think you see a typo in a blog, it is more polite to send the writer an email than to post a snarky (and in this case off-base) comment.
One of the scary thoughts from this article is the fact that the scans are $0.15 per file. Well, maybe not the cost exactly, but the idea that the low cost per scan is made up in volume of scans from malware writers. That concept is scary.
I don’t think malware coders are paying with their personal credit cards.
This is likely just another form of micro-money laundering of ill gotten gains from credit card skimming or wire fraud $00.15 at a time.
Dump a whole hdd of files (also probably stolen) that adds up to a chunk of change which flys under any scrutiny of regulators.
Really to stop virus development and malware is a dual prong attack. The right prong is moral and the left is economic. I intend means other than jail and fines. For starters stripping convicted malware writers of all their academic credentials and tainting/embargoing institutions/states that trained them would be a start.
I really don’t think the organized malware virus/writers are completely self taught by a “learn to program book” as they sat in a shack in the woods. They have support somehow. Friends/family/peers that don’t get the same shame/embarassment as if their friend was making CNB weapons with their chem set at their apartment.
While a man could reform, I really have doubts that they can re-enter the industry “clean” after conviction. Doctors ban “bad” doctors from practicing and transmit that info to the next state or contry or put them on long probation. Virus / Hackers/ Malware authors setup their own company or get hired as a grey-hat and make seriously good money.
As Jesse Ventura reminds us – “follow the money.” This is the only way to clean up the real miscreants and dangerously organized types who fund the malware IT pipeline.
Are these sites actually breaking any laws by offering what they do?
I think they probably violated some related agreements with AV software they are using to “test” the malcode. But it seems like these services are basically operating 100% lawfully. Certainly makes putting a stop to malicious software much more difficult when you can’t really pursue these type of support services that are springing up to help the bad guys. It would be sadly interesting to see how the 24X7 support for some of these trojan kits, compares to the support for a valid security tool…
Its actually quite easy, and I would suspect someone with the ability to write their own malware can do it, to script this yourself using multiple VMwares.
If I was a malware author I would rather use my own homegrown solution than risk using a third party.
Could any of these sites actually be sting operations run by law enforcement? Could LE take over a site like this as an aid to track down the source of malware? It is an idea worth considering.
Also, a good reason for the bad guys to use a homegrown solution. That may well be where this originally came from. A virus writer that realized that his homegrown service could actually make some money.