I am often asked to recommend security software, but it’s important to remember that staying secure is just as much about removing little-used software that increases your exposure to online threats. At the very top of my nix-it-now list is Java, a powerful application that most users have on their systems but that probably few actually need.
 Not only do most users have some version of Java on their systems, most Windows users likely have multiple copies of this program on their PCs, because older installers failed to remove previous, insecure versions of the software.
Not only do most users have some version of Java on their systems, most Windows users likely have multiple copies of this program on their PCs, because older installers failed to remove previous, insecure versions of the software.
Worse still, Java is now among the most frequently-attacked programs, and appears to be fast replacing Adobe as the target of choice for automated exploit tools used by criminals.
Readers of the blog are no doubt familiar with my previous stories on the Eleonore Exploit Pack, a commercial software package sold by and to criminals that is used to booby trap Web sites with exploits for the most common Web browser vulnerabilities. Check out past posts on Eleonore, and it’s clear Java flaws are a key target of this increasingly common exploit pack.
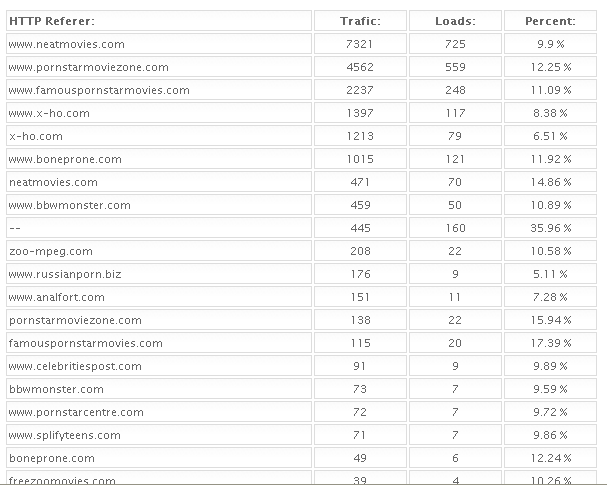
Below are a few screen shots taken from the administration page of yet another working Eleonore Exploit Pack: The first image shows the exploits used by this pack, along with the number of times each exploit (“sploit”) was successful in delivering malicious software payloads (or “loads”) to the visitor. As we can see, the “java2e” and “javae0” are by far the most successful of the exploits.
The exploits from this pack were stitched into a number of hacked or maliciously crafted porn sites, shown below. But just because you don’t surf porn doesn’t mean these exploit packs can’t touch you: Many are stitched into more mainstream sites, such as those belonging to online stores and blogs. I hope it goes without saying that readers should assume all of these sites below are still hostile and that you should *not* visit them unless you *really* know what you are doing:
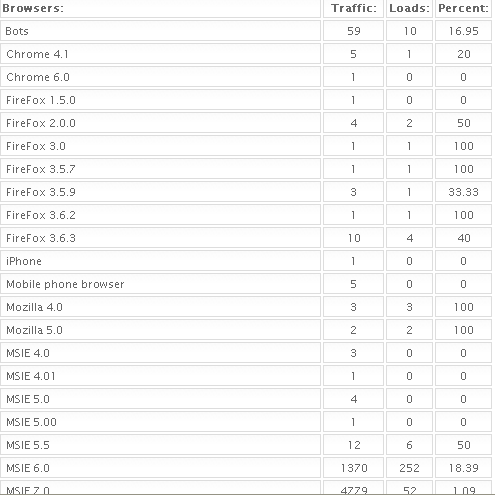
It’s probably worth noting the overall browser stats for this particular exploit panel: A little more than 11 percent of those who visited these…err…booby trapped Web sites were successfully hit with an exploit. At least with this group of exploit sites, nearly all of the visitors and victims appear to have visited with some version of Internet Explorer. I should note these stats should be taken with a grain of salt, because it seems Eleonore’s visitor numbers always contain statistical oddities that make them suspect at best. For example, according to these numbers, only 30 out more than 20,000 visitors (slightly more than one out of every thousand) visited the sites with some version of Chrome, Firefox or Opera.






Have to say, I’m rather disturbed by the way that people ‘red thumb’ anything they disagree with. Given the way the blog handles such matters, it means that unpopular views get hidden. Even when I click to see them (and I think unpopular vs. lacking content tend to be the most vital things to read), they are still somewhat censored by being grayed out to almost unreadable.
Calandale, that’s because the thumbs down is free. You can just clicky click it all day long. People are opinionated, but they are also lazy.
Clicking the thumbs down is both effortless and opinionated, the ideal combination for lazy egos.
It might take someone five or ten minutes to put together a cogent post, but it only takes a split second to click thumbs down.
This is why more serious sites place restrictions on how often you can vote down items, as it prevents spurious negative voting by the lazy.
And even if you need Java (some business applications and also a few freeware tools need it) you can still decide to not install (or disable) the browser plugin for Java applets, as applets are mostly dead anyway (except for exploitation).
Sure, if you don’t need it, uninstall it, but if you need it check if you really need it in your browser and if not, disable it there.