A group tasked with devising strategies to deter cyber attacks is calling for mandatory public disclosure of fraud and hacking incidents by governments and organizations of all sizes, including banks.
 The recommendations were a major thrust of a report issued earlier this month by the National Research Council, which was asked to examine the issue by the Office of the Director of National Intelligence. The 400-page document is actually well worth the time to read, or at least skim. The bulk of the paper addresses how solving the problems associated with cyber crime requires aligning incentives and liabilities so that those in the best position to fix the problems have an incentive to do so.
The recommendations were a major thrust of a report issued earlier this month by the National Research Council, which was asked to examine the issue by the Office of the Director of National Intelligence. The 400-page document is actually well worth the time to read, or at least skim. The bulk of the paper addresses how solving the problems associated with cyber crime requires aligning incentives and liabilities so that those in the best position to fix the problems have an incentive to do so.
But to me, the most interesting and useful components of the report come at the end, where the group makes several broad policy recommendations, including:
- Mitigating malware infections via ISPs by subsidized cleanup
- Mandatory disclosure of fraud losses and security incidents
- Mandatory disclosure of industrial control system incidents and intrusions
- Aggregating reports of cyber espionage and reporting to the World Trade Organization
I don’t know how effective or realistic the last two recommendations would be, but as a reporter I’m naturally inclined toward disclosing data whenever possible. Loyal readers no doubt know where I stand on the first two points. I have long called for some kind of system in which ISPs are encouraged or given incentives to regularly scrub their networks for bot-infested customers and compromised Web sites.
And hardly a month goes by when I don’t hear from someone asking me where to find aggregated statistics on the costs of cybercrime and Internet banking fraud in the United States. The banks don’t have to publish reports of their losses, and although they are supposed to publish indicators of fraud (through suspicious activity reports) financial institutions seem to be spotty and begrudging about this level of reporting as well. Writing for SC Magazine earlier this summer, Charles Jeter of security software maker ESET penned a useful three part series on the lack of reporting by banks about the costs of online banking Trojans.
The free report is available at this link.
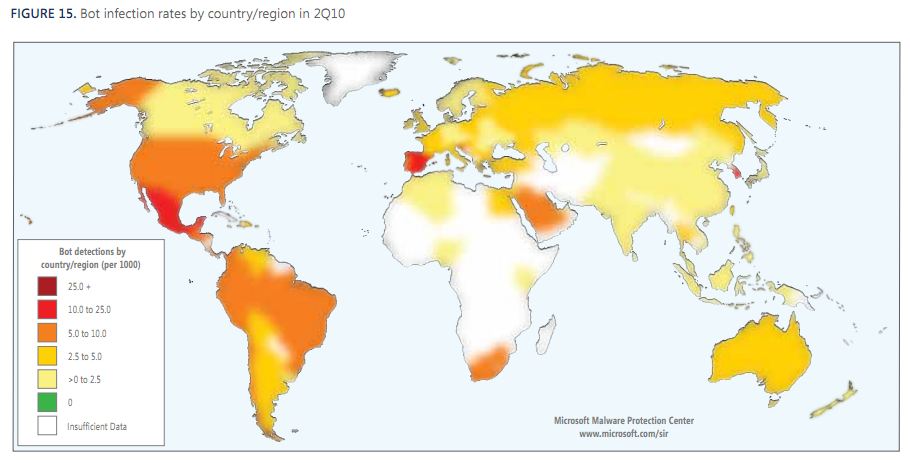
Speaking of global trends in cybercrime, Microsoft published its biannual Security Intelligence Report covering cybercrime activity it has observed in the first half of 2010. Anyone looking for granular data on which threats are most prevalent (at least from Microsoft’s perspective in scrubbing millions of PCs) should have a look at this informative report. Unsurprisingly, the United States (or more accurately — US-based ISPs) continues to lead the world in botnet infections.
 While we’re on the subject of data breach and attack disclosure, now seems like a perfect time to mention that Arbor Networks is seeking additional perspective for its annual Worldwide Infrastructure Security Threat Report. Arbor is looking for a few clueful network administrators to anonymously share experiences and perspectives about operational risks and challenges involved in building, operating and defending large networks. If this describes you, check out their survey.
While we’re on the subject of data breach and attack disclosure, now seems like a perfect time to mention that Arbor Networks is seeking additional perspective for its annual Worldwide Infrastructure Security Threat Report. Arbor is looking for a few clueful network administrators to anonymously share experiences and perspectives about operational risks and challenges involved in building, operating and defending large networks. If this describes you, check out their survey.




The US certainly is in the dark orange category, but I find the bright red in Mexico and Spain very interesting. Any thoughts/conjecture on why that is? More lax attitude by consumers? Better targeting by botnet operators? Something else?
The governor of CA should talk to the authors of that report, since he claimed in his veto of SB 1166 that there is no evidence that central reporting of such incidents helps consumers.
“incentives and liabilities ” / carrot and stick
The best way to advance change in a free society under the Constitution.
I don’t want my ISP attempting to inspect my traffic enough to flag me for a bot infection, nor make any attempt to do anything about it…
I won’t even to get into privacy/trust or net neutrality, but rather I don’t believe ISPs will be accurate or useful in that manner. I don’t know about others, but my enterprise detection mechanisms throw false positives on a constant basis except for the most obvious of attacks. And the only mitigation an ISP can do is disconnect the endpoint.
….the only mitigation an ISP can do is disconnect the endpoint.”
Not true at all. You can throttle their connection — if they’re suspected of being a spam bot for instance — and make it annoying for infected machine owners to have to put up with.
Nobody is talking about looking inside your traffic. The current systems look at which systems are connecting to bot command centers on a regular basis.
Most bots behave quite differently than normal systems, generating many times more connections to other systems than non-infected systems do. When you observe this activity over time, it’s not rocket surgery to be able to tell there’s a problem.
“… the [GOV’T] group makes several broad policy recommendations…”
Am I the only one? Doesn’t this bother anybody?
.
Oh, it bothers me a great deal. I strongly believe government involvement tends to make things worse, not better. More often than not, it ties the hands of the good guys while the bad guys continue to do their thing regardless. Sometimes, you gotta fight fire with fire! Let the good guys do their thing too! 🙂
@EY: That is a great question to which I would only add that Microsoft’s results do not stand alone concerning Mexico although I can’t speak towards Spain.
The regional impact of malware is also very interesting.
@Andre: I haven’t reviewed the bill you mentioned but I can say that California dotgov types and Federal dotgov types in San Diego are very interested in better central reporting. In my research for the FinCEN data there are many obstacles in getting actionable information of any crime Suspicious Activity Report, and the first layer is accountability of the reporting party – banks are mandated to report but gain Safe Harbor (legal term) once the report is filed within 60 days.
The interpretation of the report is then up to the regional law enforcement agency which accesses it. As expressed by FinCEN staffers in multiple quarterly releases to their audience of banks and other financial institutions, the call to action about accuracy in the narrative of the SAR has been mostly unfulfilled.
As the report Brian speaks of becomes more mainstream, the regional impact of malware should become more measurable. The call to action of elected officials should become louder as they know how many of their constituents are affected – and how much taxable revenue is lost through cybercrime.
The axis of time / geographic location should be ascertainable along with the axis of lost dollars / victim category (business, consumer) in order to effectively calculate the impact.
Its quite interesting that the US is willing to give up hard sovereignty by reporting hard facts & cases about cyber espionage and good old fashioned RICO to the WTO.
It sounds so much like hunt for red october — Andrei, you’ve lost another submarine?
It would also be interesting to see just how much all the $’s on product testing and human training/certifications projects spent up against the fact they are _just not working_.
The fact is the invention of the spreadsheet is redounding on our heads. I’ve once many years ago heard rumors of baking in margins for losses due to crime into the consumer’s cost for financial products.
It went something like this: somewhere one group is compensated for fraud losses by the global company because worldwide, somewhere someone else has offset that cost. Spreadsheets make this faster than ever before.
The company didn’t have to do anything meaningful and the problem certainly didn’t get fixed and it all went under the radar in the calls with Wall Street or .gov regulators.
If ever a fine is levied the same spreadsheet analysis is rigorously done by smart people. A branch site is closed early or for a short lengths of time and the salary and other expenses saved are then diverted to “recover” the fine.
It’s a mess. In another time the situation would have many calling for congressional hearings. But the US public is too tired and doesn’t believe in them anymore after the S&L and Irancontra and ….
As for Microsoft supporting .gov coming to my “house” looking for bot infested machines and misconfigured servers, its sounds like dangerously poor products were released and I ought to be getting the better end of the deal — not punishment upon my .org and being throttled and ultimately disconnected.
Ralph Nader once said the way US car manufactures made cars made them unsafe at any speed — Today can we now admit OSes & Apps (as they are produced now) are unsafe on any .net and get on with the real work to get them to where they ought to have been by now.
>> Aggregating reports of cyber espionage and reporting to
>> the World Trade Organization
Yeh, I don’t think China cares. But it might help everyone else care.
I just read an article on Yahoo which said the US Government was studying an Australian (Government) system set to go into effect in December whereby ISP could take action. Reading the article, which stated as fact what the “public” would, and would not agree to I could not help but think of that declassified NSA report BK published a while back …
Public Sector networks are not secure because there was a lot of money to be made by cutting corners for speed. Maybe so, but you don’t fight script kiddies with script kiddies either. The Mortgage Foreclosure nightmare is a good example; a classic pay-for-forgery scandal.
I completely agree that greater disclosure (even to the WTO) and transparency is necessary for the simple truth that the problem will not be solved by the “early adopters” it will be solved by embarrassing the cr@p out of the non and late adopters.
(sorry BK my mouse is wandering, please delete duplicate)