Criminals increasingly are cannibalizing parts from handheld audio players and cheap spy cams to make extremely stealthy and effective ATM skimmers, devices designed to be attached to cash machines and siphon card + PIN data, a new report warns.
The European ATM Security Team (EAST) found that 11 of the 16 European nations covered in the report experienced increases in skimming attacks last year. EAST noted that in at least one country, anti-skimming devices have been stolen and converted into skimmers, complete with micro cameras used to steal PINs.
EAST said it also discovered that a new type of analog skimming device — using audio technology — has been reported by five countries, two of them “major ATM deployers” (defined as having more than 40,000 ATMs).
In the somewhat low-res pictures supplied by EAST here, the audio skimming device is mounted on a piece of plastic that fits over the ATM’s card reader throat. A separate micro camera embedded in the plastic steals the victim’s PIN.
The use of audio technology to record data stored on the magnetic stripe on the backs of all credit and debit cards has been well understood for many years. The basic method for conducting these attacks was mentioned in a 1992 edition of the hacker e-zine Phrack (the edition that explains audio-based skimmers is Phrack 37). Since then, other electronics enthusiasts have blogged about their experiments with sound skimmers; for example, this guy discusses how he made a card reader device out of an old cassette recorder.
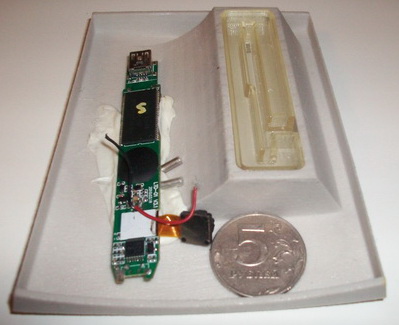
Recently, I had a chance to chat via instant message with a hacker in Eastern Europe who sells both audio-based ATM skimmers and the technology needed to decode audio skims or “dumps.” Below are some of the pictures of his wares that he sent me:
[EPSB]
Have you seen:
ATM Skimmer Powered by MP3 Player…I’ve noticed quite a few more ads for these MP3-powered skimmers in the criminal underground, perhaps because audio skimmers allow fraudsters to sell lucrative service contracts along with their theft devices. The vendor of this skimmer kit advertises “full support after purchase,” and “easy installation (10-15 seconds).” But the catch with this skimmer is that the price tag is misleading. That’s because the audio files recorded by the device are encrypted. The Mp3 files are useless unless you also purchase the skimmer maker’s decryption service, which decodes the audio files into a digital format that can be encoded onto counterfeit ATM cards.
[/EPSB]







“a 1992 edition of the hacker e-zine Phrack”
Wargames was released in 1983…
I’m lost for understanding the whys security law enforcement do not track and detain criminals that volunteer proudly display and brag about their illegal devices. If I were to blog or otherwise brag that I had robbed two banks and my intentions to continue my robbing spree, my front yard would be trespassed right away with assorted law enforcement demanding my immediate surrender.
hello
I invented a antiskimmimg device. I sent you an e-mail about it.
I know very well this criminal world because I made various models of skimmers before passing on the other side of the barricade.
If you’re interested in details please contact me.
Perhaps you could suggest how you would skim this ATM card reader which sticks out of the ATM?
http://webwereld.nl/nieuws/63504/ns-treft-opnieuw-maatregelen-tegen-skimmers.html
I cannot imagine how it could be done due to the simplicity but then im not in the skimming business.
Of course we are interested in details, although I’m afraid your claim might be just vapourware. Please enlighten us !
What would be good to know is how to DETECT ATMS that have skimmers on them?
Also, is there any knowledge of where skimmers are used in the US of A…that is what banks/branches/locations of ATMs?
“Also, is there any knowledge of where skimmers are used in the US of A…that is what banks/branches/locations of ATMs?”
Wouldn’t it be great if the criminal published where they were operating!
These look much “better” from the theives’ POV. No visible alteration to tip off the user.
Hi Brian,
Good post, as usual. Is the report of European ATM Security Team available anywhere for the large public ? I’m based in Europe and quite interested to “skim” (sic :)) through it or even read it entirely.
Thanks, George. The EAST folks asked me not to post the report in its entirety on my blog. You may be able to obtain it from them by emailing the contact info on their site.
Brian,
Thanks again for your never ending effort to make the general public more attuned to the pitfalls facing all of us.
Although this might look small and scary, the reality is that it’s pretty sloppy and most anyone that has read one of your articles would notice this in the wild fairly easily. The second set of pictures looks like a basic “spy pen” that has been gutted with no magnetic head attached. If you look at the first set of picture there is basically the same setup with a mag head attached. You can plainly see the magnetic head in the first set of photos, this is a huge warning flag and should alert anyone that is somewhat diligent in checking out ATMs before use. The exterior fascia shot looks as if there is no hole drilled for the camera, which would throw up additional red flags.
The fascia looks to be pretty good quality, but thankfully the overall execution is pretty poor. Hopefully this guy’s less refined “product” will give most citizens more of a fighting chance against it.
Let’s not forget that if the information is that public, it is probably not the “top of the market” in equipment. The best illegal equipment is not so readily available and may be of much higher quality. Some of the iequipment that illegal hackers use cost thousands and works very well. Alas why so much of it goes on everyday, they have to pay for new equipment often as the security increases. Thanks Appriver for costing Spammers untold amounts of money in new software by staying on top of their game!
Clay, I’d agree with your statement, generally. And I’ve noted this fact in previous stories on ATM skimmers: Most are people trying to scam the scammers.
However, the second set of pics above are not easily found. You need to have access to a vetted forum and chat some of these guys up on ICQ and/or Jabber; it helps if you can get by in Russian, as well.
That is more along the lines of what I was referring to. My objective with that statement is the more we protect ourselves by hiring security professionals, the harder (and more expensive) it is for criminals. The general public is most likely not going to notice someone walking around in an airport with a high resolution camera taking pictures of your computer screens or realize that the person sitting the in the mall with his laptop and black box is grabbing control of their phone with the bluetooth they left on and downloading your account information you saved in your browser. Awareness is the best answer, but not always a plausible one.
There is good reason why many countries in Europe have moved from stripe to Chip.
American banks are still reluctant to move to the better technology.
All security takes investment and using 30+ year old technology is not taking security seriously.
Are you referring to RFID-type chips? Depending on their design, these can be less secure than mag-stripes, since anyone with an RFID scanning device within range of you can read whatever card you’re carrying.
no this type of chip:
http://www.signhelp.de/shop/images/product_images/original_images/46_0.jpg
The magstripe is on the back of the card.
The chip contains information about the card holder and has to match the card and pin given and what not.
I would have some reservations about advocating chip card security especially when Cambridge security researchers recently publically released the Chip-and-PIN crack code software which successfully modifies the EMV validation protocol.
http://www.zdnet.co.uk/news/security/2010/10/25/chip-and-pin-crack-code-released-as-open-source-40090637/?goback=%2Egde_1848579_member_36113797
I wasn’t too impressed either with the response “it is unlikely that criminals will be motivated to undertake an attack ” since criminals in their opinion would prefer to focus on softer targets like online fraud. I don’t think that is the right attitude or that this will be the last security problem they will find. EMV has had 9 months since they were alerted to this security problem and its still open meanwhile MagnePrint is pushing their much lower cost anti cloning technology which works within Americas existing infrastructure.
Brian,
It needs to be said that the technology for reading magstripe cards realy has not changed in 30years. The main difference is the old inductive “casset recorder” heads have been replaced with “barber pole” magneto resistive sensors.
For those that want to know more all they need to do is look up the ABA standard which is also ISO.
I used to work many many moons ago for a company designing hotel door locks based around the ordinary magstripe card.
All you realy need is a magnetic head from a small casset dictaphone a differential amp bassed around an opamp and a lowpass filter. The output of which you can feed to a simple single transistor FM bug. The audio from the receiver can be feed directly into the mic input on a laptop. A component cost of around 2-3USD.
You can also get tiny colour cameras with 2.5GHz transmitter from the likes of Swann an Australian company. Atleast one of their tiny cameras has an audio channel as well so for an extra 30USD or less you have that part all sorted.
The next thing to sort out is battery life. Well a low cost micro switch can be used as a card inserted detector that fires up an NE555 timer chip that enables the power to the card reader and camera for say a minute and then shuts down.
The reception of audio at the PC can also be used to record video from the receiver via a capture card or USB dongle.
The hard part is making the correct housing look alike. However this is not that difficult to do provided you have an original “plug” to make a mold from.
If you want to know more just ask, and I speak English not Russian so that makes it even easier 😉
RFID chips have evolved significantly over the past few years. They are currently the most secure form of ID you can carry with you. This coupled with the additional security of biometrics on site virtually eliminates any threat of ID theft as it renders it useless. Biometrics CANNOT be copied and used by someone else. It is almost the same as a fingerprint. Duplicating it, while not impossible (if you have the original as a template and you know the points the biometric system is testing), is not finacialy reasonable.
Can’t read fingerprint from the coin. Can you place better photo?
@ Matthew Walker,
“meanwhile MagnePrint is pushing their much lower cost anti cloning technology which works within Americas existing infrastructure”
I’d be a bit carefull about this technology for a couple of reasons.
The first is it can be got around.
The second is it’s seductivly cheap and comes gift wrapped in soft soap and hard sell.
The way it works is it uses the signiture of the magnetic particles in the mag stripe to produce a “fingerprint” that although it looks like noise tends to be fairly constant for a given card.
It is a psuedo physical signature.
However there is a problem. The partical size in the magstripe of most cards is very large thus there is a quite low frequency limit on the card tracks and the signiture noise is likwise low(ish).
The problem is you can get audio or video tape where the particle size is orders of magnitude smaller and the frequency response of the tape is more than sufficient for the signiture noise” to be recorded onto it…
So the card noise signiture is clonable relativly easily…
Now the people behind this “magic grow” technology are aware of this as they have been called out on it in the past and admited it was a possibility…
So although not totaly snake oil it is something where if it is deployed in large numbers an arms race will develop.
We have seen the sorts of problems these arms races cost and at the end of the day it’s the consumer that pays both ways.
Yes there are problems with Chip-n-Pin but on balance I would rate it more secure as a system in the long run.
And this is the real point this noise signiture will if it’s deployed prolong the use of a technology that is way past retirment, just making the inevitable more expensive in the long run and causing the period of pain for consumers and traders alike to be prolonged.
@ Clive Robinson, thank you for the interesting reply regarding the particle size and the signature noise. I had assumed these details had been well hashed out but it seems if you are correct there is window of opportunity for a continuing arms race in that field. It would be good if the Magneprint people would respond to this thread. To be honest I too even before your information would have rated chip and pin in general probably more secure against cloning and most definitely has more potential functionality however as with all security the costs need to be incorporated into the equation.
The general cost of magnetic strip cards in Asia are around 5 cents each, smart cards hovering around $1-$1.50 so multiplied by the huge populations in the Area say for example Singapores neighbour Indonesia with 230 million people the cost difference can become significant especially when regional managers are working on a budget.
I dont doubt that smartchips will continue to expand market share however personal electronics and crypto based electronics systems scare me in general. In fact an underground European hacker is about to announce a serious break with a major West European contactless payment system next week at the CCC Chaos Computer Club conference in Berlin where they have reverse engineered the cipher used in the cards and found some vulnerability. I understand the fix will require reengineering 300000 terminals across 21 countries a spectacularly expensive and embarrasing task. I am not surprised the American decision makers are cautious when it comes to similar mass deployments and potential catastrophes which would probably gain far more media attention and heads rolling than in Europe.
It’s only a matter a time before other payment systems like Jack Dorsey’s Square are similarly compromised — in that case, a skimmer would be in software. In fact, it’s probably already being done, just not publicly known. Jack Dorsey has refused to comment on this particular vulnerability; perhaps you could take a stab at asking him?
Do you know if an anti-skimming device such as CPK (which detects magnetic field alteration near the card reader) would be able to capture such analog skimming devices?
I work for a company that makes an anti-skimming device which would be able to detect these skimmers as well as all sorts of others: http://www.atm-parts.com/products/anti-skimming.html.