Security experts often warn computer users about “keystroke-logging” malware, digital intruders capable of recording your every keystroke. But the truth is, real bad guys don’t care about your everyday chit-chat: They’re after the financial information. I was reminded of this reality by a feature built into a recent version of the infamous ZeuS trojan that makes it even easier for the crooks to ignore everything except for the goods they’re seeking.
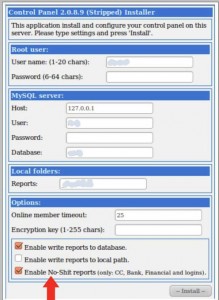 Pictured here is part of an administration panel for a botnet of PCs infected with the ZeuS trojan (version 2.0.8.9). ZeuS’ data-stealing components are legion, but one of its most useful features is what’s known as a “form grabber,” which will automatically steal any data the victim submits to a Web site inside of a form, such as an address, credit card number or password. It doesn’t matter if the Web site the victim is on uses encryption (https://), ZeuS extracts and stores user-submitted data before it can be encrypted and sent by the browser.
Pictured here is part of an administration panel for a botnet of PCs infected with the ZeuS trojan (version 2.0.8.9). ZeuS’ data-stealing components are legion, but one of its most useful features is what’s known as a “form grabber,” which will automatically steal any data the victim submits to a Web site inside of a form, such as an address, credit card number or password. It doesn’t matter if the Web site the victim is on uses encryption (https://), ZeuS extracts and stores user-submitted data before it can be encrypted and sent by the browser.
But even when a botmaster has configured his bots to only record data when the victim browses to https:// sites, the amount of data harvested from the entire botnet can easily exceed hundreds of megabytes per day, because many botnets are lifting this data from thousands of infected systems simultaneously.
So what if you only want only the cream of the crop? The ZeuS control panel I encountered has a handy feature, called “Enable No-Shit reports,” which when checked only stores very specific information sought by the criminals, such as 16-digit credit card numbers, and data that victims are submitting to pre-selected online banking sites.




Да, отличная версия, похоже.
I’ve advised a while ago some friends of mine who are totally reluctant to switch to Linux, that they at least might be a bit safer if they “randomize” their input when introducing their passwords: for instance type first the last 2 characters, then use the mouse to move the cursor in front of them and type some middle character and so on (being careful not to mix their position in the string). Brian wrote that Zeus can take screen captures when left mouse button is clicked, so this is probably effective only for password strings that are obscured on the screen, but since it looks the bot-herders are using highly automated systems to coalesce data, I was hopping they won’t bother to dig further if a password to an account of two do not match. My question to Brian and others more experienced than me is if I totally misguided my friends or my advice to them can give them some limited protection. N.B. They are the types that are almost afraid of their computers, they understand the security concepts but have trouble adjusting to new programs or OSes.
>that they at least might be a bit safer if they “randomize” their input when introducing their passwords: for instance type first the last 2 characters, then use the mouse to move the cursor in front of them and type some middle character and so on
This would have provided protection against the classic “keylogger class” of malware in the past. Zeus just collects the final form results, so there is no room for obfuscation, entry by mouse clicking on a graphical keyboard, etc. That advice now provides no protection to your friends.
@george: “They are the types that are almost afraid of their computers, they understand the security concepts but have trouble adjusting to new programs or OSes.”
1. The risk is online. For many users that means mostly while operating the browser. But some browsers are designed to work both under Microsoft Windows and Linux.
2. By running Linux for online work, but staying mostly inside the browser, users can avoid most of Linux while still benefiting from Linux malware resistance.
Terry
Thanks for the comment. That prompts a question on the approach taken by my share portfolio manager.
At log on the manager displays a small keypad on the screen, for the password, and the numbers are randomly displayed. I access the account using Firefox. Can you comment on that usefulness of that approach please?
Brian
Hi Brian!
“At log on the manager displays a small keypad on the screen, for the password, and the numbers are randomly displayed.”
So malware which does not record the screen during password entry might be confused, but recording is now a standard technique. I think we are past the era when that approach could be relied upon. Sorry.
Terry
Thanks for the reply. Disappointing but I now know there is a problem and the continuing need to be watchful.
Brian
It’s really too bad that many of the issues thought to be Zeus are never actually confirmed; rather, systems are taken offline and wiped before any work is done to verify if the incident is a result of a Zeus infection, or something else. As someone who does DFIR work, there are a number of other issues out there that do something very similar to Zeus.
If reactions to these issues were different, there might be data that could assist law enforcement in addressing the issue.
Harlan, you’re exactly right. Most business and PC users just want things working again, and don’t want to spend time or money investigating how/where the breach or infection occured. And they’ll keep happening until they wake up and realize that our investigations are the method we use to find their weak defenses and help plug them.
Dennis,
As such, I think a lot of incidents are attributed to Zeus that may not be. Even if the system were taken offline, a live acquisition performed, and then whatever the user wanted to do with it after that is fine…I’ve offered to Brian to analyze the image.
The one time someone who claimed to have been hit with Zeus reached out to me, all they could provide was some logs that gave no indication of Zeus at all.
I’ve even received this sort of request in my day job…and of those engagements where I receive hard drives or images, and I’m told, “We think we were hit with Zeus…”, I haven’t found Zeus, but something else entirely.
What a lot of folks don’t realize is that not only does their “wipe the drive and start over” approach simply lead to reinfection, but there is very likely some significant intel there for LE.
The whining begins as soon as the support guy shows up: “But I’ve got so much work to do” and “I can’t go that long without a machine” and “What about all of my information that I never back up?”
So it’s Format –> Image –> Reinfection all day and all night long. I try to tell them like this: doctors may have the capability to re-attach severed fingers, but most repeat patients would like to know who or what keeps cutting them off.
Thanks for helping make the world a safer place through information. Great article.
Such attention to customer service! If these Zeus guys supported proper commercial software with such gusto they’d make way more money than a couple grand here and there to some dodgy fat guy in sweatpants, or whoever their current clientele is composed of.
Is this truly a “new” version of Zeus? Nixing the Zeus/SpyEye merger stories. Or is this is a one off update by someone other than Slavik?
It seems like it is probably a one-off, rather than Slavik returning to Zeus.
Right now, I am wondering how my boss would handle it if I created a No-Shit Report… lol
I think most of us understand the need to get the password ‘right’ when we log into a site, but I’m wondering just WHEN this thing snags the info.. and should I not get the login info correct *the first time*.
Does this thing keep grabbing info even after I hit the key with the wrong info (a constant keylogger); thereby collecting info whether it’s correct or not?
@Jim: “Does this thing keep grabbing info even after I hit the key with the wrong info (a constant keylogger); thereby collecting info whether it’s correct or not?”
Maybe one misconception here is that we only need protect against a particular malware program. In reality, we have a whole class of somewhat similar programs which attackers change and adapt rapidly and interactively.
Our main problem is the general concept of “bot infection,” which is so powerful that, once resident, no particular defense can be sufficient. A resident bot can do anything and everything a user can do, and more, and faster. The defense is to not have a bot.
If we just had a program which could guarantee to detect a resident bot, we could run that before getting online, and that, at least in principle, would solve the problem. Since we still have a problem, we know that no such program exists. No antivirus can do what we need.
There are various approaches to addressing the malware problem. The obvious thing is to prevent any malware from getting in, typically from the network. Various current methods such as improved browsers, periodic patching and antivirus scanners have not contained the problem. In theory, a new Internet protocol which performed a cryptographic authentication of every piece of code before it could run might work, someday.
A complementary approach (a different defense layer) is to address the infection. A machine which just runs a bot in the current session has a bot for half a session, on average. A machine which is *infected* runs a bot full-time, on *every* session, for perhaps hundreds of sessions. There exists an opportunity to cut malware effectiveness by something like two orders of magnitude, *if* we can prevent infection.
Malware authors can write programs for any system. But if they want to make money, they will target the most common system. Over 90 percent of browsing occurs on Microsoft Windows. So, if a malware program somehow manages to get deposited in a machine and starts to execute, only if it is designed for Windows will it have a 90 percent chance of running.
As a result, over 99 percent of malware is written for Windows and will not function on other machines. So simply using some other operating system probably is the most effective thing one can do to prevent malware. Linux is free, and more than sufficient to support a modern browser.
A bot infection can overwhelm the operating system itself, and actually prevent the file system from reporting the existence of malware files. Files which have been changed can be dynamically “changed back” so they appear unchanged. That makes a resident bot very difficult to detect, especially by any program running in the infected operating system.
It is almost unthinkable that any program could possibly exist which could guarantee to detect any hiding bot. It might be possible for Microsoft to make a LiveCD to check and verify each file which must exist in their system, but Windows itself probably would need some redesign to deal with currently-normal changing files.
Because we cannot be assured of detecting a bot, we have almost no grounds for assuming one is not present. This is a very bad situation.
Another alternative is to prevent infection itself. This means stopping a bot from changing start-up programs and data on the boot drive which will be used to automatically restart the bot on each session. Hard drives and USB flash drives are particularly vulnerable. Even flash drives with a write-protect switch become vulnerable the instant that switch is changed for an update. Operating system software already has the goal of protecting the boot data, but has clearly failed. Perhaps someday we will have hardware support to make itt work.
Until then, we have Linux LiveCD systems, in which the entire operating system is re-loaded from a secure DVD on every session. In this way, any running malware stops at the end of a session, and is not re-installed. I am, right now, working in Firefox on a Puppy Linux system loaded from DVD. I recommend it, and I have some articles about it on my Computer Security page.
back @Terry
OUTSTANDING reply.. thanks
“If these Zeus guys supported proper commercial software with such gusto they’d make way more money than a couple grand here and there to some dodgy fat guy in sweatpants”
with some carders i know making over $30,000 a week (yes a week not per month) they can usally afford more than sweat pants.
Im not a carder, (though i do spam) and your average banking bot carder (as opposed to the low end mules and real life carders) are usally quite bright.
the problem with just limiting formgrab to https pages is that you will still pick up people writing and sending emails. hence why the custom no shit reports only limiting it to certain banking sites
Anything a spammer says is a lie. And he says he’s a spammer. Arrrghh, does not compute!
Dear Lowlife:
Spam uses up vast amounts of bandwidth that would actually be better used for pornography. It cost $ to create bandwidth. Ergo, you’re a thief. Thank you for your invaluable services.
IE: Yes, most readers of this blog & other sensible folk have a VERY BIG problem w/ Spam.
OOps. Reply to “Problem w/ Spam?”
Yes, I hate spam as much as you and most other people.
But I see as a positive aspect and a tremendous credit to Brian K. that his blog manages to attract also (self-declared) spammers and other figures making a living in this shady “business”, even more so when they leave (civil) comments allowing us a glimpse on the “other side”. Few people will argue that stealing CC info or identities is a more serious crime than sending spam and while I deeply disagree with both, I personally suspect a lower moral hurdle to become identity-stealing bot-herder if you are already a spam-sending bot-herder, thus I’m wondering if not most spammers will eventually “evolve” to steal CC info. If not, what is keeping them ? Desire to keep a lower crime profile ? Morality ?
I could have sworn that when I wrote, I had pushed the reply button to “Problem with Spam.” FAIL.
Am a fan of BK and the blog.
Dear Lowlife#2,
much porn is exploitative of the poor and destitute who are dragged into the sex industry, hateful against ethnic minorities, molds young men into an unnatural way of thinking about sex, and objectifies women causing some young women to think poorly about their sexuality.
The net would be better with NO spam and only AMATEUR, 100% unpaid in any way, sexual material if there were to be sexual material at all.
Has anyone considered writing something that would flood their server with bogus captured information that would include incorrect/random credit card numbers. If they got millions of bogus credit card numbers for every legitimate one that they captured from an infected machine, it could create a headache for the scammers as they try and figure out which ones are legitimate.
This was a fabulous article and great informative comments as well. In my biz I help folks with their Windows security layering and performance issues. It’s really unfortunate but I have found many users do not really seem to care about their security until it’s too late. I guess computer security isn’t trendy enough or something. 🙂 However, I have found many users with all sorts of little nasties running amuck on their computers too that they had no idea about.
One handy little gadget that I have come across and used is called Smartswipe. I’m not an affiliate or anything so this isn’t spam but I recommend it to my clients for online shopping. It currently supports IE and FF. Once you swipe your card, the credit card info is encrypted right inside the swiping device before it even enters your USB gateway into your computer. It only displays a screen with partial info to verify that it is correct and displays little locks where the captured credit card info is stored on the screen. If you have anything malicious on your computer, hackers will not be able to get any useful information. No typing is required so no keystrokes are recorded which is a little bit of added protection toward keylogger type Trojans.
Hi Kim!
“One handy little gadget that I have come across and used is called Smartswipe.”
Thanks for the reference; this may be a good find. Unfortunately, I find their technical explanations disturbingly casual, which immediately places me on alert.
Could you please look on the bottom of your reader and see if patent numbers are given, and if so, send them to me? (Click on my name to get to my web page, then click on “current address” at the bottom.) Patents might provide some better insight than their rather casual “white paper.”
Thanks!
This doesn’t cover session riding of course; but I still don’t understand how the bot is going to get anything out of the scrambled signal that comes from Keyscrambler. I’ve tested it and no video or keyboard can hook any information that is any good to the criminal; only random letters and numbers. Now this won’t stop them from riding the session into your accounts upon logon of course – but I seriously doubt anything you enter through the keyboard will be legible.
Form fillers like RoboForm and maybe LastPass may fail, but Keyscrambler not – unless someone can fill me in as to how they can do it.
I believe Rapport claims to do the same thing, but I haven’t tested that on it, only the session blocking, and I can attest to the fact that the code I used can’t even see a browser is in session! It can’t even see the browser is open.
@JCitizen: “I still don’t understand how the bot is going to get anything out of the scrambled signal that comes from Keyscrambler. I’ve tested it and no video or keyboard can hook any information that is any good to the criminal;”
We are forced to speculate because speculation is all we have to protect us against a future with unknown and dynamic opponents. Not being able to offer an existing bot example says nothing about our future security. Only when we can argue that what a bot would need to do is actually *impossible*, only then can we begin to accept an approach as secure.
When a bot is resident, it takes charge of the OS. So:
1) What Keyscrambler hooks might be the bot already.
2) Or the bot might come along later and still hook before Keyscrambler.
3) Or, once keys are scrambled, they necessarily must be *un*scrambled somewhere, and the bot can take the plaintext key data after that.
4) And all this assumes that some future bot cannot undo the scrambling itself, which is almost certainly wrong.
When we learn to program computers we learn the OS the way the manufacturer designed it. But when we confront a bot, we do not have the old OS anymore. Surely, almost all will be unchanged, but any critical area can be defeated, when worthwhile. We cannot depend upon our programming being able to do even as much as the expert attack code in some bots, so if an attack seems to require more than we can do, that does not mean a bot is similarly limited. The way to defeat a bot is to not have a bot.
“The way to defeat a bot is to not have a bot”
Reminds me of the 10 Immutable Laws of Security, in particular #1 and #2 which are reviewed in this old article from 2008:
http://www.eweek.com/c/a/Security/Challenging-The-Immutable-Laws-Of-Security
Law #1: If a bad guy can persuade you to run his program on your computer, it’s not your computer anymore
Law #2: If a bad guy can alter the operating system on your computer, it’s not your computer anymore
And this one is key and IMHO the main reason so many home and small business systems get compromised:
Law #6: A computer is only as secure as the administrator is trustworthy
Every computer must have an administrator: someone who can install software, configure the operating system, add and manage user accounts, establish security policies, and handle all the other management tasks associated with keeping a computer up and running. By definition, these tasks require that he have control over the computer. This puts the administrator in a position of unequalled power. An untrustworthy administrator can negate every other security measure you’ve taken. (Re-read that last sentence again!)
@Terry;
Thank you for your comments. I have a test kit that looks at interventions at all levels including the kernel space. So far only six major areas are being used by spyware now, that I’ve read about. Keyscrambler defeats all of these so far.
@xAdmin;
Ever tried WSS, DeepFreeze, or Time Machine by Commodo?
I agree we can’t be soothsayers about the future, but in my case, I’ll take the latest tech, and keep an eye open toward new developments.
Thanks!
JCitizen: “I have a test kit that looks at interventions at all levels including the kernel space.”
At severe risk of further beating this dead horse, I dispute the implication of “all levels.” These “levels” exist in the eyes of analysis, and are not limits on the malware attacker. I doubt that any “test kit” can find attacks substantially different from those which it is designed to find.
In fact, if any “test kit” *could* find all possible attacks, we would have a program which would find any malware, hidden or not. Then we could just run it before banking (if that would not take impossibly long), and if we were infected, we would not bank online. Just as simple as that, we would solve our online banking problem.
Since we still have a banking problem, we know there is no such thing. I claim that unknown attacks cannot be identified by tests any more than unknown malware can be detected by scanning, which is to say: from rarely to not at all.
I hear ya Terry; I’m only concerned with known threats not future ones. When they appear, I deal with it at that time. You are definitely right that the threat-scape is chaotic and unpredictable; I just don’t tend to worry about it – although a healthy dose of paranoia is always a good idea.
Thanks! I don’t feel the horse is dead yet.
To be proactive and try to stay ahead of the malicious out there would be a very valuable trait to have. Such a person should endeavor to start a security company, or perhaps join another existing coordinated effort in this war.
Greetings,
Has anyone tested the effectiveness of security solutions like SpyShield, Zemana, Online Armor, or (different approach) Prevx Safe Online (there is a free version), Trusteer Rapport, and lastly, Neo Safe Keys…against this type of Malware?
NN
@Norman Nescio: “Has anyone tested the effectiveness of security solutions like…against this type of Malware?”
Occasionally we do see some reports of testing, mainly from the solution providers. Commonly, previous solutions are shown to fail, while the shiny new product for sale succeeds. In reality, testing is neither very common nor very useful because those darned attackers just will not stay defeated!
Were we engaging a fixed threat, such as a particular attack program, we could prove a defense by testing. But malware evolves. Modern malware typically seems to be distributed as a development *kit* of various options, which may be enabled and even extended by the end-user/programmer. Attackers work to render defensive successes useless, and they are pretty good at it.
The current malware situation provides direct evidence that operating system software, no matter how-well patched, simply cannot be trusted with computer security. The obvious alternative is to find some way to lever absolute hardware certainty into the functioning software. But that only works when the hardware wall cannot be avoided by malware, and our current computer hardware does not seem to have the necessary secure base upon which to build. In general, our computer systems “allow” malware to make changes to the system itself, changes which render software protections useless.
As far as I can see, the vast majority of computer users (that is, Microsoft Windows users) just want some add-on to solve the malware problem. They certainly do not want to be driven out of their home, so to speak, into a Mac, or even Linux, especially since there can be no perfect solution anywhere, on our current equipment. But harsh reality intrudes:
In my view, and generally speaking, add-ons, both internal and external, can at best provide limited and temporary protection, even at substantial cost. They cannot be tested against the future. And if the past is any prediction, they will fail.
I haven’t tried any as I’ve not found the need. My preference is to use the axiom “An ounce of prevention” (prevent malware from even getting to your systems to begin with) and the K.I.S.S. principle. Those may seem contradictory, but in reality it’s about focusing on setting up a layered defense (Defense in Depth) to reduce your risk and NOT be low hanging fruit easy for the picking. As with any type of security, it starts with awareness. Become familiar with the threat landscape and take what you feel are appropriate steps to mitigate that. Learn as much you can about your computer, its installed programs and configuration setup. That becomes your baseline to work off of and stay in tune as to whether anything is astray. I think of it in terms of maintenance and paying attention to how something operates. There is a norm with most anything and if you pay attention to that you are in a much better position to notice when there may be something amiss. As with anything in life, there is no silver bullet that is going to take care of things for you. You have to put some effort into it and you’ll be rewarded in return. Or as I like to refer, you reap what you sow. 🙂
I’ve posted this before, but here is my list of a layered defense that has kept my Windows systems malware free for the past 14 years.
1. Use a non-admin (limited user) account for daily use (* see below)
2. Use a firewall (preferably a hardware firewall at the perimeter and a software firewall on each computer)
3. Use a blocking HOSTS file (ex. http://www.mvps.org/winhelp2002/hosts.htm)
4. Install ONLY required software using the latest versions, uninstall old or unused software (reduces system attack surface and minimizes patching)
5. Avoid Adobe Reader (ex. Foxit instead), Java, Quicktime, and Real Player
6. Avoid peer-to-peer file sharing software (extremely risky to obtain malware)
7. Keep the system fully patched (includes ALL software)
8. Use Antivirus (Anti-malware) software configured to update itself DAILY
9. Practice safe computing
a. Use caution with downloaded files and e-mail attachments
b. DO NOT OPEN E-MAIL ATTACHMENTS FROM UNKNOWN SOURCES
c. Be very cautious of attachments from trusted sources, if unsure, contact sender to confirm, otherwise, be safe, don’t open it, delete it
d. Be extremely cautious of links in e-mail (may be phishing attempt or malicious web site)
e. Browse wisely, hover mouse over links to see where they go before clicking
10. Routinely (at least monthly) backup your data to external media (CD/DVD, hard drive, network attached storage, etc.)
11. Use a UPS (Backup power supply and surge protector) to protect equipment from damage and minimize loss of data
12. Optional (but highly recommended):
a. Enable Windows Automatic Updates (Auto download and install)
b. Avoid webmail, instead use an e-mail client (ex. Outlook) and configure it to “Read all e-mail in plain text” and use secure (SSL) POP3 or IMAP
* A non-admin (limited user) account provides a greater level of protection should malware make it past your primary defenses to the desktop. Most malware is designed with the assumption the user is an administrator. Without “administrator” access, the malware is not able to run as designed and fails to compromise the entire system, worst case it is limited to affecting only the currently logged in user.
A few more points:
1. Disable unneeded Windows services (ex. WebClient)
2. Disable unneeded network controls (ex. File and Printer Sharing)
3. Use cookie ad blocking (ex. built into IE, Tools, Internet Options, Privacy, Sites, Block
4. If using a wireless network, configure it for WPA2 and a complex shared key
5. Never use your wireless network to access anything of sensitive nature (ex. online banking). Instead use a hardwire connection (minimizes network mischief, wireless can be sniffed over the air)
6. Before accessing any website of sensitive nature, close all programs, clear browser cache (temporary internet files, cookies, etc.). Use a stored bookmark to go directly to secured (SSL) login page. Do NOT browse to any other website (minimize cross site scripting issues). When done, use sites log out option, close browser and clear cache again.
Dear Norman;
Terry and xAdmin have excellent advice. My 2 cents follows. OnLine Armor is recognized by technicians everywhere as one of the best software firewalls going. However it doesn’t work on x64 Vista. I use Comodo on those machines, and if Defense + is possible to enable, it is a very good addition.
I’m not sure Prevx will work on a PC with Rapport installed – I value Rapport above Prevx. Prevx is not compatible with a lot of the new tools to fight these latest threats. As far as being a good AV, I can attest to that in my honeypot lab, but I NEVER use it to remove the infections, (which are rare because it blocks them before they get onboard) Prevx supposedly receives definitions from the cloud at the same time as the threat is discovered; I saw this claim with Viper too. I got to admit, Viper updated every 15 minutes or sooner, but was worse that a virus in how the system reacted to it.
However this is still no guarantee you will be even 90% protected. I have tested Rapport to other invasive code that take over the browser session and attempt to inject data into the forms open on the session. This code cannot see the browser is even open. Does this mean this will work forever? NO. However, you got to use what works for now until news surfaces that it has been pwned. Hopefully not for you are your clients.
It is my philosophy that my clients will not do as xAdmin admonishes, because they are human, and just won’t listen to good advice. I try to mitigate this as much as possible, and tell them the same thing he does, and hope for the best.
Mostly I tell folks to simply NOT enter personal data into their PCs at all, and definitely NOT to do banking or shopping online. I am surprised by the converts I have convinced of this – at least – and I don’t worry much about them. As for the rest of them, you have to take a risk assessment with each one of them, to determine what the disaster will be like after attack, and go from there. There is always an acceptable risk factor in every move on the web, if you plan right.
The million dollar que$tion still is how to get users to care about security before they’re victimized? Anybody have any great ideas about how I can drive this point home? It’s not a trendy or sexy enough subject for most people to care about until it’s too late. Fear doesn’t seem to work either unless it hits them in the a$$ets. I’m trying to educate users on preventative measures but it’s very difficult when they don’t find it of any real importance. I’m also referring to small and medium sized businesses as well as everyday single users. I genuinely care about the online safety of the user community especially newbies, seniors and children. Mac security is admittedly 10 years behind Windows and Mac users tend to feel untouchable. However, as the iPAD/iPhone craze gains popularity it will surely start seeing more attacks. Up until now, Window’s attacks deliver a poweful punch due to the enormous payload. Apple still has a ways to go but their time will come. The reason that I’m posting this here is that you all understand where I’m coming from so I would appreciate and respect your feedback. I would rather help users set up their security layering properly & educate them of risks beforehand rather than seeing them go through something that may have been somewhat preventable.
Thanks Kim
I’ve had better luck simply discouraging online transactions at all! My scare tactics seem to work pretty well. For those that refuse to implement everything I like to put in place, I try to help them determine the risk factors, and plan for damage before it hits.
They seem to react well to that. For those that are simply PC illiterate, I remote in for short lessons on in-depth defense strategy. I try not to overload them all at once, and eventually they pick it up. Suppressing the urge to IT speak in geekenese is a big winner.
Thanks J!! Appreciate your comments. Yes agreed, the remote lessons work very well. I also translate geekenese fluently for my clients. I have actually been hired to translate between client and vendor because some vendors totally speak a foreign language as far as the client is concerned. The worst part is when a vendor is totally arrogant about it, like the client is suppose to already understand their business. Perhaps then I just need to be scarier as suggested…..ha-ha!! Cookie Monster???
I hear ya Kim!
I fear I am not the worlds best saleman, but I do try – at least! 🙂