Extradition of Accused Masterminds Moves Forward
Millions of computers infected with the stealthy and tenacious DNSChanger Trojan may be spared a planned disconnection from the Internet early next month if a New York court approves a new request by the U.S. government. Meanwhile, six men accused of managing and profiting from the huge collection of hacked PCs are expected to soon be extradited from their native Estonia to face charges in the United States.
 DNSChanger modifies settings on a host PC that tell the computer how to find Web sites on the Internet, hijacking victims’ search results and preventing them from visiting security sites that might help detect and scrub the infections. The Internet servers that were used to control infected PCs were located in the United States, and in coordination with the arrest of the Estonian men in November, a New York district court ordered a private U.S. company to assume control over those servers. The government argued that the arrangement would give ISPs and companies time to identify and scrub infected PCs, systems that would otherwise be disconnected from the Internet if the control servers were shut down. The court agreed, and ordered that the surrogate control servers remain in operation until March 8.
DNSChanger modifies settings on a host PC that tell the computer how to find Web sites on the Internet, hijacking victims’ search results and preventing them from visiting security sites that might help detect and scrub the infections. The Internet servers that were used to control infected PCs were located in the United States, and in coordination with the arrest of the Estonian men in November, a New York district court ordered a private U.S. company to assume control over those servers. The government argued that the arrangement would give ISPs and companies time to identify and scrub infected PCs, systems that would otherwise be disconnected from the Internet if the control servers were shut down. The court agreed, and ordered that the surrogate control servers remain in operation until March 8.
But earlier this month, security firm Internet Identity revealed that the cleanup process was taking a lot longer than expected: The company said more than 3 million systems worldwide — 500,000 in the United States — remain infected with the Trojan, and that at least one instance of the Trojan was still running on computers at 50 percent of Fortune 500 firms and half of all U.S. government agencies. That means that if the current deadline holds, millions of PCs are likely to be cut off from the Web on March 8.
In a Feb. 17 filing with the U.S. District Court for the Southern District of New York, officials with the U.S. Justice Department, the U.S. Attorney for the Southern District of New York, and NASA asked the court to extend the March 8 deadline by more than four months to give ISPs, private companies and the government more time to clean up the mess. The government requested that the surrogate servers be allowed to stay in operation until July 9, 2012. The court has yet to rule on the request, a copy of which is available here (PDF).
Not everyone thinks extending the deadline is the best way to resolve the situation. In fact, security-minded folks seem dead-set against the idea. KrebOnSecurity conducted an unscientific poll earlier this month, asking readers whether they thought the government should give affected users more time to clean up infections from the malware, which can be unusually difficult to remove. Nearly 1,400 readers responded that forcing people to meet the current deadline was the best approach. The overwhelming opinion (~9:1) was against extending the March 8 deadline.
In related news, the six Estonian men arrested and accused of building and profiting from the DNSChanger botnet are expected to be extradited to face computer intrusion and conspiracy charges in the United States. According to the Baltic Business News, an Estonian court ruled last week that the country can extradite four of the six (two were already cleared for extradition). The story notes that the final decision on the extradition will be made by the Estonian government after the court’s ruling has entered into force, but sources close to the investigation say the extraditions are all but assured.
Among those facing certain extradition is the alleged ringleader of the group, Vladimir Tsastsin, who for many years ran a domain registration firm called EstDomains that was heavily favored by cybercriminals. In 2008, ICANN, the nonprofit organization that oversees the domain registration industry, revoked EstDomains’s contract to sell new domain names, citing Tsastsin’s prior criminal convictions for forgery, money laundering and credit card fraud.
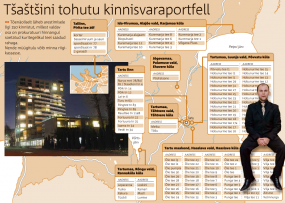
Tsastsin and the five others are alleged to have made at least $14 million selling hijacked search traffic from infected PCs to advertisers, and by swapping ads displayed on popular sites with their own ads. The government says Tsastsin laundered the ill-gotten gains by purchasing dozens of cars and real estate properties, including a number of empty lots. The infographic above, published by Eesti Päevaleht — Estonia’s largest daily news outlet — shows some of the properties Tsastsin (bottom right) and his compatriots were alleged to have purchased with the funds earned from the DNSChanger Trojan activities.
A copy of the indictments returned against Tsastsin and others is available here (PDF).





Ridiculous, it’s not that hard to remove I do it all the time. Get your act together. If they don’t force the issue these lazy companies will try to wait indefinitely. Most of the people asking for the extension just swap out PC’s anyway. Just take the things offline and reimage them.
Someone explain to me why we should trust companies that can’t cleanup an easily identifiable malware infection in under 120 days?
Has a list of companies that have not cleaned up their act be determined?
<aybe some public shaming is in order.
… or trust the government agency whose IT systems manager can’t clean up their systems in the 9 months already allowed.
I say, “shut ’em down March 8”.
That will prompt the mess clean up pronto…!!
Affected Agencies should, uhhhm, “re-assign” their IT managers to the parking lot janitorial squad detail.
I do understand that it is ‘useful’ to get your acts together an clean up infected systems. But I can’t see what’s the specific harm of this planned deadline extension. In the end it is ‘just another DNS’, that is no longer under the control of criminals (ok, you might not trust the government …).
I’am absolutely not flaming, I really have no idea what would be so terrible (and Mr. Krebs doesn’t mentioned a reason, just the vote results).
Do you really think DNSChanger is the only thing on these infected systems? When was the last time you cleaned a system that only had on piece of malware on it. These systems are doing all kinds of harm.
I’d like to know how much this is costing. A “private U.S. company” has been ordered by a district court to handle the DNS requests of 3 million users. I’m more than a little surprised that it hasn’t come up. I doubt it was community service ordered in an unrelated court case. Even if it’s being handled by one computer with the monitor unplugged, it’s a nonzero cost and I can’t imagine a government contract for service “at cost.”
Is this company one opposed to or requesting the deadline extension?
Extend the deadline and the execs of those companies will continue to obligate their resources (IT personnel) elsewhere. Like gas, and applications programs, management expands to fill all the available space (time).
I never understood why the only options are to redirect to the proper websites or kill the DNS competely. Why don’t they redirect everything to a webpage that basically gives the entire story and says the FBI says you should fix this computer, contact your IT department or follow these instructions. If these instructions are not followed the internet to this system will end in Early march.
Even my ISP has the good sense to do this if I didn’t pay my bill.
Agreed Tatarize,
I think many of the readers are missing 1 key point, and that’s some companies might not know a machine is infected. If they got a letter from the FBI then all they know is that a machine in their domain had it at one point, but since everyone NATs their IPs how can a company find a specific host that was compromised (assuming it was a corporate machine and not a visitor’s). More time allows IT to dig through logs and track down the machine and perform due diligence in case a breach occurred.
A few commands will build a list of infected machines. If an IT department won’t even do this pathetically small amount of work to clean their own network, an extension won’t change anything.
Just kick them off the Net. Their irresponsibility is a burden on everyone else and it’s not right. It’s selfish to think it’s okay for someone to make a mess and expect others to clean up after them.
Trouble finding the infected computers by IT? It’s called review DNS query logs and utilize current anti-virus protection.
120 days and they still can’t find the machines? Let’s help them out — turn down the servers and IT departments everywhere will hear immediately from all infected users (“I can’t get online suddenly!”). Problem solved. This is beyond absurd.
Personally I think there’s a thread of an idea in there:
Can’t find the machines? BLOCK the government’s DNS servers and you’ll hear immediately from all infected users.
How hard is that for an IT department to do?
Hint of arrogance coming from this forum today.
Many companies are small with no dedicated IT. They think computers are like toaster. These are obviously the companies that are most likely to be infected. They’re also the companies that are least likely to spot the infection and be unable to clean it if they do.
I agree with the “pain is educational” line. I don’t agree with the macho, “anyone could clear this” and “just reimage” comments.
I doubt many Fortune 500 companies fit that description. As for the companies that do, I don’t think it’s doing them any favors to help cover up their infections.
Nonsense, it helps IT workers save face. Besides if they just firewalled the servers they might upset people. Irony intended, but why do get this creepy feeling?
Several of the early malware variants “fail back” to using the real DNS settings if the hacker DNS isn’t available.
The version that hacked routers only seemed to change one of the DNS servers, the other was still the ISPs DNS server. I don’t know if that was specific to the router brand.
The version that established a rogue DHCP server caused immediate outages to side-impacted boxes in a typical (no DNS outbound) IT environment.
Most of you are idiots.
I wonder who will get these IP addresses next? Whoever gets them will be sucking down a bit of unwanted traffic, and they will have a chance to create some mischief of their own.
>>Also why on Earth did this need to be handed to a private
>>company?!?!?!?!?!?
Did you look at the list of companies and groups participating? Some are recognizable security researchers who have done this type of thing on their own before, with no LEA involvement.
The DNS servers are being run by the ISC. I’m sure you’re familiar with them.
Sorry, that wasn’t all in reply to Mark.
Thats like saying i dont know much about cars and i am a simple company so i dont need to keep my cars/trucks in a state that does not endanger me and others. And of course i dont need a drivers license either.
I’m really growing to hate the car analogy, so apologies for that triggering my response. That said…
Management appreciates cars and trucks, they know maintenance (or lack thereof) will have these results. Computers don’t have the same reliability in their mind, nor do they have the same connection of upkeep. Would people bother to maintain their cars to the same standards they current do if every few years the MPG doubled on the newer fleets while the bottom fell out of the market for the old? No.
Small businesses measure the expense of occasionally and possibly writing off machines as being cheaper than constantly paying someone to do something that they can’t immediately appreciate. It’s hard to prove a negative, and proving that machines “would have run fine for business needs” in the absence of an IT person is nigh on impossible.
I hate to have to self-reply.
I realized, I didn’t weigh in on the issue. I did vote for the “Let it end, pain is educational.” It’s not the macho “It’s an easy fix” attitude that drives it (Though it IS an easy detect and fix). It is because people don’t know that there is a problem until it’s in front of them.
Small businesses are the ones that will probably get hurt the most by this. The Fortune 500’s have IT people. When it goes down, they’ll finally be free to go fix the machines like they’ve been asking to do. But the little guys won’t. However, as a previous commenter has said, do you think that’s the only malware on those machines? It’s better to bring the machine 0ffline so that the business knows it has a problem and has to fix it. They’re going to lose no matter which way this falls, so it’s better to get it over with now than let it malinger on.
And how much will it costs these small companies when a key logger dumps every Credit Card number the company has ever typed into a database in Russia.
As someone above noted, it’s likely that a lot of those systems have other malware, since access to AV has been disabled, and they got a dose of DNSChanger in the first place. Are people better off continuing to do e-commerce and expose personal information on those machines, or being forced to get expert help? Judgement call, but this readership seems to agree on the latter choice as the best balance of prudence and convenience.
I’ve had the DNSChanger DNS Server IPs blocked in my corporate firewalls for some time now.
85.255.112.0 through 85.255.127.255
67.210.0.0 through 67.210.15.255
93.188.160.0 through 93.188.167.255
77.67.83.0 through 77.67.83.255
213.109.64.0 through 213.109.79.255
64.28.176.0 through 64.28.191.255
(Credit to Ars Technica)
…weighing in as firmly against the deadline extension. Frankly I can’t see ANY reason why this hasn’t been taken care of by now. @tatarize had an excellent point. The FBI should simply have just set up a redirect to an info page and left the server on for a few months then killed it. Also why on Earth did this need to be handed to a private company?!?!?!?!?!? The FBI can’t babysit a CNC server? C’mon.
@bob I’m sorry but I don’t think that this is arrogance. It’s 2012 and any business that requires the use of a computer has an obligation to both themselves and their client/customers to maintain those systems. If a business is to small to staff its own IT dept then they need to have an IT consultant that checks in on them regularly. They should also have someone in the business who is at least moderately versed in basic IT needs for business organizations. It is neither the government’s or the collective world’s responsibility to hand hold people who refuse to learn about or maintain the tools that they need to run their businesses.
For the rest of the businesses that do have an IT department there is no excuse (this goes doubly for any Gov or F500 organizations…shame on you). My god really I mean who actually fights viruses anymore? These people should absolutely just be reimaging. There is no excuse. If you don’t want to purchase an imaging system Free Opensource Ghost is great and it runs on an Ubuntu server. It takes about an hour to set up and save desktop admins an untold amount of labor. If you don’t have an imaging system, or at the least spare clean boxes lying around that you can cycle out, your IT strategy is weak and that’s no one’s fault but yours.
How about a black-out day first. Shutdown the DNS servers so that those not aware of the situation are suddenly made aware.
Redirecting also sounds like a good idea. But I’d personally be really suspicious seeing a website that said, “Click here to fix.”
That’s how my sister-inlaw got in trouble the first time – her computer was slow so she clicked on one of those ads.
I also would be shy of any click here to fix, however a redirect to an official looking FBI page (especially if the url is fbi.gov) explaining the situation and suggesting you do research on another machine would probably do the job without training users to blindly click.
Jay
Having worked for very large entities for the past 20 years, I can understand where some long forgotten machine in a closet could have been infected and still has this. Yes, machines end up in closets, built into walls, weird things when you have over 100,000 devices on the network. There is NO reason why they should have kept providing these DNS servers though. No machine that is infected would have any importance. Shut the temporary DNS setup down.
Brian, i really can’t understand the problem. The most correct idea is to resolve ALL dns requests TO ONE ip, where will be the site about DNSChanger, with full information about the problem on some lang, may be with free program for uninstalling DNSChanger. “If you see this page, you are infected by DNSChanger, blah-blah-blah, to remove it blah blah blah, unlit you make it, all your dns requests will go to this site”. Why they can’t do that way? Sorry for my english.
Why are companies allowing communication with random DNS servers in the first place? Egress filtering should be established to allow communication with only “sanctioned” DNS servers. Then, if the DNS settings were overridden, the end user would immediately realize something is wrong.
If we are disconnected from the Internet, how do we get service from our anti-virus etc. security service, to fix the problem?
If we are infected with this thing, we can be disconnected from the Internet, so how can we know if
(a) we are in fact infected
(b) our ISP or anyone else THINKS we are infected, and thus might disconnect us?
I have in the past had hassles with my ISP, because while my anti-virus etc. service said I was 100% clean, my ISP both said I was infected, but was unable to tell me with what, or how to fix it, other than by doing exactly what I was already doing.
Checking for DNS Changer on Windows XP
To check if your Windows XP machine is infected, frist click the “Start” button.
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
this is what i get clicking on the ……”step-by-step instructions at this link to learn of possible DNSChanger infections.”
no option for vista!
first not spelled right!
Am i infected?
Checking Home Routers for Infections
Coming soon
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
also i get this clicking on Home Routers
Pull the plug on the FBI servers and donate the infected comp;uters to the local high schools. The students could try to clean them up using the various free downloadable standalone anti-virus products loike Microsoft System Sweeper for example. The companies could take a tax deduction an d the kids might learn something.
I can see why the state department would want to delay shutting down the DNS servers until they’ve actually completed the extradition of the Estonian perps. Half a million angry people disconnected from the internet in one fell swoop in the middle of a business day? A lot of European countries won’t extradite criminals to the US if they could potentially face a death penalty. 😉
“I can see why the state department would want to delay shutting down the DNS servers until they’ve actually completed the extradition of the Estonian perps”
Perhaps the plan is to shut the servers down during their trial, to make a point. And hope that none of the jurors has an infected PC and is suddenly cut off from the internet ….
I wouldn’t want to have to deal with the change of venue hearings. They may want to keep the servers going until they’ve got the jury sequestered somewhere they won’t hear the howls of agony when people can’t visit FB from work.
Brian,
Do you know if there has been any thought to include DNSChanger detection in the monthly Microsoft Malicious Software Removal Tool? I’ve read security reports in the past, claiming that this tool has removed millions of various infections over the years. Not sure if the DNSChanger malware is too embedded/complex to include in the monthly MS patch, but it’s at least worth a little pondering.
http://support.microsoft.com/kb/890830
It can be difficult for IT departments to track down rogue DNS traffic through within their network. Taking the DNS servers offline would be the best thing to do – the infected NATd computers would no longer function and IT departments could easily track them down based on service calls.