Global Payments Inc., the Atlanta-based credit and debit card processor that recently announced a breach that exposed fewer than 1.5 million card accounts, held a conference call this morning to discuss the incident. Unfortunately, that call created more questions than it did answers, at least for me. The purpose of this post is to provide some information that I have gathered, and a few observations about the reporting on this breach so far.
 In a conference call this morning, Paul Garcia, Chairman and CEO of Global Payments (NYSE: GPN), declined to offer few new details about how the breach happened, beyond the details the company released in its press release last night. He also declined to comment on reports that the breach may have dated back to at least January 2012. Garcia emphasized that the company self-reported and discovered the intrusion in early March, and proactively notified law enforcement officials and hired independent forensics investigators.
In a conference call this morning, Paul Garcia, Chairman and CEO of Global Payments (NYSE: GPN), declined to offer few new details about how the breach happened, beyond the details the company released in its press release last night. He also declined to comment on reports that the breach may have dated back to at least January 2012. Garcia emphasized that the company self-reported and discovered the intrusion in early March, and proactively notified law enforcement officials and hired independent forensics investigators.
When asked about the timeline first reported by KrebsOnSecurity.com last Friday — that Visa and MasterCard were warning of a payment processor that had an exposure between Jan 21, 2012 and Feb. 25, 2012 — Garcia said, without elaborating:
“There’s a lot of rumor and innuendo out there which is not helpful to anyone, and most of it incredibly inaccurate. In terms of other timelines, I just cannot be specific further about that.”
He went on to state that, “This does not involve our merchants, our sales partners, or their relationships with their customers. Neither merchant systems, or point of sale devices, were involved in any way. This was self-discovered and self-reported.” Databreaches.net has a decent round-up of the call details, as well as other reporting on this breach. A recording of the conference call is available here.
I’d like to share a few thoughts on my own reporting as it relates to this breach. First, when I published the story early last Friday morning that is widely credited as the first to break the news of a large processor breach, at that time I did not know for sure that Global Payments had been compromised. I’d heard it from one source, but could not get it from a second source. The old-school reporter in me held back those details from my story.
Several readers have called me irresponsible for quoting anonymous sources stating that the Global Payments breach may have affected more than 10 million cards. This is simply not true. I didn’t even mention Global Payments in my original piece. That information was dug up by reporters at The Wall Street Journal. Indeed, given GPN’s statements thus far, I continue to be nagged by the possibility that my initial reporting may have been related to a separate, as-yet undisclosed breach at another processor. I mentioned this to a reporter at ABC News today, who included my perspective in a story here.
RUMOR AND INNUENDO
GPN said it would allow an hour for the call and for questions, but it told callers at the beginning of the conference that it would be using a portion of the call time to talk about its 4th quarter earnings. Although I sat in on the GPN call this morning for the entire hour and waited in the queue to ask questions, I was not afforded the opportunity. Nor did I hear questions allowed from reporters at mainstream news media outlets cited in this story. The company has not yet responded to my questions, which I submitted in a phone call after the news conference.
What follows is a partial brain dump on some of the information and interesting tidbits I’ve been able to uncover in my reporting today, in no particular order. Some or all of them may turn out to be relevant to the Global Payments breach, to a separate incident, or not at all.
-For the past two years, GlobalPaymentsInc.com has been hosted at MaximumASP, a hosting provider in Louisville, KY. On Feb. 20, 2012, the company moved its Web site to Amazon’s EC2 cloud hosting service. MaximumASP declined to answer questions about possible reasons for the switch, citing customer confidentiality policies.
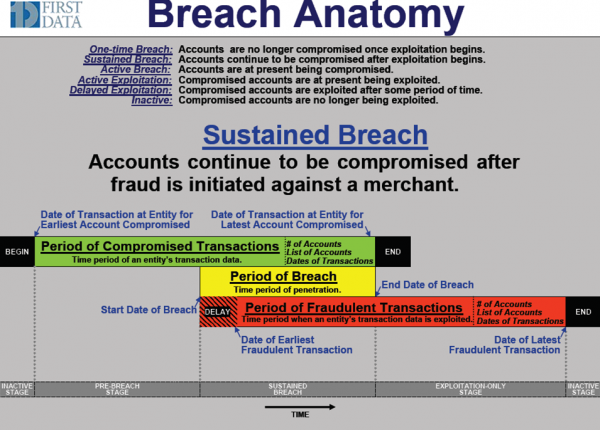
-A source shared with me the following diagram, which provides a bit more perspective on how these breaches are typically viewed by Visa, MasterCard and card processors. Note that the period of compromised transactions is also sometimes called the “window of vulnerable transactions.” It’s also important to note that that discovery of the breach may or may not happen after the start date of the breach.
-The New York Times in a story published Saturday cited unnamed sources saying that this was the second time in a year that Global Payments had experienced a breach. I have heard likewise from an anonymous hacker who claims the company was breached just after the new year in 2011. The hacker said the company’s network was under full criminal control from that time until March 26, 2012. “The data and quantities that was gathered [was] much more than they writed [sic]. They finished End2End encryption, but E2E not a full solution; it only defend [sic] from outside threats.” He went on to claim that hackers had been capturing data from the company’s network for the past 13 months — collecting the data monthly — gathering data on a total of 24 million unique transactions before they were shut out.
When asked if he had evidence that would back up his claims, the hacker produced a Microsoft Word document with Global Payments’s logo entitled “Disaster Recovery Plan TDS US: Loss of the Atlanta Data Center.” The document appears to have been created on May 6, 2010 by Raj Thiruvengadam, who according to LinkedIn.com was an Atlanta-based Oracle database administrator for Global Payments from May 2006 through August 2011.
I asked Global Payments if they could verify the authenticity of the document, but have not yet heard back from them. I will not publish it, as it contains apparently sensitive information about the organization’s internal databases. A screen shot of the title page is below.
More to come as information is available.





“Bran”, “Brain”, “Mr. Integrity”, whatever we may call you Brian, thank you for your exemplary commitment to keeping us informed with your un-biased reporting!
Brian, amazing reporting, and gigantic props on the scoop. This is very enlightening, and weighs heavily on the business I am in. You have definitely provided me with a service that I cannot procure for myself.
This story just continues to get more interesting, and I must say that the line, “the company’s network was under full criminal control” was very disturbing.
call it a hunch, call it facts, call it reporting. But I think that another company that is in the same area is involved with this.
Company name: TSYS
Brian I am sure you know more than I do about them… perhaps you can use your skills to investigate….
TSYS, aka “Total Systems”. Another big processor that has been around for a while.
Maybe they spent too much effort on ethics?
http://www.greensheet.com/newswire.php?flag=display_story&id=25830
Hey Brian – quick typo fix for you: very=verify?
“I asked Global Payments if they could very the authenticity of the document”
yup, thanks. fixed.
another typo I guess – sorry that I’m lazy to write you by mail
…who according to LinkedIn.com was an Atlana-based Oracle database administrator…
should probably be Atlanta-based
That document proves nothing. It just proves they had access after the document creation date. If you were to break into the company I work for, you could find procedures from as early as 2004 that have not been changed. They just sit on a directory and are referenced as needed.
If your company hasn’t updated DR procedures since 2004, you better hope you don’t need them.
That document proves *little*. Leaked internal documents do point to a large-scale compromise however. At the very least, Global Payments needs to explain how and when this document got leaked. But that seems unlikely – they seem to be in the downplaying mode now and refusing to give out any additional information.
• Well I thought you were main stream media but anyway better to get a story that is told with some integrity even if some facts are askew as is generally the case on breaking news than to get drivel from a spin doctor. Earlier in week Computerworld were running a story that was a veiled criticism of your story (or maybe it was overt) claiming it was only 50,000 you said 10,000,000 it turns out may be more like 1,500,000 well you were out by 6 fold overstated but they were out by 200 fold understated. In any case it is irrelevant as even one breach from a privacy perspective is one too many. Computerworld then followed up with headline “Global Payments says fewer than 1.5m cards affected in data theft” I don’t have anything against the media bickering about facts that is all part of getting the story out about these incidences to protect the public and I hope Krebs doesn’t become too circumspect as long as facts in error are correct in follow-up the job is done. Not quite so easy for the companies the subject of the stories because the days of saying “well we only had a small breach” are over, from a privacy perspective zero tolerance is all that is acceptable if individual rights are to be respected and expensive class actions avoided.
Brian, do you know whether this payment processor handles Discover as well as Visa and Mastercard? My Discover card was breached and cloned recently, and in resolving that I determined that there was a significant breach at Discover recently. I have heard nothing indicating that Global Payments handled Discover….
GPN today said all card brands were affected.
You know you rock, don’t you! 😉
Btw: “Raj” seems to be short for “Rajamani”…
Global Payments does handle Discover. We are a Discover merchant who had a merchant agreement directly with Discover until they farmed it out to Global Payments a couple of years ago.
Hey Brian… thanks for the diligent reporting on breaking news; sounding the alert, and inspiring us all to check into our accounts more often than the ‘once a month’ billing cycle.
We all should observe that any enterprise victimized by such a breach will be in damage control mode and rather parsimonious with the details on the extent of the data theft.
Criticisms on your reporting are brushed aside, as major damage is likely to have occurred and the details of which will take time to discover, if fully revealed at all. Not likely IMO.
Im sure the FBI will catch them soon. *snicker*
I’m sure Albert Gonzalez thought the same lol.
The FBI didnt catch Gonzalez.
A disaster recovery plan is hardly a top secret document. I would suspect that dozens of Global employees and contractors would have had access to it. I also guess that it would have been updated far more recently than 2 years ago.
If that is the best that your “source” could provide then my bet it that it is some poop disturber looking for attention.
On the other hand why should GlobalP. update a disaster recovery plan “Version 1.0” from 2010 if it took sooo long to complete the document – maybe they’re just lazy and that’s the vulnerability used? (AFAIK source didn’t claim it was the last update…)
A disaster recover plan outlines the process a company is to follow in the event of major systems outage or failure. I suspect that this document details how Global would fail over to a backup datacentre or remote site to continue operations in the event of any emergency.
The document could contain information on what to do in the event a security breach but that it usually covered elsewhere under PCI and would not be the primary purpose of the document.
Hey Brian, wanna sell me some of those cvv you’ve been stealing lately? I can buy wholesale and we flip the price to retail bro, get at me. I’m at carder.pro
Uh, April Fool’s Day was yesterday, bro.
It must be assumed that Global Payments was at least compliant with one of the basic tenets of PCI DSS; that Track 2 data is never stored. It’s dangerous to speculate, but it may be that the data was being collected in real time and not from accessing the transaction database files. In which case, the diagram does not apply because the Period of Compromised Transactions should be concurrent with the Period of Breach. However, if the breach first happened some time ago one would have expected to have seen some fraudulent transactions because the fraudsters don’t usually hang around before they start to exploit their cardbase.
I wouldn’t be quick to make that assumption, TDJUK! Even for a processor, I’d be surprised to hear of them storing TRACK data, but I’ve seen much worse. I agree that it is much more likely the attackers were able to capture transactions in transit.
Speaking of fraud, I saw in one place that there were 800 occurrences of fraud traced to this breach, but other stories claim there has been no fraud associated with it.
What’s the word on fraudulent activity and GPN breach data, Brian?
I don’t think it matters that Track 2 is not stored. If you look at Wikipedia’s article on “Magnetic stripe card”, you will see that the data on Track 2 is a subset of the data on Track 1. (Track 2 is stored at one-third of the bit density as Track 1. Apparently it functions as a backup in case Track 1 is hard to read.)
Track 2 is NOT a subset of the data on Track 1 as it has a separate purpose that Track 1 thus is not a backup. I will not mention what is on either tracks in detail, but both contain enough information to clone a credit card.
Processors are not to store any magnetic strip data, which is Track 1 and Track 2 data as dictated by the payment networks. PCI also indicates this, but the networks have additional rules on how these companies are to operate when dealing on their network.
If GP indicated that track 2 data was stolen, then I can make the assumption that either they are storing data that they are not supposed too. Or the data compromised was being taken at real-time, meaning that other data and not just track 2. This means that the authorization message may have been compromised, which contains more information that other than just the credit card number and expiration date, such as security authentication codes.
No issuers have controls to help mitigate the fraud once it has been determined that these card numbers have been compromised. That would entail re-issuing new cards and identifying the old as stolen. Now it is going to take some time for GP to make the full analysis on what those card are, so anyone that has the information is going to quickly use it before it is useless.
This is precisely my concern. There is much more to this story than we’re being told. I think Global Payments is gambling on what we will find out, if there’s no fraud, then they can maybe remotely contain it. If there’s fraud, it will just be a matter of time before this unravels. And it could sink the company.
If it turns out this company has been breached for a couple months, let alone 13, it’s virtually inconceivable there will be no fraudulent transactions. They refuse to answer extremely basic questions about the nature of the compromise, which is the least incidental aspect of the situation. The breach details are even more obscured.
I think the lid has hardly opened up on this story.
Thanks for all your digging and probing, your tenacity, and the smart logical posts.
Arguing about whether it was 50K or 10M compromised accounts is like saying you’re only a little bit pregnant. (Well, not you personally, Brian…) There’s not supposed to be any leak, even for a single transaction. The attitude that there is no point investigating how a single card has been compromised is how carders can get a continuous free flow of stolen accounts, one at a time.
The Track2 data can be stored, if needed. the PCI DSS requirements are suitably vague on this.
See PA DSS V2.0, requirement 1.1
” It is permissible for Issuers and companies that
support issuing services to store sensitive
authentication data if there is a business
justification and the data is stored securely”.
Whether GPS had such a need, and whether it was stored securely we don’t yet know. It could have been an insider attack that bypassed secure authentication. We can but speculate for the moment.
Paul
Agreed. PCI DSS 3.2 has the same get-out for issuers, but does GPN offer issuing services? The indications are that the breach is on the acquiring services side, but we’ll have to wait and see.
Vague yes, but in specific situations. Here, the “suitably vague” bit in section 3 is out of context. You’re reading from the PA-DSS, which is written for payment applications, and doesn’t apply to processors and merchant acquirers.
The issuing process, which is arguably the only reason for storing track data also doesn’t apply to a processor like Global. The banks issue. Processors authorize and settle.
Processors do not authorize or settle as they just pass the data onto the Issuer to authorize the transaction or send the settlement data to the Acquirer to pay the merchant and charge the cardmember.
They may perform some aspects of the acquiring process, but they will never authorize the transactions as the Issuers have more sophisticated systems to handle this work.
I work for a company in Europe (ATOS Worldline) who provide business process outsourcing for the major European banks (hence PCI DSS applies).
We also, in some cases, licence our systems to be installed and run on clients premists (hence PA DSS applies).
We handle processing on the acquiring side AND on the issuing side. So processors can Issue!:)
Moreover, looking at Global Payments website, it seems that they may handling issuing, in Europe at least (see http://www.globalpaymentsinc.com/Europe/productsServices/cardIssue_personalization.html).
Anyway PA DSS 1.1.1 is covered by PCI DSS3.2, with the same caveat/exception.
If Global Payments US do not support Issuing functions then it looks more likely that this is indeed transactional data where the channel has been compromised or not encrypted.
Anyway, for me, I find this situation troubling. Heartland Payment Systems were PCI certified. They were hacked, they lost their PCI certification (and now have recertified). The same story is happening here with Global Payments.
So what is at fault here. Are the PCI standards not strong enough? Is the audit not testing enough?
Hearltand Payment Systems were severely damaged and Global Payments are already suffering, on their share price and on public image. Lawsuits to follow?
Visa and Mastercard have their noses clean. They publish the Data Security Standards. If there is a breach, it’s because someone is not following these standards (even if they are certified!). Not our fault say they!
Here is hoping for strict regulation for software vendors and financial institutions, to make everything clear and clean for everyone, and to concentrate on security, not on covering asses.
PCI’s (Council, Processors, Merchant Banks, Merchants, and their security folks) main challenge is transformation from a mindset geared toward once-per-year audit for compliance to a day-to-day proactive security posture. PCI-DSS 2.0 already covers eg. daily log monitoring, but the mindset still needs tweaking.
Brian, as always, excellent reporting with integrity. I read your stuff with interest, but this one hits home, because GPN is the processor for most of the merchant IDs where I work.
It seems though as the premise on PCI-DSS holds true that it won’t do anything against dedicated attacks. I hope they realize this and begin to focus on the topic at hand. It doesn’t matter if you’re compliant, what matters is if you are actually secure.
Typos & misspellings drive me crazy…
“Indeed, given GPN’s statements thus far, I continue to be nagged by the possibility that my initial reporting may have been related to a separate, as-yet undisclosed breached at another processor.”
Brian,
To be honest, I did not realize you broke this story when I came to your website today. I just knew that I could count on you to explain the situation without over-simplifying or delving too deep into technical details without explaining.
Congratulations on the scoop and thanks for the ongoing informative readable coverage.
FWIW, GPN does not store track 1 or track 2 data so any capturing of cardholder information had to come from either the merchant’s site or while being transmitted to GPN. That severely limits the number of accounts compromised since it would be no more than the merchant’s transaction count. A likely detection scenario is that GPN’s monitoring of merchant activity beyond the actual transactions, such as atypical large downloads of activity logs. The logs don’t contain any card holder information and would be of little or no use to a hacker. On the other hand after a time this activity would have attracted the attention of Global, who in their follow-up would discover the merchant’s operation had been compromised. In actuality this is more or less what happened.
My gut feeling this is one merchant site that was compromised and in an effort to gather more information the culprits tipped their hand to GPN who then uncovered the problem. This is different from the perception that seems to be out there, that GPN’s servers were hacked and vast amounts of data downloaded. Reinforcing this gut feeling is the highly limited nature of the “hack”, basically one high volume merchant. If a hacker could get into a payment processor’s site and tap in to the data stream as it passes from the merchants to the card issuer (the only possible way to capture track data) they could and would gather transactions from everywhere.
Lastly the 1.5M figure is likely the merchant’s transaction count for the time their site was compromised. In retrospect Visa’s action may be looked upon as a hasty knee-jerk reaction as opposed to MC, or Amex, or Novus all of whom know more about this than any of us.
Its a good spin, but then GP would have come right out and said that their systems were not compromised and that it was one of their merchants that had a data breach. They are trying to do damage control right now and in this scenario they would pass the blame onto the merchant. Visa has the most clout in the payment industry, so I would assume they know more than anyone else as it sounds like GP does not have a clue. I would take GP press releases with a little caution as they are leaving a lot of information in the dark. Per contract requirements, they have to keep the payment networks (Visa, MC, etc) in the loop on their investigations.
I received a call from GPN, or rather, Mastercard security and fraud services saying my card was one of the compromised ones. He asked me if I had noticed any irregularities and then he asked me specifically if any PA pymnts were on that card and asked me who my cable supplier was. When I told him his response was “that’s exactly what I was looking for”. I gave him no account info despite his confirming his identity – nor did he ask for any.Makes me think the main source of the hack was the cable company…I live in Canada and my provider is Shaw Direct. Not sure if they are a US owned company or not..
The whole thing is making me leery and I am just one tiny little fish in the tank. What a mess. Now I have to go and change my payment plans and reset all my cc info. Crazy! I can’t imagine having to do this on a huge scale.
The NY Times, on Sunday reported hackers “gained access to” Track 1 and Track 2 data. Yet Global Payments is only saying Track 2 card data may have been stolen. I’m not reading Track 1 data mentioned in any of their releases.
I find the release of information by the company thus far itself circumspect at a minimum.
Visa’s demotion of Global Payments is a no lose proposition for Visa, it makes them appear concerned. But in reality, as Global Payments has said, they continue to process all credit card transactions normally. Which means there’s no meaningful effect by Visa’s actions.
If it turns out Global Payment or some other company has been continuously breached for even a few months, let alone 13 months, it calls into question the practices of the entire industry all the way to the top. It’s no secret the card brands and issuing banks consider it cheaper to deal with breaches even of this magnitude rather than improve the security of consumer cards.
Visa’s demotion of Global Payments is a financial gain for Visa. Global will now have to pay a higher per transaction fee to Visa because of the down grade, a fee they will not be able to pass along to their customers. If Visa were seriously concerned they would cut Global off.
Don’t forget the fines. Global will get fined, and there are no limits on the breach fine amounts.
Also, there is nothing stopping Global from passing on breach costs to customers. Obviously, they won’t call them “breach fees” or anything like that. After all, processors have been known to pass on the cost of PCI to merchants.
Basically, the consumer does not need to worry as they take it up with their Issuer who takes it up with Visa. Additionally, the Issuer will implement fraud rules preventing unauthorized transactions. Visa makes GP get their act together by raising their rates, as once you hurt someones wallet they will make things right. Additionally, merchants may leave GP as they too may be concerned about their data being compromised or being associated with a processor that has issues.
It’s not that Visa is trying to make money in a bad situation, its just their operation policy when GP signed up to be on their network. I am surprised the other networks have not done the same.
Disturbing trend found while using iron key
paypal did not like fact I was using a “proxy” and shut down my account
upon calling them they told me they reduced password complexity from
32 char to 20 char .. Huh… and will not allow me to use there service while
using my iron key though I explain I travel and use this as security ..
I have a paypal OTP and this did not matter to them.. WOW..
Similiar problem found while using iron key with craig’s list .
they prompted me to enter a real phone number. no VOIP etc.
basically they are requiring me to be tracked.. Same with paypal.
Not cool with this. Don’t post much but thought this was a thing worthy of alert.