Google plans today to begin warning Internet users if their computers show telltale signs of being infected with the DNSChanger Trojan. The company estimates that more than 500,000 systems remain infected with the malware, despite a looming deadline that threatens to quarantine the sick computers from the rest of the Internet.
Security experts won court approval last year to seize control of the infrastucture that powered the search-hijacking Trojan in a bid to help users clean up infections. But a court-imposed deadline to power down that infrastructure will sever Internet access for PCs that are not rid of the malware before July 9, 2012.
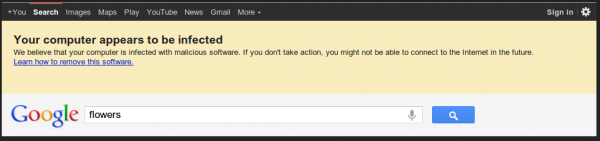
The company said the warning (pictured above) will appear only when a user with an infected system visits a Google search results property (google.com, google.co.uk, etc.), and will include the message, “Your computer appears to be infected.” Google security engineer Damian Menscher said the company expects to notify approximately a half-million users in the first week of the notices.
“In general we want to notify users [of malware infections] anytime we are capable of doing so, but the fact that we don’t do this more often is really just because it’s hard to come across cases where we can do it this accurately,” Menscher said. “In many cases we only have maybe a 90 percent confidence that someone is infected, and the false positive rate of 10 percent is simply too high to be feasible. But in this case we can be essentially certain that someone is infected.”
The warning that infected users will see is nearly identical to a similar alert Google used last year in a campaign to rid the Web of another search hijacker that was trying to frighten users into purchasing bogus antivirus software — also known as “scareware.”
DNSChanger may no longer be hijacking search results, but the malware still carries secondary threats and risks. It was frequently bundled with other nasty software, and consequently machines sickened with DNSChanger also probably host other malware infestations. Additionally, DNSChanger disables antivirus protection on host machines, further exposing them to online threats.
To address these concerns, Google is steering users of infected systems to a set of instructions that include steps to eradicate DNSChanger and to third-party cleanup tools that may help scrub infections from other malware.
Menscher said Google will be displaying the warning in dozens of different languages.
“We think part of it is that all of the public press on this so far has been in English or a handful of other languages,” Menscher said. “It turns out that only half of these infected users speak English as their primary language.”
DNSChanger modifies settings on a host PC that tell the computer how to find Web sites on the Internet, hijacking victims’ search results and preventing them from visiting security sites that might help detect and scrub the infections. The Internet servers that were used to control infected PCs were located in the United States, and in coordination with the arrest last November of the Estonian men thought to be responsible for operating the Trojan network, a New York district court ordered a private U.S. company to assume control over those servers.
The government argued that the arrangement would give ISPs and companies time to identify and scrub infected PCs, systems that would otherwise be disconnected from the Internet if the control servers were shut down. The court agreed, and ordered that the surrogate control servers remain in operation until March 8. When the March 8 deadline approached and cleanup was discovered to be taking longer than expected, the court agreed to extend the cutoff date to July 9, 2012.




Now, tell me wth update installed itself this morning. It isnt patch Tuesday.
Updates released 2012/5/22
http://www.microsoft.com/en-us/download/details.aspx?id=29869
http://www.microsoft.com/en-us/download/details.aspx?id=14668
Available in all operating system flavours.
This is good information for the masses. Generally we tell users that when you see such warnings it’s BS or Fake-AV. Now we’ll know that it’s expected behavior.
that warning looks like the kind of junk i’ve been telling people to ignore for years.
here’s my thing, google knows so much about us why nog make it a little more personal with something like, “hey, elliott, this is google. seriously, you’ve got some malware on your system and you’d better fix it soon. ” i dont know, i think people would respond to that.
“that warning looks like the kind of junk i’ve been telling people to ignore for years.”
Exactly what I’m thinking. For example it goes against the “don’t install anything you didn’t explicitly ask for” doctrine that Brian and various others espouse as basic security advice.
Not that I can really fault this course of action though I suppose … sigh.
like, i dunno, maybe this.. [http://goo.gl/Dbk4X] ?
“that warning looks like the kind of junk i’ve been telling people to ignore for years. ”
That’s my big problem with this too! Just like the “Don’t click on links in e-mails” security email reminders that then have links IN THE E-MAIL to more information. If they led to pages that said “You failed, don’t click on links in e-mails” I could over look it.
Instead, they keep saying, don’t follow links you didn’t ask for, but ours are kosher. Now people are going to think that those stupid “You may have been infected” pop-ups are going to be real. Because hey, they got it once from Google and it was real. *bangs head on desk*
Kreb’s broken record keeps playing over and over because people keep repeating the mistakes to help others.
Calling the user by a name… or claiming “this is REALLY google” proves something? That’s the same thing a virus can do.
I’m not wishing for this, but I bet another extension happens…
Anybody have the “Learn how to remove this software” link?
Well, it’s good that my computer (and my mom’s and my dad’s) is not infected with the DNS Changer trojan. 🙂
Undetected secondary infections are the reason I advised most people visiting the store I used to work at that the best option was to back up their data and re-format.
The other advantage of doing that is then it also gave me a chance to update their OS as well as other vulnerable softwares that were the likely source of the infection in the first place. (The virus remove service we offered didn’t allow for installing updates, and was more expensive than a recovery + backup)
prairie,
Sorry to disagree but that sounds like a terrible idea– any malware above basic script kiddie-level garbage will be backed up and then restored right back to that machine.
I prefer to destroy them where they are, then clean and patch the computer.
Depends on the backup you run. The Windows Vista backup for example refuses to backup any executable or script file types. The Windows 7 backup however might backup an executable if it isn’t referenced in the registry. I wrote a custom script to exclude any executable file types and known problem locations – like the temp files or browser caches.
Is it possible to backup malware doing that – yes – but I never had it happen once in over 300 recoverys I did while I was at that store.
> The Windows Vista backup for example refuses to backup any executable
Huh? How is that a “back up”???? It excludes 100s of exe files that you need?
It is a back up in that it backs up your data – your data should not be executable. The OS, applications, and drivers are best installed from the source or better yet – brought up to date. I would never allow an executable to be included in any backup I make. Too much risk and easier to get the latest version on the occasion of re-install.
It’s been a full day and no-one’s piped up yet to say that DNSSEC would have fixed this?
(Apologies for the trolling, I’ll go away now :-).
What an ideal situation to peddle scamware!
Everybody hears about this pending disaster on the news, does a search and comes up with a familiar looking site, such as Google, Microsoft, etc that redirects them to a ‘clean up’ website. Unfortunately, they pick one that isn’t kosher, and instead of mild malware, they get full blown badware.
Google must over-ride any SEO manipulation and have the government websites showing what to do listed first and foremost for the innocent victims.
Of course, anybody warning you have been infected is going to be ignored, regardless of the method (via email, a web browser screen, a popup, a telephone call) – we have emphasised that over many years as a scam, and now it will come back and bite us.
Would Obama on the television news be the correct level of seriousness to warn people? Would they take notice?
After all, it is international cyber-terrorism, and those affected are most likely not to notice until it is too late.
Can ISPs put in place a circumvention/cure that doesn’t rely on DNS to be able to push a fix when their customers finally do lose access? If so, it may be in their best interest to do so before the storm hits their hotlines.
So, maybe I missed this but how do I spot an infection without Google having to tell me?
Dan,
Browse here
http://dns-ok.us/
It will tell you if that machine you’re visiting with is infected.
Why not have television and newspaper stories tell people to type “dns-ok.us” in their browsers? Teaching them to type in a URL would be useful. Teaching them to follow the instructions in a pop-up window is not.
Already done
http://goo.gl/1qCix
Im still baffled, that so many parties care about the infected PCs.
Microsoft, the Government, Google ….
Its like:
“hey your drunk, but please keep driving, you need to get to work and stuff. We understand!”
most Users who are still infected, wont care about the google popup either.
as long as people can work on their PC, they dont really care what else is going on.
When the Internet goes away, thats a pretty good reason to send the PC to the much needed checkup.
Its simple and effective.
Haha, Christian. If I could give your comment 100 thumbs up, I would 🙂
It’s an absurdity by itself that Google cares to tell useres and Microsoft still isn’t able to popup a note on identified and infected Windows-PCs. (Instead they leave it to the FBI to inform national CERTs to inform national ISPs to identify IP & timestamp to inform users… :-()
This happened to me, a couple of years ago. Every time I googled something I was directed to another site-NOT google. It was so frustrating and I KNEW right away something wasn’t right..long story short..I kept GOOGLING to try and find an answer…my computer was finally totally wiped out because no one warned me or told me what to do….everyone I asked said they never heard of that happening….so I think it is a good idea..I use google all the time..
I think you should expand your circle of friends to include someone with some amount of technical ability. Google redirects have been all the rage for the better part of the last decade, it’s usually the first clue to normal users have that something has gone wrong.
The only reason this particular alert is going to work is because the system is effectively deactivated, if the botnet was in full force and still functioning the person controlling the client would quickly update it to not display Google’s message, assuming it was ever displayed at all.
I wonder what mechanism is used at the google site to detect whether the PC is infected.
Any suggestions?
The detection of infected PCs happens when the PC contacts the malware servers which are now under US law enforcement control. That may actually be worse than the malware itself.
But wait – isn’t the detection made when Google receives a query from an infected machine? Or does the malware force all queries to proxy though their servers? I don’t think that’s likely – they just do the dns lookup, I think.
So what in the query to google says that the machine is infected? Maybe the replacement servers give a special dns address for google, and so any requests to that address must have come from an infected machine.
Or is there something else I’m missing?
“Maybe the replacement servers give a special dns address for google, and so any requests to that address must have come from an infected machine.”
I’m sure that’s it. That’s how http://dns-ok.us/ works.
Just install Linux asito to your current OS and use Linux only for surfing the Internet