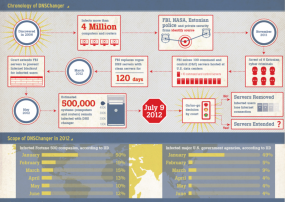
In about two weeks, hundreds of thousands of computer users are going to learn the hard way that failing to keep a clean machine comes with consequences. On July 9, 2012, any systems still infected with the DNSChanger Trojan will be summarily disconnected from the rest of the Internet, and the latest reports indicate this malware is still resident on systems at 12 percent of Fortune 500 companies, and roughly four percent of U.S. federal agencies.
In a bid to help users clean up infections, security experts won court approval last year to seize control of the infrastructure that powered the search-hijacking Trojan. But a court-imposed deadline to power down that infrastructure will sever Internet access for PCs that are not rid of the malware before July 9, 2012.
According to Internet Identity, 12 percent of all Fortune 500 companies and four percent of “major” U.S. federal agencies are still infected (a link to Internet Identity’s full infographic is here). The latest stats from the DNSChanger Working Group, an industry consortium working to eradicate the malware, more than 300,000 systems are still infected.
That number is likely conservative: The DCWG measures infections by Internet protocol (IP) addresses, not unique systems. Because many systems that are on the same local network often share the same IP address, the actual number of DNSChanger-infected machines is probably quite a bit higher than 300,000.
Google certainly seems to think the number is higher, possibly by as much as 30 percent higher. On May 22, Google said it would begin warning users if their computers show telltale signs of being infected with DNSChanger. The company estimated at the time that more than 500,000 systems remained infected with the malware. On that date, the DCWG was tracking infections tracing back to 333,908 IP addresses.
To find out if a system on your network is infected, visit the DNSChanger Check-Up page. Other resources for cleaning up DNSChanger infections are here.
DNSChanger may no longer be hijacking search results, but the malware still carries secondary threats and risks. It was frequently bundled with other nasty software, and consequently machines sickened with DNSChanger also probably host other malware infestations. Additionally, DNSChanger disables antivirus protection on host machines, further exposing them to online threats.
DNSChanger modifies settings on a host PC that tell the computer how to find Web sites on the Internet, hijacking victims’ search results and preventing them from visiting security sites that might help detect and scrub the infections. The Internet servers that were used to control infected PCs were located in the United States, and in coordination with the arrest last November of the Estonian men thought to be responsible for operating the Trojan network, a New York district court ordered a private U.S. company to assume control over those servers.
The government argued that the arrangement would give ISPs and companies time to identify and scrub infected PCs, systems that would otherwise be disconnected from the Internet if the control servers were shut down. The court agreed, and ordered that the surrogate control servers remain in operation until March 8. When the March 8 deadline approached and cleanup was discovered to be taking longer than expected, the court agreed to extend the cutoff date to July 9, 2012.




“disconnected from the rest of the Internet” – anyone know exactly what this means?
Victims will no longer be able to resolve domain names when the DNS Changer servers are taken down, so anything they access via a domain name (rather than an IP address) will no longer be accessible until DNS settings are properly restored.
It means they will probably be able to get to their ISP’s home page and email server but nowhere else.
“Because many systems that are on the same local network often share the same IP address, the actual number of DNSChanger-infected machines is probably quite a bit higher than 300,000”
While I don’t dispute that networks using NAT could result in undercounting of some victims, how can you be sure that this number is greater than the number of machines regularly connecting from multiple IP addresses? My work computer is a laptop, and I use it from both my home and office every day of the week, as well as at airports, coffee shops, hotels, VPNs, etc. Saying that the number of infected hosts may be higher or lower is wildly speculative.
Hrm. “Wildly speculative”? Did you read the next paragraph, or go straight to leaving a comment?
I offered an explanation for the guess there:
“That number is likely conservative: The DCWG measures infections by Internet protocol (IP) addresses, not unique systems. Because many systems that are on the same local network often share the same IP address, the actual number of DNSChanger-infected machines is probably quite a bit higher than 300,000.
Google certainly seems to think the number is higher, possibly by as much as 30 percent higher. On May 22, Google said it would begin warning users if their computers show telltale signs of being infected with DNSChanger. The company estimated at the time that more than 500,000 systems remain infected with the malware. On that date, the DCWG was tracking infections tracing back to 333,908 IP addresses.”
Ok, I’ll concede that it is only mildly speculative. And yes, I did read the following paragraph (and the rest of the article, which I otherwise enjoyed). My problem was that you deemed it probable, instead of merely possible, that the number of infections is higher than the figure from DCWG. The methodology of DCWG is pretty clear, although for the previously mentioned reasons, it isn’t a measure of the number of actual infections – just unique IPs. Without knowing Google’s methodology (and maybe you do…I admit I have no idea) I am not sure it is fair to conclude that the number is probably anything. I happen to disagree that it is probably higher, merely that it is possibly higher.
That’s quit a nit, Hector. Are you part of the DCWG by chance?
No, I’m not a part of DCWG (although I will disclose that I know a few folks who are). Then again, I wasn’t trying to say “DCWG RIGHT! BRIAN WRONG!!” I agree it is somewhat petty, this is just the sort of thing that gets under my skin.
According to Google, the main reason for the discrepancy is that DCWG is counting IPs, and Google is counting cookies. So they measure the number of households and businesses, and Google measures the number of affected devices.
@ Hector
While some of those infected computers are likely to be mobile units like yours, that change their IP address through the day as they move around, I suspect the overwhelming majority of the infected machines are dull and boring desktops doing dull and boring (but essential!) jobs in those Fortune 500 and Government offices. Those desktops are likely to be connected to the Internet via large local networks and NAT, hiding the true number of infected machines, as the article stated.
You are the exception, not the rule.
Oh Well! I guess that is all I got to say, besides, thanks to Brian for continued coverage of the problem. All of my clients tested clean so far.
Here’s UCLA’s eye chart:
http://security.ucla.edu/dnschanger/
I’m still not infected by the DNSChanger Trojan on our computers! Lucky! That means that we won’t be disconnected from the Internet on July 9. 🙂
Thanks Brian. Appreciate you keeping me and others updated.
Just pull the plug on the servers and be done with it. If they keep extending the deadline to pull the plug, infected PC’s will never be fixed as their users have no clue. Once they lose internet access they will contact their IT people and it will be taken care of, they should have shut the servers down in March as was planned and it would no longer be news.
I agree. Looking at the numbers in the Infographic, I think it’s clear that while there were dramatic drops in the number of infected individuals orginally, now it’s mostly tapered off which means (to me) that the easy ones have taken care of it and the rest won’t until it’s shut down. Time to shut it down, definitely.