Nearly four years after it burst onto the malware scene, the notorious Grum spam botnet has been disconnected from the Internet. Grum has consistently been among the top three biggest spewers of junk email, a crime machine capable of blasting 18 billion messages per day and responsible for sending about one-third of all spam.
The takedown, while long overdue, is another welcome example of what the security industry can accomplish cooperatively and without the aid of law enforcement officials. Early press coverage of this event erroneously attributed part of the takedown to Dutch authorities, but police in the Netherlands said they were not involved in this industry-led effort.
The Grum ambush began in earnest several weeks ago at the beginning of July, following an analysis published by security firm FireEye, a Milpitas, Calif. based company that has played a big role in previous botnet takedowns, including Mega-D/Ozdok, Rustock, Srizbi.
Atif Mushtaq, senior staff scientist at FireEye, said the company had some initial success in notifying ISPs that were hosting control networks for Grum: The Dutch ISP Ecatel responded favorably, yanking the plug on two control servers. But Mushtaq said the ISPs where Grum hosted its other control servers — networks in Russia and Panama — proved harder to convince.
“I sent the Russian CERT [computer emergency response team] abuse notices about these command and control networks on Russian ISPs and they sent us a one-liner email saying ‘These are not our IPs,” Mushtaq said, referring to the Internet addresses of the Grum control servers that were operating on Russian ISPs. But FireEye found success in appealing to the Russian ISP’s upstream Internet provider, which severed its connection to some 256 Internet addresses in the area of the Russian Grum controllers.
The Panamanian hosting firms followed suit, but the takedown effort suffered a temporary setback when the Grum botmaster(s) set up backup control networks at ISPs in Ukraine. But they, too, were soon disabled, leaving the infected Grum bots without any control networks telling them what to do.
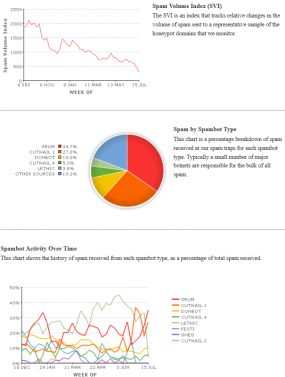
“According to data coming from Spamhaus, on average, they used to see around 120,000 Grum IP addresses sending spam each day, but after the takedown, this number has reduced to 21,505,” Mushtaq wrote in a follow-up blog post. “I hope that once the spam templates expire, the rest of the spam with fade away as well.”
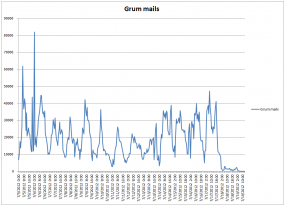
And fade away it has, at least according to data recorded by Symantec’s MessageLabs (see graphic at the top of this post).
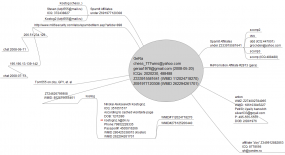
It remains unclear whether the individual(s) responsible for Grum will ever be brought to justice. Grum has long been associated with spam promoting rogue Internet pharmacies, and in February, I published a lengthy analysis of data leaked from two of the largest pharmacy spam affiliate programs showing the earnings and possible identity information of the Grum botmaster. That analysis tied Grum’s activities and profits back to a hacker who used the nickname “Gera,” and whose payment accounts were linked to a Russian named Nikolai Alekseevich Kostogryz (see graphic below for more details on Gera).
At that time, Grum was the world’s most active spam botnet, according to statistics maintained by M86 Security Labs, a company since acquired by Trustwave. Very soon after my investigative piece on Grum was published, KrebsOnSecurity.com was the target of a rather large distributed denial of service (DDoS) attack. I’ve recently learned that the attack was launched by the Grum botnet, suggesting that the findings were a little too close to home for the Grum botmaster(s).
Brett Stone-Gross, a senior security researcher for Atlanta-based Dell SecureWorks, analyzed a copy of the Grum malware from that time and found that it was instructing all infected systems to visit 94.228.133.163 (the IP address for krebsonsecurity.com). The nonexistent filename that the Grum bots were told to fetch from my site was “fuckingyou^^/9590899.php”.




Nice update. I have a few questions:
1) Why was FireEye working against the botnet? Were they just trying to show off some “skillz” to drum up new business? If so, good for them, I hope they get a ton of traffic for this. But if not a clever marketing scheme, what’s the motive here?
2) “I hope that once the spam templates expire, the rest of the spam with fade away as well.” This quote had me a little curious. Do the spam bots have instructions that eventually expire, or will they likely continue to attempt the last instructions given to them by the botmasters?
3) Why can’t people be more imaginative? “fuckingyou^^/9590899.php” Really?
>> Why was FireEye working against the botnet?
Can’t nerds just do nerd things once in a while? You know they didn’t enter this line of business by accident.
>> But if not a clever marketing scheme, what’s the motive here?
I’m not speaking for the company in question but seeing as they’re a computer security firm they probably see it as their business to disrupt criminal operations which neatly dovetails with getting their name out there (ie. marketing).
I don’t really see the point of your question. Another way they could have made people aware of their brand is purchasing ad space so you have to look at it but it’s so much more legitimate when it’s done this way.
>> Do the spam bots have instructions that eventually expire
Once again an assumption on my part but I imagine all spam campaigns have expiry dates not least because the bot net may have been rented out to other spammers.
Guess the tables got turned after the DDoS hassles, and good riddance! Kudos to FireEye and everyone involved in taking this spambot out of commission, and thanks to Brian, as always…
KUDOS, Brian, on your accomplished reporting..!!
Question: I notice the take down occurred on or about 02:00, on 07/18/12, only a day and a half ago…
How much trouble will it be for a new C&C network to be setup, maybe in China say, or some other, uhhh, ‘neutral’ country??
I was wondering the same thing.
In addition, why can’t industry do this will all of the bot nets? The way Mushtaq’s blog read, it made it seem “easy.” They just call up contacts/put pressure on ISP’s and boom, no more spam.
I realize this as always been very difficult, but the blog and the article don’t really convey how hard it may have been to accomplish this feat.
I think they are trying to do this one by one, but it takes some amount of legwork (identifying all of the CnC servers, then identifying all of the ISPs, finding the contact information for all of the ISPs, and finally trying to get them all to take down simultaneously.
The problem is that if you miss one CnC server, the owner of the botnet can quickly try and set up some others, and push out an update. You really have to take them all down simultaneously so that infected machines have no location from which to download an update.
Leaving those spambots ready for recovery ‘again’ and their masters at large makes me a little… let’s say… grumpy:
Threat aliases for Backdoor/W32.Bredolab.72192:
:
Dropper.Grum.A
:
TrojanDropper:Win32/Grum.A [Microsoft]
TrojanDropper.Grum.a [CAT-QuickHeal]
:
Backdoor/W32.Bredolab.72192 [nProtect]
Backdoor.Win32.Bredolab.oxw [Kaspersky]
Backdoor.Win32.S.Bredolab.72192 [ViRobot]
“Very soon after my investigative piece on Grum was published, KrebsOnSecurity.com was the target of a rather large distributed denial of service (DDoS) attack.” Suffering the wrath of the Internet’s Lord Voldemorts is a badge of honor, a sign of a job well done and for that society should thank you. As for the future, the next Emperor of Darkness will hit you with a DDoS. When that happens, rest assured that your readers do understand the situation and will return eager to learn the details of your latest battle.
“Brett Stone-Gross, a senior security researcher for Atlanta-based Dell SecureWorks, analyzed a copy of the Grum malware from that time and found that it was instructing all infected systems to visit 94.228.133.163 (the IP address for krebsonsecurity.com). The nonexistent filename that the Grum bots were told to fetch from my site was “fuckingyou^^/9590899.php”
9590899@gmail.com lol i config it’s ,
us have grum projects and grum aff rx lol , grum not new but nerver die!
Too much tramadol, uh? Read adverse effects next time… 😀
Apparently, he’s suffered a bit of “nerver” damage.
simple for big botnet via PPI
soon grum come back in topten www spam
if you want grum code and projects email to me
Sry, stupid, but the truth is grum didn’t even touch top10. That’s the reason why just message labs and bot-hunters noticed grum bombing their spamtraps… The rest of the world didn’t even recognize it has been around ’cause of blocklists – and you know that. LOL
9590899@gmail.com
grum coder and botmaster support!
Yes, here, /me, plz:
Why did thousands of unnoticed bots flood Shadowserver Foundation’s dropzones simultaneously to the grum takedown? ❓
Hello, lol,
We know what Krebs and FireEye’s motivations are about Grum, but what is your motivation? You obviously have issues with the Grum people, right? You seem gleeful.
Well issues with, or are involved with.
or just “issues”
Wouldn’t the botnet master have a record of all the bot’s IP addresses and be able to send an update later?
The zombie PCs may be behind firewalls, NAT routers, etc. or their ISP policies may prevent outsiders from connecting to the server. The botmaster will have to re-infect the computers. He probably has backdoors to do so (e.g. an old version of Java or Flash that is used only some of the time and is not updated).
d:\Work\Malware\Gera-projects\Spam-bots\
lol gera and funny
so, if i’m reading this right, russia’s CERT disavowed any knowledge of their own IP addresses? that kind of anomalous behaviour seems like something worth looking into.
I’m getting plenty of viagra spam, still.
I have proof that the people that are sending out this spam are making it look like some of it is coming from my SecureMecca.com domain. I know that they are doing it to another domain for certain and suspect they are doing it to many other domains as well. Here is my blog on it with links to the proof that is coming in with maybe a momentary lull but no end in sight:
http://securemecca.blogspot.com/2012/06/why-i-block-spam.html
They intend to keep it going forever. This is where the PeskySpammer link in the blog goes to:
http://securemecca.com/public/PeskySpammer/
This is not pointing to static data. It is ongoing and changes at least weekly. I just got a list of another 100+ hosts selling drugs that can potentially kill you or disable you for life from bounces in my email during the past 12 hours. Most of the hosts are in the Russian domain and for now are hosted in China. Do not rush to a judgement that the people doing it are in those countries. The criminals may live in the United States or Europe. I do add blocks of their hosts in my hosts file and rules in my PAC filter which feeds into some of the information stored in the PeskySpammer folder.
I would not be surprised to hear that the drugs these people are selling kill or disable people for life. When the people selling them hear that what they sold killed or disabled a person for life they would probably laugh. They are not just being nerds. They are evil criminals that don’t care who they harm.
I forgot to add one thing. I stabilized on one file that indicates that the PeskySpammer.7z contents have changed. It is called SpamOfTheDay.txt. I take it this one lone negative vote against what I have written is from the people that are doing this that also tried to give me an anonymous phone call yesterday (2012-07-24) that I did not take. But if spammers don’t want me blocking their hosts the solution is simple – just grep out hhhobbit, henryhertzhobbit, and securemecca out of their spam sending lists.
It could be because you don’t understand how spam works (and to be fair, most people do not). This is/was hardly the only spam botnet, and comments like this will probably just rile people on (for the record, I am a security professional). Good luck to you.
Thanks
I removed the blog entry.
Krebs,
Do you know that the RSS feed to your website is not working. It hasn’t been for a couple of days. I assumed that maybe the feed link was changed but that doesn’t appear to be the case. clicking on https://krebsonsecurity.com/feed/
just sends the browser in to a constant connect, reconnect loop.
Try now.
First of all , I’d like to thank the author of this website for doing such a great job. When I read it for the first time a few years ago, I couldn’t believe it. So I started doing my own research and I was amazed how incredibly easy available atm skimmers or their parts are on the internet. Then I thought: Obviously its possible to build a skimmer at home . But can someone actually come up with some sort of antiskimming device that would be simple , cheap to produce and would be EFFECTIVE at the same time ? I’ve read there are several good antiskimming technologies that work to some extend , but not always. Plastic antiskimmers that supposed to make it harder for crooks to install a skimming device , actually make it easier. Every time a new antiskimmer comes out , you can see skimmers that look identical to those antiskimmers. Moreover, they buy an antiskimmer and rebuild it making it a skimming device. Then of F2Fasic delta microchips and software that is made specifically to target interrupted swiping , thieves are still able to beat it. Another way is “scale” that is weighing fascia around a card reader on ATM . Supposively , if any foreign device is attached it should alarm the authorities. Well , usually crooks attach a nail or something heavy during the night hours and watch if the location is being checked up by the police. Plus with all those mini and nano skimmers that literally weigh 5-10 grams “scales” isn’t that effective. The best antiskimming technology IMO is a lazer scanner that looks like a camera and it scans the fascia around reader and other parts of ATM.if any foreign body is attached , the lazer that constantly scans the facia , alarms the authorities with a silent alarm .
To be honest this is a very interesting subject and since I read it for the first time , I’ve been on the mission to build an antiskimming device. I have a few good ideas. Maybe if Im successful , I’ll be able to share it with you in the near future .
Sincerely , John ADAMS