“When nobody hates you, nobody knows you’re alive.” – Diplomacy, by Chris Smither
During the last week of July, a series of steadily escalating cyber attacks directed at my Web site and hosting provider prevented many readers from being able to reach the site or read the content via RSS. Sorry about that. What follows is a post-mortem on those digital sieges, which featured a mix of new and old-but-effective attack methods.
I still don’t know who was attacking my site or why. It’s not as if the perpetrator(s) sent a love letter along with the traffic flood. There was one indication that a story I published just hours before the attacks began — about a service for mass-registering domain names used for malware, spam and other dodgy business — may have struck a nerve: In one of the attacks, all of the assailing systems were instructed to load that particular story many times per second.
Oddly enough, the activity began just one day after I’d signed up with Prolexic. The Hollywood, Fla. based company helps businesses fend off distributed denial of service (DDoS) attacks, assaults in which miscreants knock targeted sites offline by flooding them with garbage traffic. Prolexic was among several anti-DDoS companies that offered to help earlier this year, when KrebsOnSecurity.com came under a separate spate of debilitating attacks.
The first DDoS campaigns consisted of several hundred systems repeatedly requesting image-heavy pages on my site. Prolexic’s analysts say the traffic signatures of these attacks matched that of a family of kits sold in the underground that allow anyone to quickly create their own botnet specifically for launching DDoS attacks. Both are believed to have been created by the same individual(s) behind the Dirt Jumper DDoS toolkit. The traffic signatures from the attack strongly suggest the involvement of two Dirt Jumper progeny: Di-BoTNet and Pandora.
Pandora is the latest in the Dirt Jumper family, and features four different attack methods. According to Prolexic, the one used against KrebsOnSecurity.com was Attack Type 4, a.k.a “Max Flood”; this method carries a fairly unique signature of issuing POST requests against a server that are over a million bytes in length.
Pandora’s creators boast that it only takes 10 PCs infected with the DDoS bot to bring down small sites, and about 30 bots to put down a mid-sized site that lacks protection against DDoS attacks. They claim 1,000 Pandora bots are enough to bring Russian search engine giant yandex.ru to a crawl, but that strikes me as a bit of salesmanship and exaggeration. Prolexic said more than 1,500 Pandora-infected bots were used in the assault on my site.
The third sortie was by far the largest, and employed a very effective method known as a DNS reflection attack. In such attacks, the perpetrators are able to leverage unmanaged DNS servers on the Web to create huge traffic floods.
Typically, DNS servers only provide services to machines within a trusted domain. But DNS reflection attacks rely on consumer and business routers equipped with DNS servers that are (mis)configured to accept queries from anywhere on the Web. Attackers can send spoofed DNS queries to these so-called “open recursive” DNS servers, forging the request so that it appears to come from the target’s network. That way, when the DNS servers respond, they reply to the spoofed (target) address. Indeed, I used this tool to check dozens of Internet addresses that were seen sending my site replies to spoofed DNS lookups, and all were home to open recursive DNS servers.
The bad guys also can craft DNS queries so that the responses are much bigger than the requests; they do this by taking advantage of an extension to the DNS protocol that enables large DNS messages. For example, an attacker could compose a DNS request of less than 100 bytes, prompting a response that is 60-70 times as large. This “amplification” effect is especially pronounced if the perpetrators query dozens of DNS servers with these spoofed requests simultaneously. And this is exactly the approach they used with the DNS attacks on my site.
The DDoS problem overall is not going away and seems to be worsening. As illustrated above, it’s never been easier to build your own DDoS bot army. The Pandora/Dirt Jumper bot toolkits are designed to allow miscreants to quickly conscript attackers and then dissolve the attacking army. And a proliferation of consumer-grade and SOHO routers deployed by ISPs that are unmanaged all but ensures the raw firepower for reflected DNS attacks will remain a nuisance for some time.
According to a recent report by Arbor Networks, DDoS attacks have grown 82% since June 2011. “The general availability of botnets and DDoS tools has led to larger, more frequent and more complex attacks,” the report notes. “Multi-vector attacks can take sites and services down, and keep them down, for longer periods.”





Glad you are back Brian.
DNS amplification attacks have been made much more powerful thanks to DNSSEC adopters. In short, you spoof the victim’s IP address in a ~40-byte query, and the DNSSEC server sends a ~3KB response to the victim. Leveraged by a botnet, such an amplification factor is brutal.
http://dnscurve.org/amplification.html
I was looking forward to this article, very interesting. One question I have – is there a way to tell if your router has an unmanaged DNS server?
If you use the tool mentioned by Brian with your own ip.
cool thanks! Didn’t realize that.
it’s just begining…..
Are you people mentally ill or just stupid? Do you not understand Brian actually ‘enjoys’ the added attention of the attacks. Hell, you are not only boosting his ego, but you are giving him something to write about for a new blog post. Not to mention it proves he is doing something right if it pissed off childish fools like yourselves?
I might add my grandmother could pull more than 2 GBps in DDos with 2 dedicated boxes and she is half blind, what kind of pussies are you guys? If you are going to be foolish enough to attack at least do it right and use 10x the BW.
… you might want to run off and investigate how DDoS attacks are pulled off Particuarly the “distributed” part LOL
Oh once again neej you seem to be a very confused soul… Hopefully you are intelligent get lost but I sense you aren’t that smart.
Just because Distributed is in the name means nothing. I’ll explain so people like you that don’t grasp much hopefully won’t make a fool of themselves a third time. Or maybe you are going for three times in a row?
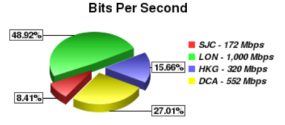
My comment is in relation to the total power behind the DDoS attack as listed in the chart at the top of the article. The Attack barely touched over 2 GBps. However, Brian seems to be on the lucky end because the people upset at him don’t have much of a backbone and had to use many hosts to reach these speeds.
Where-as it wouldn’t be difficult for certain parties to hit just as hard with no more than two un-metered GB lines. Now lets imagine if said people actually got annoyed at someone they of course wouldn’t use only two GB boxes. It is simply a statement as to how pitiful this attack was that it could be overpowered with a meager 2 hosts.
Back to my original comment, the attack on Brain is as one might say “weak sauce”, “pussy shit” because they had to use so many hosts to muster enough BW to reach the recorded high.
I’m fairly certain Brian has been on the receiving end of far more powerful attacks in the past. Let me put it into a metaphor for you, maybe that will be easier on your tiny brain to comprehend.
The current people that think they are proving a point might as well as be throwing sticks at a cement wall. If they really meant business they should get a bulldozer and at least make a fair effort to do some damage.
It’s cute how you keep associating courage and manhood with the amount of traffic someone sends in an DoS attack. I normally associate those things with doing something other than sitting in front of a computer and launching attacks on websites but each to their own 😉
Also cute is how you said:
>>I might add my grandmother could pull more than 2 GBps in DDos with 2 dedicated boxes
And then you said:
>>Now lets imagine if said people actually got annoyed at someone they of course wouldn’t use only two GB boxes.
banned.
Oh. I guess that pretty much makes the comparison worthless if you wouldn’t do that then. Makes sense.
neej, you really should take a few English classes. I’ll try to spell it out even slower for you. I’ve basically called the perpetrators behind the attack fools. They are not accomplishing anything (hence sticks @ cement). Not only have I associated their work with being a “pussy” at least where I come from that means the opposite of courageous. Generally people of this type like to hide behind others and think highly of themselves but don’t grasp the reality that they are really chicken shit.
So no I would not tend to associate such people with manhood or courage by any stretch of the imagination. I didn’t think I had to spell this out for you… Should I go one word per line or something for you to understand?
Now as to this comment of yours, do you even understand English? As I said I “my grandmother could pull more…” means they aint got shit. Then the other comment “if said people got annoyed…” I am talking about the kind of people you should be afraid of because they wouldn’t go after your site, they would drop your upstream provider. These of course should not be compared to the childish acts that have been performed as of late against Brian.
And no personally I feel DDoS is beneath me as it should be with most people that have dignity. So of course I wouldn’t go around attacking people. How does this make a comparison worthless? Do you even comprehend the words coming out of your mouth?
Funny, you can use proxies to block comments you don’t like neej. Are you sure you aren’t related to the people behind the Attacks on the site? You sure seem to be about as intelligent as they are.
As I said before
————————————————————————-
you really should take a few English classes. I’ll try to spell it out even slower for you. I’ve basically called the perpetrators behind the attack fools. They are not accomplishing anything (hence sticks @ cement). Not only have I associated their work with being a “pussy” at least where I come from that means the opposite of courageous. Generally people of this type like to hide behind others and think highly of themselves but don’t grasp the reality that they are really chicken shit.
So no I would not tend to associate such people with manhood or courage by any stretch of the imagination. I didn’t think I had to spell this out for you… Should I go one word per line or something for you to understand?
Now as to this comment of yours, do you even understand English? As I said I “my grandmother could pull more…” means they aint got shit. Then the other comment “if said people got annoyed…” I am talking about the kind of people you should be afraid of because they wouldn’t go after your site, they would drop your upstream provider. These of course should not be compared to the childish acts that have been performed as of late against Brian.
And no personally I feel DDoS is beneath me as it should be with most people that have dignity. So of course I wouldn’t go around attacking people. How does this make a comparison worthless? Do you even comprehend the words coming out of your mouth?
————————————————————————-
I see you like talking to yourself and rambling all over the place as well as making lulzy statements. You’re hilarious.
@Brian:
Checked those few IPs – most are only listed at abuse.rfc-ignorant.org. – Maybe that’s a way to go… (or just start a “my-little-pissed-off-childish-friends-RBL”) ;-))
Btw: Someone else seeing correlations between a remarkable drop in russian botnet activities and London 2012 Olympics?
At the very least you know someone is reading your column.
Q: How does the external service claim to mitigate the effects of DDOS on your site?
At its most basic, the approach is to look at the apparently abnormal traffic and see if it matches pre-set rules that have been seen in previous DDoS attacks. If not, it’s time to create some strict traffic rules that let you filter or drop any incoming packets that trigger on all of those flags.
Sorry to hear about your recent misfortunes, Brian, but I do see that you’re making hay with them, and that’s not bad at all.
And thanks for sharing a strategy to deal with DDOS attacks. If you can drop incoming packets by filtering on data in the packets and you know some bits of data that they all have, that would probably work. Key of course would be identifying the data to filter on, but I imagine that could be done with packet analysis of the DDOS packets already received.
My domain is so dinky and dedicated to private use that I don’t really have to worry about being DDOS’d now. But I’ve wondered how I would deal with the problem if I ever make a big enough ass of myself on the internet that someone would want to. So thanks for the tip!
And I do hope the strategy works for you in the future.
😉
Brian,
1.What are the preset rules?
2. Is there a way to shunt duplicate messages to the side?
3. It would appear that most of these DDos are coming from offshore accounts, Is there a way to treat them as foreign visitors requiring proper IDs, both from their sending site and recognition from the receiving site?
Didn’t even notice the site was being attacked 🙂 … but congratulations – obviously you’ve either pissed off or materially damaged some criminals.
Must be nice to get the positive feedback, please continue in the current vein 😀
Maybe I’m misunderstanding, but wouldn’t one key way to mitigate this be to restrict inbound DNS traffic from your trusted upstream provider? Or is the intent just to flood your firewall as it tries to drop them all?
I guess the attacks are a backhanded compliment. So glad you are standing up.
I like how you deleted my comment. All you want is attention. You don’t deserve any credit over this. Its not like HackForums is a super secret underground site. Nobody there cares if you’re a reporter or an FBI agent and I could care less either. A majority of HackForums is a bunch of teenagers who do nothing all day. All I do is remove malware. I could care less, my issue is personal information. You have no business posting it publicly, I don’t care reporter or not.
– Tha Sneak (6-year Computer Security veteran)
Nobody deleted your comment. And posting personal information? I posted what was in the WHOIS for that domain name. WHOIS is public information.
the point in not to destroy this beautiful website ( gold mind for a web criminals ) but to make Brain waist his time i think .. as u can see its getting more and more personal .first it was Email flood now its D-dos attack very soon every article in this blog will be about Brian and his struggle to defeat the world .)
continued:
4. Could you establish and require a password system.
With your permission, I would like to send you a proposal I authored a while back.
Why would I want to do that? What’s the point?
I’m sorry, I guess I always look for simple solutions, Too I thank you for all information. It has caused to spend some considerable time and research looking for a solution to the password difficulies.
9/23
The Analogy is simple: When one enters or leaves a foreign country you need certain formal documents,
A. -Passport, up to date with the following information;
B. -Your photograph
C. -Country of origin,
D. -Place last visited
E. -Record of inoculations,
F. -Purpose of visit, etc.
If paperwork is in order you are allowed to proceed. Your papers are stamped, given a formal recorded number and in many places a photographic record is made. If not, you are shuttled aside until closer inspection can be made or you are refused entry.
In the event of unexpected numbers additional resource are brought to bear. (DOS)
How can we compare this to incoming Internet traffic?
A -Passport,
Incoming: Internet Border Control should have one job, a single mandate at all its various locations, to inspect incoming traffic all hours, all days! If an unexpected large number requesting entry appear (DOS), first you bring up system reserve forces to bear, if still overwhelmed, you turn your attention to those with current documents, active certificate and or a history of activity, and site “White Paper” listings, these are moved to front; those without proper ID papers are shuttled aside or denied until traffic thins.
B –Company Certificate* and Country of origin,
Obviously, known trouble areas are given more through screening, particularly when routed through multiple sites (Records of Routing)
C -Record of inoculations,
Malware, Virus Products used; date last run; Certification granted with verifiable dated serial #
D -Country last visited, or origination
Out of country should receive a visitor tag and record of size of file incoming and out-going / Permit expiration
E -Purpose of visit, etc.
Business, Banking, Research,
F -Security Dogs (SNIFFERS)
Continually updated to detect malware, Trojans, Zeus etc. and all their various families as they are identified
G -White Paper Listings*
Continually updated list of account names that company does business with.
I.E.
Aberdeen Components Int’l
Contact Person:
Company ID/ Recorded Certificate Number / Your Assigned File #
Street Address / POB
City, State, Country Zip Code –ID code
Business Bank – ID # Persons to contact
Envoy Status
Why people always like to compare the computer stuff with real world stuff?