Researchers in Norway have uncovered evidence of a vast Middle Eastern espionage network that for the past year has deployed malicious software to spy on Israeli and Palestinian targets.
The discovery, by Oslo-based antivirus and security firm Norman ASA, is the latest in a series of revelations involving digital surveillance activity of unknown origin that appears designed to gather intelligence from specific targets in the Middle East.
 Norman’s experts say the true extent of the spy network came into focus after news of a cyber attack in late October 2012 that caused Israeli authorities to shut down Internet access for its police force. According to press reports, that incursion was spearheaded by a booby-trapped email that was made to look as if it was sent by Benny Gantz, the chief of general staff of the Israel Defense Forces.
Norman’s experts say the true extent of the spy network came into focus after news of a cyber attack in late October 2012 that caused Israeli authorities to shut down Internet access for its police force. According to press reports, that incursion was spearheaded by a booby-trapped email that was made to look as if it was sent by Benny Gantz, the chief of general staff of the Israel Defense Forces.
Security vendor Trend Micro suggested that the initial target of that attack were systems within the Israeli Customs agency, and said the malware deployed was a version of Xtreme RAT, a Remote Access Trojan that can be used to steal information and receive commands from a remote attacker. According to Trend, the latest iterations of Xtreme Rat have Windows 8 compatibility, improved Chrome and Firefox password grabbing, and improved audio and desktop capture capabilities features.
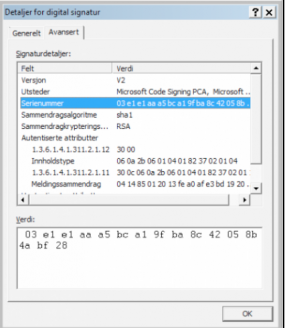
All of the malware files Fagerland discovered as part of this campaign were signed with this phony Microsoft certificate.
Snorre Fagerland, a senior virus researcher at Norman, said he examined a sample of the Trojan used to deploy the malware in that attack, and found that it included a rather telltale trait: It was signed with a digital certificate that was spoofed to appear as though it had been digitally signed by Microsoft.
The faked digital certificate would not stand up to validation by Windows— or anyone who cared to verify it with the trusted root certificates shipped with Windows PCs. But it proved to be a convenient marker for Fagerland, who’s been scouring malware databases for other samples that used the same phony certificate ever since. So far, he’s mapped out an expanding network of malware and control servers that have been used in dozens of targeted email attacks (see graphic below).
“These malwares are set up to use the same framework, talk to same control servers, and have same spoofed digital certificate,” Fagerland said in an interview with KrebsOnSecurity. “In my view, they are same attackers.”
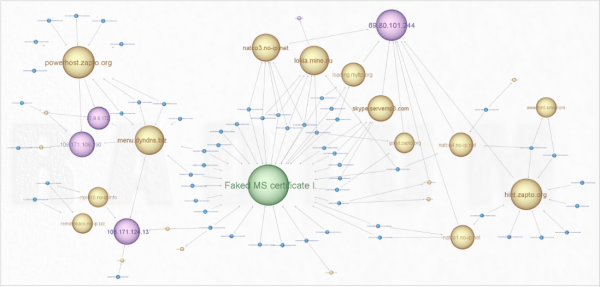
Fagerland discovered a vast network of command and control servers (yellow) that all bore the same forged Microsoft certificate and powered malware that targeted Israeli and Palestinian users.
Fagerland found that the oldest of the malicious files bearing the forged Microsoft certificate were created back in October 2011, and that the Arabic language email lures used in tandem with those samples highlighted Palestinian news issues. He observed that the attackers used dynamic DNS providers to periodically shift the Internet addresses of their control networks, but that those addresses nearly always traced back to networks in Gaza assigned to a hosting provider in Ramallah in the West Bank.
After about eight months of this activity, the focus of the malware operation pivoted to attacking Israeli targets, Fagerland discovered. When that happened, the attackers shifted the location of their control servers to networks in the United States.

An image and text taken from one of the booby-trapped bait files included in email malware attacks against Israeli targets.
Until recently, much of the discussion about espionage attacks has centered around activity thought to emanate from state-sponsored hacking groups within China. But espionage campaigns such as this one highlight activity from a growing movement of apparently independent hacker groups that may not enjoy state backing but which nevertheless can be effective at gathering useful intelligence and surveillance.
While Chinese espionage attackers use many of the same tactics and techniques (a heavy reliance on dynamic DNS providers and targeted, contextual email lures), these actors tend to use locally-made malware and homegrown lures (although they’ve shown a remarkable fondness for the freely available Poison Ivy RAT), Fagerland said.
“When it comes to the Middle East hackers, they have obviously expended less effort in making their own stuff, and tend to rely on off-the-shelf tools, such as Blackshades, XtremeRAT and Dark Comet,” he said. Indeed, researchers have documented numerous examples of these commercial tools being used in espionage attacks against activists in other countries of the region, most notably Syria.
Fagerland declined to speculate about who might be responsible for the attacks, suggesting only that it was “an entity with intelligence needs against both Israelis and Palestinians.”
“But I think it’s almost unheard of in a cyberwar context that two parties involved in a conflict get spied on by the same entity,” he said.
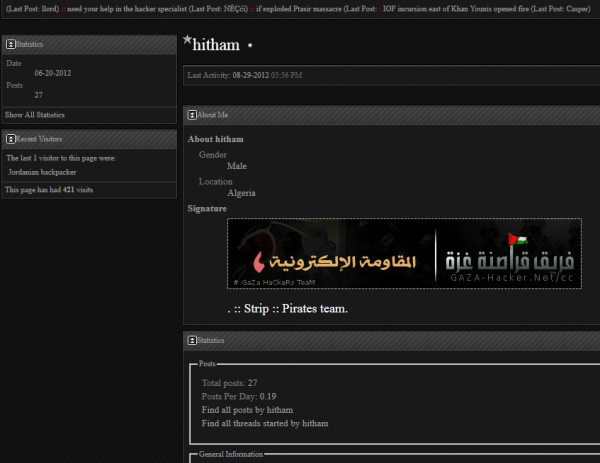
Fagerland noted that the attackers failed to scrub the metadata included in most of the email bait files. Those files, mostly booby-trapped Microsof Word documents, appear to have been created and saved by handful of users, including “Hitham,” “Tohan,” Aert,” and “Ayman.” I spent a short while searching hacker forums popular in the Middle East, and found several accounts matching those nicknames at a forum called Gaza-Hacker.net. The profiles of both Hitham (pictured below) and Aert suggest they are young men from Algeria. Hitham’s signature suggests he is a member of a group calling itself the Gaza Hackers Team, which claimed responsibility for defacing Israeli government sites earlier this year with messages calling for “Death to Israel.”




Full report from Norman is now available: http://download01.norman.no/whitepapers/Cyberattack_against_Israeli_and_Palestinian_targets.pdf
Brian,
This is off topic, but you might want to suggest to your advertisers that they do not use Flash in their ads. I, like many of your readers, use a Flash blocker. Or we’ve removed Flash entirely from our machines.
On this page I see two ad boxes with the grayed out Flash button.
What can we say? You taught us well! 🙂
I understand why you would block Flash outright, but I don’t think you have much to fear from my site, which is entirely ad-supported and, yes, employs Flash for some of the ads.
To put your mind at ease, I personally review all of the Flash ad creatives – a small number — that run on my site, and can assure you that it is not possible for advertisers to run rogue creatives on my blog.
As a developer;
So you actually de-compile every flash ad and read the source code?
Otherwise; what is to stop “me” from a benign looking ad that has a simple date and/or ip range based trigger (let alone a complex trigger) that actually just redirects to a different payload on a different server? (i.e. a simple navigateToURL(request, “_self”); will get your browser to run my page)
– Nathan
Nathan, do I decompile the Flash code? No. But the total number of unique Flash creatives that have run on my blog in the past six months is barely in the double digits. Not many other sites can say that. And the reason is that I’m sensitive to this issue. But I’ve been around this industry long enough to know that some people will not allow Flash on sites no matter what, and no amount of my trying to convince them it’s safe to make exceptions will matter.
Brian,
I’ve been reading your stuff since way back at the Washington Post, I realize you have been around for a while. 🙂 And I hope you will be around for a long while longer. 🙂 I find your stuff informative in other aspects of security that I don’t deal in and you do an excellent job of doing in-depth coverage which is rare in this industry. I enjoy reading every piece you produce. (I have you in my RSS feed)
However, in this case I think the original poster had a excellent post. “We” disable flash for a reason, and in your specific case you are playing with fire with gasoline nearby. 🙂
If I (as a bad guy) wanted to cause you lots of harm —
I would pay to put a very benign NORMAL image ad on your site for something very legit; upgrade to a benign flash ad on your site a month or so later month, replace it with another benign flash ad a month later, and then on either the third of forth flash ad replacement (when you would be a lot more lax) — replace it with a “date” and “software version” triggered ad that would redirect some users to a site containing kits under my control.. It would even be a reasonably smart trigger; and even have browser version and flash version detection and only redirect those users with which I have a known working vulnerability… So even if you pre-screened it, you by default of the “date” code would not see it. And more than likely because you are (I assume) pretty religious about updates; never see it because you would always be running the latest versions of things… And if you didn’t detect it this month — I would continue to run newer versions of the ad. 🙂 The longer I allow you to shoot yourself; the happier I would be. Then at some point in the future if you never did discover it — I would leak the information to someplace that would make a big deal about it to complete the plan of discredit.
The main point I’m trying to make is that if you aren’t de-compiling the flash every time to investigate what they are doing — you are allowing ANY third party (who might mean to harm you) to run ANY code they want on my browser when I visit your site. Which means they can easily re-direct me to a site under their control running complete drive-by-downloading infection software suites.
If you were just a normal site not dealing with shining light on the “Bad” actors; this would not be as big of a concern. But you have a nice target on your back; and the disruption “I” (as a bad actor) could cause to your site by causing your site to be responsible for compromising your readers would be imho worth 6+ months of ad cost!
That would be my warning to you; the risk for you running any Java, Flash, Silverlight or even a simple third party JavaScript based ad’s is not worth the potential credibility hit you would take if a bad actor was patient and really wanted to get “even” with you. (& I’m sure you don’t have any bad “actors” who have the financial means and/or any motive to want to get even with your reporting, do you? 🙂 )
Maybe I’m a long term kinda guy; but the above plan is very obvious to me on how to hurt you where it counts (your readers and what they think of you), and depending on how patient and $$$ they wanted to spend they could do a serious number on your credibility.
Nathan
P.S. To be extra devious; a bad actor could frame another bad actor easily to make you waste resources when cleaning up… 🙂
You could also just stop using the internet since attacks could, in theory, happen while you are using it.
Or you could just accept that the scenario you just painted is possible but very unlikely due to the number of hoops an attacker would have to jump through.
Neej,
I would agree in most circumstances it is unlikely. However if anyone has a grudge against Brian specifically (hmm, how many people has he painted the connection to X or Y with his articles that they wouldn’t have liked known?) — This is a fairly cheap and very easy way to exact some revenge. The code (as a developer) is very, very simple (around 4 lines to redirect to another site) and it all depends on how much damage “I” as the bad guy wants to do. The simplist and cheapest way is the first flash add has a date bomb half way into the month. Doesn’t matter how many times Brian views it — it won’t trigger anything bad until mid-month.
I’m not worried about myself; I’m already paranoid about security on my computer and run with several things like noscript, ghostry and requestpolicy, etc. 🙂
But I happen to hope Brian will stick around for a long time and don’t want to see him take any hits that he could have easily prevented. Very much like we recommend boot disks or dedicated computers for financial stuff. It can easily be prevented…
Nathan
OK, you review your flash ads personally and approve that they are “safe”. I’m willing to concede that you know more about the specific mechanics of flash attacks and your word is good enough for me.
BUT, that means I have to install Flash to support your site through advertising. I do know for a fact that I CAN’T trust other sites, and the simplest defense is to not allow FLASH in my primary browser.
Yes, I do have a browser installation to view flash items when I want to, but, I do not use it for day to day browsing. So I don’t see your flash ads, and I therefore you lose potential click-thru revenue. Sorry, but my simplistic approach to security is more important to me than me denying you 2cents (or whatever …) worth of advertising revenue.
Leaving alone the fact that no one can be forced to install and use flash. And admiting that click-rates tend to 0,000% (nothing), I still hope for the mug, the poster, the book and the dvd. 😉
On the other hand if Ads still rely on flash they’ve still to learn something from Google… so much text-ads… how uncool, Google must be stupid. oO
I suspect you are one of these users that never clicks on ads (or probably sees them to click on in the first place) – good for you -but given the arrangements here concerning the displaying of ads I doubt very much that the campaigns being run by the advertisers are unprofitable or that Brian is getting a CTR rate tending to nothing.
The reason I say this is because (my guess) this isn’t a property where entities would pay for non-performing ads (read losing money) to stop competitors running their ads on the same property – this often happens in some verticals on larger properties such as relevant SE results pages. And I’d also expect Brian to stop running with these same ads and try something else if they aren’t at least profitable.
Oh and in some circumstances Flash/banners will outperform text by a country mile BTW but it comes down to circumstances.
“The average click-through rate of 3% in the 1990s declined to 0.1%-0.3% by 2011.” (Wikipedia.org/wiki/Click-through_rate)
Today maybe ads are more an instrument of SEO… (I prefer sponsorship – and no, Flash isn’t an option if the audience includes iOS or Chrome users…)
I’m really not sure how that figure was calculated (feel free to go and look at the citation, I haven’t got the time) but it’s not typical of a well run ad placement campaign. I suspect the figure was arrived at by using impressions as a whole across the board in which case it’s not a surprise considering the explosion of pages that’s occurred not least SEO efforts creating pages on Web 2.0 properties.
I earn my living largely by creating and managing PPC campaigns and conducting media buys. A typical CTR on a on well run Adwords campaign is 2-3% – and indeed Google encourages higher CTR by materially punishing those advertisers with low CTR (your bid price goes up to achieve the same number of impressions vs entities bidding on the same triggers).
There has not been a drop in Google’s revenue from Adwords revenue which currently sits at over $100 million … per day.
Bottom line is advertising online is not dying by a long shot.
As an elderly female user of the internet, actually since Windows 98, I have Flash turned off because with my computer on Windows Vista and also for reasons best known to newspaper sites it takes longer to load a page where the flash player advertisements are judged suitable for my delectation. Most are entirely unsuitable but that is another matter.
How is it Brian started this discussion talking about an international spy network and now it’s dissolved into the good-bad-and-ugly of using Flash? Use it or not, we could care less, but try to keep the discussion on-topic. If you want to send Brian a comment about his advertising practices why don’t you use his freely-available email address and be done with it.
And if you don’t see the ads because you’re blocking them (like most of us) why don’t you consider clicking on the PayPal Donate button and sending some coin to Brian so he’ll keep posting his excellent and unique content. I’m going to do it right now, why don’t you join me!
Its a good discussion, and a valid point. Anybody following his guidelines won’t see the ads anyway, seems like they could be structured differently where they would benefit both parties a lot better way. Flash has a bad track record and it is a bit hypocritical that Brian is using it on his site, would seem more in line with his goals to have a page with recommended products or services that are presented without flash.
As for the article, it is interesting but not the first to handle targeted spying on that part of the world, definitely represents a shift in the direction our nation’s will go to that relies less on a physical carpet bombing of earlier wars and does a virtual carpet bombing instead.