Microsoft and Symantec said Wednesday that they have teamed up to seize control over the “Bamital” botnet, a multi-million dollar crime machine that used malicious software to hijack search results. The two companies are now using that control to alert hundreds of thousands of users whose PCs remain infected with the malware.
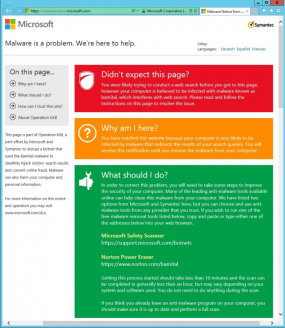 The tech firms said their research shows that in the last two years, more than eight million computers have been attacked by Bamital, and that the botnet’s search hijacking and click fraud schemes affected many major search engines and browsers, including those offered by Microsoft, Yahoo and Google.
The tech firms said their research shows that in the last two years, more than eight million computers have been attacked by Bamital, and that the botnet’s search hijacking and click fraud schemes affected many major search engines and browsers, including those offered by Microsoft, Yahoo and Google.
Users of machines infected with Bamital are likely to see a Web page like the one pictured at right the next time they search for something online. That’s because Microsoft convinced a judge at the U.S. District Court for the Eastern District of Virginia to give it control over the infrastructure that Bamital used to coordinate the search hijacking activities of host PCs.
On Wednesday, technicians working on behalf of both Microsoft and Symantec raided data centers at Leaseweb USA in Manassas, Va., and ISPrime in Weekawken, New Jersey, accompanied by U.S. federal marshals. The two companies are now using the botnet’s control channels to communicate with infected PCs and to notify affected users.
According to Microsoft’s lawsuit, Bamital is most often installed via drive-by downloads, which use exploit kits stitched into hacked and malicious Web sites. Microsoft said the bad guys behind the botnet exclusively used the Phoenix Exploit Kit, a malware tool that uses vulnerabilities in Web browsers to silently install malware.
Bamital alters the organic search results on the host machine, redirecting victims away from sites as indexed by the major search providers toward pages that provide advertising and referral commissions to affiliate marketers. Redmond included several examples in its petition to the court, such as when a victim with Bamital searches for Microsoft Halo, and upon clicking the top link in the results is taken to a completely different set of search engine results.
Microsoft said Bamital also orders infected systems to participate in “click fraud,” or to generate automated Internet traffic by instructing those computers — without the owner’s knowledge or intervention — to connect to any Web site chosen by the botmasters. Meanwhile, the owner of the infected computer – even if they were sitting at the computer – would not see the hidden browser.
It’s not hard to see why threats like Bamital are so prevalent: An estimated $12.7 billion was spent on Internet advertising in 2012, and click fraud is taking a huge bite out of the expected returns. Microsoft’s own research indicates that 22 percent of all ad-clicks are fraudulent.
The takedown comes amid the release of even more alarming figures about bot-driven ad traffic. In its latest Bot Traffic Market Advisory issued today, New York-based ad network Solve Media said it tracked a “staggering” spike in bogus bot traffic affecting ad networks in the 4th quarter of 2012; the company estimates bots like those enslaved by Bamital cost marketers $1 billion in display ads and more than $2 billion in digital advertising investments.
Microsoft and Symantec told the court they believe that the fraudsters behind Bamital earned at least $1 million a year in profits from the operation. In its lawsuit, Microsoft listed the email addresses and other information supplied by 18 “John Does,” individuals thought to be affiliated with the scheme that Microsoft is hoping to identify.
Microsoft said all of the websites that it found were directing computers to the Bamital download sites installed a small “cookie” or text file on the user’s computer. “The text of this particular cookie is ‘yatutuzebil,’ which is an approximate phonetic spelling of a Russian phrase loosely translating to, ‘I was here already,'” Microsoft wrote. “It is likely that the cybercriminals use this cookie to identify computers that they have already probed.”
Microsoft and Symantec both warn that Bamital was often bundled with other malware. The two companies are guiding victimized users toward free tools to help clean up the malware, including Microsoft’s Safety Scanner and Symantec’s Norton Power Eraser.
A copy of the lawsuit Microsoft filed is here (PDF); a supporting declaration with more information about Bamital and its click fraud schemes is here (PDF).





I’m all for this type of notice letting people know their computer may be compromised. I can’t tell from the screen shot however if the user has the choice to proceed to search results (a “continue” link or somesuch) or if they can no longer do searches until malware is removed.
I would hope it’s the latter. If a user can work around it where’s the strong incentive to scan their machine not only for Bamital but other compromises?
If you do not know your computer has been compromised how can you help with the next security features needed. Innovation is the key, along with layers, and layers of safety!!
How long do you suppose until the criminals are putting up pages that look like Microsoft’s redirect with malicious rather than helpful links?
Hrm, it seems to me they’ve been doing this forever already. It’s certainly possible — maybe even likely — that fraudsters will jump on this and put up similar warnings. But I don’t think that means Microsoft shouldn’t use the access it has to try to clean up infected systems. It would be silly of them not to try, IMHO.
I believe the term Ransomware was created to describe software that did just that. Get the person infected, then “help” the person by getting them to pay you money to “remove” the infection, only to pop up another “helpful” warning a few weeks/months later that they’re infected again.
Y’ call it a p’otection racket. Y’ know whadI mean?
Fuhgedaboudit.
I wish authors, when writing about malware, would direct people, or better yet, have it in the text of their articles, how to manually identify and remove this. I can understand why you might not want to include it in the text of the article, so at least a link would be nice. Just using someone else’s tool isn’t a good idea, as you don’t know what that tool is doing.
I believe I specified one way to manually identify it. If you’ve got a cookie like the one mentioned in this story, you probably have this malware.
Why is a tool from MS or Symantec any more suspect than a tool from anywhere else? You generally don’t know what they’re doing, unless you can inspect the code, and most of the tools out there are for diagnosing and removing malware from Windows machines are not open source.
I think the point he was trying to make is that much of the time we don’t know what the tool is doing.
We don’t need to inspect the source code. We just need some documentation as to what the tool is doing, in case it screws up.
For instance, running Combofix is considered “at your own risk” – but there is ZERO documentation as to what it’s doing when it runs through its fifty or more “steps”. That makes me as a tech support guy nervous. If it fries the client’s computer, I’m going to get blamed especially if I had no idea what it did.
For finding Bamital manually, it is very simple. You just need to check 3 files on your PC using an online sandbox like: http://www.virustotal.com
– C:\Windows\explorer.exe
– C:\Windows\system32\svchost.exe
– C:\Windows\system32\winlogon.exe
Virustotal will tell you very clearly whether the file is infected and with what. As far as manual removal goes, you are not going to have an easy time with that. Manual removal for this infection is not recommended as Bamital is a file-infector, and the files it infects are necessary for Windows to function properly.
I agree that references to the IP address the MS put up or other details about the remote networks used by the malware for C&C would be helpful so we can load up our SIEM’s and do some validation across the enterprise. I reviewed the court order linked in Brian’s article – however the appendices which listed domains / IP’s were not included. I then went to symantec and checked on malware technical details – discovered the following:
1. Microsoft owns this ip 199.2.137.138/32 and 90% of the domains referenced by Symantec resolve to this address – hence that’s the address that MS is using to sinkhole this thing (assumption only)
2. Several other IP’s were referenced by Symantec, which aren’t owned by MS 46.4.31.134/32,202.141.12.3/32,50.63.202.12/32
202.141.12.3/32,202.141.12.3/32,64.74.223.34/32
212.154.192.98/32,195.22.26.231/32,108.59.3.131/32
I’m adding all these to my SIEM so I can get alerted if computers in our org end up going there. Doesn’t mean it’s malware but w/o any other information – it’s all I have to go on.
I wish readers were more knowledgeable in the subjects they read about. You trust Microsoft for your operating system and allow auto updates but you’re weary of an automated botnet removal tool from MS?
Wow, over 22% of pay-per-clicks was fraud in 2012. This is not good to for people using AdWords and Bing Ads. At least, they stopped that botnet.. but is there more running? could it be 50%? scary.
Just wondering why this is dated as futuristic – Feb 13.
I wonder when the elephants are going to gain attention – over 50% of spam comes from Cutwail 1, Cutwail 4 and Lethic. See
https://www.trustwave.com/support/labs/spam_statistics.asp
Hi Terry. Haven’t seen you in a while. Welcome back. The date is not standard, to be sure, because it confuses a lot of people. The day in the date box at the top left of every story is the big number on top. The month, and then year.