Several years ago, Microsoft released the Enhanced Mitigation Experience Toolkit (EMET), a free tool that can help Windows users beef up the security of third-party applications. This week, Microsoft debuted EMET 4.0, which includes some important new security protections and compatibility fixes for this unobtrusive but effective security tool.
First, a quick overview of what EMET does. EMET allows users to force applications to use several key security defenses built into Windows — including Address Space Layout Randomization (ASLR) and Data Execution Prevention (DEP). Put very simply, DEP is designed to make it harder to exploit security vulnerabilities on Windows, and ASLR makes it more difficult for exploits and malware to find the specific places in a system’s memory that they need to do their dirty work.
EMET can force a non-Microsoft application to perform ASLR on every component it loads, whether the program wants it or not. Please note that before you install EMET, you’ll need to have Microsoft’s .NET Framwork 4 platform installed. And while EMET does work on Windows XP (Service Pack 3 only), XP users cannot take advantage of mandatory ASLR and a few other notable protections included in this tool.
However, EMET includes several important security features that can help fortify third-party applications on XP. Namely, its “Structured Exception Handler Overwrite Protection,” or SEHOP protection, which guards against the most common technique for exploiting stack overflows on Windows. Microsoft says this mitigation has shipped with Windows ever since Windows Vista Service Pack 1.
In addition to a revised user interface, EMET 4.0 includes a handful of new features that were bundled with the 3.5 tech preview version, such as novel methods of blocking an exploit technique called return-oriented programming (ROP). Attackers can leverage ROP to bypass DEP protections by using snippets of code that are already present in the targeted application.
One of the much-hyped new capabilities of EMET 4.0 is its “certificate trust” feature, which is designed to block so-called “man-in-the-middle” attacks that leverage counterfeit SSL certificates in the browser. The past few years saw several attacks that impersonated Webmail providers and other top Internet destinations using fraudulent digital certificates obtained by certificate authorities, including Comodo, DigitNotar and Turktrust. This feature is a nice idea, but it seems somewhat clunky to implement, and only works to protect users who browse the Web with Internet Explorer. For tips on configuring and using this feature of EMET, check out this post.
To proceed with EMET, download the program and install it (if you are upgrading from an older version of EMET, uninstall the older version first before proceeding with the EMET 4.0 install). This new version of EMET gives users an option to allow a pre-set group of applications to be automatically protected by EMET, including Java, Adobe Acrobat, Internet Explorer and any Office apps that may be installed. Alternatively, users can start from scratch and select their own applications to put behind EMET.
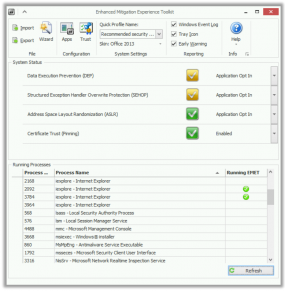
To wrap EMET’s protection around a program — say, Mozilla Firefox — launch EMET and click the “Apps” button in the upper portion of the main EMET window. Selecting the “Add Application” button in the next box brings up a program selection prompt; browse to C:\Program Files (x86)\Mozilla Firefox, and then add the “firefox.exe” file. It should be okay to accept all of the defaults that EMET adds for you.
While you’re at it, add the rest of your more commonly used, Internet-facing apps. But go slow with it, and avoid the temptation to make system-wide changes. Changing system defaults across the board – such as changing ASLR and DEP settings using the “configure system” tab – may cause stability and bootup problems.
I’ve been using EMET on a 64-bit Windows 7 system and phasing in some of my most-used applications one-by-one with the “configure apps” button just to make sure the added security doesn’t crash the programs. Microsoft’s support forum has a useful thread on applications that may not play nice with EMET’s default protection settings.
For example, a handful of applications will simply crash or not work with EMET’s “export address table access filtering” (EAF) mitigation turned on. Skype is one well-known example here. I’ve also experienced issues with running EAF on Google Chrome.
This is really where EMET’s unobtrusiveness can be a blessing and a curse. Unlike some security and antivirus tools that periodically pop-up annoying warnings or notifications to let you know they’re still there and doing their job, EMET is likely to do its job unnoticed by most users. I say curse because on one occasion (I can’t recall the name of the application at issue) I spent a few days scratching my head over an app that wouldn’t work properly, only to remember later that I’d set it to use EMET months before.
If you have questions about EMET or run into issues with the program, check out the Microsoft support page for EMET, which lets you to submit questions to the user community if you don’t see your problem addressed in a previous support thread.
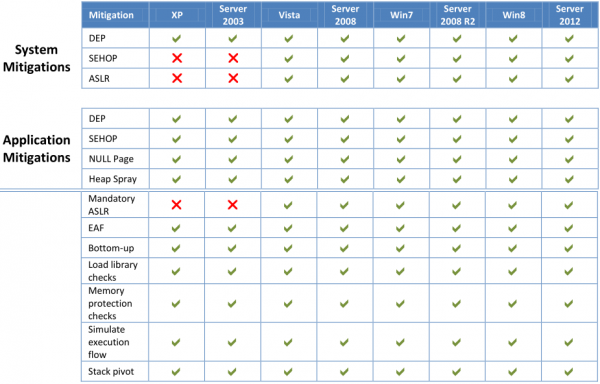
The chart above indicates which system- and application-specific protections in EMET 4.0 are available for each supported version of Windows. Visit this link to download EMET 4.0, as well as a detailed user guide on the software.




The average user would probably not be interested in the tool because it does force him/her to be a bit of a “techie.” Why doesn’t Microsoft incorporate this into the OS, making it transparent to the user? This is no way to incorporate better security for all!
Regards,
And those are exactly the people that need it most. Microsoft provides several pre-canned templates that most all users can simply import into the configuration and they’ll be good to go. If an application is acting up they can simply deselect it from the list.
Yeah, I’ve been reading Brian Krebs and his former colleague Rob Pegoraro since their Washington Post days, but this seems like too much for me.
I realize this post is quite a bit nerdier than most of my pieces — like Geek Factor 5 nerdy — but believe me when I say EMET is not a difficult tool to use.
If you’re unconvinced, don’t take my word for it: Grab a copy of the program, and see for yourself. For the protection that it offers, it seems silly not to take advantage of it.
Where can I buy this kit? I have not read the article yet, as i’m legally blind & need larger print to read at length. May I have your permision to copy/paste & enlarge it? I’m desperately trying to get my husband to pay closer attention to security issues! Maybe if we hire a computer guy in our area, he can download it for us.
Thanks….
The program is free if you have a valid copy of microsoft windows, and the download-link is provided in the article:
http://support.microsoft.com/kb/2458544
/b
Here is a more direct download-link:
http://www.microsoft.com/en-us/download/details.aspx?id=39273
Have you ever tried using Narrator, a feature in Windows 7, to read text to you?
http://windows.microsoft.com/en-us/windows7/hear-text-read-aloud-with-narrator
Most browsers will increase/decrease the display size of a website if you hold CTRL and scroll with the mouse wheel.
CTRL + = works to increase size as well,
CTRL + – to decrease
CTRL + 0 to return to default size.
Well if people are prepared to download non-Windows endorsed software on to their Windows system then they should be techie enough to secure it, surely?
Yeah, no kidding. People usually don’t add anything more complicated than seat covers and fuzzy dice to their car, yet they add applications to their PC from every Tom, Dick, and Sergei and then complain when something goes south.
And don’t call me Shirley.
The short answer is that if a program stops working:
1. users won’t know why
2. users will blame Microsoft
A more detailed answer:
* Not every user uses every feature of a program. it’s very easy for the security improvements that are being offered here to not break 99% of a program. but happen to break 30 rarely used paths. If a user happens to use even one of those paths. the user will be upset when the program breaks.
* Programs get updated. s0metimes they’ll use a clever feature which in a new version that could be incompatible with the settings you have (this shouldn’t happen. but w/ browsers. it is possible).
* Many programs support modular additions:
– Office has “Add-Ins” — actually. it has a bunch of kinds – the main one that matters here are “COM”
– Firefox has plugins — actually. it has two kinds NPAPI browser plugins. and XPCOM based browser extensions
– VLC has codecs — they’re plugins
– Explorer has shell extensions
– Reader has plugins — e.g. for form submission/crypto/signing/…
— all of these things allow third party modules to be loaded into an application. When you turn on a setting in EMET for an application. it affects the application. its normally shipped libraries. and these third party libraries that you may have installed separately knowingly or unknowingly (Skype for instance adds plugins into Firefox).
There’s a reason that Brian is recommending that you install EMET and change a single application’s settings at a time. If you change too many. and a bunch of things break. you’ll be really frustrated. and you won’t know what to undo/how to fix. If you install EMET and gradually apply changes. you’ll be able to recognize “oh. I recently applied EMET to Firefox. and it started crashing. maybe an EMET setting is incompatible with something about the configuration of _my_ Firefox. let me try turning off EMET and see if the problem goes away. Aha. it did. Ok. if I have some spare time. why don’t I try turning on /half/ of the EMET options for Firefox. Oh. the problem came back. let me turn off that half and try the other half…. ooh. Firefox seems to work with this set. Let’s try turning on half of the first set of options…” By trial and error and using this divide and conquer approach to individual applications. you will eventually be able to find the most protective set of options that work for your applications as you have them configured today. Unfortunately. you’ll have to be aware that if your program stops working after an update (to it. or its components). that it could be an incompatibility between your EMET settings and the program’s new components. So. when the program starts crashing. you should try turning off EMET and see if the crash goes away. if so. you’ll want to repeat the process of identifying which EMET options can be applied to the new program configuration.
Ideally. people would complain to the right vendors with sufficient information about problems w/ EMET. But that involves – identifying which version of the application. which version of any addons. which EMET option. and the steps it takes for the problem to occur. along with something equivalent to a crash-report. — But most people won’t do this.
“There’s a reason that Brian is recommending that you install EMET and change a single application’s settings at a time. If you change too many. and a bunch of things break. you’ll be really frustrated. and you won’t know what to undo/how to fix.”
In IT classes, students are taught the above theory: if you make lots of changes and something breaks, you have no idea what was responsible. And the reverse is true: if you make lots of changes to fix something and the problem goes away, you have no idea what the fix was.
Customers and managers often do not understand this.
Some people here may disagree with me, but I believe that antivirus products play a role in EMET strangeness. I have already seen one antivirus product (Norton) work perfectly, but another had minor, temporary strangeness. I could see how a less-popular antivirus product was never tested.
This may be “Windows Security 101” to a guy as incredibly smart as Brian Krebs, but it’s version 1,000,001 to 99% of PC users…
BTW, the 2nd issue on the “check out the Microsoft support page for EMET” page is entitled, “EMET 4.0 default install breaks IE 10…” and the 5th issue is entitled, “EMETv4 GPO system settings ignored” — OOPS! Should this have been called a beta? Could version 4.1 be out soon?
Oh, Lord, it never ends. 😉
Those issues are due to folks not reading the documentation and release notes. EMET 4.0 should NOT be installed over any older version other than EMET 3.0. The GPO issue isn’t really an issue; when assigning the settings via a GPO they will not show up in the local client’s EMET interface. The admin can do a gpresult against the computer in question to see if the settings have been applied.
Worth noting that when settings are deployed via GPO, the computer must be restarted for them to take affect.
Is there a significant impact to system or application performance when using EMET? If no, why doens’t Microsoft integrate it into their OS?
Some aspects of EMET are already included in Windows from Vista onwards. In fact, many of the features are usable by software developers without EMET.
The problem is that many developers don’t bother to use these features.
EMET allows you to force applications to use these features, along with a few newer features not currently implemented within the Windows OS. However, because the applications were designed without these features in mind it is possible for EMET to break their operation.
Because of this I believe Microsoft wish to keep EMET as an option for those more familiar with Windows and Security than ship it for use by the average user.
As one of the 99% (non tech savvy) folks out there, this is problematic–do I spend the time (potentially hours if not days of my hectic life) learning and then installing and figuring out how to use this software? Is it important enough to warrant that level of effort? I wish Brian (or someone in the tech community) would address the time/learning curve tradeoffs instead of just taking the attitude, “here’s another nifty piece of software to spend/waste time with.”
As one commenter already stated, EMET 4.0 makes it silly easy to set up the basic protections; it requires clicking a box after installation to set the defaults.
After that, it’s really just adding the .exe files for the main internet-facing applications that you use each day, whether it’s Chrome, Firefox, Pidgin, iTunes, whatever. This process really doesn’t take more than a few minutes, and after that it’s done.
I agree, I’ve just installed it and it’s easy if you just use the included templates. Although, I can see why some people maybe a bit apprehensive about using it because it’s not clear which applications people should and shouldn’t add to it or which settings are going to lead to app crashes. At the moment it seems to be trial and error. It would probably be more appealing if a blogger were to put a big list of applications/settings known to work without app crashes (sort of an expanded version of the bundled templates, which includes more programs).
Another thing, if the Certificate Trust feature uses the Windows Certificate store, why they didn’t make it so it could be used with email clients such as Outlook or Windows Live Mail for SSL/TLS mail server connections? Or even the desktop Skype application. I guess it’s not as simple to find out what certificate are being used, as it is when using Internet Explorer?
The story above contains at least two links to what you’re seeking. The instruction manual that Microsoft ships with EMET and a separate forum thread on MS’s site where users have shared their experiences with apps that present glitches in EMET.
http://social.technet.microsoft.com/Forums/en-US/emet/thread/1e70c72b-67b2-43c4-bd36-a0edd1857875
Ah Brian, don’t let them get to you. If these folks had to read Xylibox and only get a rough, technical outline of an online operation instead of getting the whole story from you, half their heads would explode.
” I wish Brian (or someone in the tech community) would address the time/learning curve tradeoffs”
One of the problems with the Internet is that most people are trying to sell you something; their advice should be taken with a grain of salt. If Brian recommends something, it is well worth considering. EMET 4.0 is worth the trouble.
I agree with the other non-techy comments. this is way beyond me. if it’s so easy, then microsoft should give us non-tech people step by step instructions or as others have said make it part of the operating system.
For example, how do i add “the .exe files for the main internet-facing applications that you use each day, whether it’s Chrome, Firefox, Pidgin, iTunes, whatever.”
I explain how to do that in the story:
“To wrap EMET’s protection around a program — say, Mozilla Firefox — launch EMET and click the “Apps” button in the upper portion of the main EMET window. Selecting the “Add Application” button in the next box that brings up a program selection prompt; browse to C:\Program Files (x86)\Mozilla Firefox, and then add the “firefox.exe” file. It should be okay to accept all of the defaults that EMET adds for you.”
Here’s the download link. http://www.microsoft.com/en-us/download/details.aspx?id=39273
The download link is in already in the story (last sentence).
Also, another simple way to add your apps (e.g. FireFox, QuickTime Player, iTunes, or whatever) is to start those apps, then find them in the “Running Processes” box, right-click them and choose “Configure Process.” They get added to the protection list on the spot. This capability was new in 4.0 Beta.
EMET is easy to install, as easy as any other program. Run the installer, done. If that’s all you do, and you simply go with the Big Green Shield option like an average person would, you’ve already EMET’ed Office, Adobe Acrobat and Reader, Java, Internet Explorer, and WordPad.
Once EMET is open, the very large green, yellow or red symbols for the system protection options should be fairly obvious. Oh, I’ve got a yellow symbol… *clicks on it* …hey, and choosing this other option gives me a green symbol, and we all know green is better. There! 🙂
From there, adding additional apps to the protection list may not be something you expect the average homeowner to do intuitively, although if they actually understand *why* they’re installing EMET, it does follow logically. On the other hand, if they could get free music albums using EMET, I guarantee most of them would have it nailed within an hour 😉 That’s the challenge with computer security; people generally don’t have the motivation to learn, when the best-case outcome is that nothing visibly bad happens.
Brian, the link you give to the Microsoft’s support forum thread is for EMET 3.0 incompatibilities.
I don’t know of any other link. That’s the link that Microsoft itself gave out in its EMET 4.0 PDF User Guide, which is at the same link as the EMET file download.
The link in the article to Microsoft’s EMET Support Forum is to the sticky post in that forum (“Incompatibilities”) – and if you read it, remember that the oldest posts are at the top. Several posts from the past couple of weeks seem to indicate few or no new problems with version 4.
The main EMET forum is easy enough to find :
http://social.technet.microsoft.com/Forums/security/en-US/user/threads?user=EMET%20Support
The only thing hard about using EMET is how long it takes you to realize that was really all you had to do. I used EMET 3 in a community college security course where the teacher was almost totally hands off. We had it figured out and our test server secure in a couple hours with no help whatsoever. EMET is about as hard to configure as your average decent AV or firewall. I’ve had way more challenging installs of Windows itself than EMET.
I have a question that likely reflects my shallow knowledge of all of this:
is there any advantage to wrapping EMET around a program like VirtualBox? Suppose you are using VirtualBox to run a virtual machine and using the vm to browse websites online.
I also have to say that I appreciate posts like this. They form a bridge between highly technical articles elsewhere that a novice like me can’t begin to understand, and articles too basic to provide enough information. In fact, I wouldn’t mind seeing some posts on things like the virtual machines and highly security conscious operating systems like the Lightweight Portable Security version of Linux, both of which sound intimidating to someone like me but which are incredibly easy to explore without damaging your system.
Good question. You can wrap EMET around virtually anything. If it stops working as usual, you can dial back the mitigations one at a time until it works as expected. Often, a simple search online will tell you what mitigation caused the problem, or perhaps it is already documented at the link I mentioned in the story (http://social.technet.microsoft.com/Forums/en-US/emet/thread/1e70c72b-67b2-43c4-bd36-a0edd1857875)
To answer your question, yes, you can and should wrap vbox.exe inside of EMET. It works just fine with all of the mitigations that EMET 4.0 has, I’ve found.
Hey, Brian, you mentioned it didn’t work well with Chrome. That wouldn’t surprise me. I recall from a detailed technical investigation that the outer sandbox uses a huge number of Windows security API’s and privilege reduction techniques. It could be a clash between what EMET is trying to do and what Chrome does already, like we saw with AV companies in early days. Of course, Chrome’s so well-architected I probably wouldn’t worry about applying EMET to it anyway but I know many people like extra layers.
I wonder how many applications might have problems with EMET simply b/c they did their job, already used security API’s and dumped privileges. Maybe some, maybe none. I’d find it interesting though.
Thanks for the post, Brian!
1) I would try EMET,
but in my case, I have XP-PRO 32 bit,
(as the article points out,
the EMET protection for XP is not as effective).
2) Also,
having to install the dreadful MS .NET framework,
(a real headache MS software),
is a show-stopper for me.
I UNinstalled .NET, four years ago.
No more messy .NET upgrades or vulnerabilities…
Anyhow,
in April 2014, when MS stops delivering
Security Updates for XP,
I’ll be moving to UBUNTU Linux.
We are very happy with Ubuntu on our other PCs.
Fully operational.
We can concentrate in doing real work,
and not carrying MS’ failed OS.
I really have developed “Windows Vulnerability Fatigue”…
Just sharing here.
Thanks again, Brian.
You are fooling yourself if you think any other OS or piece of software doesn’t have vulnerabilities…MS does a fantastic job of securing and patching their product given the size, complexity, and age of the company and their products. It’s not like it was 10 or 15 years ago…Also, EMET works for Windows XP (SP3) but just doesn’t offer two or three features – check the article again, Brian has a chart that even clearly outlines it for crying outloud…And again, like Brian said it’s SO totally worth putting it on for the simplicity in manging and configuration it requires for the benefits received.
If it wasn’t worth it or easy, he wouldn’t have posted such a fantastic article on it and suggested that it’s easy. Seriously…
SF109 wrote:
> I UNinstalled .NET, four years ago.
> No more messy .NET upgrades or vulnerabilities…
“Messy” is one of many spot-on adjectives to describe the .NET .MESS Framework and its absurdly nonsensical numbering scheme:
http://en.wikipedia.org/wiki/.NET_Framework#History (<– formatted table looks better there)
Overview of .NET Framework release history
Generation Version number Release date Development tool Distributed with
1.0 1.0.3705.0 2002-02-13 Visual Studio .NET N/A
1.1 1.1.4322.573 2003-04-24 Visual Studio .NET 2003 Windows Server 2003
2.0 2.0.50727.42 2005-11-07 Visual Studio 2005 Windows Server 2003 R2
3.0 3.0.4506.30 2006-11-06 Expression Blend Windows Vista, Windows Server 2008
3.5 3.5.21022.8 2007-11-19 Visual Studio 2008 Windows 7, Windows Server 2008 R2
4.0 4.0.30319.1 2010-04-12 Visual Studio 2010 N/A
4.5 4.5.50709.17929 2012-08-15 Visual Studio 2012 Windows 8, Windows Server 2012
QUESTION: Does anyone know why there so many numbers in 4.5.50709.17929 or the other versions?
Do those digits actually mean something?
Leo Notenboom, of Ask-Leo.com fame, agrees with SF109, too:
http://ask-leo.com/what_is_the_net_framework_and_do_i_need_all_these_versions.html
In 2008, he wrote:
".NET versioning, unfortunately, is apparently a mess." and "Rumors are that the mess will get cleaned up in a future version, but in all honesty, I'm skeptical."
Leo tends to be pretty spot-on, too! 😉
I don’t understand why this technology is not included with windows by default. To protect at least some microsoft’s own apps like IE or office.
In all of this discussion, nobody has mentioned a rather glaring flaw with EMET 4.0: installing it on a formerly EMET-free Windows 7 box and adding Firefox to it results in Firefox causing a BSOD at startup. Removing Firefox from EMET after the reboot allows its use again, but it will have forgotten all of its open tabs, without “restore previous session” being enabled.
Since the #1 most important thing to protect with EMET would be your web browser, and you’re insane if your web browser lacks AdBlock (leaving Firefox and Chrome), or lacks NoScript or comes from a company that participates in PRISM (leaving Firefox), that’s pretty much a show-stopper.
A warning that EMET + Firefox = reboots, data loss, and other trouble would have been useful, at any rate.
Did this happen to you personally only, or is it a known issue that affects 100% of every installation…?
…You must have some sort of conflict with something else and are attributing it to Windows/EMET/Firefox combination incorrectly and/or your EMET settings are too strict for it by default and simply need tuned as Brian clearly mentioned.
We’d appreciate a bit more fact-checking before you spout statements like that…! :oP
Seriously though…So sit there and squabble about this as if EMET is greatly flawed and is terrible and no use when in truth it really is an excellent utility to help protect from the “unknown” as well as the “known”…You’re doing a great disservice to protecting the general user and a great service to malware/virus writers…Nice work!!
Firefox was working fine. The only thing changed was to install EMET and hook it up to Firefox. And I let EMET use the default (which, mind you, looked like it was “all the mitigations”) without altering it (for Firefox, or elsewhere).
Furthermore, the original article implied that the worst that would result from a wrong setting (other than if you unwisely applied it to things like your graphics drivers, or forced mitigations on system-wide) was an *application* crash (or EMET misdiagnosing it as malware and shutting it down, with equivalent results). That implication was also clearly incorrect.
I’ve now uninstalled it completely after getting another blue screen apparently triggered by something else than Firefox.
EMET 4.0 is not ready for prime time.
Excellent comment! I can’t begin to understand why people who are supposedly intelligent would make some of the comments I read here. One would think that anyone reading this particular blog would have a modicum of tech savvy and appreciate the value of a great tool. I’ve used the previous version since it first came out and believe me it doesn’t take a rocket scientist to understand it. I guess it is easier to write complaints than to read instructions; it sure seems that way from observing what people put into print.
Who’s “not reading instructions”? It’s not supposed to cause ordinary user-mode applications to BSOD, period, no matter what else goes wrong. Only forcing mitigations on system-wide was indicated as potentially being able to make the system itself unstable (or even unbootable).
Furthermore, doing with firefox.exe *exactly* what was described, no more and no less, resulted in a BSOD.
If you can quote chapter and verse to point to exactly what I (allegedly) did wrong, go right ahead. If you can’t or won’t, that shall be taken as your tacit admission that your initial, knee-jerk judgment of me was based on assumptions, not knowledge of any error on my part, and moreover, on assumptions that were incorrect.
I have installed it on two PCs running W-7 Pro 64-bit. I have experienced no problem whatsoever in running Firefox. I will shortly install it on a few more W-7 PCs and I will be shocked if I have a lick of trouble.
Yours is not a universal problem. As “me” wrote, you probably have a problem with something else. Did you look at your system logs for error messages? Are you sure your PC does not have malware which is fighting EMET?
EMET 4.0 is so much better than previous versions. Having the most common applications initially added is a nice feature.
Everyone should remember to add their PDF reader application to EMET.
Here it’s W7 Home Premium 64-bit. Same version of EMET, presumably, and same version of Firefox (since Firefox auto-updates unavoidably these days). The only logical conclusion is that it doesn’t work properly on W7 Home, as that’s the only difference in a relevant component, or else its behavior with Firefox incorrectly depends on something other than itself, Firefox, and the operating system.
(Malware fighting EMET? EMET is supposed to stop malware from getting in the door; it does nothing to threaten malware that already has infected the local machine, and such malware can open a door for additional components to be installed that EMET wouldn’t block. I can’t see any reason why malware would fight EMET; all that could accomplish is to open the door to *competing* malware. Besides, I’m quite sure this machine is clean. I use NoScript and have disabled the in-browser Java; Avast isn’t detecting anything; and there are no symptoms of any problems. Everything was working fine before I tried to use EMET, and everything is working fine again since I uninstalled EMET. The problem was EMET. And the solution is I’m never using a “.0” version of anything from MSFT ever again. :P)
I now have it running on two W-7 Home Premium 64-bit, two W-7 Pro 64-bit, and one HP laptop with HP’s version of W-7 Pro 64-bit. The only problem I have seen is on the laptop, where some of the EMET icons at the top do not appear, but I’ll bet that is an artifact of the not-so-great display resolution and my setting of the text-size to MEDIUM.
I just threw out the malware bit because it is not uncommon for it to interfere with anti-virus software, so it is not a stretch to assume that some young-un has done the same with EMET.
I still say it has to do with your PC. Has it had a few different anti-virus and other applications, first installed and then uninstalled? After a period of that, a PC needs to have its OS reinstalled, because Windows is notorious for not removing all traces of applications. At least use Ccleaner to freshen-up the registry.
If there was a problem with this PC, it would surely result in other symptoms besides EMET not working correctly. If everything else works except EMET, the problem is EMET more or less by definition.
As for your suggestion that stale registry keys from no-longer-installed apps could be a problem, first note that this machine is quite young and has had very little of that sort of thing — I’ve maybe uninstalled three things from it, including, most recently, EMET. And second, if EMET causes blue screens if there are stale registry keys lying around, whereas nothing else I’ve ever encountered in a decade of working with NT-kernel Windoze boxes has *ever* done so, then it’s safe to say that that’s a problem with EMET.
In fact, the only blue screens I’ve had on Windoze boxes have come from bad device drivers, hardware problems, really demanding games very infrequently triggering one in a graphics driver, and, one time quite mysteriously, running a MiKTeX-related binary on a Vista box which should have been user-mode stuff utterly incapable of causing one. And now EMET, which has the dubious distinction of managing to trigger *three* of them in as many *hours* before it got put out with the trash.
If it works properly if installed on a factory-fresh Windoze box with nothing else on it, but is prone to make the OS catastrophically unstable when used on a real, live, actually used and lived-in PC with even just a few months worth of accumulated registry cruft, as you are suggesting is the case, then it’s NFG. At best it’s not ready for prime-time, and at worst it looks good on paper but is impractical to make work reliably for all, or a vast majority of, real-world users.
Again, things have change since 10 years ago. Thousands of varying combinations of hardware and software are out there and MS does a great job at trying to keep quality assurance in check. There will invariable be some cases where it just doesn’t work without an update, tweak, or whatnot. This seems to be your case. Not a bad outcome for free software that does work for millions of others, but just not you. I can tell you that I’ve installed and accepted defaults on two win xp boxes today without incident and added firefox too. Both boxes are +3 years old and run fine…you should contact ms about it and file a bug report or something that is more constructive than whining about It and saying how lame it is when it’s obviously a rare isolated issue…(You’re of course entitled, but don’t expect any sympathy from here when you’re just blabbing about the negatives without any constructive feedback or whatnot).
You don’t seem to get it. I, and other users, don’t *want* to have to “tweak” something (what?). Especially not if it’s going to be trial-and-error, without the foggiest clue what might be relevant, and having to wait five minutes for a reboot between each attempt.
We just want it to work.
If major vendors of antivirus products can hook deeply into the filesystem, network, and lots of other things in kernel mode on such a diverse assortment of machines and avoid causing blue screen errors, then a Microsoft product that “only” checks executables for certain behaviors (which AV products also do, at least if they include heuristic detection capabilities), while not doing any of the other stuff AV products do, applied to a specific executable running in user mode, surely should be able to avoid doing so.
Crying me a river about how it’s “difficult” to make these kinds of things not destabilize the OS won’t cut any ice with me. If companies like McAfee can do it, with much more extensive hooking into a closed-source operating system they don’t have the source code to, then that behemoth of a software company, Microsoft, hooking much less extensively and *with* access to the OS source code, *certainly* can.
Now, if there was some simple and obvious adjustment to make that would almost certainly fix it, I *might* try it again. But there isn’t. If there was, someone would have posted it: “Oh, blue screens with EMET? Just turn on/off X or change registry key Y to Z and reboot and it should work”. It’s pretty clear that this isn’t something like that, but rather something that would require futzing about with a debugger or something to even begin to get a handle on, or else days or weeks of just randomly disabling/uninstalling things and rebooting until the problem went away, then adding everything else back but the last thing removed. And I don’t feel like doing either. It seems like it would amount to doing some of Microsoft’s work for them. And I don’t feel like doing *that* unless Microsoft will be cutting me a check afterward.
“Not a bad outcome for free software that does work for millions of others, but just not you.”
Do you have any evidence to support this “statistic”, “me”? Going by the unique names on comments here indicating the results they experienced, the data available to me indicates that it doesn’t work properly OOTB for 6 out of 25 people — “Somebody” getting blue screens, someone else had it blow up Acrobat, a complaint of IE not working (maybe a blessing in disguise there), a complaint of multiple applications not working, a complaint of Foxit not working, and a complaint that it messed up someone’s Java when *un*installed. And several say EMET 3 worked fine for them, but 4 screwed something up, suggesting 4 introduced a bug that 3 lacked.
On the other hand, that 6 out of 25 comes from a small sample size, so take it with a grain of salt.
Still seems likely that the problem rate with this is closer to 1 in 4 than it is to 1 in “millions”, though.
So, anytime a browser (or any other application you run on your computer) triggers a bluescreen, there’s something else at play.
In order to identify the primary culprit (which is usually a driver, but could technically be hardware– it almost certainly isn’t, so let’s assume it’s a driver), there are a few steps you should take:
1. per http://support.microsoft.com/kb/254649/en-gb change the registry key in HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\CrashControl for ‘CrashDumpEnabled ‘ to 0x1
— while in theory there’s a UI for changing this, in practice, I’ve hit a bunch of computers w/ >2gb of ram where the drop down doesn’t offer complete, so it’s just easier to edit the registry than to try to search through and then eventually edit the registry anyway.
2. you can configure `AutoReboot` to your liking.
3. install WinDbg
3a. get the SDK installer from http://msdn.microsoft.com/en-us/library/windows/desktop/hh852363.aspx (don’t worry, the SDK version has very little relation to the OS version, and we’re only downloading the latest version of the Debugger which will work on pretty much any Windows NT computer).
3b. run it
3c. choose to install locally
3d. uncheck everything
3e. check Debugging Tools for Windows
3f. install
4. After your computer blue screens, and you reboot the computer, you should have a file c:\windows\memory.dmp
4a. open a command prompt running as administrator
4b. icacls c:\windows\memory.dmp /setowner %USERNAME%
(if you’re in a domain: %USERDOMAIN%\%USERNAME%)
4c. icacls c:\windows\memory.dmp /grant %USERNAME%:f
4d. rename the file and move it somewhere (e.g. your desktop, or another computer) — the reason is that if your computer blue screens again (this isn’t unlikely, after all it already has once recently), you want to keep the blue screen you were working on.
5. Run windbg (if you’re using a 64bit version of windows, then the x64 version, if not, use the 32bit version) — it’s in the start menu, but on Vista and newer you can do: windbg and then click on the app instead of hunting through the menu
5a. file>open crash dump
5b. browse to the dump file from 4d.
5c. view>command
5ci. .symfix+ c:\symbols
5cii. .reload /f
[wait]
5ciii. !analyze -v -f
[wait]
5d. eventually you’ll get a long report — the report will identify which driver was to blame, take that driver file name and ask the Internet (Google) about it, that will identify the vendor to contact (it won’t be Mozilla).
5e. include the entire output from WinDbg when you contact the vendor. — and don’t delete the .dmp file, eventually once you manage to speak to an actual technical person from that vendor, they’ll probably want the .dmp file.
Note: if you blue screen repeatedly, try the process for a couple of blue screens. In my experience w/ very buggy McAfee Endpoint Security, they had at least 4 different ways to blue screen (i.e. there were at least 4 different crashing modules).
Note that you could probably tickle your blue screen by using the Windows Driver Verifier http://support.microsoft.com/kb/244617 without using EMET. That’s the more official way to identify problems w/ buggy drivers. Basically, it’s sort of like what EMET does to applications, but for drivers. It sticks the OS into a paranoid mode where whenever it does something, it first sets up annotations, and then after the thing happens it validates the annotations — and as soon as it sees that a driver messed up the annotations, the OS will blue screen to let you catch just the right driver right as it was in the act of messing up initially. — If you’re blue screening, this will make you blue screen *much* faster — the value is that it will be faster, much more likely to be repeatable, and the logs from it/windbg will clearly implicate the buggy driver to anyone actually working on the driver — i.e. once you get through the clueless entry level tech support to someone actually familiar w/ their driver code, they’ll actually accept “oh, yeah, that’s us, and oh yeah, Microsoft is implicating us in your Blue Screen, oh yeah, um… maybe we should fix it.” On the “maybe you the vendor should fix it”, don’t hestitate to say “oh, if you don’t fix it, i’m going to take my business to your competitor — who won’t give me blue screens”.
If the buggy driver is your AntiVirus or your AntiMalware, or your Disk Encryption, tell the vendor “i’m looking into switching to Microsoft Security Essentials” http://en.wikipedia.org/wiki/Microsoft_Security_Essentials / “i’m looking into switching to Microsoft Forefront” http://en.wikipedia.org/wiki/Forefront_Endpoint_Protection or “i’m looking into switching to BitLocker Drive Encryption” http://en.wikipedia.org/wiki/BitLocker_Drive_Encryption
— Yes, i’ve lost way too many hours to buggy AntiVirus and Disk Encryption (McAfee is currently on my “do not like list”, although it only recently surpassed SecureDoc.
In particular, the last sentence of this paragraph of the blog article is demonstrably, and catastrophically, wrong in its context:
“To wrap EMET’s protection around a program — say, Mozilla Firefox — launch EMET and click the “Apps” button in the upper portion of the main EMET window. Selecting the “Add Application” button in the next box brings up a program selection prompt; browse to C:\Program Files (x86)\Mozilla Firefox, and then add the “firefox.exe” file. It should be okay to accept all of the defaults that EMET adds for you.”
I’d appreciate a bit more fact-checking before you spout statements like that, from now on. Couldn’t you have tried it with Firefox yourself and seen what happened with “the defaults that EMET adds for you”, before writing that paragraph? Yeesh.
@Somebody — Wrong? What you mean to say is that your experience wasn’t the same. I’m sorry to hear that, but that doesn’t make others wrong. I can assure you I did not experience the same problem as you.
Can you describe what options you selected when you installed EMET? Did you instruct EMET to change any system defaults across the board? That can sometimes lead to the symptoms you describe.
Also, did you try scaling back any of the specific mitigations? In particular, I would try unchecking the ROP mitigation if EMET isn’t playing nice with Firefox.
“Did you instruct EMET to change any system defaults across the board?”
No. Just installed it, with the default options, then added Firefox without changing any of the resulting Firefox-specific checkboxes, then tried to run Firefox. No previous version was installed over, either.
“Also, did you try scaling back any of the specific mitigations?”
If a specific mitigation was triggering falsely, but otherwise EMET was working as it should, the result would only have been to terminate the Firefox process. A BSOD means that EMET was f*cking up kernel-mode stuff in some way. That should not have been happening, even with a false positive triggered by Firefox.
Besides, if it was supposed to BSOD the machine any time it triggered, it would merely mitigate remote code execution exploits down to denial of service attacks that were still severe enough to require a reboot, and not just an application restart. That’s not the advertised level of mitigation. Therefore it was malfunctioning rather than performing as advertised.
There’s something abnormal about your system, Somebody. I set someone’s system up with EMET 4.0 Beta (same mitigations, different UI) and FireFox works fine for them. I ordinarily wouldn’t use FireFox since it lacks some good security tech (e.g. sandboxing, Low integrity mode) but for the sake of verification I installed it on my own rig with EMET 4.0 final and it has no issues. If you feel like investigating, try running FireFox in its safe mode (all extensions disabled).
Hi all, here’s another non-techie question (guess this should be interesting for most non-techies). Most win users probably have installed NET Framework 4.0 Client Profiles. Is this sufficient for a successful EMET 4.0 installation, or will I need to install the complete NET 4.0 framework??
NET Framework 4.0 Client Profiles is not sufficient. What you need is “Microsoft NET Framework 4 Extended” (use Bing to search on that exact string). The EMET installation will fail if you do not have Extended already installed (EMET will give you an option to install that).
Don’t forget to first uninstall any previous EMET version.
Thx a lot for your advice … I’ll do so.
And there are eight large Microsoft Updates which will be available immediately after installing Extended.
I’ll bear that in mind when I do the install, as I too only have .NET 4 Client, not Extended. But I’ll try the EMET install first *without* getting .NET Extended, to see what happens.
This is all I found about .NET on
http://blogs.technet.com/b/srd/archive/2013/06/17/emet-4-0-now-available-for-download.aspx
“If you have EMET 4.0 Beta or EMET 3.5 Technical Preview installed on the system, you will need to uninstall them before installing EMET 4.0, and you will need to remove EMET’s configuration from the registry, by deleting the registry hives HKLM\Software\Microsoft\EMET and, if existing, HKLM\Software\Policies\Microsoft\EMET. If you have EMET 3.0 installed on the system, you don’t need to uninstall it before installing EMET 4.0. The previous version will be uninstalled and at the end of the installation you’ll have the opportunity to migrate the existing settings or to reset EMET configuration with the new default settings.”
“saucymugwump” is absolutely correct. EMET 4 won’t install without .NET 4 Extended, plus the extra 8 .NET updates. And that was the worst part of the whole upgrade process. On a slow PC (mine) the .NET updating took two hours. The EMET upgrade took 5 minutes.
No problems to report so far with programs or browsers, but I’ve gone with the recommended settings. It’ll get interesting when 3rd-party apps start to be included.
No problems with Firefox but EMET didn’t go too well with Chrome in v3 so I’ve left that off the list.
Interesting all in all. I tried it and our Sophos installation immediately flagged every EMET protected executable I launched as having been compromised and threw them into Quarentine Interesting results. At least it is paying attention 🙂
Cheers Brian, I did not know about this. I think the non-tech savvy people that are being intimidated are focusing too much on what EMET does and not how to use it. As you said, it is simply a few clicks to add a new application.
No, it’s not clear what should be added to EMET and what shouldn’t. For example, explorer.exe and msfeedssync.exe are both ‘internet facing’, so should they be added to EMET?
If they should, then why aren’t they part of the default template? If they shouldn’t, then why don’t they need adding, but Windows Media Player does? Or what about Windows Photo Viewer, which runs under dllhost.exe. Should dllhost.exe be added?
That’s the problem. With the exception of just using the built-in templates, how exactly should it be used for maximum effect? Adding applications is easy enough, it’s knowing which ones.
MS picked the bare minimum, but you can add whatever program you feel needs to be added. Btw, explorer.exe is not Internet Explorer (explorer.exe is Windows Explorer — the Windows Shell – while IE is iexplore.exe).
To find out which applications you should add, consider those you use the most. Look in your Windows start menu, or just go to your Program Files folder and perhaps that will jog your memory. Everyone has different programs installed, so it’s really what you use the most.
Earlier today I installed EMET 4 (Windows 7, 64bit), took all defaults (as I always do), so that “C:\Program Files (x86)\Adobe\Reader 11.0\Reader\AcroRd32.exe was protected by EMET. When I tried to open the EMET user guide I saw the cover for half a second and then Acrobat reader stopped (disappeared from memory). Opening AcroRd32.exe is OK, but then opening any pdf file from the reader gives the same effect: half a second a view of the file and the AcrRd32 stops. Uninstalling EMET fixes the problem. Conclusion: no EMET for me.
Or you could uninstall Adobe Reader and install Sumatra PDF instead.
Brian, I just got an “this post is being sent unencrypted etc etc” and ended up with saucymugwumps posting credentials instead of mine displayed in the form fields.
Either the sites software is buggy or I just discovered a bug in the spy ware being applied
@the spyware: Ever heard of forensic data seeding
“ended up with saucymugwumps posting credentials instead of mine displayed in the form fields.”
I tried to post another comment yesterday, but it failed with no error message, just a flash and a re-scroll back to the top. I assumed I had been put on double-secret probation again.
I now believe that the comment software on this site has a major bug or two. Possibly Scott S and I submitted comments at the exact same time, causing his name/email/website form fields to be populated with my data.
Now when someone accuses me of writing something controversial, I can just blame Scott S. 🙂
Bart Simpson: “Hey, I didn’t do it!”
I had the same thing. Although I selected to ‘Use Recommended Settings’ in the configuration wizard, for some reason the Wizard didn’t use ‘Recommended Security Settings’, it used ‘Custom Security Settings’ instead.
At the top of the EMET in the middle under ‘System Settings’, select ‘recommended settings’ from the drop-down list, reboot and Adobe Reader should work.
The guys who monitor Windows Error Reporting data must be wondering what the hell is going on. 🙂
EMET killed my Internet Explorer. IE would crash immediately upon start. when I uninstalled EMET IE worked fine.
IE9 + windows 7 and latest patches.
If there is a problem with EMET and Internet Explorer I’m sure the EMET development team would want to know. I’m not sure if any of them read Brian’s articles, although this one they should be paying attention to. Have you posted to the EMET forum to tell them you encountered a problem with v4?
Same goes for whoever had a problem with Firefox. I haven’t updated yet from 3 to 4, but FF21 has no problems with v3 at least.
While running through your site for an EMET update, my MBAM pro picked out a security.hijack in the registry key and as a not so tech savvy type, thought I should post this.
Also, I have had no issues with this EMET since it was first installed via the article here.
Yes it appears as usual data mining spyware is active and only just started a few hours ago.
Given that Brian has made a few enemies in Russia and China, and with many members of the Jerry Springer generation, it should not surprise us that a cracker is messing with this site. To peruse this site (and many others) I use Firefox with privacy and security settings cranked to “paranoid” including No Script and I kill the browser after each use.
@Sombody, have you ever heard of Chaos theory regarding OS vs applications vs end user? Given the huge diversity in application, software installed, end user knowledge and skills, types of display devices and the plethora of security issues that tags along with it all, it is a “bloody miracle” that anything works at all…
Hello!
Here are some experiences with EMET4.
I installed MET4 under Win7 and Win8 and tested it. Here’s my (current result):
Firefox, Thunderbird, Word,Excel, Powerpoint (2007) stopped working. IE10 on Win7 opened for some seconds and the window closed then. My Antivirus solution told me there’s was a buffer overflow in the apps. The process list shows an unesponsive zombie process for each one. These have to be killed by taskmgr or i.e. pskill. Deactivating antivirus is not a solution as it does not work. So I walked through the config for the apps. Disabling all features for the single apps is not enough. The problem is still there. After removing the apps from the app list everything is running again. Antivirus vendor was able to reproduce the problems and will contact Microsoft.
I had EMET3.0 on the Win7 box before and everything was running fine there even with activated features.
Which antivirus do you have?
I’m running Sophos Antivirus 10.2.
I finally gave up my fear of making the family pc non functioning and installed EMET . All went well until i added foxit, a program i cant do without. it now crashes everytime on startup. And it doesnt show up on list of apps in EMET consul. How can i undo foxit from EMET? Thanks for helping!
“And it doesnt show up on list of apps in EMET consul.”
Open a Windows Explorer shell and open the Program Files (x86) folder. Look for a folder with Foxit in the name. Open that folder and find something with a filetype of Application. That will be the filename you are seeking, with “.exe” for a suffix. I would have guessed that the file would be foxit.exe.
I know the exe file name, it just doesn’t show in EMET so I can remove it from there. The other programs I added like Firefox and chrome are also not there, though they are working fine…
“The other programs I added like Firefox and chrome are also not there”
That was an important clue.
At the risk of being insulting, are you sure you added them properly in EMET? I suggest trying to add them again being very careful to follow Brian’s instructions. I wonder if you forgot to click on the OK button after adding them. One of the things I do not like about EMET is that the add dialog requires a click on the OK button, yet the main dialog has no OK button at all.
The sequence I use is:
-start EMET
-single-click on Apps (at the top)
-single-click on Add Application (at the top)
-find your executable file via the file selection dialog and single-click on it
-single-click on Open
-single-click on OK (at the bottom)
-single-click on the red ‘X’ at upper right
You should see a message to the effect that a restart of the application may be necessary.
Brian, here’s my experience with EMET 4.0. After installing yesterday on my Windows 7 OS it began clocking all day. Since this was no impact I left it. This morning I uninstalled EMET and voila! – it blew up everything Java – which my primary security tools depend on. I’m still trying to fix it as reinstalling Java is not the answer. I can’t work unless I have Java working. Wow! There goes my day!
This sounds like a great program to better protect either Internet Explorer or any third party browser , but I am a little hesitant on installing something like this without doing some serous research first
According to https://social.technet.microsoft.com/Forums/security/en-US/cec4aaeb-d513-48ab-a816-356ff2a2cf63/i-experienced-a-blue-screen-on-my-windows-7-it-said-there-memory-dump-disk-100, “EMET does not touch any kernel memory and should not bluescreen a machine.”
According to https://social.technet.microsoft.com/Forums/security/en-US/e532774d-9325-4b59-acb0-c51c61f71f78/emet-and-system-stability, “if you don’t change the system mitigation defaults and only use EMET to configure a subset of the applications on your system, there will be no side effects to other applications on any of the supported OS”.
The latter claims to be from “The EMET Team”.
However, on my W7-64 box it caused multiple BSODs after clean installing it without changing the system mitigation defaults, contrary to both of those claims. I ended up uninstalling it as a result.
Anybody know anything else about this? Can’t say I’m really all that surprised that MS employees would misunderestimate how much and how badly one of their products might affect things when it screws up, though.
With a new laptop, W8 Pro, we experienced system break on boot. From kernal to user-land the desktop did not load due to the prevention of System Event Notifier from starting as it should automatically. Audit mode is what we will try for some time.
First I’d like to say this is an excellent article thank you.
I only wish I’d read it before installing v4 then I might have known to uninstall the previous one first- shame I didn’t find this out when looking through Microsoft’s blurb!
For those of you whom may be a little overwhelmed, please don’t be. Whilst I may be somewhat of an expert home user, I’m far from being a geek, and let alone a level 4 geek. And I’ve been using EMET since version 2.
Ignoring most of the jargon it’s no more difficult than spending an hour sorting out your bookmarks.
Thanks again, especially for the helpful links which I shall now use to troubleshoot a couple of irritating bugs I’m experiencing. These are only to do with the settings and privilages for the tray icon though…
Found some interesting notes on EMET 4.0 and ROP mitigations on 64 bit processes in this article (see more below in the text)
http://www.cert.org/blogs/certcc/2013/06/microsoft_exchange_and_oracle.html
May be someone more tech savvy than me could explain, if these shortcomings of EMET might have implactions on e.g. IE10/64x protection (or is it just a secific problem of the setting described in the beginning of the article?) .
I’d like to add another, more general question but still in context. We’ve meanwhile all learned that EMET is heavily dependant on the .NET framework, the latter showing up all kinds of vulnerabilties pretty frequently. Isn’t this a principle threat to EMET’s reliabilty? Would there have been different ‘engineering choices’ at all in order to circumvent this basic problem?