Last week’s article about how to prevent CryptoLocker ransomware attacks generated quite a bit of feedback and lots of questions from readers. For some answers — and since the malware itself has morphed significantly in just a few day’s time — I turned to Lawrence Abrams and his online help forum BleepingComputer.com, which have been following and warning about this scourge for several months.
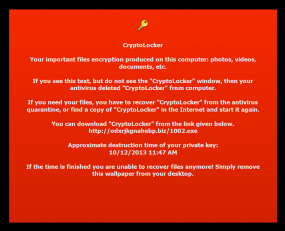
This message is left by CryptoLocker for victims whose antivirus software removes the file needed to pay the ransom.
To recap, CryptoLocker is a diabolical new twist on an old scam. The malware encrypts all of the most important files on a victim PC — pictures, movie and music files, documents, etc. — as well as any files on attached or networked storage media. CryptoLocker then demands payment via Bitcoin or MoneyPak and installs a countdown clock on the victim’s desktop that ticks backwards from 72 hours. Victims who pay the ransom receive a key that unlocks their encrypted files; those who let the timer expire before paying risk losing access to their files forever.
Or, at least, that’s how it worked up until a few days ago, when the crooks behind this scam began easing their own rules a bit to accommodate victims who were apparently willing to pay up but simply couldn’t jump through all the hoops necessary in the time allotted.
“They realized they’ve been leaving money on the table,” Abrams said. “They decided there’s little sense in not accepting the ransom money a week later if the victim is still willing to pay to get their files back.”
Part of the problem, according to Abrams, is that few victims even know about Bitcoins or MoneyPak, let alone how to obtain or use these payment mechanisms.
“We put up survey and asked how many [victims] had paid the ransom with Bitcoins, and almost no one said they did, Abrams said. “Most paid with MoneyPak. The people who did pay with Bitcoins said they found the process for getting them was so cumbersome that it took them a week to figure it out.”
Another major stumbling block that prevents many otherwise willing victims from paying the ransom is, ironically, antivirus software that detects CryptoLocker — but only after the malware has locked the victim’s most prized files with virtually uncrackable encryption.
“Originally, when antivirus software would clean a computer, it would remove the CryptoLocker infection, which made it so the user could not pay the ransom,” Abrams said. “Newer versions change the desktop background to include a URL where the user can download the infection again and pay the ransom.”
The idea of purposefully re-infecting a machine by downloading and executing highly destructive malware may be antithetical and even heresy to some security pros. But victims who are facing the annihilation of their most precious files probably have a different view of the situation. Abrams that said his testing has shown that as long as the registry key “HKCU\Software\Cryptolocker_
“Some antivirus companies have been telling victims not to pay the ransom,” Abrams said. “On the one hand, I get it, because you don’t want to encourage these malware writers. But on the other hand, there are some companies that are facing going out of business if they don’t, and can’t afford to take the holier-that-thou route.”
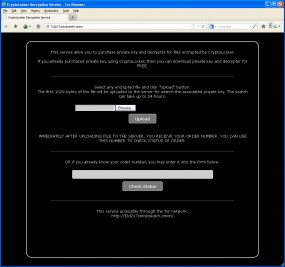
CRYPTOLOCKER DECRYPTION SERVICE
On Friday, Nov. 1, the crooks behind this malware campaign launched a “customer service” feature that they have been promising to debut for weeks: a CryptoLocker Decryption Service. “This service allow [sic] you to purchase private key and decrypter for files encrypted by CryptoLocker,” the site reads. “Customers” of the service can search for their “order number” simply by uploading any of the encrypted files.
“They’re calling it an ‘order,’ as if victims posted an order at Amazon.com,” Abrams said.
“If you already purchased private key using CryptoLocker, then you can download private key and decrypter for free,” explains the service, which is currently hosted at one of several addresses on the Tor anonymity network. The decryption service site is not reachable from the regular Internet; rather, victims must first download and install special software to access the site — yet another potential hurdle for victims to jump through.
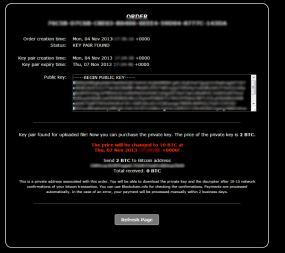
According to Abrams, victims who are still within the initial 72-hour countdown clock can pay the ransom by coughing up two Bitcoins — or roughly $200 using a MoneyPak order. Victims who cannot pay within 72 hours can still get their files back, but for that unfortunate lot the ransom rises fivefold to 10 bitcoins — or roughly USD $2,232 at current exchange rates. And those victims will no longer have the option to pay the ransom via MoneyPak.
Abrams said the service exposes two lies that the attackers have been perpetuating about their scheme. For starters, the bad guys have tried to dissuade victims from rolling back their system clocks to buy themselves more time to get the money together and pay the ransom. According to Abrams, this actually works in many cases to delay the countdown timer. Secondly, the launch of the Cryptolocker Decryption Service belies the claim that private keys needed to unlock files encrypted by CryptoLocker are deleted forever from the attacker’s servers after 72 hours.
DETECTING AND PREVENTING CRYPTOLOCKER
Last week’s story pointed to two tools that can help block CryptoLocker infections. Individual Windows users should check out CryptoPrevent, a tiny utility from John Nicholas Shaw, CEO and developer of Foolish IT, a computer consultancy based in Outer Banks, N.C. Small business administrators can avail themselves of a free tool from enterprise consulting firm thirdtier.net, which recently released its CryptoLocker Prevention Kit. This comprehensive set of group policies can be used to block CryptoLocker infections across a domain.
As this scam illustrates, relying on antivirus software alone to protect you from attacks is foolhardy. Also, it’s vitally important not only to have a backup plan for when a malware or hardware disaster strikes, but also in the event of nasty attacks like this one. For example, backing up your files to a removable or network drive is a great idea, but one added layer of protection against attacks like this is to perhaps disconnect those drives when you’re not backing up your data.
Also, I hope it’s clear that tools like CryptoPrevent and antivirus are no substitutes for common sense. Threats like these are opportunistic, and as with many modern threats your best protection against them is to employ basic online street smarts: Street smart rule #1 is don’t blithely open attachments in emails you weren’t expecting, even if they appear to come from someone you know.
For other tips on keeping your data and computer safe, see my tutorial — Tools for a Safer PC. While many of these CryptoLocker attacks have been perpetrated via cleverly disguised malicious email attachments, there are indications that this malware is being disseminated via networks of PCs that have already been hacked through other methods. Abrams said many recent CryptoLocker attacks have actually started with infections from the ZeuS or Zbot banking Trojan, which is then used to download and install CryptoLocker.
“If you’re really lucky, your system may also get [the spam bot] Cutwail installed on there as well and start spamming,” Abrams said.
For more information on this threat, see BleepingComputer.com’s CryptoLocker Ransomware Information Guide and FAQ.




If I use a program such as TruCrypt to create an encrypted partition on my hard disk and copy all of my important data there, would that be considered a good safeguard?
From what I read on the 1st article on this threat, I don’t think that would work. Much easier to simply install Crytoprevent by Foolish IT.
However, some have questions whether password protecting a folder or network share would prevent it; and that question was not fully answered, that I recollect. Someone may have addressed that issue by now.
I believe it would provide protection provided the partition is not mounted at the same time you are infected since the data is not unable to be accessed when it isn’t mounted.
If the partition was mounted at the time you are infected then it would not provide protection since it is just like any other drive as far as your OS is concerned.
Further from what I understand about this malware if you made a Truecrypt container and associated it with Truecrypt (which I think is the default behaviour) then the container would be encrypted by Cryptolocker as it encrypts any file that has a program associated with it.
I think it will just double encrypt everything? Your encrypted files will be crytplocker encrypted as well lol. I think Steve Gibson also addresssed this question on his podcast called security now. (but you knew that 😉
Every business should be backing up often to drives not on their network. For example accountants I have worked for back up their current work a couple times a day and have archives on disks for years. They would have to get physically robbed.
So the NT6 NTFS system of password protection is worthless! Interesting. 😐
Even easier to ask your congressman to push for a drone strike against the creators of it : )
Get them labeled as terrorists …then one day .. they will be picnicking with their family and out of the clear blue sky.. a predator drone.
What’s to stop the malware from encrypting the truecrypt container?
I would suggest as mentioned in the article, create a “backup to disk” solution (USB, NAS or what-have-you) and disconnect from the PC when not backing up. Or Skydrive for that matter, then you know NSA will do the backup for you 🙂
The “how often” question depends on how much data one can recreate in case of emergency.
Backup is always a good answer no matter what the question is.
>If I use a program such as TruCrypt
It won’t help. As others said, when the TrueCrypt partition is mounted, it’s vulnerable.
A bit of additional caution, if you use a keyfile with an extension CryptoLocker targets — like SomeInnocousName.doc — and you don’t have it backed up, now your keyfile has been encrypted and you can’t get mount the TrueCrypt filestore.
——————-
We had this hit a laptop at work. It looks to me like it was an escalating cycle of malware beginning with search toolbars that began with almost two weeks before CryptoLocker infected the laptop.
Infection vector was about 90% poor user attitude — probably the same type of personality who’ll sleep around without using a condom. Can’t be bothered to think critically about what he’s clicking on, and it’s someone else’s fault if anything bad happens. Installed Malwarebytes on his laptop as some additional protection.
8,205 files affected, we were able to restore all from our backups (and happily, from disk based backups so I didn’t have to make a trip to load tapes at the data center). The infection was active for ~2 hours one morning until the laptop went to sleep, then McAfee disinfected it upon waking.
For the files on the network share affected, it changed the ownership as it encrypted, so after I restored backups to an alternate directory our offshore team compared ownership and copied over the files that had changed to being owned by the infected user overnight (and any he previously had owned.)
I hate assigning manual work like that, but I didn’t have time to export the registry key, transform it into a batch program, and proofread it before running it to restore the affected files.
Opened files weren’t impacted, and most files that were infected were historical in nature so the business wasn’t impacted at all other than IT spending about 40 man-hours on recovery and investigation.
My clients are as flabbergasted that there is a preventive measure as they are in the original threat! Great coverage here!
CryptoPrevent has been updated to version 4.0 (2013.11.05 @ 2056).
If the correctly loged in user does not have change rights to the file does that keep it from being deleted, or does this attack use other vulnerabilities to escalate privileges?
I have to continue cleaning up share permissions on our NAS. This is a great excuse to set that time aside on my agenda.
@Andy, no it did not have any escalation of rights in the version I saw running, It could only see in context of the logged on user.
Unfortunately in my case this particular user had escalated rights on a network share. Lot’s of restoring and checking.
The code ran through the directory in alphabetical order, which helped in the forensics a bit. It also appeared to select files based on a preference table of some kind. Hitting office stuff first then JPG and less important extensions like mp3.
Finally a great malware that punishes naivety, ignorance while raising awareness.
One can only hope, that you’ll never fail , any time, in life. Failing is human, however, so it’s likely you’ll fail. If you do, you better pray it’s not in front of a computer with all your assets – and no backup.
@Torchin
“Finally a great malware that punishes naivety [sic], ignorance while raising awareness.”
Spoken like a truly elitist sociopath.
@Diane
False, I just have enough experience to know that getting kicked in the ass once make you think twice and raise awareness much better than AV scams.
@Torchin,
We are in the times when NBC.com installs malware on peoples machines, just by visiting the url and not having to click on anything.
But when your not very active on your pc… Meaning you don’t do anything but go to the same couple unpopular websites, never install anything, or just play with yourself offline you probably have nothing to worry about. (I don’t know why some people even own a pc)
I feel bad mostly for the kids. IMO, its people like you and these malware creators that are really taking away our freedoms and potentials.
Not the NSA.
Install Linux, Luke
Why install Linux? It’s crap. Most open source software is crap.
@Gene,
Sir You totally impressed me today by making such uninformed, blatantly false statement.
@CoolAC
If you have been infected by visiting the NBC’s website simply by browsing their pages it means that your browser or its add-ons have issues.
The kids here have no issues with malicious softwares, but that’s maybe because they do not use deprecated and defective be design operating system although I am pretty confident that if they would run something such as Microsoft Windows they won’t have problems too.
I can also say that it is because of people like you, casual users, that we today have freedom restrictions, incoherent laws and censorship.
It can be also said that it is because of people like you, facebook.com youtube.com users that we have centralization and corporations able to coerce others.
Sure. I guess. If by issue you mean unpatched exploit.
I bet you’re still going to blame the user for carrying out (or not carrying out) some action though right.
You mean CBS? CNET sucks! 🙁
No one says you have to surf the web with your most trusted device. if your intent is to surf, buy a el-cheapo laptop or other device and use that specifically for that purpose. Then if the system gets whacked, simply insert the installation disk, slick the drive and partitions. Reinstall the partitions and install the software and your back online.
A laptop, especially this time of the year near the holiday season can be found quite cheap. It saves your more important files from getting jacked up by these micreants. It is only a matter of time before these morons, like many other – are yanked from their comfort zone and put in front of a judge.
Bulletins like this should be part of a weekly podcast. I want to listen to essays like this on internet radio networks like: The Micro Effect, Republic Broadcasting, The Rense Radio Network and Liberty Broadcasting.
Back up your important files to a cloud storage site not in the United States and make sure your files are password protected and encrypted that are not affected by the CryptoLocker file extension list
My friend lost her files that were stored on DropBox. To other users viewing into the shared files, it looked like she was logged in an systematically editing every file.
DropBox was able to recover most of them, but only after she reformatted the infected computer so it would stop re-encrypting things.
I have an XP desktop and an W7 laptop. Wouldn’t running them in Limited (Restricted) mode without Admin privileges while online by itself prevent this payload from launching and encrypting my files?
No. It would prevent it to encrypt other users’ files (if there are multiple people who work on this PC), but not yours.
Also checkout HitmanPro.Alert 2.5 with the new feature CryptoGuard. See also http://www.surfright.nl/en/cryptoguard
”
HitmanPro.Alert 2.5 contains a new feature, called CryptoGuard that monitors your file system for suspicious operations. When suspicious behavior is detected, the malicious code is neutralized and your files remain safe from harm.
CryptoGuard works silently in the background at the file system level, keeping track of processes modifying your personal files. CryptoGuard works autonomously, so no user interaction is required.
To protect your files from being taking hostage, simply download and install HitmanPro.Alert.
CryptoGuard is part of HitmanPro.Alert 2.5 (or newer) and supports Windows 8, XP, Vista and 7 (32-bit and 64-bit).
“
Thanks WSPU. I went to the site, and couldn’t see any information on compatibility with other solutions. Wouldn’t this particular utility clash with Comodo Defense + or say – Rapport? Just curious. I assume this application runs at the kernel level, maybe not?
Lots of articles and information about cryptolocker but nary nothing about the criminals behind it.
@Canuck, I think you’ll see some movement on this front shortly. Stay tuned.
Go get ’em Brian!
Cryptolocker… at last, a way to protect your files from the NSA.
HA!HA! Good one Doogie! 😀
Do I just not understand BitCoins, but since they are essentially code, wouldn’t they be traceable if they were converted to cash?
Since you’re not familiar with bitcoins, you aren’t familiar with “washing services” either. So no, if you know what you’re doing. Even if you don’t, tracing the V2P conversion is near impossible.
these guys need to experience the “Slice of Life”
@Torchin,
You have to be really arrogant and delusional nowadays to think that even experienced and careful pc users can’t get infected.
Especially when sites like NBC.com get infected and install malware on a users computer without having to click anything. Just visit the URL on sites nowadays and your infected. And it doesn’t have to be a porn or pirate site.
Basically it just depends on how active you are on your pc. If you don’t do anything on your computer but go to the same couple websites everyday, never install anything, or just play with yourself offline…..you probably don’t have to worry.
IMO, its people like you and these malware creators that really take away our freedoms online, not the NSA.
I disagree. If you don’t allow NBC.Com to run scripts, you won’t have these problems. I do not allow CDNs to script, and I never get infected.
The problem is, you have to allow scripts for certain things on a website to work.
Why should people limit their experience, or miss out on info, especially on a major website? Again, I don’t think the NSA is limiting anybodies experience anywhere near what these malware creators do…
So this stuff is a little bit more, how to say – Nasty than ealier this year? I found an article online a while back alerting the staff here of the potential issue about this heap. BACK THEN, the crypto was easily cracked by some one knowing their way around powershell. It even gives the command lines;
March 05, 2013 Security researchers have discovered a novel ransomware scheme that uses Windows PowerShell to encrypt files on a victim’s computer.
After encrypting the files, it holds them hostage, demanding payment of a ransom to unlock the data.
PowerShell is a scripting language Microsoft bundles with Windows 7, although it works on other versions as well, and is typically used by administrators to automate tasks used to operate a Windows network.
Researchers at security software maker Sophos, describe how the attack, directed at Russian users, works: A spam message delivers two malicious scripts to a machine. The first script checks the system to see if PowerShell is installed. If it isn’t, it will fetch a copy from a Dropbox account and install it.
The second script starts encrypting files with PowerShell. Some 163 file types are targeted — documents, spreadsheets, images, videos — anything in which a person might keep valuable information.
After the script has done its dirty work, it displays a message telling the user that their files have been encrypted, and they need a code to unlock them.
To obtain the code, the user has to pay the attacker 10,000 Rubles (about $360).
However, the researchers discovered that the files can be decoded without paying the ransom. That’s because the code can be retrieved by using the application that encrypted the files: PowerShell.
The ransomware uses either one of two types of encryption keys. One uses a UUID as the encryption key; the other, a randomly generated key that’s 50 characters long.
*******The UUID key can be obtained by typing this statement into PowerShell: Get-wmiobject Win32_ComputerSystemProduct UUID. ******
The randomly generated key can be retrieved with this statement: wmi win32_computerSystem Model.
While the ransomware scheme is easy to crack for someone who knows their way around PowerShell, it would be effective against most casual computer users.
Yeah, I got a heads up a while ago, but the criminals just keep ahead of the game! Eh?
If the NSA can’t even provide the necessary intel to shut down the CryptoLocker malware crooks (who are using domain names, servers, accepting ransom payments, etc.), then WTF is the point of having the NSA at all?
I’m sure the NSA knows exactly who the CryptoLocker Crew is and where they are. Why even TOR couldn’t mask the identity of the Silk Road guy, and what a buffoon loser he is. It’s only a matter of time. Then it’s Drone-ville for them.
Or it’s the NSA that’s been doing it all along. And that wouldn’t surprise me in the least. That’s just how they operate. Just like cowards.
Or its Unit 61398 A Chinese cyber espionage unit on the outskirts of Shanghai, and if that’s the case. MS, NSA, CIA, FBI, nor any US administration present or future will do diddly squat about it, because, this is how they’re going to let them recoup some portion of their billions in the us borrowing from the Chinese.
Another possibility is that it’s the Israelis’, and this is payback for that Snowden duffus and more importantly, the STUXNET FusterCluck admission.
Either way, you’ve just got to be smarter than your devices. Turn them off and go outside. They’re useless and nothing more than a diversion from your family and your life. Sad to see so many people being sucked into this calamity of digital BS.
Life is short, and then you die. It’s just that simple.
Move along, there’s nothing to see here folks.
The NSA is too busy gathering worthless meta data on innocent citizens to do anything worth while! HA!
Are you kidding? The NSA is too busy chasing political enemies to actually focus on any problems, domestic or otherwise! ]:)
Thats a super hero style statement. NSA is mainly for the protection of USA based assets. They shouldn’t ( notice I did not say can’t) have the rights to go into computers that are out of their area of responsibility and mess with them. For the reality side of the house, no one knows for certain if any other state sponsored party has poisoned the systems the hackers own, and they are colecting evidence on the miscreants as we speak.
With the Secret Service, FBI and others swarming in on the Silk Road issue, they were able to recover a significant number of bitcoins, which, in my opinion, they should throw a “handful” of those over to Krebs for breaking the story – even if the Feds knew about it earlier – Krebs still made them spring into action, and off the doughnuts and couches.
I think the law enforcement has learned over the years to have an over whelming amount of evidence available in order to get a conviction. Sometimes these events may take longer than people want them to, and in the end, the sentences may be light.
BUT, on the other side, the Feds may have harvested a LOT of information about other bad people and have a baseline of information, and may monitor / prosecute them over time as well.
Yes, all true, but i’m a simple man and abide by the rule of my countries laws. these are changing times, just as they were in the 1930’s. i’ll be honest. i don’t trust anyone, other than my family or very close friends. computers and teh interwebs is the vehicle of criminals today. there’s no denying it. our Rome will soon collapse too. that’s just history repeating itself.
Super hero statement, no. just a life of human observation.
…as I go back to my computer to observe more…Wow
It really is like watching a train wreck.
Respectfully
Flipping A tweetie Dexter! O:)
I’m sure the NSA knows exactly who the CryptoLocker Crew is and where they are. Why even TOR couldn’t mask the identity of the Silk Road guy, and what a buffoon loser he is. It’s only a matter of time. Then it’s Drone-ville for them.
Or it’s the NSA that’s been doing it all along. And that wouldn’t surprise me in the least. That’s just how they operate. Just like cowards.
Or its Unit 61398 A Chinese cyber espionage unit on the outskirts of Shanghai, and if that’s the case. MS, NSA, CIA, FBI, nor any US administration present or future will do diddly squat about it, because, this is how they’re going to let them recoup some portion of their billions in the us borrowing from the Chinese.
Another possibility is that it’s the Israelis’, and this is payback for that Snowden duffus and more importantly, the STUXNET FusterCluck admission.
Either way, you’ve just got to be smarter than your devices. Turn them off and go outside. They’re useless and nothing more than a diversion from your family and your life. Sad to see so many people being sucked into this calamity of digital BS.
Life is short, and then you die. It’s just that simple.
Move along, there’s nothing to see here folks.
I don’t understand why governments don’t consider this terrorism and go get them. Think of all the money that could be made by finding them and executing them on pay-per-view. Unless of course this IS some government somewhere… The same punishment should apply in that case.
From Today Money:
“It’s the same type of encryption used in the commercial sector that’s approved by the federal government…”
And it’s intellectual sloth to think some poor person’s naivety has earned them this. That’s the equivalent of some auto mechanic saying “Well, you own a car, if you don’t know how to rebuild an engine your a fool for owning a car or driving the roads.” Not everyone that owns a computer is tech-savvy, they simply don’t want to be left out of the 21st century. Not every rich person that owns a Lear Jet knows how to fly or repair it. I deal with people every day that are NOT a+ certified, but still own a PC. The level of expectation with owning a PC is you can use it well enough to do on a consumer level what the machine was made for. Not every person that uses one recognizes a threat when it happens because some are so innocuous looking they fool people, and anyone that thinks an antivirus is 100% protection is strongly misinformed. As someone mentioned here, if you derive some sadistic pleasure from people getting ripped off by criminals for not knowing they were being preyed upon, you’re most likely an undiagnosed sociopath.
This is criminal activity, and they need to be dealt with as such.
Would back up on a flash drive protect ones files?
Thank you in advance…
If left unattached (unplugged) then yes. If the drive is connected, the malware will encrypt it too.
someone should take the time to hunt down the beneficiary to these funds and place 2 taps to the head
I’ve installed CryptoPrevent on all the machines at my house. However, im still wondering if i had not installed CryptoLocker, how could i have protected my NAS drive in case one one the computer did get infected.
Mount your drives in read-only and give write permissions to a machine which is safe.
Keep your Operating System up to date and read the changelogs.
Avoid proprietary softwares or run them in a restricted environment.
Hopefully Torchin – but no one has satisfactorily answered any of my questions on these traditional solutions so far. I may be that the developers of the free CryptoPrevent, were just trying to take advantage of FUD to eventually sell their centrally managed solution.
The old adage, “back up, back up, back up your files regularly” certainly applies here.
How long do you think it will take before a mac version of this comes out?
Never,there is no exploit for MAC OS yet .
Yeah! Just keep that head in the sand! We’ll understand! My brother is a Mac head and he as already seen plenty of traditional problems, just like Windows systems. Only they seem like early DOS days! None-the-less, they are a reality!
Ransom will go up , nothing will change .Its so lucrative.Mama Mia padre .
Orele! :v
Watch me . 1000 $ a pop sounds fair .Bitcoin going ballistic right now too .
@Hans
Any backup drive is good as long it is not connected when the infection hits. Do your backups, pull the flash drive out. Done. Any drive connected (USB, NAS, etc…) will be scanned and targetted files on that drive encrypted.
What happens when they start to use time delay, 2 weeks out, 1 month out? We need quad based rotating drives.
Why this ransomware is being considered as something new? I really don’t understand.
The news about it go back at least to 2006:
http://news.techworld.com/security/5892/ransomware-trojan-demands-cash/
http://news.techworld.com/security/9512/new-wave-of-ransomware-hits-pcs/
http://news.techworld.com/security/101710/av-firm-seeks-help-cracking-ransomware-key/?intcmp=nws-af-rtd-home
True Anatoly, but this is the 1st time it has exhibited worm or virus behavior, where it can infect an entire LAN! I would hope paying attention to a plain old HIPS would suffice, but then I’m not really an egg head on these things.
I really doubt that nobody in 7 years have created a crypto ransomware with a LAN-worm functionality.
Even if not so, as far as i know, the majority of CryptoLocker’s installations come from opening email attachements.
And btw, i can’t find an information about this kind of functionality in Cryptolocker, could you please point me to it?
Just read the article – sounds like it to me!
I’ve read both of Brian’s articles on the topic, along with multiple articles on the web, and i can’t remember any mention of LAN-specific distribution mechanism.
I think this Brian’s quote underlines the propagation:
According to reports from security firms, CryptoLocker is most often spread through booby-trapped email attachments, but the malware also can be deployed by hacked and malicious Web sites by exploiting outdated browser plugins.
>End of quote<
The only network-specific action is encrypting files in shared folders.
It is new because it uses a Public/Private Key encryption process instead of using an symetric key which can be decrpyted much easier with comparing an original file from the backup with an malware encrypted one.
http://www.securelist.com/en/blog/208214109/Cryptolocker_Wants_Your_Money
In the past, we have witnessed similar malware like the famous GPCode that used RSA keys for encryption. Back in 2008, we cracked the 660 bit RSA key used by GPCode and provided the victims with a method to decrypt and recover their data. Later, the GPCode authors upgraded the RSA key to 1024 bits, putting it perhaps only in the realm of NSA’s cracking power.
>End of quote<
I don't think the usage of PKI should be an argument for creating a new category of malware. It's still encrypting files without any reasonable chance of restoring them.
great information and really helpfull to protect your hard disk from nsa.
thanks for sharing