Microsoft warned today that attackers are targeting a previously unknown security vulnerability in some versions of Microsoft Office and Windows. The company also has shipped an interim “Fix-It” tool to blunt attacks on the flaw until it has time to develop and release a more comprehensive patch.
 In a post on its Technet blog, Microsoft said the attacks observed so far against the vulnerability have been “carefully carried out against selected computers, largely in the Middle East and South Asia.” It added that the exploit needs some user interaction because it arrives disguised as an email that entices potential victims to open a specially crafted Microsoft Word attachment.
In a post on its Technet blog, Microsoft said the attacks observed so far against the vulnerability have been “carefully carried out against selected computers, largely in the Middle East and South Asia.” It added that the exploit needs some user interaction because it arrives disguised as an email that entices potential victims to open a specially crafted Microsoft Word attachment.
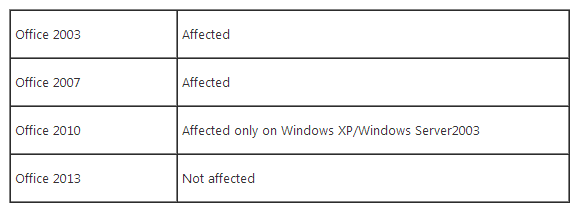
The exploit attacks an unpatched security flaw in the way some older versions of Office and Windows process graphical images. According to Microsoft, the exploit combines multiple techniques to bypass exploit mitigation techniques such as data execution prevention (DEP) and address space layout randomization (ASLR). The company says this exploit will not affect Office 2013, but will affect older versions such as Office 2003 and Office 2007.
“Due to the way Office 2010 uses the vulnerable graphic library, it is only affected only when running on older platforms such as Windows XP or Windows Server 2003, but it is not affected when running on newer Windows families (7, 8 and 8.1),” Microsoft wrote.
Microsoft’s latest Fix-It tool should help blunt attacks on this vulnerability. Also, while this particular exploit does try to evade DEP and ASLR protections, it’s probably as good a time as any to remind readers about Microsoft EMET, a free tool that can increase the security of third party applications that run on top of Windows.
Interestingly, news of the exploit surfaced less than 48 hours after Microsoft announced it would expand its $100,000 bug bounty program for researchers who can find and report novel exploitation techniques for evading Windows’ built-in defenses.




Office 2011 for Mac isn’t listed. Am I safe to assume the Mac version of Office isn’t affected by this?
My understanding is the vulnerability lies in a certain combo of Windows and Office, so, no. Also, Mac versions are not listed among those versions of Office that are vulnerable.
https://support.microsoft.com/kb/2896666
Got ‘er done! Thanks Brian! 🙂
Brian, I interpret the MS security advisory’s list of affected software as more than just Office 2003/2007 as your original post implies — the list specifically includes several versions of OS including Vista SP2 (both 32-bit and 64-bit) and Server 2008 (looks like all flavors), plus the Lync 2010 and 2013 communications software (again, looks like all flavors). In other words, if a user is running any one of the items reflected in the affected list, the FixIt patch should be applied — correct?
Now there is a “perfect storm” for next April when security updates end for Microsoft XP that have Office 2007 and 2010 installed.
I can see it now the black hole malware tool kit with this zero day exploit targeting Windows XP machines all over the world next spring.
How many Microsoft XP users who don’t install security updates will evetually get nailed by either a drive by download (IFRAME) or by way of a Blackhole exploit kit through a email attachment?
Only time will tell.
MS writes in its advisory
“An attacker could exploit this vulnerability by convincing a user to preview or open a specially crafted email message”
Well, to me that does not match to another information by MS which says
“the exploit needs some user interaction”
Given an Outlook client with preview pane…does a user still need to do something here? Or isn’t the receipt of a specially crafted email with active preview pane enough here?
Cheers
Claus
ok…you need MS Word as default email reader
Oooh, I wonder if a certain ex-boss of mine, who always insisted on using Word as his email reader despite warnings from everyone remotely technical in his life (even his wife!), has been infected.
One can only hope.
At least this exploit needs some user interaction not remote.
FYI:
EMET running on XP can disable the manual Windows update. It looks like it blocks part of the validation; but iexplorer reliably crashes during that portion. Removing EMET restores the update function.
EMET has enough granular control, that you can generally get it working on any operating system – but I found I had to uncheck all protections on IE9 because it interferes with Rapport’s protection schema. I still run EMET for everything else on the local machine, just not for IE9 on Vista Ultimate x64.
I’ll have to look into that for my XP machines, but I have auto-updates turned on.
So if I’m understanding this correctly face book, adobe, and windows have all had a security breach and the only company that bothered to tell me was adobe? How do we fix all of these? Change all passwords?