Last week’s article about how to prevent CryptoLocker ransomware attacks generated quite a bit of feedback and lots of questions from readers. For some answers — and since the malware itself has morphed significantly in just a few day’s time — I turned to Lawrence Abrams and his online help forum BleepingComputer.com, which have been following and warning about this scourge for several months.
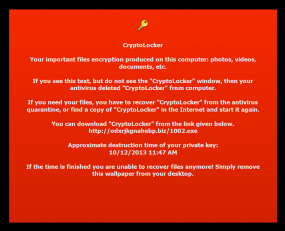
This message is left by CryptoLocker for victims whose antivirus software removes the file needed to pay the ransom.
To recap, CryptoLocker is a diabolical new twist on an old scam. The malware encrypts all of the most important files on a victim PC — pictures, movie and music files, documents, etc. — as well as any files on attached or networked storage media. CryptoLocker then demands payment via Bitcoin or MoneyPak and installs a countdown clock on the victim’s desktop that ticks backwards from 72 hours. Victims who pay the ransom receive a key that unlocks their encrypted files; those who let the timer expire before paying risk losing access to their files forever.
Or, at least, that’s how it worked up until a few days ago, when the crooks behind this scam began easing their own rules a bit to accommodate victims who were apparently willing to pay up but simply couldn’t jump through all the hoops necessary in the time allotted.
“They realized they’ve been leaving money on the table,” Abrams said. “They decided there’s little sense in not accepting the ransom money a week later if the victim is still willing to pay to get their files back.”
Part of the problem, according to Abrams, is that few victims even know about Bitcoins or MoneyPak, let alone how to obtain or use these payment mechanisms.
“We put up survey and asked how many [victims] had paid the ransom with Bitcoins, and almost no one said they did, Abrams said. “Most paid with MoneyPak. The people who did pay with Bitcoins said they found the process for getting them was so cumbersome that it took them a week to figure it out.”
Another major stumbling block that prevents many otherwise willing victims from paying the ransom is, ironically, antivirus software that detects CryptoLocker — but only after the malware has locked the victim’s most prized files with virtually uncrackable encryption.
“Originally, when antivirus software would clean a computer, it would remove the CryptoLocker infection, which made it so the user could not pay the ransom,” Abrams said. “Newer versions change the desktop background to include a URL where the user can download the infection again and pay the ransom.”
The idea of purposefully re-infecting a machine by downloading and executing highly destructive malware may be antithetical and even heresy to some security pros. But victims who are facing the annihilation of their most precious files probably have a different view of the situation. Abrams that said his testing has shown that as long as the registry key “HKCU\Software\Cryptolocker_
“Some antivirus companies have been telling victims not to pay the ransom,” Abrams said. “On the one hand, I get it, because you don’t want to encourage these malware writers. But on the other hand, there are some companies that are facing going out of business if they don’t, and can’t afford to take the holier-that-thou route.”
CRYPTOLOCKER DECRYPTION SERVICE
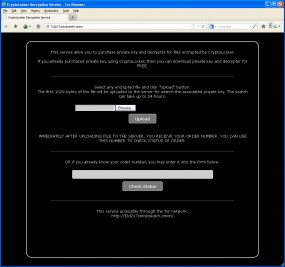
On Friday, Nov. 1, the crooks behind this malware campaign launched a “customer service” feature that they have been promising to debut for weeks: a CryptoLocker Decryption Service. “This service allow [sic] you to purchase private key and decrypter for files encrypted by CryptoLocker,” the site reads. “Customers” of the service can search for their “order number” simply by uploading any of the encrypted files.
“They’re calling it an ‘order,’ as if victims posted an order at Amazon.com,” Abrams said.
“If you already purchased private key using CryptoLocker, then you can download private key and decrypter for free,” explains the service, which is currently hosted at one of several addresses on the Tor anonymity network. The decryption service site is not reachable from the regular Internet; rather, victims must first download and install special software to access the site — yet another potential hurdle for victims to jump through.
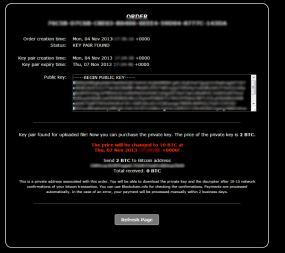
According to Abrams, victims who are still within the initial 72-hour countdown clock can pay the ransom by coughing up two Bitcoins — or roughly $200 using a MoneyPak order. Victims who cannot pay within 72 hours can still get their files back, but for that unfortunate lot the ransom rises fivefold to 10 bitcoins — or roughly USD $2,232 at current exchange rates. And those victims will no longer have the option to pay the ransom via MoneyPak.
Abrams said the service exposes two lies that the attackers have been perpetuating about their scheme. For starters, the bad guys have tried to dissuade victims from rolling back their system clocks to buy themselves more time to get the money together and pay the ransom. According to Abrams, this actually works in many cases to delay the countdown timer. Secondly, the launch of the Cryptolocker Decryption Service belies the claim that private keys needed to unlock files encrypted by CryptoLocker are deleted forever from the attacker’s servers after 72 hours.
DETECTING AND PREVENTING CRYPTOLOCKER
Last week’s story pointed to two tools that can help block CryptoLocker infections. Individual Windows users should check out CryptoPrevent, a tiny utility from John Nicholas Shaw, CEO and developer of Foolish IT, a computer consultancy based in Outer Banks, N.C. Small business administrators can avail themselves of a free tool from enterprise consulting firm thirdtier.net, which recently released its CryptoLocker Prevention Kit. This comprehensive set of group policies can be used to block CryptoLocker infections across a domain.
As this scam illustrates, relying on antivirus software alone to protect you from attacks is foolhardy. Also, it’s vitally important not only to have a backup plan for when a malware or hardware disaster strikes, but also in the event of nasty attacks like this one. For example, backing up your files to a removable or network drive is a great idea, but one added layer of protection against attacks like this is to perhaps disconnect those drives when you’re not backing up your data.
Also, I hope it’s clear that tools like CryptoPrevent and antivirus are no substitutes for common sense. Threats like these are opportunistic, and as with many modern threats your best protection against them is to employ basic online street smarts: Street smart rule #1 is don’t blithely open attachments in emails you weren’t expecting, even if they appear to come from someone you know.
For other tips on keeping your data and computer safe, see my tutorial — Tools for a Safer PC. While many of these CryptoLocker attacks have been perpetrated via cleverly disguised malicious email attachments, there are indications that this malware is being disseminated via networks of PCs that have already been hacked through other methods. Abrams said many recent CryptoLocker attacks have actually started with infections from the ZeuS or Zbot banking Trojan, which is then used to download and install CryptoLocker.
“If you’re really lucky, your system may also get [the spam bot] Cutwail installed on there as well and start spamming,” Abrams said.
For more information on this threat, see BleepingComputer.com’s CryptoLocker Ransomware Information Guide and FAQ.




What’s wrong with you people…Why are you playing their silly game. Track the money, find the people and take them out! It’s ridiculous to pay ransom, better if you lose your files and business. If you’re dumb enough not to back up things you get to start-over back to square 1.
Whoever pays these people…are promoting this to occur and then it’ll happen more frequently. Soon, all the people that paid the ransom will be targeted even harder…since they got ransom money out of them..and will kidnap your computer/s again. Stop toying with them, follow the money and put a bullet hole in them. Don’t be a dummy, back up system, don’t pay them, and clean HD and re-load operating system. Don’t feed the devil, kill him.
You sound very angry Mark. I hope things get better.
It’s probably frustration, which I agree with his sentiments, except for the bullet hole. Let the authorities take care of it, but I agree that it could probably be tracked by the right person. Still, I kinda like the Charles Bronson approach… 🙂
No I agree. Kill them. It’s the more elegant solution.
It’s easy to say “Kill them” but what if these hackers turn out to be kids as some viruses running around have been written by.
As if you’re allowed to kill adults more than kids, hm. The above posts – American logic?
Cybercrime sucks. Well, ignoring all the personal damages, at least Cryptolocker is cool and innovative in a way that penis pill spam and click fraud are not.
“cool and innovative” you complete scumbag, you must lead one sad existence if this kind of extortion is your idea of cool. Mark is right, they need tracking down and killing. I’d be very happy to pull the trigger on them kids or not.
These malware isn’t from young kids for sure. Look at their level of sophiscation!
In all seriousness, why hasn’t any government made a serious effort to find these people and put a halt to this? This is little short of cyber terrorism and the longer they are allowed to get away with this the more of a threat they pose to the rest of the world. If the US government can shut down Silk Road why can’t they do the same for this lot and send the filth behind it to prison?
Maybe it’s because the government is the one responsible for it in the first place……
What better way to increase your “tax income” then by using an anonymous money and transaction network…..
You are just dumb ass ..Excuse mua .
How about get rid of all the drug dealers too while you killing all them hackers ? Drug dealers do bigger damage then all the hacked in the world put together .Track the money,find the people and take them out — sounds easy right .Good luck .
I see people speed down my street in cars and on motorcycles. They are going way too fast and have killed a number of pets. There have been a few people hit as well.
I’m sure the people speeding didn’t intend on hitting someone or killing their pet.
I keep my pets indoors around holidays when people tend to get drunk/insane and go driving around.
…all in all the rise of vigilantism seems like a REALLY BAD idea, but so does having check points every few miles.
You are suggesting they track the bitcoin payments? lmao.
Bitcoin is not as anonymous as you think.
They can certainly track Tor. They managed it with Silk Road didn’t they?
I’m afraid they didn’t. What they actually did was use the list which Dread Pirate Robert (pseudonym of SR’s creator)’s assistant accidentally leaked.
Also, two weeks later and Silk Road is back up. Think how many years it took the US to take it down in the first place.
Mark, it traces back to Israel. So good luck trying to get anyone to do anything about it.
Mark, I read that Cryptolocker targeted mainly company computers in UK. Imagine what can happen if a CEO of a mid or big company gets all his files crypted. I too think that people should not pay this awful ransom, but all depends on the crypted data value.
Don’t mount your drives in windows just use an external browser, the virus only infects filesystems, but it can’t infect files through ftp, etc
Or don’t use Windows, period. Use Linux, Mac OS X, BSD or any other system that was designed ground-up with separation of administrative and user roles.
Nothing is a panacea, but “do not use Windows” falls under the common sense section of how to avoid malware.
And then they would have to spend on training for the new OS.
Most people don’t use other OS and don’t know how to use other OS.
Most applications are compatible with Windows, it is the most popular, unlike other OS.
Windows should die in a hole, but I doubt that will happen anytime soon.
Windows does separate administrative and user roles. This virus does not need administrative access to do its damage. It’s manipulating the user’s documents in the user’s context. So your point about admin & user roles is incorrect. If this virus had been written for MAC, Linux, BSD, OS2/Warp, or anything else, it would not matter. It’s not using any administrative access or exploiting any vulnerability. The user receives the files as an attachment and runs it themself. It’s social engineering. So please stop with the ‘MAC and Linux are sooo wonderful’ BS please… It’s not helpful to this conversation. It’s distracting background noise.
the attached files obviously contains exploits designed for whatever program is used for opening them
With Linux, programs downloaded from the internet isn’t automaticly marked as executable. So most people wouldn’t be infected, as they wouldn’t know how to execute it. And those who would know how has to be more IT-competent, and which isn’t generally those who would run random applications from the internet.
If you have a vulnerable file handler on Linux (perhaps VLC, Adobe Reader, Open Office, Java), then this sort of thing could happen there too. And if someone manages to exploit your User Agent (Web Browser or Email Client), then that too is enough.
Please don’t tell people that Linux / Unix are magically more secure against these attacks. MB is correct, the attacker is using a user space process to rewrite the user’s files. Another comment mentioned an attack against Firefox, someone who has managed to do that for Windows could easily do it for Linux / Unix.
I use CryptoPrevent and it’s updated frequently. The guy who programs it it really know what he is doing.
I have what may be a dumb question:
If I am already using full disk encryption on my machine, would that somehow conflict with the CryptoLocker infection and stop it in its tracks? If so why, and if not why not?
Sorry Horace,
Full disk encryption protects up to the point when you mount and use the disk: that’s when the volume is unlocked, and that’s when b@stards like CryptoLock can do their dirty work.
At worst: if infected, you’ll have CryptoLocked data files on your fully encrypted disk …
Encryption pattern should be revised so no one will understand it to hack.
Complexity is the enemy of security not its friend. An overly complex solution simply will not get used – ask the NSA. They know, and have used this fact to prevent your cell phone carriers from offering meaningful encryption on your private conversations.
the comment nsw offshore humanitaraian processing centre
Uh oh…. Krebs has some back tracking to do….
35. November 7, IDG News Service – (International) Silk Road online drug marketplace resurfaces. Underweb marketplace The Silk Road, reappeared about a month after its alleged owner and operator was arrested. The marketplace that allegedly offers illegal drugs, fraudulent documents, and other illicit goods and services claimed that 7,000 individuals had registered as of November 6. Source: http://www.computerworld.com/s/article/9243869/Silk_Road_online_drug_marketplace_resurfaces
Back tracking? How so?
Any idea if this requires Admin rights to install and then encyrpt the files? Or since you have access to the files it does not require admin rights? Trying to determine if an awareness notification should be sent company wide.
Does not require admin access. Runs under the security context of the invoker.
Brian, Where is the best, “Complete”, instructions for CL’s removal.
The one on Microsoft is disjointed and hard to follow at best.
KUTGW
Hello Brian ,What about this tool from Bitdefender ?
http://labs.bitdefender.com/2013/10/cryptolocker-ransomware-makes-a-bitcoin-wallet-per-victim/
I’m using HitmanPro along with CryptoPrevent.
10 BTC is like $3600 with the current Bitcoin rate. Seems they are getting greedy and exploiting their skills 🙂
I came across one of these today. Domain registered in China, hosted in the Ukraine.
A bunch of them actually on 193.169.86.250 they seem to generate fake police websites. Anyway the interest thing was they have an exploit of sorts against the latest version of FF.
Who says those police websites are fake? Just because they create them doesn’t mean they aren’t funded by or organized by a governmental authority. Particularly an authority that doesn’t have to provide proof of fighting the crime coming from its country…
They’re only upset when they hack their own nation’s banks.
Hundreds of my clients still running Windows PCs (zero run Win8.x) also use online backup services of some sort, mostly Carbonite, which is very cheap for unlimited data and is HIPAA compliant (Carbonite’ll sign a HIPAA vendor doc or whatever it’s called).
One client uses eSureIT online backup for a server. Two still use Connected.com (not recommended, though).
Several clients also use DropBox, Google Drive and Box.com, though they don’t use them for backup, just regular sync storage.***
A high percentage of clients switched to OSX UNIX boxes. But for both Macs and Windows PCs, we don’t install or do disable or remove Java.
Online backup is cheap, and you can configure it to run only during non-business hours to avoid congesting the LAN or Internet connection, especially when starting the service on the same day for lots of PCs.
===
*** Doesn’t each local computer folder for an account of Box, DropBox and Google Drive lives on the user’s hard drive like any other folder? If so, couldn’t any encryption program, virus-driven or legit, encrypt those files, which would then update throughout the user’s account? I think DropBox has versioning, though. I don’t know if Box.com or Goog Drive have versioning.
Google Drive doesn’t require users to install its local program and folder; users can instead manually upload/download folders/files through browsers. But several clients use the local app/folder AND they also run Carbonite, which includes the local Google Drive folder AND they subscribe to Backupify.com for cloud-to-cloud daily backup of their gmail, cal, contacts, Google Drive data and any other goog stuff.
If I encounter the cryptolocker virus on a heavily backed-up PC, it’s going to give me great pleasure to reject the ransom request. Hopefully, the virus provides a little message box to communicate with the criminals.
I could convert the infected PC into a honeypot and isolate it from the rest of the LAN, but that’s too dangerous for the LAN. Maybe I’ll take it home and do that. Tempting! Maybe I’ll pay only ten cents ransom and promise another dime once a week. I won’t bother, of course.
Anyway, realistically, I’d replace the drive after infection or format the old one and make sure to remove the hpa if present. It just occurred to me not to throw away a cryptolocker-ed drive without wiping it, at least partially, because someone could pull the drive from the trash, boot off it and pay the ransom to see all the data.
=====
PS Just got back from Russia. My friends in Moscow use Linux in order to avoid 99.999% of the circulating mayhem. I don’t think they currently can afford OSX UNIX machines.
=====
Pre-Internet, sociopaths’ damage was limited to their region, unless they used a postal service or headed a government with planes, etc. But now, in the 21st century, all of the world’s Internet-savvy sociopaths have access to everyone else in the connected world. Now, instead of just dealing with your town’s, your county’s, your state’s sociopaths, you have to deal with the worst of the USA, China, Russia, Ukraine, Nigeria, India, Germany and every other country with even dial-up. YOU BETTER BACK UP LIKE CRAZY!!!
Another option that fits everyone’s needs, especially businesses would be SOS Online Backup. These guys are just good.
I have been using SOS Online Backup. They have helped us protect our business from any such threats. We go to sleep in peace 🙂
I bet the key they generate is totally predictable, or they are just using java encryption in ecb useless mode anybody can decrypt themselves. Where can I get infected lol? I highly doubt this is properly implemented crypto. If they are running a db to search for keys it means that db can be yoinked too
Says it right on the screenshot (the red one). And the public/private key part sounds like RSA. Good luck ‘predicting’ that.
Thanks for sharing 🙂 I use too CryptoPrevent and it’s updated frequently. The guy who programs it it really know what he is doing
Imagine that! Facebook warning users of a security problem!
Regards,
We paid the Ransom and got nothing. It just said it could reach the server and to wait the server would be back on. After about 2 hours we pulled the plug and tried to offload MoneyPak cash onto Paypal to find they already too the cash and did not decrypt the files!
we have the Zip file that infected us. We were able to recover the person files and out server files but the person did a lot of work over the weekend off the Network so no backup
Thanks for posting – this kind of thing needs to get out there so people will not give up and capitulate to the criminals. If the crooks would actually follow up and send the key, I can see where they would probably have a lucrative world market, but of course there is no honor among thieves, so they can forget that.
Are all the smart people on the wrong side of the law? Why can’t the authorities find people who can better track these people. If you round up a few and send them to jail. Maybe it would reduce some of this. I agree, people should seek out help before just paying. I think much of my stuff is backed up and I don’t store much on my PC anymore. If I do, I have a backup somewhere. People are just too lazy until they get attacked. Then all of a sudden they want to blame someone else. The solutions are out there. You just have to make a effort to protect your information.
The authorities won’t find them if they’re in a country that only cares about the cyber crime they commit on their own populace. Cyber crime against the US is probably funded by those same authorities.
interesting twist in events, by encrpyting victims files.
Kids making computer viruses? I don’t think this one was created by kids. A criminal is a criminal. DO NOT PAY. Start from scratch if you have to, and back up your files. I lost one year of pictures of my kid. Good reason to go back to see world and other places we went and take more pictures and back them up. It was a good thing I just lost one year and not 10. I learned my lesson. Run backup jobs more frecuently. BACK UP all your files.
It’s sad how these online discussions that start off great, and are a place you can go to find help, always devolve into the realm of useless self indulgent blathering.
-It’s the government stealing your money!
-Get Linux, it’s solves all your computer problems and butters your toast for you!
-It’s the NSA running this theft network!
and on and on and on….
Seriously people. If you don’t have something worthwhile to contribute, which would be how to decrypt or prevent the infection, please knock it off!
Hi, I have been working on a fix using a DIY quantum computer loosely based on D-wave’s system.
Hope to have it ready by the end of 2013 if the materials all turn up on time and I can perfect my electrostatic field annealing technique.
Its about a 1024 ie 1 kiloqubit system, using doped MgB2 based outer shielding so LN2 can be used instead of costly helium.
Who said RSA-2048 was unbreakable, 1024 bit fell to a simple voltage variation hack.
Just add an entanglement chipset for defense! All fixed! 😀
I have had this infection penetrate deep through several layers of security. Unfortunately the user is a director in the company, and the data is valuable. Data is backed up weekly on local servers and Dropbox is used to share some critical files, but only a few days worth of work makes it worth the $300 to “unencrypt” the data. Sucks, but the data is worth more than the time it would take to re-create some of these documents.
Seems like SOMEONE should be able to just block the process that is used to start the RSA encryption, but so far all our Endpoint products seem worthless (McAfee, Webroot, Microsoft) even when in conjunction with good firewall policies. You can’t protect users from themselves (especially directors of your company).
I’ve been following cryptolocker for a while now. youtube.com/CryptoLocker
No. I’m with Mark here: we need to find them and take them out. These fuckers are just like the Zetas; just like Al Qaeda and they don’t deserve to live. End of fucking story.
Hello!
Maybe there’s a simple solution, we have not tested ourselves but it could work.
WINDOWS 7, right click on the folder that is encrypted and select properties> then go to the tab previous versions in properties you will see an earlier version of the folder that your computer has been saved. Then you can simply choose one from the day before you got the virus, and then click the Copy button, make a new folder and copy your work in the new folder – you will get back almost all your files unencrypted, maybe not the last job you have done, but most will be there.
Myzone Team Sweden