Adobe and Microsoft today each released software updates to fix serious security flaws in their products. Adobe pushed an update that plugs a pair of holes in its Flash Player software. Microsoft issued five updates, including one that addresses a zero-day vulnerability in Internet Explorer that attackers have been exploiting of late.
 Microsoft’s five bulletins address 23 distinct security weaknesses in Microsoft Windows, Internet Explorer and Silverlight. The Internet Explorer patch is rated critical for virtually all supported versions of IE, and plugs at least 18 security holes, including a severe weakness in IE 9 and 10 that is already being exploited in targeted attacks.
Microsoft’s five bulletins address 23 distinct security weaknesses in Microsoft Windows, Internet Explorer and Silverlight. The Internet Explorer patch is rated critical for virtually all supported versions of IE, and plugs at least 18 security holes, including a severe weakness in IE 9 and 10 that is already being exploited in targeted attacks.
Microsoft notes that the exploits targeting the IE bug seen so far appear to perform a check for the presence of Microsoft’s Enhanced Mitigation Experience Toolkit (EMET); according to Microsoft, the exploits fail to proceed if EMET is detected. I’ve recommended EMET on several occasions, and would encourage any Windows users who haven’t yet deployed this tool to spend a few minutes reading this post and consider taking advantage of it to further harden their systems. The latest version — 4.1 — is available at this link and requires Microsoft’s .NET Framework 4 platform. For those of you who don’t mind beta-testing software, Microsoft has released a preview version of the next generation of EMET — EMET 5.0 Technical Preview.
This month’s updates include a fix for another dangerous bug — deep within the operating system on just about every major version of Windows — that also was publicly disclosed prior to today’s patches. Microsoft’s Technet Blog has more details on these and other bulletins released today.
Readers still using Windows XP should remember that after next month, Microsoft will stop releasing security updates for that version of Windows. Microsoft recently announced that it will make available for free a Windows XP data transfer tool to ease the hassle of upgrading to a newer version of Windows. I would submit that if your PC runs XP and came with XP installed, that it might be time to upgrade the computer hardware itself.
In any case, using Windows XP beyond next month is not the greatest idea, and it’s time for XP users to consider other options. Don’t forget that there are many flavors of Linux that will run quite happily on older hardware. If you’ve been considering the switch for a while, take a few distributions for a spin using one of dozens of flavors of Linux available via Live CD.
FLASH UPDATE
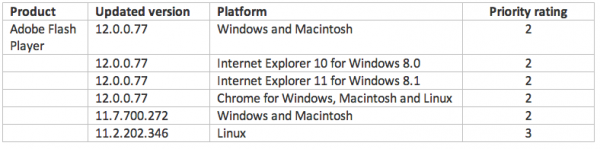
 Adobe’s Flash update brings the media player to v. 12.0.0.77 on Windows and Mac OS X. This link will tell you which version of Flash your browser has installed. IE10 and Chrome should auto-update their versions of Flash. If your version of Chrome (on either Windows, Mac or Linux) is not yet updated to v. 12.0.0.77, you may just need to close and restart the browser.
Adobe’s Flash update brings the media player to v. 12.0.0.77 on Windows and Mac OS X. This link will tell you which version of Flash your browser has installed. IE10 and Chrome should auto-update their versions of Flash. If your version of Chrome (on either Windows, Mac or Linux) is not yet updated to v. 12.0.0.77, you may just need to close and restart the browser.
The most recent versions of Flash are available from the Adobe download center, but beware potentially unwanted add-ons, like McAfee Security Scan). To avoid this, uncheck the pre-checked box before downloading, or grab your OS-specific Flash download from here. Windows users who browse the Web with anything other than Internet Explorer will need to apply this patch twice, once with IE and again using the alternative browser (Firefox, Opera, e.g.). Adobe does not appear to have released any updates for AIR as it often does when pushing new Flash patches.
As always, please drop a note in the comments section if you experience any issues with the updates released today.




“I’ve recommended EMET on several occasions”
EMET is great when it runs, but I have run into situations where it causes problems. Today’s patches broke a system running W-7 / IE10 / Office 2010 / EMET 4.1.
Here is my advice to make it work problem-free. Every Patch Tuesday, if EMET starts whining, uninstall and reinstall it. I can just hear the complaints, but I have had to uninstall EMET and reinstall it on a few systems. Also, EMET seems to have problems with Bitdefender; I gave up on making both work together.
Also, I have noticed that if you start IE immediately, before EMET has had time to fully start, EMET will refuse to allow IE to start at all (it complains about caller mitigation). A reboot will be needed in that case.
“requires Microsoft’s .NET Framework 4 platform”
While technically true, this statement deserves an update. If you build a new PC with a fresh copy of W-7, Windows Update will install .NET 4.5.1., avoiding the need for a separate installation of .NET 4 for EMET.
“I would submit that if your PC runs XP and came with XP installed, that it might be time to upgrade the computer hardware itself”
I have had good success installing Fedora Linux GNOME 32-bit on old XP hardware.
I downloaded the two versions of Flash, EXE installer, for IE and Firefox using http://www.adobe.com/products/flashplayer/distribution3.html. The Firefox version says 12.0.0.77, the new version, while the IE version says 12.0.0.70. I used install_flash_player_12_active_x.exe , Created: Today, March 11, 2014. The Details say File version 12.0.0.70, date modified 3/11/2014 2:19PM, Product version 12.0.0.70.
Anyone else have this problem?
This probably won’t help, but I have had a few W-7 systems running today. I have not updated any system’s Flash because I was curious as to the update schedule. I just checked: one system has 12.0.0.70 and another has 12.0.0.77 for IE.
Old School, I’ve had that same problem on manual downloads of previous Flash updates, including the previous one. Thankfully, today’s manual update went fine; 12.0.0.77 installed for both ActiveX and plugin.
Do you uninstall the previous Flash Players before installing the new ones?
If you perform a manual install of the Flash update(s), you should go ahead and manually uninstall the existing one(s) first — although the installation executable should recognize a prior version and uninstall it, that may not fully occur, so better to be safe and not end up with leftover bits of an insecure version. If you have the automatic updating feature enabled that should take care of the uninstall as well.
I have never removed the current version prior to installing the new version. When I went to try the uninstall, I noticed that the Control Panel listed the version as the current 12.0.0.77. When I ran my test Youtube video, the version displayed was the obsolete 12.0.0.70. I downloaded another copy of the Active X version from Adobe and tried to install it but I was told that the downloaded version was not the most current version. This error message is new just within the last few hours. By this time I was not a happy camper! So I followed Adobe’s recommended install path which took me to the Adobe page that has the additional download of Chrome, the one download page I try to avoid. I downloaded just Flash, installed it, ran my test Youtube video under IE and I finally got 12.0.0.77 when I checked the version on the video screen. This page: http://www.adobe.com/products/flashplayer/distribution3.html gave me the version of the Active X module that caused the problems.
Now, back to taxes.
Why do your posts show “Mar 14” date from the future? Today is only Mar 11.
The ’14’ means the year 2014. (Somewhat of a modified Y2K problem)
Yep, the big number is the day. There is also a timestamp at the end of every post, albeit in fairly small typeface.
Hackers have “zero days” but Brian is so good he has “-x days”.
The N.SA. is monitoring again?
I use EMET, but I wish there was some way to be notified that a new version is available, other than by reading this blog.
See http://technet.microsoft.com/en-us/security/jj653751 . 4.1 is current, 5.0 is on the way.
I think it’s funny that on the Linux version’s readme, Adobe includes a typo on a critical filename “libflashplayer.so” (note it says ‘layer instead of ‘player) From Adobe’s official readme:
Copy libflashplayer.so to the appropriate browser plugins directory. At the prompt type:
+ cp libflashlayer.so
What isn’t funny is that it took me a good 10 minutes to figure this out since I copied and pasted from the readme.
Chrome updated today to version 33.0.1750.149 – haven’t checked to see if this is the one covering flash vulnerabilities. I really appreciate Brian’s update alerts on this! Plugins are supposed to be dropped by the end of this year, and many are doing that now. They either download an applet or script that runs in stead of a plugin; or like my version of Chrome, they change the whole version to cover flash vulnerabilities.
LogMeIn has switched over to the future, many will soon follow.
EMET 5 throws off way too many errors and is really beta-y. I would not recommend installing it unless you have a tolerance for “known” issues and crashes on closing IE.
It really is a “preview” and just shows what they are planning.
I’m using EMET 5.0 Tech Preview on four 64-bit Win8.1 Pro boxes with IE11 and it’s not giving us any problems. All EMET’s options are enabled. I use Enhanced Protected Mode and 64-bit tab processes, which means some of EMET’s tweaks don’t apply (some are only for 32-bit processes). What Windows/browser config are you using?
On the main topic, this round of updates went smoothly for me on about a dozen systems (Win8.1 and one Windows Home Server). All the updates installed on the first try, unlike some months where it takes a couple go-arounds. Haha, the computers are like 4-year-olds sometimes… “I’m not eating the peas, they touched the mashed potatoes!!” 🙂
I think my problem with EMET 4.1 is the fact that I’m trying to use in on a Vista x64 system with IE–9. I suppose that is a losing proposition, no matter how you stack it! 🙁
I’m about to go back to the previous version on my Vista Ultimate x64 system anyway! This went smoothly on that one, but now I can’t run Internet Explorer at ALL. I’m still trying to tech that, for now, anyway! Re-installing IE-9 seemed to help, but I never had problems with the previous version of EMET, except where web sites were misbehaving; so I’ll run it long enough to send a lot of crash reports, and then I’ll revert to the previous version, until Secunia PSI tells me it is not safe!
I am running Chrome Beta Channel, and the abobe page is listing that I have version 13,0,0,133 installed
Maybe Brian or somebody can chime in on this, but I’ve had Adobe alert me on the check page that only a Chrome version such and such, can plug a particular vulnerability to that browser. In this update the version sited in the article seems to do the trick – but I’ve had at least one update cycle where that was not the case, and the Adobe site listed a new Chrome version number as the only solution. I firmly believe this is because of my previous statement about plug-ins and standard Adobe practice going away by the end of this year. Adobe will still help developers with HTML-5 coding, but there will be no more plug-in support.
(excuse me for not reading the whole thread so far…)
XP isn’t quite dead. For those who can run software on an XP box without upgrading it, I’d recommend making yourself a little archive of the ~140 patches to the system, for if you ever had to rebuild from scratch. We can consider anything that requires XP to be in a near-sealed box, like an iPad. You just have to wall it off from the internet.
For example, perhaps make a “sealed” box to let the kids play some of the older puzzle (help-you-learn-thinking-skills) games when they’re old enough. Yep, XP isn’t totally dead. If you protect if from the internet, then it’s still useful as a limited-trick pony. Of course, if what we have can run on Win7, then don’t bother with XP. If for only those applications that can’t run on 7.
Firefox blocks mixed content on a page delivered using SSL, and I have the HTTPS Finder add-on in Firefox.
That means Brian’s link changes to “https://www.adobe.com/software/flash/about” in Firefox; and that page contains insecure content which Firefox blocks. One blocked item is only a banner advertisement, but the other is the box showing the currently-installed Flash version.
Has anyone else encountered this? Perhaps Adobe should be notified.
Why would you tell Adobe what a good secure browser you have? I doubt they’d care!
If you need to see the flash test, simply allow that site, or put it in your exceptions list.
I care about security, so I care about Best Practice. An https page shouldn’t include content from a non-secure source.
And in fact the content coming in from http sources on that page includes several javascript files, so it’s not just (as it usually is) an image which can be safely excluded.
I hear ya Hayton, but insecure, just means the objects are scripts like java or flash. Since the objective it to test flash, you really need the scripts to complete the mission. I have a cousin who codes java, and he says he can make any java utility as safe as you can get, by writing the code properly. He was so successful at it he sold his company at a hefty profit – so I figure he knows what hes talking about. Sure java can be inherently insecure, but what code doesn’t have holes in it? Java has more history of it because it is a powerful tool. I think anything like that is going to be that way. Coders make it worse with sloppy programming though.
Author: George said,”The way I read Hayton’s comment is that the scripts are coming from a different source, so it does not seem right for me to say ‘insecure, just means the objects are scripts’.
Something that is quite obvious when using NoScript on Firefox is the number of scripts/etc that come from URLs different from the one of the page one is looking at.”
That is interesting, and I will watch for that now – but most of those browser messages probably don’t analyze the scripts that closely. I’d be very surprised if they did anyway. Perhaps a plugin or some of the other tools mentioned here in this thread could, but not the generic system. I could always be wrong – but 9 times out of 10, my hunches are correct.
MBAM Pro is so good at blocking known outgoing/incoming malicious server IPs, that I’d tend to defer to those rivets in the armor of a blended defense.
You realize more than half the sites that use HTTPS don’t even use it as well as they could, right? You’d have a field day running sites through this: https://www.ssllabs.com/ssltest/
I use the https://www.eff.org/https-everywhere addon myself.
I’ve used the Qualys SSL Server Test before, and I agree you could have a lot of fun showing the results for their site to some administrators. Not every “secure” site is as secure as it likes to portray itself …
I use HTTPS Everywhere in Chrome, and recommend it. I had to disable it a while back in Firefox (I forget why) but it’s there too. In Chrome it’s said to be a Beta version but apart from what may be a memory leak it seems to be stable. In Firefox it’s stable.
In the light of recent annoyances from certain Acronyms this EFF extension should be more widely promoted. It’s not a cure-all but it’s helpful.
I’ve sent in a few really bad rating myself but only one site ever got back to me with any sort of indication they’d actually look into it- it was patreon.com. One of the other sites though was a hospital records site who had gotten an F for still supporting SSL 2, and I never got a reply yet.
I don’t know. I really wish it was a web standard these days, but I know a lot of sites don’t feel it’s warranted if they’re not a shopping site or something. That, and depending on where you buy your certificate it can be kind of pricey.
Some people though would even say HTTPS even isn’t enough, but, I think it’s a lot better than nothing. The only thing really rock solid is OpenPGP.
Your post reminded me of when I discovered how sloppy many sites were setting this up. Back then I was using Comodo’s Verification Engine, and I was having luck contacting web-masters about the mistakes they were making.I forget the analysis page I was plugging the URL into to check what was actually wrong, but I was able to tell them specifics, and they seemed to appreciate it. But then I told them I was not going to do business with them until it was fixed – for whatever small motivation that was! Surprisingly it was fixed by my next visit to the site, on average.
I quit using it when I noticed that most browsers actually do provide certificate and setup information right from the address bar now. So I simply look at the color coding on Dragon and decide if I wan’t to take the chance or not. I’ve become rather lazy now that Rapport is installed and working on the big three browsers – Chrome, Mozilla, and Internet Explorer.
“Windows users who browse the Web with anything other than Internet Explorer”? Like, say, everyone who reads your posts?
It’s still about 25 percent of my readers, according to my site stats.
Thanks once again, Mr. Krebs, you do a top-notch job of keeping your subscribers informed.
2 questions:
1) Why does Microsoft consider Update for Root Certificates for Windows XP [March 2014] (KB931125) to be an “Optional” software update? Aren’t up-to-date certificates key to secure https web usage?
2) Does anybody have any idea how much Adobe might actually manage to bring in every month from McAfee Security Scan, Ask! toolbars and the like via the http://get.adobe.com/flashplayer/ web site?
Inquiring (enquiring?) minds want to know… 😉
Why updates for root certificates in XP are an optional download : see “How to get Root Certificate Update for Windows” (http://support.microsoft.com/kb/931125)
“Windows XP does not fully support the automatic root update mechanism. When a root certificate is already present on a user’s system, it will not be updated even if the copy of the root certificate available on Microsoft Update has changed. Windows XP also does not support the weekly pre-fetching of certificate properties from Microsoft Update feature, and the only way to install new root certificate properties on Windows XP is by installing the root update package.
We recommend that users who are running Windows XP download and install the root update package to update their root certificates. Root certificates are delivered for Windows XP through Microsoft Update as an optional root update package – an executable that contains every root certificate that is distributed by the Windows Root Certificate Program. Windows XP users can opt to download the package every time that it is updated and presented by Microsoft Update. Or, they can opt to download the root update packages automatically when they are updated.”
This doesn’t explain why it’s optional, but http://technet.microsoft.com/en-us/library/bb457160.aspx gives an explanation (sort of) :
“In a medium-size to large organization, for the greatest control of communication with the Internet, it is recommended that you manage the list of certification authorities yourself, meaning that on users’ computers, you would control or remove the Update Root Certificates component or prevent it from being installed with Windows XP”
So some companies might not want the root certificate download to be automatic –
“If the user is presented with a certificate issued by a root certification authority that is not directly trusted, and the Update Root Certificates component is not installed on the user’s computer, the user will be prevented from completing the action that required authentication. For example, the user might be prevented from installing software, viewing an encrypted or digitally signed e-mail message, or using a browser to engage in an SSL session.”
(Hi Hayton — Please accept my belated thanks for your detailed response to my earlier question; my comminuted wrist fracture, surgery, and subsequent oxycodone medication has kinda upset my “flow.” 😉
Just for kicks, I tried doing a mid-month Windows Update on my desktop XP computer, and lo and behold, there was an optional Update for Root Certificates for Windows XP [November 2013] (KB931125). Huh, November? And, same number as the March certificate update?? SMHx2… BTW, I got the same optional update on my XP laptop; both are XP SP3.
Isn’t it ironic that Internet Explorer, by the very company that controls the OS, is the industry’s LEAST secure browser? Go figure.
My XP machines and my Server 2003 box all decided they needed to reinstall KB2728973 (from July 2012). After reinstalling that old patch, now they want to reinstall KB2917500 from January. I let one of them do it, and now that box wants KB2728973 again–another patch loop. Anyone else seeing this?
Not many people still running XP, I guess. One of my machines still has XP and I did notice that after the main batch of updates went through and I had re-booted there were two which came back demanding a re-install – KB2929961 and KB2932677 (for Silverlight). No more requests for re-installation since then. I haven’t seen anything about the two KB patches you mention.
One thing I noticed, EMET 5.0 Technical Preview does no work on XP unlike the Emet 4.1 that required NET. Framework 4 (a slowdown for XP and another vector of atack) but worked on XP.
It looks like MS does no bother to help protect XP anymore. I hoped that I could at least use EMET 5 Technical Preview for some sort of protection against exploits after the XP end of support.
Shockwave Player was updated to v12.1.0.150 late yesterday FYI.
Hayton:
‘An https page shouldn’t include content from a non-secure source.’
‘And in fact the content coming in from http sources on that page includes several javascript files,….’
JCitizen:
‘I hear ya Hayton, but insecure, just means the objects are scripts like java or flash. Since the objective it to test flash, you really need the scripts to complete the mission.’
The way I read Hayton’s comment is that the scripts are coming from a different source, so it does not seem right for me to say ‘insecure, just means the objects are scripts’.
Something that is quite obvious when using NoScript on Firefox is the number of scripts/etc that come from URLs different from the one of the page one is looking at.
Your comment finally showed up here in the thread – so I replied to a previous post. I’ll repeat it here too.
I thank you for your interesting observation. I still feel the standard browser alerts don’t analyze the script environment that closely, although other plugins or tools do.
I’ll take the time to look more closely at NoScript blocking alert content from now on!
Thanks George!
That is correct. The script files (javascript, not java) are coming into the webpage from an external source over a non-secure connection. It might not matter in this case (or indeed in most cases) but as a matter of principle any webpage which is allegedly “secure” (delivered over a secure connection, and with the “https” prefix) should not include any content from another source which is delivered over a non-secure connection.
There are people out there who can explain the technical details of MITM attacks and certificate spoofing better than I can, and there are plenty of articles and blogs by security experts which give detailed explanations of why exactly mixing secure and insecure content on a webpage is undesirable.
The important thing to note is that insecurely-delivered passive content can be tolerated, although deprecated; but insecurely-delivered **active** content has the potential to compromise the integrity of the entire webpage.
See the Mozilla blog about this, from the time of FF23
https://blog.mozilla.org/tanvi/2013/04/10/mixed-content-blocking-enabled-in-firefox-23/
I agree for sure with the comment on that Mozilla article that,
“the web isn’t ready for passive mixed content blocking” HA! Man that’s for sure!
I don’t get the content warnings from the Adobe Flash update page, so I may have blocking turned off; but there again, I’m not sure I’d care about that page as I’m not accessing anything in HTTPS, and I’m not worried about the security of the session. These are the main reasons I commented so negatively about that factor. I did learn a lot here, so I appreciate this discussion. Thanks Hayton!
I will have to check my controls in Dragon to see if any security features are disabled. That Comodo Chrome based browser generally breaks a lot of pages as it is, so I may have disabled many things to get functionality on average. I have their version of NoScript enabled, and it is easier than NoScript to use as far as general settings granularity. I like that I don’t have to constantly setup script allowances on every new site I visit with that tool present.