Adobe and Microsoft today each released updates to fix critical security vulnerabilities in their software. Adobe issued patches for Flash Player and AIR, while Microsoft’s Patch Tuesday batch includes seven update bundles to address a whopping 66 distinct security holes in Windows and related products.
![]() The vast majority of the vulnerabilities addressed by Microsoft today are in Internet Explorer, the default browser on Windows machines. A single patch for IE this month (MS14-035) shores up at least 59 separate security issues scattered across virtually every supported version of IE. Other patches fix flaws in Microsoft Word, as well as other components of the Windows operating system itself.
The vast majority of the vulnerabilities addressed by Microsoft today are in Internet Explorer, the default browser on Windows machines. A single patch for IE this month (MS14-035) shores up at least 59 separate security issues scattered across virtually every supported version of IE. Other patches fix flaws in Microsoft Word, as well as other components of the Windows operating system itself.
Most of the vulnerabilities Microsoft fixed today earned its “critical” rating, meaning malware or bad guys could exploit the flaws to seize control over vulnerable systems without any help from users, save perhaps for having the Windows or IE user visit a hacked or booby-trapped Web site. For more details on the individual patches, see this roundup at the Microsoft Technet blog.
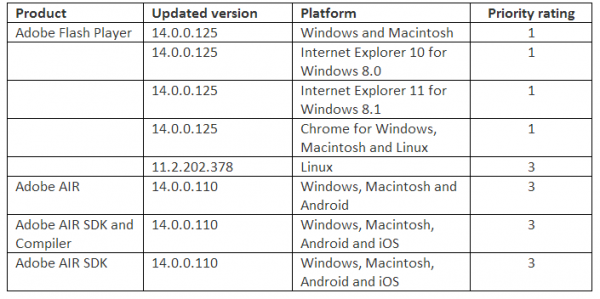
Adobe’s update for Flash Player fixes at least a half-dozen bugs in the widely-used browser plugin. The Flash update brings the media player to v. 14.0.0.125 on Windows and Mac systems, and v. 11.2.202.378 for Linux users. To see which version of Flash you have installed, check this link.
 IE10/IE11 and Chrome should auto-update their versions of Flash. If your version of Flash on Chrome (on either Windows, Mac or Linux) is not yet updated, you may just need to close and restart the browser. Chrome version 35.0.1916.153 includes this Flash update; to see which version of Chrome you’re running, click the 3-bars icon to the right of the address bar and select “About Google Chrome.”
IE10/IE11 and Chrome should auto-update their versions of Flash. If your version of Flash on Chrome (on either Windows, Mac or Linux) is not yet updated, you may just need to close and restart the browser. Chrome version 35.0.1916.153 includes this Flash update; to see which version of Chrome you’re running, click the 3-bars icon to the right of the address bar and select “About Google Chrome.”
The most recent versions of Flash are available from the Adobe download center, but beware potentially unwanted add-ons, like McAfee Security Scan). To avoid this, uncheck the pre-checked box before downloading, or grab your OS-specific Flash download from here.
Windows users who browse the Web with anything other than Internet Explorer will need to apply this patch twice, once with IE and again using the alternative browser (Firefox, Opera, e.g.). If you have Adobe AIR installed (required by some programs like Tweetdeck and Pandora Desktop), you’ll want to update this program. AIR ships with an auto-update function that should prompt users to update when they start an application that requires it; the newest, patched version is v. 14.0.0.110 for Windows, Mac, and Android.




Firefox 30 was also released today, if you don’t want to deal with a browser that has 59 separate security issues. 🙁
Furthermore, Microsoft has a new website to keep track of your bulletins according to your Operating System and MS software installed
htttp://www.mybulletins.com
http://www.mybulletins.com
No, baby, no. This is a squatter site.
That is NOT a Microsoft site!
http://whois.domaintools.com/mybulletins.com
Maybe he meant mybulletins.technet.microsoft.com
Yes it redirects to the Microsoft sub-domains
http://www.pcworld.com/article/2207346/microsoft-simplifies-security-updates-with-mybulletins.html
Still, Microsoft doesn’t own it, and why would PCWorld obfuscate their link? The text doesn’t match the link. Maybe they had it wrong and “fixed” it, but they need to fix it right and change both.
There are vulnerabilities in all browsers. At least Chrome and Internet Explorer use low-privilege processes/protected mode (on Windows at least). With Firefox afaik any successfull exploit will get the same privileges as the current users which might be bad.
https://www.mozilla.org/security/known-vulnerabilities/firefox.html
This is the kind of trolling that makes it harder for Good Security to happen. When someone says “59 vulnerabilities in one patch cycle! look how insecure!” there is no qualitative basis for that claim, but the layperson will latch on to it psychologically. Take my boss, for example. He swears that IE is “more secure” than Chrome because quantitatively there have been more CVEs and Bugfixes in Chrome than in IE11. He is an otherwise smart person, coming to a completely backward conclusion because internet trolls spin security research to their own ends, and we are all less secure as a result.
This possibly?
http://mybulletins.technet.microsoft.com/
That one worked, its pretty slick actually.
Adobe AIR’s full version archive age:
http://helpx.adobe.com/air/kb/archived-air-sdk-version.html
The version of Polycom CMA Desktop we use uses AIR and expects v4.0 to be installed before it will install, so I had to install that, then Polycom would install, then it’s OK to let AIR update itself.
Piece-a-cake. Heh
Something uses Adobe AIR? First, I’ve heard of anything…
Yup, that and the 2 Brian mentioned make 3 whole programs. lol
Java 7 Update 60 is available.
http://www.java.com/en/download/installed.jsp
There are no security updates in that Java release.
There may or may not be a security problem fixed by Java 7u60, but the bottom of http://www.oracle.com/technetwork/java/javase/7u60-relnotes-2200106.html
references a now resolved security library issue.
I have one such (Air) program. It is run on Mac OS X though. Not sure that matters.
I develop stuff. Usually in .Net for work. I had thought about learning Java, but after following Mr. Krebs I have dismissed it completely. Same with any programming platform by Adobe.
Maybe I’m over reacting, or “over vigilant”, if there is such a thing.
Greg
There’s nothing particularly wrong with Java the programming language. Java the plugin is a different matter.
I couldn’t believe Ninite took the flash update off their site – whatta rip! >:(
Brian: Your choice of the adjective “whopping” in your 2nd sentence “a whopping 66 distinct security holes in Windows and related products” is spot on.
Thesaurus.com suggests these synonyms for whopping: “colossal, massive, big, extraordinary, gargantuan, giant, gigantic, great, huge, immense, large, mammoth, mighty, monstrous, mountainous, prodigious, tremendous”. In the original context, “phenomenal” and “unbelievable” would have also been appropriate, too. 😉
Microsoft Security Bulletin MS14-035 – Critical – https://technet.microsoft.com/library/security/ms14-035
“This security update resolves two publicly disclosed vulnerabilities and fifty-seven privately reported vulnerabilities in Internet Explorer. The most severe of these vulnerabilities could allow remote code execution if a user views a specially crafted webpage using Internet Explorer.”
Somehow, the idea that the number of updates needed would asymptotically decay over time doesn’t appear to apply to the Windows IE product; instead, it seems the reverse is happening. Although I don’t really care for the way Chrome updates itself automatically without asking, it and Firefox are certainly safer browsers with which to surf the web.
These are fine browsers, but you are fooling yourself. The others have equal count of bugs, but bundle them.
In fact …
https://www.nsslabs.com/reports/browser-security-comparative-analysis-report-socially-engineered-malware
Be aware you don’t fall for stereotypes!
In fact IE11 + EMET has *never* been hacked.
Now again, the others are fine browsers, but the MS bashing is just not factual, sorry…
Am I the only one suspicious that such a large IE update came out so soon after EOL for XP?
Though the fact that the majority of vulnerabilities are in newer versions is also troubling.
I’m not suspicious. Honestly, just between .NET and Internet Explorer, there are huge batches of security updates every other month, if not every single month.
Now imaging trying to support a corporation that needs to approve, test and finally deploy those updates. Except it’s not the same patch, because you have Windows 7 x86, Windows 7 x64, Windows 8, Windows 8.1, Windows Server 2003, Windows Server 2008, Windows Server 2012. For IE, a lot of corporations have IE 8, 9, 10, and 11. x86 and x64 variations for all of those too. And you’ve got offices all over the world/country that need to be patched, often in different languages.
This is getting to be a nightmare. “What did you study in college? Oh, I got a Masters in Software Patching.”
Amen. It is crazy insane the poor quality of the software programs that are being released, -and from hence emerges the continued demand for these Patch degree-holders. Sloppy science.
But what to do? My USPS mail delivery has obviously borrowed the tech designed shoddy-suit as I didn’t even get a utility bill last month.
Well, the version numbers are correct. Thanks Brian. I now have have two versions of the Flash plugin listed on my Mac’s Flash Preference Pane – instead of the usual one.
To wit: NPAPI Plug-in version 14.0.0.125 is installed.
PPAPI Plug-in is not installed.
(Gee…that’s nice to know!?)
Word on the street is that the latter is called “Pepper” and reportedly has a working relationship with Google’s Chrome Browser (which I do not have installed nor do I understand the complexities thereof).
Tuesday Afternoon by the Moody Blues is such a nice song. Don’t cha think? My psychiatrist doesn’t care for it at all, however. ;-]
Must be that bit about “those gentle voices I hear”!
For those who, like myself, prefer to not reboot their systems more often than four or five times a year, here’s a tip on mitigating CVE-2014-1817:
In Firefox about:config set
gfx.downloadable_fonts.enabled = false
in Chrome add –disable-remote-fonts to the start-line in the “properties” section of the icon.
Obviously I have not run IE for years and will never touch it again.
Wish I had know about these sooner. Fancy downloadable fonts have been one of the major points of vulnerability over the years. That and it’s a nearly useless feature.
For those who do want to arbitrarily block font download on IE, that is a per-Zone option in the Security tab of Internet Options, and can also be configured and enforced via Group Policy. Given that font exploits do happen every so often, I opt to disable that feature, and I haven’t missed it. I think that option has existed since IE5, but I’m not dredging up a Win2000 box to verify it 🙂
For those looking for some more easy wins to harden their IE installations, my next nominees would be to enable ActiveX Filtering, enable Enhanced Protected Mode and 64-bit tab processes if you have 64-bit Windows, and install Microsoft EMET for good measure. The EPM and 64-bit settings are in the Advanced tab of Internet Options.
NoScript can selectively block downloadable fonts…
Today’s patches (4 of them) auto-installed on my Windows XP system! I guess it’s a tossup which will get delayed longer: XP’s actual “sunset” or ObamaCare’s employer mandate.
Those patches on XP were for Office 2007. No IE or core OS patches.
The reverse engineering of the Internet Explorer bugs will be happening as we speak, and XP users will be targets of these ‘0 days’ in the coming weeks.
Brian, be aware that IE10/11 don’t automatically update Flash Player. *Windows 8.x* will automatically update the ActiveX version of Flash Player, since Microsoft shipped it as an included component. It therefore gets updated by the Windows Update mechanism. This is why the ActiveX Flash Player updates that come from Microsoft Update are only for Win8.x. e.g. http://support.microsoft.com/kb/2966072
On Win7, which didn’t ship with an Adobe Flash Player, it would be up to Adobe’s own updater to check for AFP updates. It would be great if Adobe and Microsoft did team up to deliver Flash Player updates (for all browsers) via Microsoft Update. Heck, and Adobe Reader as well. But then what would they call it… Microsoft-and-Adobe Update? 😉
I installed this month’s batch of updates on Win8.1 with no hangups. On my Windows Home Server 2011 box, it failed to install three of ?eight? on the first shot, so I had to do them on the next boot.
Trying to manually update Flash Player to todays version in Firefox 30 on Windows 7 32bit. I am having issues with the installer saying “Failed to Launch Application”. I have tried completely uninstalling and then reinstalling with version 14. Anyone had similar problems?
as a JackOfAllTrades(tm) IT guy stuck with supporting IE9 for some reason… screw updating flash player all the time.
I tried running the Flash Player update for Firefox 30 under XP and got a message “failed to run application”
Flash player version stayed at 13.0.0.214.
Bob, see my post above, I am having similar issues under Win 7 FF30