Three Israeli defense contractors responsible for building the “Iron Dome” missile shield currently protecting Israel from a barrage of rocket attacks were compromised by hackers and robbed of huge quantities of sensitive documents pertaining to the shield technology, KrebsOnSecurity has learned.
The never-before publicized intrusions, which occurred between 2011 and 2012, illustrate the continued challenges that defense contractors and other companies face in deterring organized cyber adversaries and preventing the theft of proprietary information.
According to Columbia, Md.-based threat intelligence firm Cyber Engineering Services Inc. (CyberESI), between Oct. 10, 2011 and August 13, 2012, attackers thought to be operating out of China hacked into the corporate networks of three top Israeli defense technology companies, including Elisra Group, Israel Aerospace Industries, and Rafael Advanced Defense Systems.
By tapping into the secret communications infrastructure set up by the hackers, CyberESI determined that the attackers exfiltrated large amounts of data from the three companies. Most of the information was intellectual property pertaining to Arrow III missiles, Unmanned Aerial Vehicles (UAVs), ballistic rockets, and other technical documents in the same fields of study.
Joseph Drissel, CyberESI’s founder and chief executive, said the nature of the exfiltrated data and the industry that these companies are involved in suggests that the Chinese hackers were looking for information related to Israel’s all-weather air defense system called Iron Dome.
The Israeli government has credited Iron Dome with intercepting approximately one-fifth of the more than 2,000 rockets that Palestinian militants have fired at Israel during the current conflict. The U.S. Congress is currently wrangling over legislation that would send more than $350 million to Israel to further development and deployment of the missile shield technology. If approved, that funding boost would make nearly $1 billion from the United States over five years for Iron Dome production, according to The Washington Post.
Neither Elisra nor Rafael responded to requests for comment about the apparent security breaches. A spokesperson for Israel Aerospace Industries brushed off CyberESI’s finding, calling it “old news.” When pressed to provide links to any media coverage of such a breach, IAI was unable to locate or point to specific stories. The company declined to say whether it had alerted any of its U.S. industry partners about the breach, and it refused to answer any direct questions regarding the incident.
 “At the time, the issue was treated as required by the applicable rules and procedures,” IAI Spokeswoman Eliana Fishler wrote in an email to KrebsOnSecurity. “The information was reported to the appropriate authorities. IAI undertook corrective actions in order to prevent such incidents in the future.”
“At the time, the issue was treated as required by the applicable rules and procedures,” IAI Spokeswoman Eliana Fishler wrote in an email to KrebsOnSecurity. “The information was reported to the appropriate authorities. IAI undertook corrective actions in order to prevent such incidents in the future.”
Drissel said many of the documents that were stolen from the defense contractors are designated with markings indicating that their access and sharing is restricted by International Traffic in Arms Regulations (ITAR) — U.S. State Department controls that regulate the defense industry. For example, Drissel said, among the data that hackers stole from IAI is a 900-page document that provides detailed schematics and specifications for the Arrow 3 missile.
“Most of the technology in the Arrow 3 wasn’t designed by Israel, but by Boeing and other U.S. defense contractors,” Drissel said. “We transferred this technology to them, and they coughed it all up. In the process, they essentially gave up a bunch of stuff that’s probably being used in our systems as well.”
WHAT WAS STOLEN, AND BY WHOM?
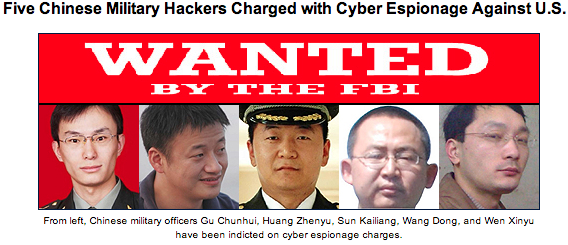
According to CyberESI, IAI was initially breached on April 16, 2012 by a series of specially crafted email phishing attacks. Drissel said the attacks bore all of the hallmarks of the “Comment Crew,” a prolific and state-sponsored hacking group associated with the Chinese People’s Liberation Army (PLA) and credited with stealing terabytes of data from defense contractors and U.S. corporations.
The Comment Crew is the same hacking outfit profiled in a February 2013 report by Alexandria, Va. based incident response firm Mandiant, which referred to the group simply by it’s official designation — “P.L.A. Unit 61398.” In May 2014, the U.S. Justice Department charged five prominent military members of the Comment Crew with a raft of criminal hacking and espionage offenses against U.S. firms.
Once inside the IAI’s network, Comment Crew members spent the next four months in 2012 using their access to install various tools and trojan horse programs on systems throughout company’s network and expanding their access to sensitive files, CyberESI said. The actors compromised privileged credentials, dumped password hashes, and gathered system, file, and network information for several systems. The actors also successfully used tools to dump Active Directory data from domain controllers on at least two different domains on the IAI’s network.
All told, CyberESI was able to identify and acquire more than 700 files — totaling 762 MB total size — that were exfiltrated from IAI’s network during the compromise. The security firm said most of the data acquired was intellectual property and likely represented only a small portion of the entire data loss by IAI.
“The intellectual property was in the form of Word documents, PowerPoint presentations, spread sheets, email messages, files in portable document format (PDF), scripts, and binary executable files,” CyberESI wrote in a lengthy report produced about the breaches.
“Once the actors established a foothold in the victim’s network, they are usually able to compromise local and domain privileged accounts, which then allow them to move laterally on the network and infect additional systems,” the report continues. “The actors acquire the credentials of the local administrator accounts by using hash dumping tools. They can also use common local administrator account credentials to infect other systems with Trojans. They may also run hash dumping tools on Domain Controllers, which compromises most if not all of the password hashes being used in the network. The actors can also deploy keystroke loggers on user systems, which captured passwords to other non-Windows devices on the network.”
The attackers followed a similar modus operandi in targeting Elisra, a breach which CyberESI says began in October 2011 and persisted intermittently until July 2012. The security firm said the attackers infiltrated and copied the emails for many of Elisra’s top executives, including the CEO, the chief technology officer (CTO) and multiple vice presidents within the company.
CyberESI notes it is likely that the attackers were going after persons of interest with access to sensitive information within Elisra, and/or were gathering would be targets for future spear-phishing campaigns.
Drissel said like many other such intellectual property breaches the company has detected over the years, neither the victim firms nor the U.S. government provided any response after CyberESI alerted them about the breaches at the time.
“The reason that nobody wants to talk about this is people don’t want to re-victimze the victim,” Drissel said. “But the real victims here are the people on the other end who are put in harm’s way because of poor posture on security and the lack of urgency coming from a lot of folks on how to fix this problem. So many companies have become accustomed to low-budget IT costs. But the reality is that if you have certain sensitive information, you’ve got to spend a certain amount of money to secure it.”
ANALYSIS
While some of the world’s largest defense contractors have spent hundreds of millions of dollars and several years learning how to quickly detect and respond to such sophisticated cyber attacks, it’s debatable whether this approach can or should scale for smaller firms.
Michael Assante, project lead for Industrial Control System (ICS) and Supervisory Control and Data Acquisition (SCADA) security at the SANS Institute, said although there is a great deal of discussion in the security industry about increased information sharing as the answer to detecting these types of intrusions more quickly, this is only a small part of the overall solution.
“We collectively talk about all of the things that we should be doing better — that we need to have better security policies, better information sharing, better detection, and we’re laying down the tome and saying ‘Do all of these things’,” Assante said. “And maybe a $100 million security program can do all these things well or make progress against these types of attacks, but that 80-person defense contractor? Not so much.”
Assante said most companies in the intelligence and defense industries have gotten better at sharing information and at the so-called “cyber counter-intelligence” aspect of these attacks: Namely, in identifying the threat actors, tactics and techniques of the various state-sponsored organizations responsible. But he noted that most organizations still struggle with the front end of problem: Identifying the original intrusion and preventing the initial compromise from blossoming into a much bigger problem.
“I don’t think we’ve improved much in that regard, where the core challenges are customized malware, persistent activity, and a lot of noise,” Assante said. “Better and broader notification [by companies like CyberESI] would be great, but the problem is that typically these notifications come after sensitive data has already been exfiltrated from the victim organization. Based on the nature of advanced persistent threats, you can’t beat that time cycle. Well, you might be able to, but the amount of investment needed to change that is tremendous.”
Ultimately, securing sensitive systems from advanced, nation-state level attacks may require a completely different approach. After all, as Einstein said, “We cannot solve our problems with the same thinking we used when we created them.”
Indeed, that appears to be the major thrust of a report released this month by Richard J. Danzig, a board member of the Center for New American Security. In “Surviving on a Diet of Poison Fruit,” (PDF) Danzig notes that defensive efforts in major mature systems have grown more sophisticated and effective.
“However, competition is continuous between attackers and defender,” he wrote. “Moreover, as new information technologies develop we are not making concomitant investments in their protection. As a result, cyber insecurities are generally growing, and are likely to continue to grow, faster than security measures.”
In his conclusion, Danzig offers a range of broad (and challenging) suggestions, including this gem, which emphasizes placing a premium on security over ease-of-use and convenience in mission-critical government systems:
“For critical U.S. government systems, presume cyber vulnerability and design organizations, operations and acquisitions to compensate for this vulnerability. Do this by a four-part strategy of abnegation, use of out-of-band architectures, diversification and graceful degradation. Pursue the first path by stripping the ‘nice to have’ away from the essential, limiting cyber capabilities in order to minimize cyber vulnerabilities. For the second, create non-cyber interventions in cyber systems. For the third, encourage different cyber dependencies in different systems so single vulnerabilities are less likely to result in widespread failure or compromise. And for the fourth, invest in discovery and recovery capabilities. To implement these approaches, train key personnel in both operations and security so as to facilitate self-conscious and well- informed tradeoffs between the security gains and the operational and economic costs from pursuing these strategies.”





Where can I download the full report?
http://www.cnas.org/surviving-diet-poisoned-fruit
I was referring to the CyberESI’s “lengthy” report
Guess: the materials sought were English language not Hebrew. I would bet the hackers grabbed whatever they could but the odds they have many people skilled in reading Hebrew, particularly on the fly, is much lower than having people skilled in English looking for anything relevant in English.
Maybe we should switch to Navajo.
” Maybe we should switch to Navajo.”
Everyone uses Google translate now, even crooks.
The reason Navajo worked so well in WW2 was obscurity. There was little documented about the language and few speakers left making it the ideal candidate for a code language. Fast forward 70+ years and with the numerous forms of documentation around the Navajo language, especially in response to their critical role in the war, and their is little, if any, obscurity remaining in the Navajo language.
Yeah, but just try to understand what a native speaker of the Navajo language is actually saying if you aren’t already someone with years of focused training in it.
I’m not sure what your getting at here. Understanding someone else communicating in another language is basically the first step to learning that language. Would you be able to speak Chinese to a native speaker without knowing the language? Of course not. But if you had say, a book on Chinese, that might make things a bit simpler would it not? Would you be able to speak Chinese armed only with a book? Probably not right away, but that book would sure help wouldn’t it? Were talking about China here. If the info. was important enough do you really think they couldn’t spend a couple million paying someone to learn and understand the language? Relying on a language barrier for security is doable, but the only protection you have is obscurity. When entire books, movies, and scholarly articles on that language come out, sorta makes that impossible.
I’ve done a lot of work in China over the past 20+ years, and spent a lot of time in and around Navajo country over the past 40+ years — book-based learning in either language wouldn’t get you squat in the way of real understanding on how to speak or use it (even if you could read and comprehend the Chinese pictographs, though reading would help with the Romanized version, Pinyin). Trying to converse on that basis alone with any native in both locales would likely generate a highly quizzical expression of confusion and perhaps peals of deep-belly laughter at the malformed and ultimately nonsensical efforts of the speaker’s efforts, since both languages employ subtle tonality and cadence which affects not only the delivery of emotional content but can determine the actual intended meaning of words employed (and thus how accurately that meaning is understood by the listener).
Navajo was quite effective as a spoken code in the 1940s because there were really no Japanese (or Germans, for that matter) who were aware of, much less familiar with it and little or no exposure to the culture or its actual usage — a huge difference by comparison with a similar arcane and difficult language like Welsh that has both a written and spoken lexicon, with which both enemy countries had some exposure and experience to draw on from prior diplomatic exchanges with the UK in their military intelligence circles.
Navajo isn’t listed among the languages which Google Translate offers in its drop-down options, and while I have seen written passages (in newspapers and online stories) in that language, it appears to be a modern Romanized construct analogous to Pinyin (though with a LOT more apostrophes employed).
I think your missing the point here. Taking out established language altogether for second:
You have a book written in language B. This book has information you would very much like to know, but your can only read language A. Now, if you don’t have a clue what the language is, you could do some things like design computer heuristics, or get a language expert in to try and decipher the language, but chances are you wouldn’t be able to glean too much from it unless you had some kind of Rosetta stone (the ancient tablet written in stone, not the software) to help guide your efforts.
Now lets take that same scenario:
You have a book written in language B. This book has information you would very much like to know, but your can only read language A. However, there is a plethora of source material about language B available, and is accessible with only a very trivial effort and expense. There are even experts on language B that you could hire to interpret the data into language A for you.
Would you be able to communicate with others in language B after doing this? Probably not coherently, but does that matter? Not at all, your only goal is to decipher the text and learn what it says, anything else is secondary.
The difference being computers were rarely utilized in the 1940s, now they can if not decode the message, at least identify patterns and get a rough idea of the content it would contain. They might not be able to completely decode it, but even if they simply identify what language it is then finding someone who could decipher it becomes much easier.
If in your example either ‘A’ or ‘B’ is not an established language of some sort, then the non-established one will not have extensive (much less widespread) usage. Someone capable of communicating effectively in the well-used one but not the other will be left without a sufficiently broad database (set of analytical opportunities) to parse, compare, contrast and test possible equivalence in meaning UNLESS there is a third language (‘C’) to make that association, just as was the case with the original Rosetta Stone. Your response presumes there is a someone who is not only aware of the unknown language, but has a sufficient degree of understanding in it to effect a rudimentary translation and is willing (or made under extreme duress) to do so — that set of conditions simply did not exist in WW2 with the Japanese and Navajo code-talkers, particularly the last condition which is exactly why US military personnel were under strict orders NOT to allow the code-talker under their direct command to be captured alive.
Today is a different story for those particular languages (and computers can parse and test far faster and more accurately), though still not necessarily so for some ancient ones — archeologists and anthropologists have made significant advances in understanding Mayan hieroglyphs during the past 20-30 years, but only after extensive effort building a substantial database of examples, coupled with some pretty incredible flashes of insight and luck finding a partial copy of a Mayan codex buried in some European archive (Germany, as I vaguely recall) that had escaped from being burned by Spanish priests after the wholesale subjugation of New World native cultures to Catholicism by force.
My understanding is that the Navajo code talkers not only spoke in their own (obscure) language, but used coded language for particularly sensitive terms as well – “apple” instead of “grenade”, for example. The combination of an obscure language with some elementary cryptography would make breaking language-based security that much more difficult.
What you are referring to is a substitution cipher.This is a basic tenant of cryptography, dating back to Alexander the great. Even during the 1940’s it was considered weak, but the combination of an obscure language couple with it made a substitution cipher a great method of preventing enemy interception. The problem is the Navajo language is no longer obscure. Since the end of WW2 there has been extensive documentation of the language even documentaries and movies about it, resulting in a upsurge of Navajo speakers; effectively breaking any obscurity remaining in the language. The only thing your left with at this point is the substitution cipher, which even 70 years ago was considered weak. Security through obscurity only works if there is some kind of obscurity.
“tenet”, not “tenant”.
Is it worth recalling that it was the Japanese reliance on a belief in the “obscurity” of their language that made their comms one of the least secure of the WW2 major powers?
When the guys at Unit 61938 are busy hacking through a contractor’s system, they are constrained by time and in the volume of material they can acquire.
Therefore they troll through a system trying to find useful-looking files, minimising their footprint by issuing a minimum of commands and only moving stuff identified as useful-looking. They don’t have time to sit down with “a book” and figure out what each hebrew word means as they go along.
As the article states – the hacking concentrated on english-language files/directories for the very obvious reason that the hebrew-language files/directories were obscure to them.
Hence it is empirically clear from the known facts of the hacking action in question that a file/directory system employing the Navajo language would have provided greater security than one that uses the english language.
All Israeli tech companies use English for all documents. Especially with projects like these which are cross company/continent together with Boeing and LM.
It appears that, once again, the original point of intrusion was a spear-phished email. It’s not that high-tech! It is no wonder that smarter malware writers have switched their targets from individual PCs to businesses/organizations/governments. The payoff is better, the reluctance to report intrusions is probably worse, and the lack of involvement in security is also worse.
Regards,
We live in a world with incredibly complex computer systems that take hundreds of man hours to implement and significant resources to maintain and harden that can be defeated by a single user. Its so much easier to attack a business by crafting one spam email than it is to try and engineer an advanced threat to penetrate the various levels of security in place.
Enjoyed the read. fyi two typos:
form/from – “that were exfiltrated form IAI’s network during the compromise.”
companies/campaigns – “were gathering would be targets for future spear-phishing companies.”
What’s the point of using the comments section to notifying Brian of a typo in the article? Even if Brian corrects the typo, thanks to your comment, everyone is still made aware of the typo.
If you click on “About Author” at the top of the page, there’s a contact form where you can e-mail Brian directly.
+1
What I always enjoy about China is their ‘great firewall’. They know everything about everything coming into the country and see fit to filter out what they don’t want entering.
Now contrast that with all the malicious traffic leaving the ‘great firewall’. Somehow at that point they don’t care what type of traffic leaves the country.
Because they’re China.
To them, all internet is fair game.
Now our NSA is becoming the same way.
The prroblem that happens with control over the internet is it isn’t known when to stop. That goes with offense as well. We spy on China all the time, too, but so does almost every country spy on every other country. We even spied on Germany and we are friends with them. We probably spy on Britain and vice versa. Israel gets spied on by Palestinians and vice versa.
Cyber-espionage is all-too-real in all atmospheres.
Lets say USA started the spy stuff much years earlier than chinese or all others
in 1850 USA allready started
Occasionally this great firewall extends into North America, I assume they are hacking routers and switches to get a similar obfuscating effect. Last I heard a few years ago they were even bouncing this off satellites into South America.
The Great Firewall is more concerned with the flow of information and censorship for political reasons than it is with security.
Most obscure or encrypted traffic will get through unless the endpoint is blacklisted. Whereas standard HTTP is scrutinised to the Nth degree, contextually blocked, frequently injected, and probably logged.
The so called “Chinese great firewall” has the same problems as those Israeli companies have. Securing a company with a firewall does not mean that the company is secured against cyber attacks.
Article states that the ‘discovery’ pieces should be invested in more, but even Danzig puts it last.. “And for the fourth, invest in discovery and recovery capabilities.”
Reminds me of sending via the ‘Reply All’ button, THEN realizing that you hit the Reply All rather than Reply..
onward
I’ve run across a couple of articles recently that say the Iron Dome is a big bluff, that it really doesn’t work. Any truth to that?
“The evidence that shows Iron Dome is not working”
http://thebulletin.org/evidence-shows-iron-dome-not-working7318
Here’s hoping that the People’s Army has invested big chunks of $ imitating Iron Dome.
I would think the Israelis would not be that interested in blocking this, if it is true, because the hit on Israeli civilians would make good world news and garner sympathy like that for the Palestinians.
How long to you think they can hide that, if it is fact? I’d think the citizens of Israel would riot at that attempt. It is true that Iron Dome does not fire at every rocket that comes from Gaza – the reason being, the fire control already knows it is a miss. Those rockets are notoriously inaccurate
I’ve been watching Iron Dome’s development for years through many of the DOD buzz and other forums, and the performance was down right impressive! Seems the Israelis did one better than our outdated Patriot system(which was definitely better than nothing).
Ed, the Iron Dome works. And works very good. They don’t don’t even launch a missle against a rocket if the trajectory of the rocket is known to fall in open spaces.
As someone who lives in Israel and unfortunately benefits from the Iron Dome system, I can attest to the fact that it works. Otherwise … there would have been a lot more destruction in Israel than there has been over the past 2 years since we started using it.
Sigh.
+1
So to counter-act the analysis of an MIT physicist with particular expertise in ballistic technology who was a technical advisor to the OTA, we have JCitizen’s speculation that ‘if this were true, Israel would riot’ and an Israeli speculating that if it were true, damage would have been worse over the last two years.
I find the former much more credible than the latter, particularly since there were only 32 rocket attacks in 2013, making only one of the year’s data on ‘relative damage’ before and after the Iron Dome relatively pointless.
I also read the article, unlike those who are handwaving it away with defenses like ‘the rockets only fire if it is determined a viable target will be hit’. Since the article is an analysis of contrail data, the Iron Dome obviously fired in the analyzed instances. Again, this is obvious if one actually reads the article instead of making knee-jerk replies.
Since the only defenses are purely speculation on how Israelis would react if the findings were accurate (and discounting them since the Israelis have not reacted in the manner predicted in said speculation), I can counter-speculate with at least as much credulity. If the MIT physicist and ballistic weaponry expert is correct (and I find him to be vastly more credible than anonymous forum posters), then it’s relatively easy to come up with numerous reasons that the IDF would be reacting precisely as it is:
1)Iron Dome, even with 5-10% effectiveness, is better than nothing
2)The rocket attacks are a terror attack, not one primarily aimed at direct physical casualties and damage. The attack is psychological, so a psychological defense is perfectly valid. If people believe the Iron Dome is making them safer, that is in and of itself a success.
3)In keeping with item 2, cognitive dissonance (even in forum postings) will help sustain the psychological surety. Those invested somehow in the program, whether because of nationalism or enthusiasm for the technology, will WANT to believe it works and will intentionally rationalize or ignore evidence to the contrary.
I here ya O M , especially on point one – but I was in the artillery, and counter battery fire is already a proven concept – when we’d pick up the incoming round, we’d answer accordingly in a matter of seconds. They were direct hits on the target. I was with the FAC officer and witness this in real time(this was 1980’s tech). So I think the radar on Iron Dome is accurate, but you arguments to effectiveness will probably never be proven, unless the results are an uprising of the citizenry for too high a failure rate.
I would think with the press flooding the neighborhoods over there, CNN, or the BBC would be all over the subject after just a few failures. Even with the thousands of rockets they’ve fired from Gaza, only three have found their mark that I recall – heck they need to reload iron dome just like any missile battery, so this may have occurred between resupply missions for all we know.
Just to clarify, the old technology attacked the launcher, this new “Star Wars” tech attacks the actual incoming round – of course.
JCitizen wrote “the old technology attacked the launcher, this new ‘Star Wars’ tech attacks the actual incoming round”
Counter-battery fire is probably two orders of magnitude easier than hitting a bullet with a bullet. All you had to do is calculate the incoming round’s trajectory, reverse-engineer it, and fire one of your own to land in their lap. However, their round landed, regardless of what you did. If their round contained a nuclear warhead, the people in the vicinity would have a very bad day.
One of the problems with Iron Dome is that it needs to strike the incoming missile pretty much head-on. If it strikes the tail, the warhead will continue on its original course (with a little bump to one side) due to basic physics.
If things continue as they have been, we will soon see a definitive test of Iron Dome. It won’t be too long before Israel has built-out the entire West Bank, so there won’t be as much uninhabited land for rockets to land on. If the number of missiles which strike buildings rises, Iron Dome will be proven to be a failure.
A matter of course. I do remember when Iron Dome was not existent in Israel, and the news reports cited many civilian casualties. Back then the rockets were less numerous and smaller and less effective. Now Hamas uses new longer range Khaibar-1 M302 rocket.
The excellent civil defense shelter programs are the main reason very few people are killed in Israel.
-www.jpost.com/Defense/Study-Civil-defenses-cut-86-percent-of-deaths-from-Gaza-rockets-345676
-blogs.reuters.com/great-debate/2014/07/25/israels-iron-dome-is-more-like-an-iron-sieve
All true. I’ll add #4:
4) The military-industrial complexes of U.S. and Israel have invested a great deal in the concept of missile defense. It would reduce their profit and credibility if the world learned that the many U.S. tests, which the U.S. government advertises as proof of its technical prowess, were gamed. All of the tests so far have been conducted with the interceptor team knowing the time of launch, trajectory, speed, etc., none of which would be known regarding an adversary. And even so, they have missed more than they have hit.
“by tapping into the secret communications infrastructure…”
Wouldn’t that be illegal?
I believe they tapped into the communications network the hackers had set up illegally within their own network, or at least that’s how the proceeding statement reads to me. In which case, no, its not illegal to tap/monitor a system illegitimately setup within their own network.
depends. theoretically, no. But it can become a gray area if you, are, in fact, inside the network, part of it, but not the owner of it. I.E., School networks. the IT admins are allowed to sniff, but put a student at the computer lab into the equation, he’s technically doing it to the network he is allowed to use, but doesn’t mean he won’t be liable if he sniffs traffic that INCLUDES others’ data,
A school is different than a private corporate network. If someone gains access to your corporate infrastructure they don’t get some kind of squatters rights to use it. The company still owns the hardware, licenses the software, and pays for the data connection; they have every right to determine what should or should not be transmitted over that network.
“To implement these approaches, train key personnel in both operations and security…”
I believe companies need to invest in training ALL personnel in at least basic IT security practices. We can spend all of the money we want on detection and prevention systems, but if something happens like your entire HR department opening a trojan laced ZIP file from an unknown sender, none of the money spent on IT systems matters. At all.
This is just another example of that happening. I feel bad for the engineers and admins that get the blame for these types of incidents, even though they have usually done everything they could to prevent this.
While I don’t disagree with you, how does IT OPSEC translate into small business? While in this case the data is more sensitive than most; No matter how much training you give Marge in HR, she is still going to click that UPS tracking link for the package she never ordered. The weakest point of any IT infrastructure is the users. Hell, Microsoft had a breach not too long ago because an employee clicked a phishing email. If one of the biggest tech companies on the playing field hasn’t figured out a way to stymie human stupidity, how on earth does an organization consisting of 1 or 2 IT folks divide up enough of their day to train dimwitted users and continue to run the organization as a whole? While I don’t have a better solution in mind, every organization I have been a part of for the last 10 years has included some form of IT training around this kind of thing, and invariably someone always falls for similar scams. The problem isn’t preventing users from following through, the problem is catching intrusions as soon as they happen, and there is no really good way to do this as yet, because the playing field keeps changing.
The ONLY solution is making it so dummy clicking the links cannot do anything… Any malware or links scrubbed, neutralized, or blocked taking her out of the picture.
“The ONLY solution is making it so dummy clicking the links cannot do anything… Any malware or links scrubbed, neutralized, or blocked taking her out of the picture.”
In theory, this sounds great. In practice, unless you block all links in all emails, there is no way to prevent potentially malicious links from slipping through.
Its not easy, but honestly out of 100 people how many are going to click a link? Usually at least 1. Proxies, host scanners, web filters, etc all play a role, but fundamentally this problem will never get adequately solved just by telling people not to click on things.
Why is stuff this incredibly critical to Israel allowed anywhere near an internet connection? Sometimes making data impossibly painful to access IS THE POINT. Sheesh.
Because that’s just not an option anymore. If you haven’t seen what’s been going on since the smartphone revelation and the internet of things, people want access to information wherever they go. Pulling the plug, even on top secret data, just isn’t possible. Even if an organization has the best IT team in the world, if the CEO or high level exec wants access to the top secret military missile schematics from their tablet, IT cant just say “no” no matter the security concerns.
IT can certainly say no to the executives. The executives should know better than to ask, or at the very least to override IT when they tell the executive to micturate vertically on a fibrous cable.
Absolutely, in a perfect world IT security concerns would trump the CEO’s convenience, but in reality IT departments of every size are forced to implement poor to terrible solutions “because management said”. I’m not saying this is the case everywhere, or even most places, but there are numerous businesses out there than have a fully staffed IT department who’s even basic security suggestions are disregarded. Do we know if this was the case here? No. But it is a possibility.
Porgie. I agree with you comment but the CyberESI’s “lengthy” report may answer some of the questions if one could review it. From what the article implies the technology from the US was under export control and the documents may not have been all that sensitive. If they were sensitive and the companies were in the US then yes, there would be no internet connection unless it was a violation of US procedures. Plug in hardware to these networks would be restricted also, no PADs in other words.
Securing a network against penetration is relative simple. But that is not all. The majority of security breaches are performed physically! To implement security against penetration from the outside (like Internet), you do the following:
The network is physically designed in layers. The first layer has connection to other networks like Internet. The security is here is mostly implemented by firewalls, scanners and antivirus software. All transfer of data (in and out) is arranged here (and no, no sensitive data).
All other layers from the network are heavily secured. First, all computers, terminals and other devices do no carry disk drives, USB, COM and LPT ports, so nobody can copy something from a terminal. From these layers, it is not possible to access the Internet or any other network system. Mobile phones will not work here (electronically blocked).
The next layer is designed to access different company departments and functions. All devices on the network are guarded by monitoring software (what users do the whole time they are connected) and cameras, which are monitored by people in a central location.
All data, which are sensible, are stored on storage and accessed by terminals and other devices only in separate rooms.
This is not hard to implement. It’s relative cheap, but you need to use your head or better, common sense. So for small companies, it’s easy to implement. For larger companies it is a bigger problem though.
And that is not all. Profiling must be implemented too. With other words, every person, terminal and major process in the network must be monitored and its behavior at the network registered. A profile must be applied for each of them. In case monitoring detects a change in the profile (or behavior), security must interfere immediately.
And then some words about education. You don’t start educating people in the company, who are using the system on a daily basis. No, you start with senior management. If they refuse, it’s a sign of incompetence and the security officer will refuse them physical and electronic access. That is mostly enough. If senior management knows and understands, everything else will fall in place by the changes senior management requires of the organization.
If you think that is extreme, it isn’t. It’s not a game. Working in the so called Hi-Tech is not playing games. It requires knowledge. If you don’t have the knowledge, don’t work at a Hi-Tech company and you don’t deserve a fat salary sitting on your behind making noise and looking interesting.
The principle of exceptions applies:
* If you have bedbugs in your home, you destroy them and no exceptions. Only one exception means you have bedbugs again.
* If you have a network, you secure it electronic and physical. No exceptions.
China needs to be blocked from the web permanently. They want to censor everything to keep their people from starting a revolution, Tienanmen square ring a bell, then stay in your own country and research and develop your own technology instead of stealing it from the rest of world. China is a leach on the world scale plain and simple.
Obvious troll is Obvious.
Does Google do Navajo? Also, typo pickers, give it a rest. Thanks!
Google translate doesn’t by default, but a quick google search will turn up numerous books on the Navajo language fairly easily.
“At the time, the issue was treated as required by the applicable rules and procedures,” IAI Spokeswoman Eliana Fishler wrote in an email to KrebsOnSecurity. “The information was reported to the appropriate authorities. IAI undertook corrective actions in order to prevent such incidents in the future.”
Gosh this sounds an awful lot like any Israeli news report about anything they screw up. The coverage of the GAZA situation is a lot like this statement. They mess up and kill a few hundred extra people and it’s just a little technical difficulty, that’s all.
What WE lost YOUR missile designs? Nah was not us, you must have given them to us by mistake along with over 1 billion dollars to deploy them.
One big mistake apparently deserves many more. IRON DUMB.
What is the purpose of this article? Old news from 2011 about security leak of Israeli know-how that happened in US and most probably coincided with RSA hack and later attack on Boing. Why Israeli companies are even mentioned? Why now? Krebs is running out of themes to run?
Go home Israeli Defense Ministry, your drunk.
Krebs says they’re “never-before publicized intrusions.” Could you please cite the public source where you read about these intrusions before this week?
I am a strong believer that most of the IP numbers related to mainland china should be blacklisted for ongoing abuse
Why are we taxpayers spending a billion (or more) dollars for the ‘israelis’ to slap a star-of-david sticker on our Patriot missile systems?
A couple of reasons — the Israelis have been far more focused (politically, militarily and economically) on a robust R&D effort to improve the basic Patriot system capabilities by comparison with the US over the past several decades, and they exist within a region which provides a regular, ongoing missile test range experience.
Presumably, part of the deal is for the US to gain some of that R&D benefit to make improvements in our version.
That is correct. They do the same in French, Germany, the UK, previously in South America, South Korea and other countries all over the world. There are even such projects with Russia!
The profit for the US defense is enormous.
It’s similar like outsourcing the R&D and it saves billions.
Experience proves that the profit of such outsourcing in Israel is the most profitable.
“STAR of DEATH”
Israel CLAIMS they were hacked ….. in order to coverup their SALE of American funded technology. Or did Israel GIVE it to China as Israel prepares NEW-sponsors after America has been bled dry. —- “Once we squeeze all we can out of the United States, it can dry up and blow away.” — A comment made by Benjamin Netanyahu to Jonathan Pollard (convicted traitor and spy) upon exiting Pollard’s jail cell.
not another Israel conspiracy. Sure, Israel isn’t innocent with malware, but neither is Egypt, neither is Syria, Libya, Iran, Iraq, Russia, or China.
At least Israel tries to be our friend.
For sure!! I’d sooner believe that! In fact if anything was compromised, I sooner believe it was a sham target to make the attackers believe they got something. The Israelis are not as stupid as most of the US forces networks, which are so cumbersome as to probably be impossible to defend.
I disagree.
Israeli’s are good in short term R&D projects. Their weak sides are specifications and analysis. Do you know that in Israel more then 96% of all IT projects fail if they take longer then 3 months? This is the case in commercial, governmental and military projects. Get the specifications and reports from the Bank of Israel, there you can read it and more.
The reason for this is the lack of discipline, knowledge and education.
On the other side, they are extremely good in short term projects. The majority of those projects succeed (more then 60%). I used to call this always “… working with a wet finger in the air …”.
Interesting Wim Vincken! I also understand the Israelis have an information sharing agreement from the US DOD, and are deeply intertwined with US defense networks. That would also explain their vulnerabilities – US defense networks. HA! 🙂
Well, this is gonna rile some people, but I think it has merit. It’s no secret the West has created nations and seated governments more times than will likely ever be completely known. That’s how Israel came to be. ‘
A few minds after WWI saw value (oil) in the idea for a number of reasons, but the one put forth was to create a state for the Jews because they had been run out of their homeland thousands of years before.
The idea went on the shelf till WWII, when oil became paramount to the industrialization of the West. WWII had also established global routes and ports in all the best harbors everywhere. After the war business was quick to take over those routes and ports and turn them into profits. It was time to give life to the idea of a homeland for the Jews and it didn’t take long. In 1948 the Palestinians were driven back and the State of Israel created in their place.
But the West’s purpose was not so noble as practical. The growing need for oil and the abundance of it in the Middle East … we needed an attack dog in the heart of that area. And we have one.
The West, with the U.S. in the lead, has seen to it that Israel is weaponized and technologically equal to any potential threat.
The choice of that homeland was also a big mistake. Jerusalem is sacred land to a number of religions, not just Judaism. In addition to Moses’s birthright, it’s where Christ was crucified, where Mohammad was lifted up to heaven and where the Buddha achieved Nirvanna.
If anything, that vortex of belief and faith to so many should have been declared a World Heritage Site and protected from all harm for all time. It certainly shouldn’t have been handed over to the Jews.
Equally duplicitous was the pronounced reason to give the Jews back their homeland. If that is a moral goal, there are hundreds of millions of us that need to pack up and leave where we are. Nor does it matter that we’d have no idea where to go.
But there is no import to this any longer. The goal is peace. The new flag is little different than that of the ’60s. Make love not war has transformed into make money not war. We are finally realizing that war destroys assets and lines the pockets of a small few.
That’s all.
The information will be sold to ISIS (not the ISIS spay agency with Sterling Archer) who will use it to begin their global Islamic Thug caliphate.
“We are finally realizing that war destroys assets and lines the pockets of a small few.”
I’d like to introduce you to my friends, Blackwater, Northrup-Gruman, Lockheed-Martin, Boeing, General Dynamics, Raytheon, L-3 Communications, GE, Pratt & Whitney, and many others who made 235 Billion dollars last year from the combined sale of arms and armament, these companies collectively represent a significant portion of the top 100 companies in the world. War is good for business, and business is good. Evidently if anyone has realized, no one is doing anything about it.
It seems like some major institutional appearing honeypots might come in handy here. Surely it’s already being implemented.
Also I just wanted to say I noticed a typo in the above and fixed it.
😉
not to get political, but why in the heck are we calling these people our friends, then, exactly. It’s obvious they’ll stop at nothing to destroy us. Russia spies on us all the time.
Communist USSR has roots in hackers, at the end of the empire. It still lives on. So does it in China. Conficker is from there, and now the RBN is hiding there if I’ve heard correctly.
I’m sure for everything they’re doing to hack us, the NSA is doing something worse to them. I suspect the reason the US doesn’t make a bigger stink about cyber warfare/espionage from China/Russia/etc. is that we’re just as guilty of it as they are.
Why in the world are computers containing classified and sensitive military information and design documents connected to the internet? There is absolutely no single valid reason for that.
Security is a mindset, not an add-on. Regardless how well you protect something, if it is connected to the internet it can be hacked. If you don’t want it hacked, don’t connect it to the internet. It _is_ that simple.
Boeing had to share the confidential 700+ file(s) with IAI .. .we expected Boeing to send a protected team to fly to Israel and hand them a physical copy of the files?
They did. Or better, that’s the protocol.
But then those files were stored on the servers, where various people had access to.
You’re absolutely right. I’m thinking the same thing while I’m reading the article. How in the HELL are the systems that contain that sensitive data/information connected to the internet in the first place? That’s government security 101. These Israeli companies are saying it’s “old news.” No, they just want to limit the bad press they’re getting. In reality, they should immediately lose these defense contracts, and other firms that have a basic security infrastructure in place should take over.
From my knowledge of the topic, a US firm would never win a contract like this, unless they already had a secure network (a “box”, not connected to the internet) built, audited, and accredited. Sure, there are other ways that a “SCIF” could be compromised (Snowden), but it wouldn’t happen over the internet by Chinese hackers.
Elisra Group, Israel Aerospace Industries, and Rafael Advanced Defense Systems all need to be removed from these contracts, until they prove that they can handle secure data.
don’t be stupid. i was working with those named israeli firms. they have a parallel computing systems that are NOT connected to internet.
those materials were leaked in US. RSA hack, then Boing penetration, there you go.
the only reason Krebs is mentioning Israel and Iron Dome here is because it is on the news.
Krebs, really, shame on you for trying to make more publicity on this. if one were a real journalist, the first question would be: which american counter-party those names israeli companies were working with in 2011. that is your leak. but i guess you already know that, right?
Okay – we know who the key players are. That wasn’t so difficult to find out because they’re in China and they’re protected by China. There’s nothing that the US will do since we have large commercial interests there and no one wants to upset Big Corporation Money (and there’s every possibility that China may be spying for the US – people poo poo the idea, but with the NSA under a microscope … you never know …).
Isreal on the other hand, couldn’t care less about China. Time for Isreal’s HaMossad leModiʿin uleTafkidim Meyuḥadim to switch gears from World War Two War Criminal assasinations to Chinese Hacker Assasinations.
Infantile fantasy.
So in your mind the US is collaborating with China to hack Israel to get missile specifications that the US sold/gave to Israel in the first place? How does that even work? Why on earth would the NSA contract out to China for this? Even with the NSA under “the microscope” (which they really aren’t, the Snowden leaks are things the NSA has ALREADY done, and have triggered little to no additional NSA oversight) why would they allow an enemy nation free reign to spy on other Americans when they have proven they can do it so well already?
Also, are you saying Israeli intelligence should infiltrate China and assassinate hackers? Forget about the ill will this would breed, and how this would virtually guarantee China would begin fighting a proxy war with Israel if not outright conflict; What purpose would it serve other than guaranteeing China would focus more efforts on Israel?
You don’t know that.
This penetration is only one occurrence, which is published only now.
Normally and commonly “stealing” of sensitive data is done locally. A simple USB disk is being used, or a small optical disk or a hard copy. There is no way to determine if externals have already all the data or not.
In security, you assume the worst and the whole world has the data. Unless you secure it physically and electronically.
Are we sure it was a honeypot attack. And not a pooh bear.
Ever read the country of origin of the workers of these companies. Isreal probably want locals. Damn spell check on tablets. But check out the amer government version of h1b. Come over as students, think of the bear, and sleepers.
Grandma writes sleeper, new ways adapted, and so it goes on and……..
Don’t be too sure that Iron Dome has shot down all those rockets. Israeli scientists have examined those claims and determined they are not true.
See http://www.haaretz.com/opinion/how-many-rockets-has-iron-dome-really-intercepted.premium-1.508277.
See also http://thebulletin.org/evidence-shows-iron-dome-not-working7318.
I’d sooner believe MIT’s figures, but Haaretz leans just far enough to the left as to be incredible to me.
Love seeing heroes hacking out evidence from terrorist States. Go, Anonymous!
Chinese hackers are heroes? You realize this is the same group of individuals that stole from American companies recently as well right? Also, the “evidence” they stole was classified and/or sensitive American technology.
There are numerous state actors who are employed to go into online forums and promote the idea that the patently illegal actions undertaken by their state is legal, even heroic.
In the time leading up to the Russian election protests (not that long ago) I was arguing with a similar actor on another site. He ended up disappearing from the forum in short order, because he was redirected to Russian forums to discredit citizens who disagreed with their government. And it’s not just a guess, either… someone else on the site tracked him down on a Russian language site doing exactly that. Using the same names everywhere may make their lives easier, but it makes tracking them down easier too.
This guys are Dangerous
a quick observation on brian’s post:
http://www.nytimes.com/2014/06/30/us/sky-isnt-falling-after-snowden-nsa-chief-says.html
NSA chief Adm. Rogers is suggesting the same approach, namely reducing the scale such that the breaches are constrained.
And the august Scientific American had a short piece by Alex Pentland from M.I.T. which suggests folks “scatter the haystacks.”
While I’m pleased to see folks understanding the need to de-scale,including the creation of intentionally inefficient systems, I think folks are still missing the need effectively assess the intrinsic value of data. The valuation still tends to be based on the organisation’s use in an organisational centric model. With the iron dome example, they gave up externalities, ( the aegis.). They protected data of value x to themselves, value y to others, thus a breach ends up giving data of higher value (x+y).
The organizational centric valuation leads to folks allowing access that in hindsight seems foolish (not all that different from a teen oversharing on fb who later regret the postings).
Anyway, I suspect that a careful review would show that at least some of the breached information did not need to be stored online in such a readily available fashion. As a simple fix a librarian that checks in/out sensitive docs could implement the speed bump. it would trigger scale alerts and could implement the proverbial second factor authentication.
folks are on the right track, yet i still feel we are missing the very important scale vectors of size and valuation.
We covered this topic and the possible ramifications in the U.S. here: https://entrisk-technologies.com/cyber-attack-of-israels-iron-dome-missile-defense-system/ Check it out!
If you have the responsibility over a network, which is connected to a wider network, like Internet, that means that your system (was/) is being penetrated or will be penetrated.
The fact that those perpetrators could access the system shows the lack of discipline of the network users and the security authorities of the network and the failure of the internal organization at those companies. Think! Access the system via email? Most of the none-experienced computer users know NOT to open an executable attachment. They probably used a firewall, some outdated antivirus software and they thought they were safe.
The fact that those perpetrators could continue using that access and expand on it shows the failure of the security authorities of the network. There was no manual network monitoring in place!
It also shows that the network is not designed correctly (or at all).
Proper networks in such companies must be designed in several layers. When a layer is penetrated, they can’t access the next layer. You can easily secure a layer in the network, which allows only physical connections (not remote). With other words, you need to be physically present to access one layer to the other.
This type of architecture of one or more networks is not expensive to implement. It’s all based on common sense. But the problem here (and in most cases) is that senior management overrides this because they want easy access and user friendly usage of their internal systems. They don’t assign a security officer with great authority. For those companies it’s not a priority.
Network and computer discipline is always the key for good security.
I bet that everyone there is allowed to access the systems with their laptops. I bet too that the computers being used in those companies are standard computers with USB slots and open LPT- and COM ports. And I also bet that those companies really didn’t change their security. And I also bet that most of their data is being copied by people internal in the company and being exchanged to externals for money.
I also bet that there is no physical monitoring in place, no electronic monitoring of the use of workstations and laptops and mobile devices, no cameras, nothing, no secure rooms for terminals with high security clearance.
Heck, I’ve designed layered network systems without any use of any toys (like anti-virus software, scanners and firewalls) and nobody could penetrate the core systems, not even physically.
And logic and experience also shows that in such organizations there is no physical protection against spying. It must be so easy to simply copy information on a flash disk and walk out and collect loads of money from someone interested in the data.
The same logic and experience shows that those companies didn’t change their network architecture and they are still open for cyber attacks.
BS. Israeli sells China all the gear they get from America. That’s well known.
you are a genius. did you come up with this nonsense by yourself?