I’ve long recommended that small business owners and others concerned about malware-driven bank account takeovers consider adopting a “Live CD” solution, which is a free and relatively easy way of temporarily converting your Windows PC into a Linux operating system. The trouble with many of these Live CD solutions is that they require a CD player (something many laptops no longer have) — but more importantly – they don’t play well with wireless access. Today’s post looks at an alternative that addresses both of these issues.
As I noted in my 2012 column, “Banking on a Live CD,” the beauty of the “Live CD” approach is that it allows you to safely bank online from any machine — even from a system that is already riddled with malware. That’s because it lets you boot your existing PC into an entirely different (read: non-Windows) operating system. [Not sure why you should consider banking online from a non-Windows PC? Check out this series].
The device I’ll be looking at today is not free, nor is the the tiny dongle that enables its ability to be used on a wireless network. Nor is it an actual CD or anything more than a stripped-down Web browser. But it is one of the safest, most easy-to-use solutions I’ve seen yet.
The device, called ZeusGard, is a small, silver USB flash drive that boots into a usable browser within about 30 seconds after starting the machine. The non-writeable drive boots directly into the browser (on top of Debian Linux), and if your system is hard-wired to your router with an Ethernet connection, you should be good to go.
Nearly all Live CD solution have one glaring weakness: They typically are not usable over a wireless connection. The Live CD solution I most frequently recommend — which is based on a version of Puppy Linux — technically can work with wireless networks, but I found that setting it up is not at all intuitive, especially for people who’ve never used anything but Windows before.
 My review copy of ZeusGard came with a tiny USB wireless Wi-Fi adapter, which makes jumping on a wireless network a complete breeze. When you boot up with both ZeusGard and the adapter plugged in, ZeusGard automatically searches for available wireless networks, and asks you to choose yours from a list of those in range.
My review copy of ZeusGard came with a tiny USB wireless Wi-Fi adapter, which makes jumping on a wireless network a complete breeze. When you boot up with both ZeusGard and the adapter plugged in, ZeusGard automatically searches for available wireless networks, and asks you to choose yours from a list of those in range.
Assuming access to your wireless network is secured with WPA/WPA2 (hopefully not the weaker WEP) , click the “properties” box next to your network, and enter your network’s encryption key (if you need to see the key in plain text while you’re typing, tick the box next to “key”). Hit “OK” and then the “Connect” button. Once you’re connected, click the down arrow at the top of the dialog box and select “Exit to Browser Session.”
This is the second generation of ZeusGard, and I’m looking forward to seeing the next iteration of the device. ZeusGard is produced by Bancsec, a consulting firm that advises financial institutions on ways to beef up security (think Sneakers). Bancsec CEO J.B. Snyder said the next version should include a streamlined wireless setup, and will offer users more options inside the browser session (in the version I tested, for example, ZeusGard automatically shuts down after 30 minutes of use).
At $24.95 for the basic ZeusGard and $14.95 for the wireless adapter, this device is likely to be more appealing to small businesses than the average Internet user. But if you need or want wireless capability in a USB-based “Live CD” solution, ZeusGard is one of few easy-to-use options currently available.
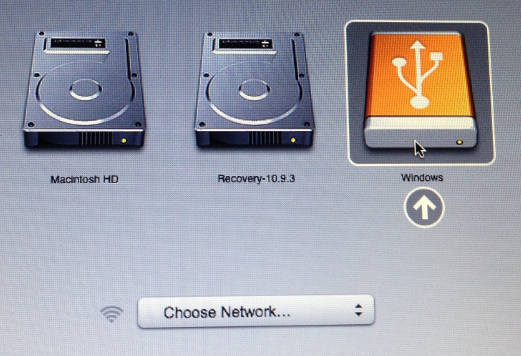
To get ZeusGard working on a Mac, hold the “Option” key while booting up, and select the volume labeled “Windows” (yes, I realize this is counter-intuitive, since the whole idea behind booting into a live CD is that you’re not in Windows).
Getting ZeusGard (or any other live distribution, for that matter) working on a Windows PC may be a bit more involved. Rather than reinvent the wheel, I’ve excerpted and modified the following instructions from my Banking on a Live CD post.
We next need to make sure that the computer knows to look to the USB drive first for a bootable operating system before it checks the hard drive, otherwise ZeusGard will never be recognized by the computer (this only needs to be done once). When you start up your PC, take note of the text that flashes on the screen, and look for something that says “Press [some key] to enter setup” or “Press [some key] to enter startup.” Usually, the key you want will be F2 or the Delete or Escape (Esc) key.
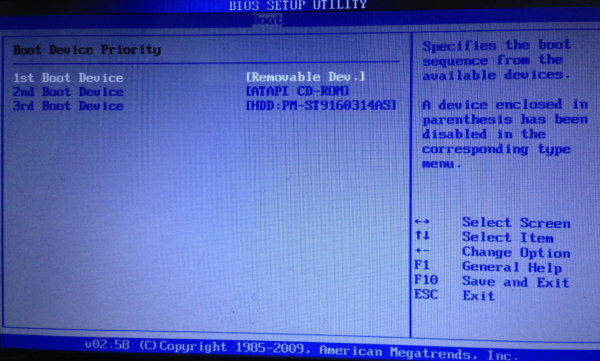
A Windows BIOS screen. If you’ve done it right, the “removable dev” option should be listed as the 1st Boot Device.
When you figure out what key you need to press, press it repeatedly until the system BIOS screen is displayed. Your mouse probably will not work here, so you’ll need to rely on your keyboard. Look at the menu options at the top of the screen, and you should notice a menu named “Boot”. Hit the right arrow key until you’ve reached that screen listing your bootable devices, and then hit the Enter key What you want to do here is move the Removable Devices option to the top of the list (it may be listed as merely “Removable Dev”). Do this by selecting the down-arrow key until that option is highlighted, and then press the Shift and the “+” key on your keyboard until the Removable Devices option is at the top. Then hit the F10 key, and confirm “yes” when asked if you want to save changes and exit, and the computer should reboot.
Unless you know what you’re doing here, it’s important not to make any other changes in the BIOS settings. If you accidentally do make a change that you want to undo, hit F10, and select the option “Exit without saving changes.” The computer will reboot, and you can try this step again.
If you’ve done this step correctly, the computer should detect the USB drive as a bootable operating system, and boot into ZeusGard.





What do you think about doing your banking on a Chromebook?
I don’t think much of it… I already don’t like Google knowing everything that I do online already
I don’t suppose you’ve thought about ceasing using their search engine, which records everything that you do on it, forever?
The alternative is called startpage.com which shields you with proxies.
Once you’ve done this, make sure to remove the USB drive, plugging it in only when you want to boot from it. Otherwise it may not boot into Windows again (until you remove the USB drive).
“The non-writeable drive boots directly into the browser (on top of Debian Linux),”
I was going to just suggest to use Debian before I even got into reading more, then to find this is based on Debian anyway.
“Nor is it an actual CD or anything more than a stripped-down Web browser.”
So if it’s Debian then I take it the browser is Iceweasel (or Gecko based)? And then even if its read only, I’d still hope there’s some way of keeping up with the browser updates (if you can update it).
I don’t know, I wouldn’t pay for this personally- just buy the hardware (wireless stick, usb drive) and install Debian on the USB drive. I mean, if your average person can figure out how to burn Tails (also Debain based and aimed at average people who aren’t programmers or whatnot) then this shouldn’t be too hard.
Also adding to that,
” The trouble with many of these Live CD solutions is that they require a CD player (something many laptops no longer have)”
You can also get external USB cd/dvd/bluray/whatever drives.
I’m not trying to shoot down this ZeusGard thing, I just want to make people aware of other options. It’s entirely up to them what they want to use to secure their own computers. Whatever works.
I think a lot of people are missing the target audience for this device: The person who’s responsible for managing the books in a small business (that has no IT department) and has never used anything but Windows her whole life.
It’s great that there are so many readers here who feel at ease running batch files, burning this or that, configuring here and there, etc. And obviously there are alternatives to this (I begin this post with a mention of and link to just that). But I like this approach because it makes things secure without also making it complicated.
One would think financial institutions themselves would *want* and perhaps require or incentivize their business (and maybe also consumer) customers to use just such a system for online banking.
Tinba and other malware is so sneaky at modifying live websites, capturing keystrokes, and intercepting even 2 factor authentication codes that only a live CD/USB system on a locked down OS could provide (some) protection. No help against a hardware keyboard logger though.
Amen.
Why not use a VPN?
Because a VPN doesn’t address any of the relevant threats.
The primary threat is that malware has already successfully infested the local computer.
If that’s the case, using a VPN doesn’t help you. If you’re incredibly lucky and you have awesome IT managing your VPN, then you /might/ get a notice informing you that your VPN connection was making suspicious outgoing connections.
But, it’s worth noting that pretty much no one has caught anything this way. Certainly the Walmart case didn’t get caught based on IT detecting outgoing transactions. There was also a case of malware which had actually attacked some computers in one (or more?) of Microsoft’s labs. (iirc) That wasn’t detected by anything Microsoft did, they learned about it when someone blocked them or something. (Sorry, trying to search for that incident, which is from a couple of years back is hard…) — Iran didn’t catch Stuxnet this way either.
“It’s great that there are so many readers here who feel at ease running batch files, burning this or that, configuring here and there, etc.”
If you were using OpenBSD as an example I’d agree, but many main Linux distros (the buntu based, the Debian based, the Fedora based, etc) are pretty easy, especially for the sole task of web browsing to a banking a site. (if they can change a BIOS setting, they can burn a Linux disk) I’ve heard of many relief aid types in third world countries and the like who do pass out Linux dvds to help people (to have all the software tools to help build their lives up). I’m also seeing mainboard manufactures (like Asus and MSI) putting a type of embedded Linux on their boards to boot from these past few years (boot sector malware, or even just hard drive failures, it’s handy to have).
Basically, though Linux will never be mainstream for daily use, using it as a secondary OS for web browsing isn’t as alien or hard as maybe back in the 2000s. I swear though the main reason most banks don’t bundle a live cd for every customer is cause of the liabilities or bureaucratic type crap, or just ignorance.
But all the same, I’m commenting for those types who would be interested. If some people favor one thing or another I don’t really care so long as it works for them and gets the job done.
This is an excellent idea, but you also have to make sure the USB drive is write-protected once it is created. And the computer on which it is created should also not be compromised.
I would go with Vee.
Find a USB drive with physical write protection switch, install Deb and from time to time enable write and update this thingie.
Brian, this is absolutely great! Setting up a Live CD is on my long list of “things to do”, and although I can certainly do it, it will require an investment of time, so it is just not likely to get done very soon. This, on the other hand, is a no-brainer: $40 for safe banking? Sold!
I sent a copy of Puppy Linux to a client, and once I instructed this person how to change the boot sequence; it was no problem to get it to boot. We could have used a USB copy from On-Disc.com of course – but since a CD-ROM is available, that is the course of action. All they had to do, once it booted, was give it the ol’ WPA2 key and it was gravy from then on!! I never had such an easy time with totally changing someone off of Windows. Not that I’m anti Windows; but my clients are indigent as a matter of course!
“I never had such an easy time with totally changing someone off of Windows. Not that I’m anti Windows; but my clients are indigent as a matter of course!”
I’m always seeing people who try to hook first time Linux users either by Duel Booting methods or other methods that just end up alienating the end users. It’s all about software, not so much the OS kernel. The way to see if a person is seriously ready to use Linux as a main OS is to get them to use as much open source software, that you’d find on Linux, on Windows. Basically, instead of Microsoft Office use Libre Office. Instead of IE, Firefox or Chrome. Instead of Photoshop, Gimp. etc. Cause it is one thing to get used to a new OS, but then to get used to using all the new software- it’s just a complete overload of information. But even then, you know, we’ll always need that secondary backup Windows system for that one thing that is just too much of a pain to setup (or sometimes impossible) on Linux.
So again, at least a separate backup system (like a laptop) that runs Windows and then becoming accustomed to most the software you’d find on a Linux distro is all that’s needed.
It seems like the biggest hurdle is to get them to be brave enough to play with it, and they quickly find out it has all those alternates you listed.. I tell them, “After all nothing writes to the hard drive, so you can’t mess up!!”
If they have a junker that needs revitalizing, they could also easily install it, as this type of distro will pretty much run with anything.
There is no doubt not all newer versions of Ubuntu and similar will run on hardware that is older; so I do warn them on that. Puppy is no threat along that route (yet).
Promo article… pretty much any live cd I’ve tried has wireless functionality and with little effort could be imaged onto a usb drive to. Linux Mint has to connect to a wireless network functionality and works a charm.
Why not just install a Linux OS along Win and switch to it for secure tasks? And you’re certainly guaranteed airtight security with a Chrome Book.
Because those are writeable, and because this is aimed at someone who doean’t know how to partition a drive, make the partition bootable, and install Linux on it.
If so, they can buy a Chromebook, not install any Chrome browser extensions and they will then have the most secure solution available on the market.
I think all these posts are missing the point. Of course I “could” do XYZ and install ABC configuration. But by the time I download the software, figure out the inscrutable setup instructions, debug it, and finally get it working, the time spent will dwarf what $40 of my time is worth plus the two minutes spent ordering on Amazon. Of course, if you actually LIKE doing Linux configuration, and would enjoy doing this, then that’s a different matter altogether . . .
You got it! I can make a lot more money attending to the stock than I can fiddling around writing USB drives.
I’ve been using Knoppix live CD for long time and I can only recommend this one. It can be run from USB Flash (with little help of LinuxLive USB Creator), has great support for various wirelles hardware and it comes with Java, in case you need this plugin (my bank used Java-based frontend for online banking for years).
Or, just use a Chromebook, which is also a Linux OS that boots into a browser in less than 30 seconds.
No, the Chromebook runs the OS from read-write memory and persists information across restarts, so it is vulnerable to malware. The point of this device is to have a guaranteed clean boot from read-only memory every time. If an infection somehow happens, it is gone after a restart.
Chromebook has a secure boot feature, which makes it impossible for any malware to run, except a malicious Chrome browser extensions. But if you don’t use extensions, you have the most secure platform on the market.
It’s booting from writable media, so it’s not as secure. Chromebook secure boot is just file validation, so for example, Google’s private key could be compromised. Or, Google’s OS build could be compromised. Or . . . you get the picture. Booting from read-only media is more secure.
Chromebook is easier than a live CD or bootable USB for the average user. I cannot find one instance of any compromise of a Chromebook (minus pwn2own 1 time). I know of no Chromebook related malware in the wild. Seems like a safe and convenient solution to me.
Chromebook – Secure: less, as I described. Convenient: less, since you have to carry around two machines now. Expensive: more. Yep, it’s definitely a tradeoff.
So what version of which browser is on this?
Also how do you update the browser? what if the version they have on here is discovered to have a huge security hole, it wont be fixed as its not writeable
so do you then have to buy another one?
In order for any browser security hole to be exploited, you would need to visit an infected website, and have malware in memory first without rebooting. The drive itself can’t be infected since it’s read-only hardware, so it guarantees a clean boot. Even if there is a browser hole, you’re safe as long as you go straight to online banking – that’s the whole point.
Right, but if the browser is exploited the payload could remain in ram until you actually reboot the system. It’s not entirely far fetched- it’s one reason they continue to update the Tails distro with patched software.
Another question regarding Online Banking and browser information is whether the browser on this stick is actually compatible with your Online Banking.
I know of an Online Banking Provider which will not support their own product if it is being used on any browser except for Firefox, IE, or Chrome on windows or Safari on Mac.
Kind of limiting for anyone using Linux. OF course, as long as it works, it’s fine. As soon as you have an issue, they tell you to log in from IE on Windows. Way to go.
Debian uses IceWeasel, which is a variant of Firefox that also reports itself to webservers as Firefox so it’s not as if the browser will be alien to either the user or to the website.
First of all, thanks Brian for this very informative and high quality weblog.
Regarding your tip, the safer option is to tell people to hit F12, F8 or whatever their BIOSes need while booting to invoke the Boot Selection Menu (nearly all BIOSes have this). This has the advantage of not booting from any USB stick you happen to forget in your PC ports.
Permanently changing the boot order poses a security risk as any infected USB stick will be able to gain full system access.
Cheers,
chross
That’s all great, but my current and newest computer doesn’t have usb device as a boot option.
It’s a fairly new HP, and I was trying to install linux on it using an ISO thumb drive I have set up and worked on a few older dells I own.
I was planning on checking to see if there is a bios update, but frankly I was surprised that a win7 machine couldn’t do this out of the box ( I was dumping linux on xp boxes)
On some BIOS you must have the USB storage device plugged in to see it as a selection in the list of bootable devices.
The non-write ability is an important aspect. Moving from LiveCD to LiveUSB usually adds write ability by default since the installer assumes you want update ability. Maybe a bad assumption?
I have installed Live Linux to the hard drive either alone or dual-boot with Windows. I configured the default to non-persist mode as the original LiveCD versions were. The same could be configured on a LiveUSB install. To update select the persist mode before the default timeout. Keep in mind, updating the installed LiveUSB may be harder than rebuilding the LiveUSB since package managers are geared towards full installs not Live installs. Even if you are compiling from source you may find the install script is not Live friendly.
Support for wireless from Live or distros in general has improved dramatically. I think the popularity of android has caused wifi manufacturers to better support non-Windows OSs.
I use a bootable WinPE3 Windows 7 style DVD that works with all wired/wireless networks.
http://www.911cd.net/forums//index.php?showtopic=23931&hl=
You could also do banking on a third party browser using a encrypted thumb or hard drive like what you can buy from Apricorn
If only Imation hadnt purchased IronKey and ruined that line….they built an amazing product called TrustedAccess that contained a portable virtualbox image that booted to the browser only, and went over their network to only whitelisted banking sites. No duel boot, no need to leave windows, no need to worry about configurations, etc, etc.
I think the original owners of IronKey still own the TrustedAccess product, but I am not sure if it is still being developed. Imagine being handed a secure, encrypted drive that allowed for you to use online banking in just about as secure of an environment as there is, when you opened a new bank account. Truly sad that there isnt a real market for this stuff…..
Anybody have any thoughts on using a separate piece of software such as Trusteer to help mitigate potential account takeover as opposed to devices which may require config most users will not be wiling to deal with.
So, I understand that even doing my banking and other vulnerable stuff by using my ubuntu-partition on my harddisk (I have ubuntu dual booting next to my windows 8.1) still isn’t waterproof, or is it? Should I really erase my ubuntu and go back to using my live cd?
Because users have to reconnect to wireless each time they may be vulnerable to WiFi honeypots like EvilAP or Pineapple wifi router which can be configured to look like a target AP and strip SSL and capture creds and inject code dynamically.
No solution will be 100% but the boot option does make for a harder target. The human side will always be the weakest link.
I’ve been interested in safer online banking for a long time. I’ve tried the Live CD approach but find it problematic because I use very long full keyboard passwords from a Password manager that are not practical to memorize. I use the maximum lengthen and strength that a site will allow, often in excess of 20 characters. In addition some sites won’t let you cut and paste passwords. The same would be true for me with the ZeusGard given that neither the Live CD or the ZeusGard have provision to use a Password Manager.
Has anyone found a work-around for this problem?
That’s actually a good point, most live cds don’t ship with a password manager. So unless someone is using an online manager like LastPast, you’d have to look for distros that ship with KeepassX (which is not yet fully compatible with regular Keepass for Windows, but there is a KeepassX for Windows).
What about Rapport and other security software? You will find them listed at http://features.techworld.com/security/3243386/the-10-best-online-bank-security-tools/ on the web. There’s some pretty good stuff there.
I work in the Banking industry. Why not simply use Trusteer? We are about to deploy Trusteer for our customers. They (Trusteer) advertise on this BLOG. Complicated tactics will not be adopted by small business users. High adoption rates come from easy to deploy and use solutions. A business user is doing more than just logging into and working in the business banking webportal. The user expects to be able to access and move in and out of other applications on their PC while working in the banking portal.
If you want to know who and when users log into a PC or laptop and what is installed… plenty of off the shelf apps do this. One of the best and cheapest is Computrace from Absolute. The corporate version does more than anti-theft tracking.
The reason not to trust stuff like this is that it doesn’t work. I’ve had malware show up on my computer exactly twice, and both times, several different anti-virus products (like Symantec) didn’t even notice it. I found it and eliminated it myself using Task Manager, Process Explorer, and RegEdit. There’s really nothing “complicated” about putting a USB key in and restarting your computer. It’s simpler than installing some “security” software that doesn’t do anything but give you a false sense of security.
I have been working in IT for twenty years. In IT Security for for the last nine. I can tell you for a fact that Trusteer works. The Computrace product is something that anyone traveling with a laptop should not be without.
It is more than just booting into an OS on a stick. Businesses have other apps that are needed. It is more than just logging into eBanking. By the way, no one makes a browser that is 100% secure. You also need to be realistic and remember a little issue called compatibility. EBanking sites and other business apps don’t work with every OS and Browser. They are written for the majority of the browsers and Operating Systems used by the masses.
Layered security, firewalls, web filters… Commons sense…
Do you really want to be responsible for your customers workstations IF they still get infected, loose money and sue you?
Brian, do you think this will work with a MAC Book Pro with a Flash drive ?
I know, probably a dumb question, but its a good price and I am hoping to get it to work on a new MAC Book Pro. I mainly use a PC for other purposes ( including Certification Classes 🙂 ) but I was/am interested in your opinion in this case.
Well, the computer in the picture at the top of the post is a Macbook Air, so I don’t see why it wouldn’t.
Re: “Should I really erase my ubuntu and go back to using my live cd?”
Yes, you should go back to the live CD. It will be safer. When you boot Ubuntu from your hard drive, you are exposing a writable device to whatever pile you step into on the internet. But you are still safer than had you booted Windows.
Removing the Ubuntu install from your hard drive is optional.
Thanks Dan,
Clear answer. Will return to my Live CD!
Marble Security (fka IronKey) has had something similar for some time for banks looking to secure customer online banking sessions. You get a Linux VM with a hardened Firefox browser, with an ecrypted keyboard driver, with no need to boot into a different OS. Unfortunately, not a whole lot of banks have adopted this security measure to provide their to customers.
+1
This is what I was talking about with TrustedAccess…I /believe/ Marble still has the product, but isnt developing for the consumer side, due to lack of adoption from banks to consumers. IIRC they have retargeted the product at the internal banking sector to depts like the wire desk and such.
Agreed, I did not see your post before I left mine. They had a great idea, but are focusing on enterprise MDM it seems.
Ironkey / Marblecloud no longer sell Trusted Access, and it looks like a previous IronKey exec actually recommends ZeusGard. VM’s are always subject to the security of the underlying host OS (weakest link), and the “encrypted keyboard driver” did really nothing at the hardware level. While perhaps less convenient, ZeusGard is a more secure option than IronKey.
How much risk is mitigated by running a live CD via VM player/workstation setup?
The main reason to run a Live CD (non-writeable) or USB (non-writeable). Is that you can be certain of the integrity of the operating system.
You will know that when you boot you do not have any spyware or malware installed. This provides you with the ability to securely conduct sensitive work such as managing financial transactions, trading stocks etc.
Running a VMware player or other hypervisor really has little impact on the end result as the LIVECD/USB does not require a hypervisor to boot/function properly.
Granted, but it’s not very convenient. Can you really say that a live CD option is ‘more’ secure when nobody really uses it?
A VM environment, while not as secure, would be easier to convince users to adopt and creating a much stronger improvement in your security posture than a mechanism that is ignored.
The problem is that the virtual machine manager could be infected, so after it boots the OS from CD, it could modify it in the memory of the VM. There are documented instances of malware that do this. However, as far as I know, there is no malware that can jump across the room onto a CD sitting in your drawer.
Thanks – that was what I was curious about and it gives me an angle to research. Would you have references to such? A quick google search shows only an impact against VMWorkstation 8
…
My thinking is that, while not perfect as it would retain any network vulnerabilities due to the passthrough NAT settings, and now the potential of a compromised VMM, a VM utilization would still greatly reduce the exposure surface due to browser issues.
You are absolutely right, you are safer running in a VM, if only because you can keep the browser “cleaner”. Also, it’s not an easy task to jump the wall between the host and guest, so you eliminate a lot of malware. Sorry if my previous comment wasn’t clear about that.
To your question, here is an article about malware that spreads from host to guest (the case we are talking about in this thread): http://www.cnet.com/news/crisis-malware-targets-vmware-virtual-machines/
Here is an article about the more “interesting” and difficult case of malware that spreads from guest to host. This is much more scary for malware researchers than for the general public: http://www.darkreading.com/risk/hacking-tool-lets-a-vm-break-out-and-attack-its-host/d/d-id/1131254
In summary, you are definitely on the right track, the goal is to make something that is easy to set up, more secure, and convenient enough that it will be used all the time!
Brian –
The caption for the BIOS image says: “A Windows BIOS screen.” Perhaps you should change it to “A BIOS screen” since the BIOS is the first thing to start up on a computer — before any operating system gets loaded.
I’ve never tried to use PuppyLinux in my laptop with a wireless connection, but I did just boot my HP ProBook with a Fedora 20 cdrom. I was able to choose my wireless network as usual. Of course, since Fedora is not a lightweight Linux, it is not the fastest, running as it does via a cdrom, but it is fast enough to do banking. Methinks Brian needs to expand his LiveCD horizons. And as others said, carrying a separate cdrom drive is not that bad of an option.