My phone and email have been flooded with questions and interview requests from various media outlets since security consultancy Hold Security dropped the news that a Russian gang has stolen more than a billion email account credentials. Rather than respond to each of these requests in turn, allow me to add a bit of perspective here in the most direct way possible: The Q&A.
Q: Who the heck is Alex Holden?
A: I’ve known Hold Security’s Founder Alex Holden for nearly seven years. Coincidentally, I initially met him in Las Vegas at the Black Hat security convention (where I am now). Alex is a talented and tireless researcher, as well as a forthright and honest guy. He is originally from Ukraine, and speaks/reads Russian and Ukrainian fluently. His research has been central to several of my big scoops over the past year, including the breach at Adobe that exposed tens of millions of customer records.
Q: Is this for real?
A: Alex isn’t keen on disclosing his methods, but I have seen his research and data firsthand and can say it’s definitely for real. Without spilling his secrets or methods, it is clear that he has a first-hand view on the day-to-day activities of some very active organized cybercrime networks and actors.
Q: Ok, but more than a billion credentials? That seems like a lot.
A: For those unfamiliar with the operations of large-scale organized crime syndicates, yes, it does. Unfortunately, there are more than a few successful cybercrooks who are quite good at what they do, and do it full-time. These actors — mostly spammers and malware purveyors (usually both) — focus on acquiring as many email addresses and account credentials as they can. Their favorite methods of gathering this information include SQL injection (exploiting weaknesses in Web sites that can be used to force the site to cough up user data) and abusing stolen credentials to steal even more credentials from victim organizations.
One micro example of this: Last year, I wrote about a botnet that enslaved thousands of hacked computers which disguised itself as a legitimate add-on for Mozilla Firefox and forced infected PCs to scour Web sites for SQL vulnerabilities.
Q: What would a crime network even do with a billion credentials?
A: Spam, spam and….oh, spam. Junk email is primarily sent in bulk using large botnets — collections of hacked PCs. A core component of the malware that powers these crime machines is the theft of passwords that users store on their computers and the interception of credentials submitted by victims in the process of browsing the Web. It is quite common for major spammers to rely on lists of billions of email addresses for distributing their malware and whatever junk products they are getting paid to promote.
Another major method of spamming (called “Webspam”) involves the use of stolen email account credentials — such as Gmail, Yahoo and Outlook — to send spam from victim accounts, particularly to all of the addresses in the contacts list of the compromised accounts.
Spam is such a core and fundamental component of any large-scale cybercrime operation that I spent the last four years writing an entire book about it, describing how these networks are created, the crooks that run them, and the cybercrime kingpins who make it worth their while. More information about this book and ways to pre-order it before its release in November is available here.
Q: Should I be concerned about this?
A: That depends. If you are the type of person who re-uses passwords at multiple sites — including email accounts — then the answer is yes. If you re-use your email password at another site and that other site gets hacked, there is an excellent chance that cyber crooks are plundering your inbox and using it to spam your friends and family to spread malware and to perpetuate the cybercrime food chain.
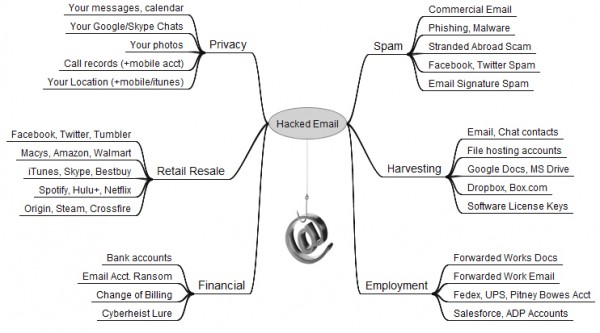
For a primer that attempts to explain the many other reasons that crooks might want to hack your inbox, your inbox’s relative market value, and what you can do to secure it, please see The Value of a Hacked Email Account and Tools for a Safer PC.
Got more questions? Sound off in the comments section and I’ll try to address them when time permits.
Update: As several readers have pointed out, I am listed as a special advisor to Hold Security on the company’s Web site. Mr. Holden asked me to advise him when he was setting up his company, and asked if he could list me on his site. However, I have and will not receive any compensation in any form for said advice (most of which, for better or worse, so far has been ignored).




Anyone surprised that a researcher would wait to reveal such a find “until right before BlackHat” hasn’t been paying attention. Nothing new there, move along… The point of BlackHat and DefCon and similar events is to wow the audience (and the press) with new findings, revolutionary hacks, and generally amazing stuff. Tools and proof-of-concept code are released AFTER the talks to get people to attend the talks and follow the presenter.
It’s not all posturing and puffery, it’s the way the process works.
If 400,000 sites were identified to be potentially vulnerable to sql injection that means Hold Security just scan millions of websites finding a vulnerability. This number is probably overated.
OK wow this makes a LOT of sense dude.
http://www.AnonGalaxy.tk
Hold Security already reported this 2 months ago. At that time with zero details. Now a bit more, but it is also introducing its new payed service to see if you are hacked.
Now don’t get me wrong, it is fine to earn money on work like this, but it feels in this case like recycling an old discovery for PR purposes …
Multifactor.
So true. +1
Information of this gravity should be recycled to a wide audience. The initiates of this domain may know it already, but perhaps they should helped others by spreading it rather than quibble about DefCon and PR
Charge it FREE: http://heraldmailmedia.com/news/tri_state/west_virginia/electric-car-charging-station-set-to-power-vehicles-in-martinsburg/article_f08e6190-f742-5dd2-b5ca-4bd8a078a0af.html
Charge cards not working so well and for $120 is that all you get for your money?
This looks like spam.
Why can’t the data be handed over to LE or a CERT to try and distribute.
What gives holt security the right to profit off selling this data.
Isn’t someone offering to sell data stolen about me , back to me technically blackmail?
What if the place used to store this data is compromised? Who is then liable ??
Russell Brandom at The Verge today parses the wording of the NYT and Hold’s own announcement, which make it clear the hackers initially bought pre-existing data from earlier hacks. He’s suggesting most of the huge number actually comes from these purchases of crummy old data from exploits resolved long ago, rather than any follow-up activity by these Russians. I’d be interested your response to a read of his piece.
Mr Krebs,
Aren’t you on the advisory board for Hold Security? If so, don’t you think you should recuse yourself from commenting on the veracity of Hold Security’s claims given this possible conflict of interest?
There are lots of others in the industry who are skeptical of the way this reveal is being handled by Hold Security.
Cmon Krebs, you love to use Hold Security and Alex as a go-to for your articles, but based on his exploitative money grubbing scheme you should move to someone else. His attitude is not worth giving free publicity too through your site.
I’m at blackhat too. Every discussion I’ve heard includes eye rolling that Alex is charging a fee to find out which provider is impacted. He’s not making many friends.
Did they simply discard compromised user names that were not email addresses?
Wait… Mr. Krebs, are you still on Hold Security’s advisory board? You’re listed as such on their website. Not disclosing this fact is making this look rather fishy. While I trust you as a professional, this is clearly a case where conflict of interest can come into account. Perhaps you should add a disclaimer to inform people.
I believe this news of this breach was actually announced six months ago. Here it is in SC Magazine.
http://www.scmagazine.com/files-containing-360-million-credentials-125-billion-email-addresses-located-on-deep-web/article/336211/
Why not contact the .5 million affected sites and inform them so they can inform end-users? Seems like they should know…
It’s a commodity.
http://www.citylab.com/design/2012/04/west-virginias-outlaw-toilet-bandit-explains-his-artistic-vision/1829/
With pay per breach, pay per flush can’t be too far behind. It used to work like nature’s calling. No more! Can’t you Hold it? We’ll find a free one!
Like LifeLock. Super reputable.
Heh! Heh! Yeah right! I forgot! 😉
Being on the advisory board of the company announcing this breach, which just so happens to be hawking a paid service to let you know if your addy’s been hacked seems… Fishy. At the least.
Shame on you for not disclosing your conflict of interest here, Mr. Krebs.
He DID disclose above… Not sure if you read the post all the way through or not…
Oh, the irony. Seems like Mr. Krebs is a bit on the good side of irony tonight.
Regarding Hold Security , which he’s an adviser at: “The ‘large hearted’ company has said it wants to help users, but… there is always a but.. there is no such thing as a free lunch. After discovering the breach and scoring a high-profile story on New York Times, the security firm is now demanding a fee from users who want to know if they are affected. This means users will have to shell out $120 simply to know if they are a victim.”
Source: http://www.scmagazine.com/files-containing-360-million-credentials-125-billion-email-addresses-located-on-deep-web/article/336211/
Seems like you got your inspiration from my ideia: indexeus.org
http://tech.firstpost.com/news-analysis/hold-security-wants-you-to-pay-120-to-tell-if-your-name-is-on-the-list-of-the-1-2-billion-compromised-accounts-228573.html
Can’t figure out why so many are upset with Br
Can’t figure why so many are upset with Brian and Hold Security.
I am grateful for all the information we get from Brian all the time (at no charge). And Hold Security has done all of us such a great favor by disclosing this massive breach. It is perfectly acceptable that they charge for their services. We need them to stay in business for those of us who are not computer geeks and need experts we can turn to for computer and identity theft support.
Brian you are a constant life saver and a BIG THANK YOU to Hold Security!!!
Hey, that’s too rich for my blood!
Anything that involves diamond
“We’ve seen two ways to use diamond in microwave technology both of which are potential career killers. The first is as a wide bandgap semiconductors. But diamond doesn’t offer a whole lot higher performance than silicon carbide, which is cheaper by a factor of Avogadro’s Number.
The second microwave application that diamond might be bandied about is as a low-cost heat sink. Hey, diamonds are called “ice” for a reason, this crystal has staggeringly high thermal conductivity. But when deposited as an amorphous film, the reduced thermal conductivity is not that much better some cheap metals.
Last, any industrial application of diamond will remind the public that diamond is just carbon, and should be cheap. Then you will have to deal with the DeBeers family, which wants us all to pretend that diamonds are worth multiple paychecks per carat. Some South Afrikaner with a crooked nose might come and break your knuckles for messing with diamond’s artificially high price. Yikes!” http://www.microwaves101.com/encyclopedias/390-microwave-career-killers
Now we’re getting ripped of on getting ripped off?
You got that right NotSA! Diamonds are so common in nature, that a perfect quarter carat diamond is actually only worth about $1.80! One of the worlds worst investments!
I don’t see how this has anything to do with the topic of the post. Why was it published here?
I wonder if Snowden had anything to do with this?
Krebs and Hold make a living consulting, investigating, and when appropriate, publishing results. All of these actions carry a certain degree of responsibility to disclose findings when it benefits the greater good and/or violates the law. However; timing, circumstances, and the extent of disclosure are all predicated on details which may be linked directly to client confidentiality and cooperation with law enforcement.
Fishy or not, we don’t know what we don’t know.
More concerning than spam, is that, where the compromised account details provide a login to an account on an eCommerce website, that account can be used for fraud. If the site has stored card details and does not perform any CVV checking on such cards, the fraud is fairly likely to succeed.
I know of several eCommerce websites that have been hit with thousands of login attempts to customer accounts, in what are clearly automated attacks (the latency between login attempts is too short and too regular to be a human).
A reasonable (from the attacker’sperspective) percentage login at the first attempt. And only one attempt is made. If the login fails, there’s no retrying of the password or another password, the ‘bot simply moves on to try the next account.
There are also low volume attacks, measured in tens of attempts, spread out over (say) an hour. Without some really decent heuristic analysis, it’s pretty difficult to determine whether the failures are customer finger trouble or an attack.
Schneier’s not convinced.
https://www.schneier.com/blog/archives/2014/08/over_a_billion_.html
On the credibility scale, let’s say that you’ve been at about 10 for me, until now.
Used-car-type sales pitches, based on fear mongering, can reduce one’s credibility. However, I understand that such risks must be taken, if maximizing revenue is the ultimate goal.
Hey,I got a question? Why the heck am I seeing comments spam on a security blogs website?? I noticed three or four adds here today.
I notified ZDNet not long ago,and they finally stopped theirs, after using a little shame on them.
Now as far as security goes,I initiated two factor authentication on every account that offers it,and never ever use the same pass word for other accounts. Also,be a little paranoid and check your accounts monthly at the very least or have some programs to do it and report. Things are only going to get worse as more and more people go online to do business. Be proactive!
Do we need to change all of our account passwords? It’s such a pain. (I’m not interested in one of those password-keeping services.) I don’t re-use any passwords for sensitive accounts.
The # of accounts found makes sense. Think of the websites underground that sell and trade accounts. They collect accounts for years and keep them in a database for later uses. I have worked for the same company for over 2 decades and in that time I have recorded spam mails that include groups of people who left the company years ago within the senders lists. The majority of spam goes to accounts that were harvested a decade ago. I am willing to bet that the majority of these accounts are from very old sources or breaches that are widely known. I had an e-mail address harvested in 1996 from a website. I still see spam mails with that e-mail address included in the sender list to this day, even though my e-mail system has been sending bounce backs for it for over 11 years.
Our best bet? Make the information they harvest useless. Multifactor, it’s not perfect, but I really do not see username/password alone acceptable anymore for any service that can be accessed from the internet.
The US$120 fee is bad enough, but Mr. Holden also “will ask you to provide an encrypted versions of your passwords to compare it to the ones in our database.”
Har.
Holden’s name is trash in the security community after all this. People at BH2014 were dissing this guy every chance they had.
yahoo has some of the highest hijack rates, out of gmail, outlook, and yahoo.
sql injection is child’s play.
and also, to respond to one person’s comment, no, not releasing method does not make it fishy. some secrets are best kept undetected, so it can’t be counteracted, until, of course, that is, it is leaked since it probably will, or found out through a backdoor against the whitehat himself, some day.