My phone and email have been flooded with questions and interview requests from various media outlets since security consultancy Hold Security dropped the news that a Russian gang has stolen more than a billion email account credentials. Rather than respond to each of these requests in turn, allow me to add a bit of perspective here in the most direct way possible: The Q&A.
Q: Who the heck is Alex Holden?
A: I’ve known Hold Security’s Founder Alex Holden for nearly seven years. Coincidentally, I initially met him in Las Vegas at the Black Hat security convention (where I am now). Alex is a talented and tireless researcher, as well as a forthright and honest guy. He is originally from Ukraine, and speaks/reads Russian and Ukrainian fluently. His research has been central to several of my big scoops over the past year, including the breach at Adobe that exposed tens of millions of customer records.
Q: Is this for real?
A: Alex isn’t keen on disclosing his methods, but I have seen his research and data firsthand and can say it’s definitely for real. Without spilling his secrets or methods, it is clear that he has a first-hand view on the day-to-day activities of some very active organized cybercrime networks and actors.
Q: Ok, but more than a billion credentials? That seems like a lot.
A: For those unfamiliar with the operations of large-scale organized crime syndicates, yes, it does. Unfortunately, there are more than a few successful cybercrooks who are quite good at what they do, and do it full-time. These actors — mostly spammers and malware purveyors (usually both) — focus on acquiring as many email addresses and account credentials as they can. Their favorite methods of gathering this information include SQL injection (exploiting weaknesses in Web sites that can be used to force the site to cough up user data) and abusing stolen credentials to steal even more credentials from victim organizations.
One micro example of this: Last year, I wrote about a botnet that enslaved thousands of hacked computers which disguised itself as a legitimate add-on for Mozilla Firefox and forced infected PCs to scour Web sites for SQL vulnerabilities.
Q: What would a crime network even do with a billion credentials?
A: Spam, spam and….oh, spam. Junk email is primarily sent in bulk using large botnets — collections of hacked PCs. A core component of the malware that powers these crime machines is the theft of passwords that users store on their computers and the interception of credentials submitted by victims in the process of browsing the Web. It is quite common for major spammers to rely on lists of billions of email addresses for distributing their malware and whatever junk products they are getting paid to promote.
Another major method of spamming (called “Webspam”) involves the use of stolen email account credentials — such as Gmail, Yahoo and Outlook — to send spam from victim accounts, particularly to all of the addresses in the contacts list of the compromised accounts.
Spam is such a core and fundamental component of any large-scale cybercrime operation that I spent the last four years writing an entire book about it, describing how these networks are created, the crooks that run them, and the cybercrime kingpins who make it worth their while. More information about this book and ways to pre-order it before its release in November is available here.
Q: Should I be concerned about this?
A: That depends. If you are the type of person who re-uses passwords at multiple sites — including email accounts — then the answer is yes. If you re-use your email password at another site and that other site gets hacked, there is an excellent chance that cyber crooks are plundering your inbox and using it to spam your friends and family to spread malware and to perpetuate the cybercrime food chain.
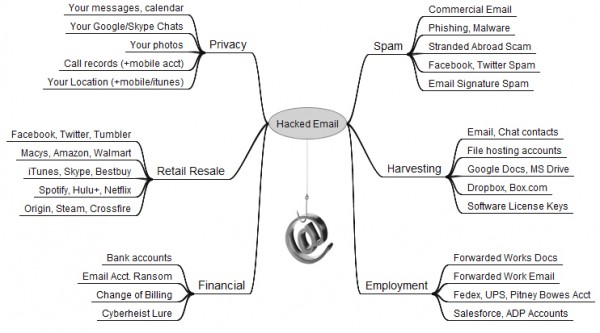
For a primer that attempts to explain the many other reasons that crooks might want to hack your inbox, your inbox’s relative market value, and what you can do to secure it, please see The Value of a Hacked Email Account and Tools for a Safer PC.
Got more questions? Sound off in the comments section and I’ll try to address them when time permits.
Update: As several readers have pointed out, I am listed as a special advisor to Hold Security on the company’s Web site. Mr. Holden asked me to advise him when he was setting up his company, and asked if he could list me on his site. However, I have and will not receive any compensation in any form for said advice (most of which, for better or worse, so far has been ignored).




This will be interesting to see how this plays out… First
I Think i was hacked Should i jump off a bridge ?
Brian, you’re listed on Hold Security’s Advisory Board. Did he consult with you before orchestrating this scare-for-pay campaign as described by the Washington Post? On the face of it, this typifies the worst practices of the security industry. Throw out news about a huge breach, provide no way for independent verification by other researchers, and charge money if you want remediation.
You have a great, well-deserved reputation, Brian but Holden’s actions reflect on you as a member of his advisory board.
+1 to you good sir
Jeff,
It is true that Mr. Holden asked me to advise him when he was setting up his business, but he hasn’t taken most of my advice. I have received and will receive no compensation for said advice.
Shouldn’t you have noted this connection in your article? Also, you are saying that Alex didn’t get help from you to get this NY Times story? If Alex is indeed this little guy in his basement working tirelessly, this seems like a pretty professional move to give Times exclusive story and then ride the media wave.
This story has all the signs of a scam and I’m surprised that you are part of this, Brian.
You’re a very respected practitioner, too, Jeff – how would you suggest he pay the people in his employ if not by charging a fee for their work product?
Yes, the timing is a bit “showy” and the message needs work, but after all the data I’ve seen Alex give away for free I can’t really question his motives now that he wants to pay some bills.
The point isn’t being paid or not for your work. The point is how he did this. The story just caused an unnecessary panic in industry, as I am sure you know Jim. There was no nuance here. He didn’t mention the fact that this kind of activity has been happening for several years and this isn’t anything new. Or that actors on the forums aggregate this data, openly soliciting dbs.
Oh and funny he sat on this data until Black Hat, just like he did last year with the 500m creds before RSA when he made his other big announcement.
This guy is a publicity hound. Plain and simple. That is what people have a problem with. I don’t get why CrowdStrike gets hammered for being media whores, but poor little Alex Holden shouldn’t.
“You have a great, well-deserved reputation, Brian but Holden’s actions reflect on you as a member of his advisory board.” – the second comma should go AFTER Brian – not after reputation.
Technically there should be both. One after “Brian” and one before “Brian”.
One point, “the cooks that run them,” …and we all understood with Brian meant just fine 🙂
Well said Jeffrey Carr. I was suspicious as soon as I saw it posted earlier today. I would doubt the majority of people are affected (ie. those who don’t use obvious and similar/the same passwords).
Actually, I believe recent research has shown that most people still indeed re-use the same password that’s used on their email account.
Do you think that Holden is capitalizing on this to drum up new business? Sure seems to be the case….
Yes and exactly yes !
all your information in article (your website and Hold Security website) in simple and speaks in general terms without any technical information (Except SQL injection !!) !
“Hold Security” with 11-50 employer (based information LD) find this big operation !?
how to study in 400 site !? seven months of research !?
kidding me!
He can fluently speak/write Russian. And he can probably pass for one. 🙂
I don’t doubt the original reported has the goods, but the timing right at the start of Black Hat might raise eyebrows, plus the heavy marketing in the article makes it sound a little “FUD-y”.
How long did he know about this before going to press?
Cooks ? kooks or do you mean crooks? Is this a typo?
I like the Chinese “kooks” who send me PDF and excel attachments daily that you can’t read or understand .
What do you think of the individual protection service Hold Security is offering? Is there any value to it?
Does using 2-factor authentication help for gmail, for example? For banks and other sites that have financial information, unique passwords make sense.
But for the 100s of forums etc, does reusing a pw really hurt all that much. And phones make using good passwords really REALLY awkward. PW managers can help, but apps have made them awkward as well: cut/paste rather than the browser plugin approach.
Of course two-factor authentication helps! Remember, that second authentication factor is a one-time code that can’t be reused (and often expires in, say, 20 minutes).
The sad thing is that with all the hacking going on today, MANY (most?) major banks offer the most feeble single-password authentication. I use several banks and none offer two-factor; in fact, one won’t even allow special characters (#!@$%&_*), just alphanumeric. If y’all don’t think that’s risky, there are several fine ostrich farms where you can stick your heads in the sand.
Hasn’t the SQL injection technique been known about for several years now? Isn’t there a simple way to adjust the code that programmers can use to protect their systems? Forgive me if this is obvious, I’m just a noob.
Hey Alan, there are many simple ways to check the input for potentially malicious SQL commands and protect their selves, but the problem is most webmasters either don’t know or can’t be bothered implementing them. It is entirely the webmasters’ (presuming they coded the site) fault, as SQL injection is easy to prevent.
That’s pretty much how I’ve seen it for years. I must admit though, that if I see something wrong with a web-site – especially their SSL certificate, I usually contact the web-master, and surprisingly, many of them reply with thanks that a vulnerability has be pointed out. So maybe many of them simply don’t know what they are doing, but have good intentions.
My own experience of researching SQL Injection in the early days led me to discover that it was entirely possible to gain access to the databases for a number of co-hosted websites via an attack on a single unsecured website. Of course, this tends to affect the smaller websites one subscribes to, but it was very sobering.
If your site is cohosted there is a potential that a security issue on ONE of the maybe scores of other websites you share a database server with can result in your data being compromised.
So even fixing the security holes in your website is not necessarily enough.
+1 for all the educational value on this site. :–)
Do we have any time frame on how recent this data was collected?
Honestly this is no different than what CSID does. They charge you to see if your credentials are listed in hacked databases. They then alert you if it was. How do you think LifeLock works? They buy their services from CSID. Just sayin.
Several thoughts:
1. The public news sources aren’t highlighting this point strongly enough: It was over a billion usernames/passwords stolen over time. Some laymen are panicking thinking this was a single breach. It’s a report of a single gang’s accumulation of databases over time and quite obviously includes some breaches that have already been publicized.
2. What’s notable is that Hold Security characterizes this as robberies of websites and FTP sites. Not harvestings from individual compromises (like password stealing malware, personal address book leaks from virus/worm/trojan compromises, and the like).
3. Hold Security noted that when you narrowed down to unique addresses, you still get over half a billion, and even then not all of them can be valid or current. He mentions fake addresses, or deprecated ones, and that makes sense: There will be MANY addresses in a compromise harvest that will be invalid. That’s an important for the news services to note to laymen. It doesn’t minimize the problem, but it does provide useful context.
4. If someone malicious was willing to datamine the addresses, I’d wonder if they’d be able to find stuff to help with future attacks. For example: Seeing nothing but 8 character-long passwords for a given domain would suggest an old mail system that might be out-of-date patchwise, and be susceptible to attack.
5. What I’m *really* curious about is how many of these credentials can be traced to a compromise/breach/leak that was already known and fixed, as opposed to ones that would be a surprise to the mail service’s administrators.
+1 for reason and logic 😉
As the late Sen. Everett Dirksen might reflect, a billion email addresses here, a billion there, and pretty soon you’re talking a lot of email addresses. 😉
I’ve found it extremely difficult to get our CISO to focus on the time tested attack vectors like SQL injection when his team is constantly off chasing butterflies of the latest exploit de jour. For our last two pen tests he didn’t even have them test for SQL injection vulnerabilities. OWASP still lists it as #1 but that hasn’t seemed to gotten anyones attention. Maybe this latest breach will.
Get a WAF for the sites. Get a FireEye NX appliance and put it behind the firewall. Patch all of your systems and don’t use default usernames and passwords. Call it a day.
> Get a FireEye NX appliance
and now you have more bugs to patch ..
Rick, your comment provides dangerous and incomplete advice that will provide a false sense of security. Also whomever is doing pentests and not touching SQL injection (assuming its a sql backed webapp pentest) is doing it wrong.
Even if you have a WAF you should test your webapp for vulns via an access point that doesn’t have WAF protection. Otherwise you are still running a dangerously insecure webapp. A WAF is akin to blacklisting known viruses, they are an easily broken method that doesn’t protect you against new stuff, or specifically crafted attacks/payloads designed to circumvent the WAF.
Your services are no longer required, Rick. Stop posting things you hear your dad and his friends talking about.
Thanks for the tip, Brian. I’m curious… would you sign up for Hold Security’s service? What’s your honest opinion of it? I’d just like an expert’s thoughts on it.
Check with CSID, they offer the same services and they have been around for a long time. I don’t work for them but have used their product and its pretty good. http://www.csid.com/
Thanks Rick! I appreciate that tip and will check it out.
I’ll 2nd CSID, great company to work with.
I find it to be quite a coincidence for this announcement to come out during Black Hat AND that it just so happens that HoldSecurity has a plan that costs AS LITTLE AS $120 a month to warn you of potential breaches… This sounds like a sales pitch.
Brian, given that you consider Holden & Co. and this news story to be credible, what would you advise a user (like myself) who has relied upon LastPass for the past few years to generate unique 12-character passwords (including numbers, upper- and lower-case characters, plus special characters when not precluded by a given website)? Go through the process of changing ALL of them, or not?
Good question I do tend to use both two factor AND unique pw/username combinations. I tend to use 27 char or more where possible with lastpass. Every important site also has a unique username
That being said do we have any idea when they might let us know what accounts to change, before too long?
Two factor auth helps a great deal with this problem. Use it if it’s available.
For more info, see: http://twofactorauth.org/
Given Alex Holden is originally from Ukraine and given the geo-political tension in the region it is plausible to presume that going public is rather a political move. Especially the coverage and the twist the press is now giving to this. Politics and business are not always good friends. It seems that responsible disclosure would be more appropriate. Further, there is new services announced (of course!) one collects scared users’ emails and names… What if Hold security falls the next victim of the cyber crime?
So, it’d be really nice for us sys admin and dba type folks to get more information on how this happened so we can do some vulnerability checking… just saying, i understand the vagueness but it’d be really nice to know if our systems are vulnerable :-/
SQL injection is not too hard to test, either internal testing or external testing can certainly help limit the size of the vector if you even have a vulnerability. Some simple validation checking is also a good place to start. Many free tools exist to testvSQL injection try the OWASP website for a place tp start.
you know the old adage.. “if you have to ask..”
I’ve already gotten spam sent to the entire contents of a friend’s address book.
This is not really a surprise. I’ve been writing about the use of compromised domains by spammers on the Cloudmark blog for more than two years now. Over the past few years we have seen it go from a handcraft to a cottage industry, and now to full scale mass production. On any given day Cloudmark will detect hundreds, and sometimes thousands of new compromised domains used by spammers. We’ve seen over a hundred thousand in the past six months, with over thirty thousand currently in use the the hackers. Median time to remediation is in months rather than days, and notifying webmasters (if they exist) or hosting companies has very little impact on this. (I know, I’ve tried.)
It would be great if the publicity around this report generates more interest in finding a more effective solution to the problem of compromised domains.
Brian, I was wondering how much money such a large set of accounts would be worth to a spammer? Is it thousands of dollars, millions of dollars? Could you enlighten us?
This is big money for someone. I know a few individuals who use/have used this method of spam that you mentioned(using hacked accounts to send spam to the contact lists of those accounts). A lot of guys now adays are pushing diet offers/work from home scams. As I mentioned, I know multiple people earning $10,xxx – $20,xxx DAILY with this method.
@narchy
really, so you hang out with criminals too? you make it sound so appealing. almost attractive in a way that i want to make a living out of it. after all i was at one time in the past the General Secretary of the Communist Party of the Soviet Union. did i mention i knew Stalin?
No, I left the spam game long ago. Back in 2001-2003 I mailed – I do however know a few people still in the business. I wouldn’t say it’s something you would ‘want to do for a living’, but make no mistake the big players are very wealthy, they drive flashy cars, they have high rise condo’s in some of the most luxurious cities, etc etc. I was just putting this out there for people who were curious.
No, spamming is not a great longterm career choice – but if you want to retire by the time you are 25, it’s a very appealing option 🙂
Good that you didn’t forget to censor out the least significant 0 figures, otherwise people would be able to see exactly how much they earn
The figures I mentioned are accurate. 10K-20K a day is not uncommon with the right method.
I thought this big news flash was a little redundant, when I 1st saw it on cable news – I just thought – this is old knowledge, spammers have been doing this for at least a decade!?
I must admit, though, that spammers are actually trying to zero in on legitimate email addresses, but the methods they use haven’t changed much in five years, so I still got to wonder why this alert is really news at all. I got to hand it to them for acting like a legitimate business does and include better efficiency in their “business model”! HA! 🙂
Brian seems to hint on this with this article, the way I interpret it..
If they got the password hashes out of the database, do we care? I assume it is easy to break some hashes but not others. Some may store plain text passwords. Do they have time to exploit them all other than sending spam email? How would they filter out the logins that are worthwhile so they can spend people resources on them?
How many actual passwords were also revealed?
Brian,
I am wondering if you think there’s any truth to this Forbes story?
http://www.forbes.com/sites/kashmirhill/2014/08/05/huge-password-breach-shady-antics/
How is this any different than all the other security researchers and companies pimping their latest discoveries right before black hat? Look at a$$hats at offensive security, who irresponsibly disclosed a Symantec vulnerability. Just more of the same.
if alex is as good as you say he is, then why not do the honorable and universally ethical thing to expose these criminals for who and exactly when they reside to allow a systematic extermination of these and all that act on their behalf once and for all?
or
is he just in it for the money like the criminals that really have no honor nor a soul?
life is way to short to allow this type of menace to continue to tear the fabric of humanity and destroy honest peoples way of life.
Here’s the thing. Whether it’s real or not the general attitude that this could never happen and that it’s BS is alarming. This is why the. ‘Bad guys’ win countless times and will continue to do so. There is such a lackadaisical attitude about breaches and hacks and it WILL come back to bite us all, if we continue to put our heads in the sand and not take threats and these criminals seriously.