If you receive an email this holiday season asking you to “confirm” an online e-commerce order or package shipment, please resist the urge to click the included link or attachment: Malware purveyors and spammers are blasting these missives by the millions each day in a bid to trick people into giving up control over their computers and identities.
Seasonal scams like these are a perennial scourge of the holidays, mainly because the methods they employ are reliably successful. Crooks understand that it’s easier to catch would-be victims off-guard during the holidays. This goes even for people who generally know better than to click on links and attachments in emails that spoof trusted brands and retailers, because this is a time of year when many people are intensely focused on making sure their online orders arrive before Dec. 25.
According to Malcovery, a company that closely tracks email-based malware attacks, these phony “order confirmation” spam campaigns began around Thanksgiving, and use both booby-trapped links and attached files in a bid to infect recipients’ Windows PCs with the malware that powers the Asprox spam botnet.
Asprox is a nasty Trojan that harvests email credentials and other passwords from infected machines, turns the host into a zombie for relaying junk email (such as the pharmaceutical spam detailed in my new book Spam Nation), and perpetuates additional Asprox malware attacks. Asprox also deploys a scanning module that forces hacked PCs to scan websites for vulnerabilities that can be used to hack the sites and foist malware on visitors to that site. For an exhaustive and fairly recent analysis of Asprox, see this writeup (PDF) from Trend Micro.
Malcovery notes that the Asprox spam emails use a variety of subject lines, including “Acknowledgment of Order,” “Order Confirmation,” “Order Status,” “Thank you for buying from [insert merchant name here]”, and a “Thank you for your order.”
If you receive an email from a recognized brand that references an issue with an online or in-store order and you think it might be legitimate, do not click the embedded links or attachment. Instead, open up a Web browser and visit the merchant site in question. Generally speaking, legitimate communications about order issues will reference an order number and/or some other data points specific to the transaction — information that can be used to look up the order status at the merchant’s Web site. I know I’m probably preaching to the choir for the loyal readers of this site, but I’m sure most of you have friends and relatives who could use a reminder about all of this. Please feel free to forward them a link to this story.



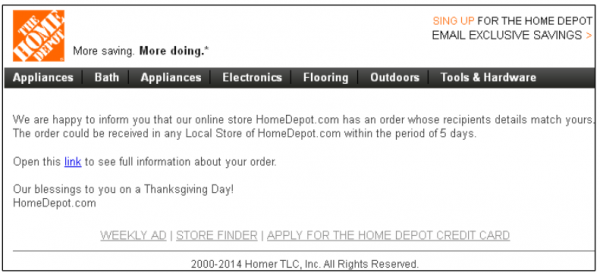
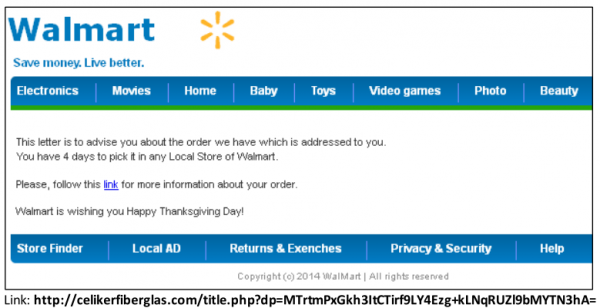
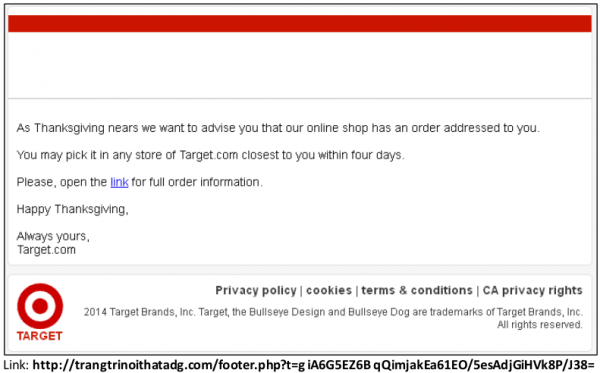
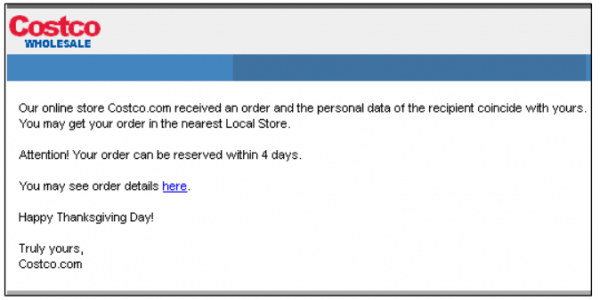

I’ve been getting these things all year, but they have increased the past week or two. They are usually sent to “sales@” or “support@” instead of one of the addresses I actually use.
Thanks for the heads-up, Brian.
Readers who are passing this advice on to their Windows-equipped friends could also recommend a checkup with the Secunia PSI utility. It can auto-patch some software for the user, and alert them to stuff they have to patch manually. This is relevant to the topic at hand, since eliminating those vulnerabilities will help deprive the attacker of traction if someone does click a malicious link in an email and lands on an exploit kit.
Caveat: Secunia PSI is licensed for personal use only.
This is useful information that the general public needs to know.
Brian, how about contacting news stations with this post?
I stopped using Secunia when it started peppering me with too many warning messages. The free version of Avast Free Antivirus can be used to find out which programs need to be patched.
I assume you meant to answer mechBgon; but I still see Secunia PSI as invaluable because it actually pops up on the limited account to tell you something needs a manual update. I agree that the software updater on Avast is great, but it has a limited scope.
These PSI popups are a great reminder to get off the limited account and go administrative to tend to the patch requirements. I never attempt to use PSI for the update, I just note which app it is pointing to and update that with the application itself or File Hippo’s Application Manager(name changed from Update Checker).
Using several sources like this is just like a blended defense scheme, in that sometimes Firefox reports is it up to date, when it is not, actually. I check all three sources to make decisions on whether the version number is correct, and a update is actually needed. Then I simply scan again with Secunia PSI to clear the alert. It really makes life easier to maintain one’s computing environment, and I don’t feel the need to constantly check for updates every day. I am confident one can keep ahead of the zero day threats by being proactive on the vulnerabilities this way. Most standard malware is very ineffective to a user on a limited account that is locked down this way, and any other malicious files can be dispatched with CCleaner, or blocked by Rapport. Having a good HIPS rounds this out very well too.
Here is another one from CVS that has been circulating lately: https://i.imgur.com/4kqkYIu.png
I notice that Home Depot requires one to “sing” up for the exclusive email savings. They don’t really say what one is supposed to sing. You would think Asprox would at least tell you what to sing to get your savings.
I wonder what the “successfully duped” rate is for those millions of messages sent? One out of a thousand?
So many people shopping online at major retailers these days, it’s easy to see how successful this ploy could be.
Thanks for the heads-up, Brian, I will indeed pass this excellent advice along to my online shopping friends…
You can add Amazon.com to this list. Got one this week saying a name that’s unknown to me purchased a 40″ TV and it’s being shipped to my address. The email looked virtually perfect, except that the order number link went to a URL outside the US.
Pity, I would have liked a new 40″ TV!
I’ve been receiving those from Purolator (Canadian courier) for months now. Still waiting for my 4 HD TVs, 3 books and others… 😛
I have seen my fair share of Phishing emails from crooks posing as Coscto, UPS, FEDEX and others. Nothing new.
Most of these have some sort of picture associated with the email. I am sure thats a way they can tell who is a live phish, errrrr fish and which ones aren’t biting.
For my email client, I NEVER use the auto preview pane – all are disabled. I also keep my spam filters set to medium.
Its easier to call the source about the potential package than have to hand over your PII to the crooks on the other end. =\
And what are the holidays if not the season to “sing up”?
This type of emails hit my inbox but i am overseas. I really dont know how they get my email address….
Same here, there is a certain email provider that I have an account with..and I use that email address for a specific purpose, I hand out this address directly to someone, and yet still have spam.. I literally have not signed up for anything with that address
if you used that email address at any of the major businesses out there, they could have shared that information with another business. Some of these businesses use – or used to use – a common logon allowing people to surf from one business to another without having to long on to each one separately.
Remember, these are the breaches we know of. I also know there is a way to query a windows box and yank some PII out of it, to include the email asdress.
And like others have stated above, another person you have shared that email with, sending correspondence with back and forth could easily fall victim and become compromised. In the past I have seen “chain mails” send out to thousands upon thousands of people and in the end, I did not see one person on that list that I knew. Those in general are ways for the crooks to get many active email addresses with hardly any effort.
There are TONs of ways that a personally held close email address can be leaked out. All it takes is one email, and all bets are off that it will remain “private”.
If the machine of any of your contacts is infected with an address harvester your address is out there for sale.
An especially poor practice by many people is to send, or forward, an email with all the addresses in To: or Cc:, instead of Bcc:
Now it does not even have to be the machine of one of your contacts which is infected.
BTW, this practice is also one that disregards your privacy.
Companies and organizations sell and trade people’s email addresses. And crooks will generate lists of possible email addresses, and see which ones don’t get bounced back to them.
Bad spelling in most of these. As was pointed out before, “sing up,” but also “Returns and Exenches” in the Walmart one.
I liked: “Our blessings to you on _a_ Thanksgiving Day!”
I got an email from supposedly Citibank credit card which looked odd in appearance. It mimicked the style of the bank, but seemed odd in a way. As my practice I just deleted it and used it as a reminder to run my alternate anti-virus software. Wonder if email was also a special gift for the holiday season? I’ll never know.
But still people continue to fall for this crap year after year. You can’t get this type of information out to enough internet users to read or they just don’t care enough about internet security.
Gmail seems to block this stuff from the main inbox. Have not seen one of these in a couple of years.
My ISP also seems to filter them all out.
Although the question comes to mind – in the book Brian suggests that one of the things that really reduced the cheap pharma spam was that Mastercard and Visa had effectively cut off the spammers ability to collect payment. If they are still sending this junk out (with the idea of pushing cheap pharma), there must still be some means by which they can get paid.
Then again, a botnet is a botnet – they can use it to phish for credentials instead..
Does this work on all OS….unless I missed it, did not see if windows only specific or also if browser is set up for anonymous browsing….saw you on tv the other day…glad to see the media is attending better to cybercrime!!!
These guys are gradually getting better at imitating the real thing. I’ve seen a lot of lazy spam but until lately, few “order confirmations” mimicking real businesses. An awful lot of this would be averted by following Brian’s advice: do not click the embedded links or attachment. Instead, open up a Web browser and visit the merchant site in question.
Brian, earlier this year I analyzed a bot agent delivered by (not nearly as convincing) order confirmation spam. The bot was instructed to brute-force 5,000 domains in search of open SMTP servers that could presumably be used to deliver yet more spam. Is that a common approach, or do you find bot clients that are themselves mail servers?
The email I saw, along with the behavior of the malware payload, is described at http://dnlongen.blogspot.com/2014/10/from-click-to-pwned.html
now you want me to click on an embedded link, warning about embedded links in emails….let me think for a minute…is this checked before it is posted or a very slick way to get me to click on this embedded link talking about embedded links in emails…
h e l p
touche 🙂
I received the first ever email of this type 2 days after joining a local Costco on Black Friday. It was exactly the Costco email pictured above. I almost clicked. It was the same email address I gave Costco when I joined. Coincidence? Maybe not. Glad I paid cash that day. I’ll be awaiting the Krebs expose on a future Costco breach…
Thanks for the heads up on these as our (real) online holiday order confirmation emails roll in.
Just received the same thing from supposedly “COSTCO.” Deleted without opening. I have been a COSTCO member for a long time, so a bit of a difference there …
Those automatically go to my junk box with all images and active content disabled. I never see them anymore.
An executive, who definitely should have known better, at my company fell for this last week. It was a fake UPS delivery notification that made it through our spam filter. The email spoofed UPS logos, etc., but had poor grammar and punctuation, and yet this VP fell for it. Supposedly the virus was caught. This happened at the end of my month long Phishing Awareness campaign. Some days I feel like I’m damned if I do, damned if I don’t.
Brian, Thanks for your efforts in raising the awareness on these. Add to the types that I am seeing more and more of lately — shipping notices (supposedly UPS, Amazon and Canada Post) as well as lots recently from supposedly Canada Revenue Agency saying I’ve got a refund just click here. (How can you tell I live in Canada?)
I received one of these emails from Best Buy and opened it. I called best Buy to inform them. The clerk there told me she had several elderly people coming in today asking about it. She had no idea and there seemed to me no management in the store that had any knowledge of what this was about. it would be helpful to have news blasts of this to inform and protect people. Now that I’ve opened it on my computer what should I do? I’m not all that computer literate but I do use it for personal use. Do I need to install a new security software or just shut it down for awhile?
Try forwarding the email to abuse@bestbuy.com.
Thanks. Will do.
Karin,
If you just opened the email, I wouldn’t worry about it. But if you clicked the link or opened the attachment, you could have bigger problems.
Brian, unfortunately I opened the attachment.
– Go to http://www.malwarebytes.org/.
– Single-click on “Free Version Download.”
– Look at the bottom right of your screen for a small popup asking if you want to Run, Save, or Cancel; select Save.
– When it is finished, select Open Folder (the words might be slightly different, I’m doing this from memory).
– Double-click on the item you just downloaded (it will be “mbam” something or other). Check the time and date to verify that it is the most recent file.
– Follow the instructions, but do not accept the free trial.
– After it is installed, click on Scan at the top (don’t click on Scan Now at the bottom).
– Click on the circle to the left of Custom Scan.
– Click on Scan Now. Depending upon your PC, it could take more than an hour.
– Follow the instructions and accept defaults if malware is found.
You can continue to use your PC while the scan is running, but your PC will be slower than usual.
P.S. Malwarebytes is the very best malware remover, but it does not protect your PC so you still need an anti-virus.
I second the idea of downloading Malwarebytes Anti-Malware.
I third the motion on MBAM – however don’t forget that the Pro or Premium version does block a lot of malware and can prevent infections in the 1st place; so it does have real time malware protection built in those versions.
Also the paid versions have auto scanning and scheduling to find things that slipped past the older definition updates; and the scans are not nearly as intrusive to daily operation as in the distant past. I like the fact that it totally ignores malicious cookies, as those can be easily removed with occasional CCleaner wipes, or blocked passively by Spybot Search and Destroy.
All true. However, in this economy I never assume that people can afford the Pro version, inexpensive as it is. Besides, someone can use the free version for a while and then convert to Pro after paying the fee.
And to continue on my free kick, if someone cannot afford anti-virus, at least install Microsoft’s free MSE and have some protection. It’s not as good as Bitdefender, F-Secure, Norton, and some other ones, but it sure beats nothing or an expired subscription.
I usually have my indigent clients coordinate with friends to buy the Premium license, as it issues three licenses for the same fee as the old Pro version. That way they pay very little for it.
I’m all for free – if they just can’t afford anti-malware at all – I like to put SpywareBlaster, Spybot Search and Destroy, and the older Windows Defender on board. They can also use Super-Anti-Spyware as a quickee scanner. Passive real time protection can at least be one small rivet in the armor.
Oops, I forgot a step. Insert the following after “Click on the circle to the left of Custom Scan”:
– Select all SSDs and hard drives (for most people, just selecting C: will be sufficient).
Yes, started seeing these more a few weeks ago. So far all of them are directed into junk mail automatically. But I am sure plenty of people will far for it as so many consumers buy online and are waiting for packages. Of course generally most online retailers communicate directly through email with consumers on orders. So the package people don’t normally contact you this way. I think only once did UPS contact me about a delivery. That was because the label was damaged and could not read address completely. The shipper had provided a phone number for this issue. Links have been so bad for so long. You really should never click a link from any mail. I definitely feel for older people who may be less sharp on detecting this. Older lady in bank today paid something that was fraudulent and was trying to do something about it to stop payment. No security suite can totally stop you from doing something wrong and foolish. Yourself being informed is the best defense.
I have to say that the two web based email systems I use are pretty good in catching spam and malware such as described above.
I have not had any in my inbox.
I was curious, so I looked in the spam folders.
Here are the most obvious ones in the last three weeks:
Best Buy acknowledgement of order
Google User support urgent notification
Walmart thank you for your order
Notice to appear in court
Barclays Bank attention beneficiary
I need your assistance to validate your name in our Bank System to enable the Bank transfer
I have picked your email address for an inheritance of $250000
oops, now I am getting all these comments, Brian, turn this off please….
Did you subscribe to comments on this thread? I don’t have a way to turn that off. I can, however, remove you from my mailing list, but that won’t unsubscribe you from a post.
The comment emails do have a link at the end to manage your subscription, from which you can unsubscribe from the comments.
Brian, how did you add the feature to notify users of followup comments via e-mail? Was it via a WordPress plugin? As far as I know, a default WordPress installation doesn’t have this feature.
OK Unfortunately I was one of the ones who clicked the link. I got a Costco email today. I have ordered numerous items over the past few weeks and clicked it. Now it had my computer to where I cant access anything! it tells me to install a virus protection and “recommends” a certain one. I exited out fast and didn’t install it. I have virus protection but it wont let me even access that! HELP! Is there anything I can do besides having an I.T. guy fix it??
You may try a System Restore.
i tried to do that. It won’t let me access anything at all. Every time I click on anythig it pops up to install that virus protection it recommends and I’m not doing that cause I fear that will just totally wipe out my computer.
Unfortunately, at this point, you will probably have to take it to an IT guy.
I tried something I read online. I used another computer and put Microsoft Security Essentials and SuperAntiSpyware on a flash drive and then used it on the infected computer. I was then able to scan for viruses and clean it up. I am now able to log in to things again and its not locked up. During the scan, it found a severe virus and removed it. So far so good! Just pray that it truly did work.
That’s good news, I may give that a try next time I have a problem. But also, to be on the safe side, make sure you update your current protection and also download an anti malware software (I like malwarebytes) and run them both in safe mode.
It is also a good idea to keep a copy of Kaspersky Rescue Disk 10 on hand fro such emergencies – be advised it isn’t capable of connecting to the internet wirelessly though – so you will have to plug in with Ethernet in those cases.
http://support.kaspersky.com/viruses/rescuedisk
It also behooves the recipient to look—scrutinize—the received “order confirmation” carefully. The swines are v-e-r-y good at copying the logos of our major retail outlets.
If you look closely, the COSTCO email really does not look like the legit COSTCO logo. The Home Depot logo could confuse even the most scrupulous purchaser.
Try calling the retailer, if you cannot remember or cannot confirm the “order” of a [potential] family member; did they indeed, place the order? A-L-L of the “order confirmations” I receive have ORDER NUMBERS, reference numbers and in particular, my name and address attached to the email.
I recently bought two batteries for my Canon camera from an Internet provider. After thinking something fishy [the price] I went to the Canon website and discovered the error. The battery looked like—and was advertised as—a genuine CANON battery.
The thieves had even gone as far as to forge the hologram…but they screwed up the colors. I did receive a refund, but it was a very good lesson learned!
Needless to say, if you call the retailer, don’t use any phone number in the email. Look it up elsewhere!
This is very timely advice, given that the holiday shopping season just started. However, there are more subtle ways to induce users into clicking links and opening attachments that simply telling them to click, and order confirmation scams can happen at any time; not just during the holidays. See my blog post (which references this one) for more details: http://realmofvincent.com/2014/12/03/protecting-yourself-against-fake-order-confirmation-e-mails/
I wonder if the death penalty was in place and strictly enforced for activities such as these, would that reduce the number of morons involved in perpetrating these activities?
One can only hope of course.
at 1:09 to 1:12 on this video you get an answer that many may want the death penalty
https://www.youtube.com/watch?v=SKDwWmBB71U&index=3&list=WL
Brian,
I’ve got elderly folks who need access to web-based email, but they’re such suckers! They’re sophisticated enough to handle Office-style programs, navigate around Windows 8+, but they’re also gullible enough to click anything they think is “from a friend” or “some place I shop.”
Short of hiding the power cord, how would you handle it? Have you reviewed any software, browsers, or browser add-ons that you’d recommend for use with someone who’s judgement has faded with age?
Oops. I meant “whose.”
I setup my clients who are security challenged with Microsoft’s Live Outlook web-based email, and then set the filters to “exclusive”. Then it is a simple task to tell them never to check the junk folder. If they can’t receive email from someone I simply remote in and configure the filter for that contact only, or any newsletters they get. I never tell them to check the junk folder to see who is being blocked, because that will lead to things just like this article is pointing to. I always give novices a primer on being aware some sources may not be able to contact them, so the address of the trusted contact is added to the allowed list to give them functionality.
Fortunately if they do look at that folder – all active content is blocked, so as long as they don’t click on anything, nothing bad can happen – even if they do, Outlook will pop up a warning about doing such actions.
Thanks for the suggestions, Heron, jcitizen, and mechbgon.
I don’t want to turn off all active links, because they enjoy receiving cat and comedy videos and sharing photo collections, like everyone else online. I want to restrict them to a whitelist of sorts.
I think the application whitelisting and family safety settings might do the trick.
I was just hoping there was some safety enabled browser or browser extension that did the hard part for me.
Whitelists are not too bad – they remember the processes and execution files you allow. They don’t block very often, because so many applications use the same processes. The MS one, scans for all presently on board, so those will be on the list from the start.
You will see all ordinary entertainment processes on browsers and email with very little problems. I use it in my honey pot lab, and it rarely goes off. This isn’t like using No Script or Script safe.
Thanks. I guess I’ve got to try it.
Gmail would be less likely to put fraudulent messages in people’s inboxes. You could also teach people how to filter legit commercial email into folders/categories, so they’ll know which messages are safe to open.
When I taught Internet classes, I showed people examples of fraudulent email messages, and gave them some guidelines for online safety. But there’s only so much you can do.
Look into application whitelisting. The simple version is Family Safety, while the full-strength version is Software Restriction Policy (or AppLocker, but it’s not supported on nearly as many variants of Windows). I have a writeup at mechbgon.com/srp on the subject.
What this can do, is to block the execution of an exploit’s payload. It’s not without its complications, of course. But have a look at it. Simply keeping stuff up-to-date (with Secunia PSI or whatever) will help prevent exploitation of known vulnerabilities, and Microsoft EMET will help prevent exploitation of both known and unknown vulnerabilities.
Also max out UAC to the “Always Notify” setting, particularly if your people are going around with Admin-level accounts.
Good one mechBgon – I always forget about white-listing. I’ve used the application control on Vista x64 Parental Controls, and it works very well. It isn’t too hard to allow any new processes that are okay, as well. I have a hard time promoting the other Parental Controls unless the client has a very powerful CPU and RAM, because they slow the machine down to an unacceptable level; but the “allow/block specific programs” is golden as far as I’m concerned.
Thanks. http://krebsonsecurity.com/2014/12/be-wary-of-order-confirmation-emails/comment-page-1/#comment-338452
On iOS, everybody should go to:
settings>mail>Load Remote Images and switch this OFF.
For legitimate emails that you receive with images you want to see, scroll to the bottom of that mail message and click “Load Images”.
Doing this will prevent your device from confirming you opened the mail by loading a pic, or getting a ping back from a single pixel image.
It is possible to enable a similar setting in OSX as well.
Sorry I can’t tell you about any other brands but Apple but I expect that they have similar features to suppress remote image loading as well.
In ios, if you want to check a hyperlink (like you would by hovering the cursor over the link on a computer) without activating it, put and HOLD your finger in the link until a box opens up. At the top will be the link in its entirety. You can then cancel the box after looking at the link.
Just about every company has an address for reporting pishing that is easily found through a web search (usually it turns out to be something like spoof@domaincom.). If you do forward the mail to the company, put the ftc in copy too.