A gaggle of young misfits that has long tried to silence this Web site now is taking credit for preventing millions of users from playing Sony Playstation and Microsoft Xbox Live games this holiday season.
The group, which calls itself LizardSquad, started attacking the gaming networks on or around Christmas Day. Various statements posted by self-described LizardSquad members on their open online chat forum — chat.lizardpatrol.com — suggest that these misguided individuals launched the attack for no other reason than because they thought it would be amusing to annoy and disappoint people who received new Xbox and Playstation consoles as holiday gifts.
Such assaults, known as distributed denial-of-service (DDoS) attacks — harness the Internet connectivity of many hacked or misconfigured systems so that those systems are forced to simultaneously flood a target network with junk internet traffic. The goal, of course, is to prevent legitimate visitors from being able to load the site or or use the service under attack.
It’s unfortunate that some companies which specialize in DDoS protection services have chosen to promote their products by categorizing these latest attacks as “herculean” and “sophisticated;” these adjectives describe neither the attackers nor their attacks. The sad truth is that these attacks take advantage of compromised and misconfigured systems online, and there are tens of millions of these systems that can be freely leveraged to launch such attacks. What’s more, the tools and instructions for launching such assaults are widely available.
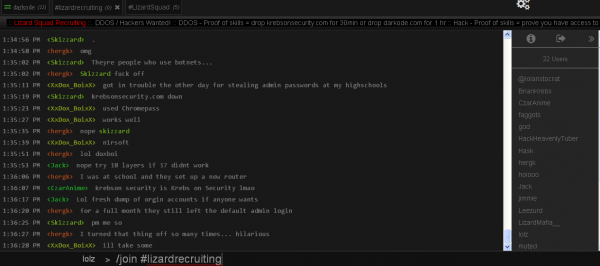
The LizardSquad leadership is closely tied to a cybercrime forum called Darkode[dot]com, a network of ne’er-do-wells that I have written about extensively. So much so, in fact, that the LizardSquad has made attacking KrebsOnSecurity.com and keeping it offline for at least 30 minutes a prerequisite “proof of skills” for any new members who wish to join their ranks (see the screen shot below).
Over the past month, KrebsOnSecurity.com has been the target of multiple such attacks each day. Prolexic — a DDoS protection firm now owned by Akamai — has been extremely helpful in poring over huge troves of data about systems seen attacking this site.
The majority of compromised systems being used to attack my site this month are located within three countries — Taiwan, India, and Vietnam. The bulk of attacks have been so-called “Layer 7” assaults — in that they try to mimic legitimate Web browsing activity in a bid to avoid detection.
But what’s most interesting about these compromised and/or misconfigured systems is how many of them are located at legitimate companies that have been compromised by miscreants. According to Akamai, most of the malicious sources were Windows-based servers powered by Microsoft’s IIS Web server technology. The top five industries where those compromised systems reside are in entertainment, banking, hosting providers, software-as-a-service providers, and consulting services.
Many of those associated with LizardSquad are wannabe hackers with zero skill and a desire to be connected to something interesting and fun. Unfortunately, many of the LizardSquad individuals involved in these attacks also are embroiled in far more serious online crimes — including identity theft, malware distribution, spam and credit card fraud. While most of the group’s acolytes are known to U.S. enforcement investigators, many are minors, and the sad truth is that federal prosecutors don’t really know what to do with underage felons except to turn them into informants. Meanwhile, the cycle of abuse continues.
Update, Dec. 30, 7:05 p.m. ET: A previous version of this story named multiple companies suspected of hosting compromised systems that may have been abused by LizardSquad members in attacks on this blog. Several of those organizations have reported being unable to find any evidence that their systems were used in an attack, and took strong exception to be included in this story. Since it is entirely possible that the traffic from these systems recorded in this site’s logs could have been mistaken for attack traffic during an active (and still ongoing) attack, I have omitted the names of those companies from this post. I would like to apologize for any confusion or misunderstanding this post may have caused.




The BBC interview was glorious. They walked straight into the dragon’s jaws and Stephen Nolan just slaughtered them.
It’s also funny how, although they claim this was “impromptu” (or would, if they could use big words) the same thing happens every. damn. Christmas. Coincidence?
Where can this interview be watched?
search for it on youtube…it is there and very good.
Experian. Lol. I think those are on purpose as you are the only one in the media that calls them out for being the frauds they are.
I might also add that Lizard Squad allegedly has at least two factions. One faction – or at least Twitter account – denies it conducted the Christmas attacks while the other applauds it.
Now given that Lizard Squad – or some faction of it – allegedly posted a bomb threat to Twitter that forced the landing of a plane with a Sony executive on it, and considering that some faction of Lizard Squad has been dumping on Sony’s Playstation for months now, is it too much to suggest that one of the alternative theories for the Sony hack is some faction of Lizard Squad?
I posted this theory on Twitter – and one of the Lizard Squad Twitter accounts retweeted my tweet.
I think this is at LEAST as plausible a theory on the Sony hack as the North Korea theory.
Note that I’m not pointing fingers at Lizard Squad or accusing them of the Sony hack.
I’m saying that until the full forensic analysis has been done of the Sony hack, given other plausible actors against Sony, it is premature to jump on North Korea based on the circumstantial evidence provided so far by the FBI, especially given previous attributions by the FBI and others that have proven to be incorrect after subsequent forensic investigation.
On dailydot.com they claim this attack is using cabling and routers for 1.2Tbps. These ISPs are morons for not noticing this traffic on their network
Sony seems to be using Prolexic but no way can it stop even 500Gbps for non-static service
actually a simple machine linked to your network not even your isp can see whats going on
Most ISP’s won’t notice this sort of thing from the attacking hosts since a proper DDOS uses many low-bandwidth attacks that focus on one target. The target sees the full traffic rate from the attack, though.
Supposedly Kim Dot Com game them some voucher to Mega to get them to stop the attack.
it’s true. see here:
http://torrentfreak.com/kim-dotcom-stops-xbox-and-playstation-attacks-141226/
I cannot condone what the lizard squad did/does. I don’t agree with them at all.
I will say that It is completely obvious that Sony cant secure their stuff. I have no love for Sony and have no problem saying it. But, alot of people seem to be very misguided into trusting them. Too many people seem to just not care…..but they will surely complain when things don’t work.
Here’s a little advise:
Don’t give Sony (or Microsoft) so much power over your lives (over the happiness of your families on Christmas morning) that craziness like this can spoil what would otherwise be a very loving and joyful occasion. These companies don’t deserve such power and WILL hurt you with it.
Be a gamer….be what ever makes you happy in this life. Just do this with an understanding of what this technology really is (and what it isn’t). Regardless of how much you paid for it….YOU ARE NOT IN CONTROL. There is no level of privacy with these things.
This event is just another ‘one’ in a very long line of let -downs from Sony. They are not worth it.
I like mojang better than Microsoft an sony.
Mojang belongs to Microsoft you tit.
Oh, piss off with your stupid armchair-philosophy tripe.
It’s easy to tell adults, “you should enjoy the intrinsic qualities of life and share that withe ones you love through meaningful interactions,” and quite another to use that with a little kid that just wants to play their with their toys. How can you not understand that? Are you brain-dead?
What these idiots did is ruin the toys of millions of kids. It’s like going around and stealing packages off of people’s doorsteps and claiming it’s to bring attention to the lack of security for people stealing packages off of doorsteps. And now your dumb ass is talking some kind of stupid about how you shouldn’t let the joy of receiving your package rule your life and that receiving packages neutralizes or diminishes your personal security. It’s stupid and you’re a moron for buying into this childish idiocy.
What Lizard Squad did is mess up people’s holidays because they’re antisocial jerks that get off on the frustrations and pain of others. They are nothing more than psychopaths with a minimal knowledge of system networking.
It seems that Anonymous agrees with you on this.
Have your frustrations if ya like like….I’m moving on.
I see no difference between Lizard Squad and Anonymous
They’re all the same.
A lot of parents were up late Christmas Eve assembling and wrapping gifts, and they didn’t need to be dealing with this kind of problem when they would rather be enjoying the holiday with their children. “Coward” doesn’t begin to describe the type of person who derives enjoyment from making hundreds of thousands of parents and children unhappy simultaneously.
….with no consideration at all given to the idea that those same parents mistakingly thought that making Sony responsible for their children’s happiness was a good idea. Hasn’t there been enough proof already?
You can blame it on hackers of ya like (admitedly some are just immature brats with nothing better to do). But Sony set this whole thing up. It is engineered to work this way. They can’t (or won’t) do anything to fix this.
Parents really need to take a good hard look at just what it is that they are shoving in their childrens face.
why are you blaming Sony? lmao….
I agree, it’s despicable! But nothing new.
“That’s life,
& as funny as it seems,
some people get their kicks,
by stomping on a dream.
But I’m not gonna let it, let it,
get me down,
’cause this fine old world
just keeps spinnin’ around….”
That’s Life ~Frank Sinatra
As a consultant, I love the fact that consumers can now purchase large amounts of upstream bandwidth. What I cannot understand is why said bandwidth is available by default. I mean seriously, you average home user has no need for anything more than 3-5Mbps upstream. The fact that my 70 year old mother’s current $100/mo service is 100Mbps/100Mbps is simply inviting this crap. The only non-corporate users who are leveraging the full upstream capacity of these small business and home connections are bad actors who are sharing things they shouldn’t be sharing and attacking things they shouldn’t be attacking. Leave the potential to have the upstream bandwidth in the service contacts, but keep it throttled by default. Make a policy where a verified phone call by the consumer will bump upstream bandwidth from say 3Mbps base to say 6Mbps. Remind them that their service include upstream up to XXX, but additional verification is required. Make the verification process similar to PayPal and high trust SSL. Address verification, credit card verification, email verification, phone verification, and bank account verification. If you can provide that, and it all matches the account in file, THEN you can have your 100Mbps upstream.
Remember, DDoS is caused by packets sent, not packets requested. If my 70 year old mother’s laptop (along with millions of other naive users), which is always a mess with viruses, can send 100Mbps of garbage traffic, thus crap will never end.
hahaha i would say something right now but i’m not allowed.
Brian,
It’s sad that some of these kids are into more serious online crimes.
But have also seen some who DDoS for money. (If I’m not mistaken, the Spamhaus DDoS was done for hire).
Plus we know that several groups have been launching escalating DDoS attacks on banks, etc., for the past two years. A bank I know of got hit by DDoS once a week like clockwork — for months! Let’s face it: script-kiddies doing things for “lulz” just don’t have this kind of attention span.
The word is there’s a ‘nation-state’ element to some of these attacks.
So I think it’s a mistake to simply dismiss groups like LizardSquad as just a bunch of talentless kids. Yes, MOST of them are undoubtedly just script kiddies. But there are always the few who know what they are doing, and the few graduate on to more sinister things.
And there are always outside groups who are willing to fund & recruit these kids for their own purposes.
Look at the DarkSeoul. It wasn’t just one attack by one group. While DarkSeoul was happening, there were a few other groups simultaneously launching DDoS attacks, perhaps to provide cover (diversion) for the real attack.
The loosely organized “freelance groups” and the highly organized “military groups” collaborating together, for a brief moment. Such is the nature of cyber warfare today. We have a continuum of actors from script kiddies to nation-states in a highly dynamic environment.
Ya I think BK has had mentioned a couple in the past, all run by like 15 year olds, that the FBI lets slide for some mysterious reason.
Ah peace to you all little crickets
Remember me old Wang guru
Who said…..only 0 and 1
Arrayed in many bits and bytes
May the farce be with us
How important is all this 30 years from today?
It could be much worse 30 years from now if it’s ignored in the present.
Problems have a way of growing into bigger, more difficult to manage problems if they aren’t dealt with when they are recognized.
Maybe they should kill hackers instead of police!
I agree with Mark and Tim! There is definitely a surplus of upstream bandwidth being provided by ISP’s for unneeded individuals. I don’t think they should limit upload speed/throughput, but I do think more IT consultants/MSP’s should take the extra time and configure firewalls/routers with features that watch and regulate broadcast storms alerts for irregular upload and download activities based on report for that business average activity. I know that personal networks won’t have features like that but the majority of these attacks are from businesses and can be avoided by monitoring packet quantity and size.
As Mark said, taking groups like this lightly is a bad mood. In fact it is ignorant to do so. If you believe that this is just some prank, that’s fine, but the same prankster could use your network to perform countless crimes which could result in having funds from your business stolen and being in difficult situation until the bank cn resolve your dispute, or even worse, lead investigators to your place to ascertain whether or not you or your employees were involved in the crime. This could bring your business crashing down even after conclusion is reached proving your innocence. No, if you ask me, any unauthorized access or transmission of data within your network should be prevented using smart monitoring and alerting in firewalls available for as little as 300$. Then assuming that your firewall does find something out of ordinary and you who is the IP, and verify it is unwanted – you can simply filter it by its MAC address. Ddos is so easy to cause, that everyone should resolve to prevent their network from being victimized or used.
I agree completely that upstream bandwidth should not be limited permanently. I was thinking more of an additional measure to put in place just to make sure that people actually need it. I bet that 90% of accounts would never call to have the throttle lifted because they have no need for it. That would instantly eliminate 90% of surplus upstream bandwidth these guys are leveraging on compromised systems / networks.
I realize that your MAC address ACL comment was meant to address best practice network security in general, but it made me realize that there is am actually very simple solution to all of this for Sony and Microsoft. I was sitting here messing with my PS4’s connection settings. I tried various NAT configs to see if it changed the error messages. Then I threw it in the DMZ and noted the error messages there. Then I gave it a public WAN IP to see if it made further into the authentication process. It did. It actually authenticated. I put it back into DMZ and then NAT and back to failure.
That’s when in dawned on me that the solution is so simple it is ridiculous. Sony has the MAC Address for the on-board NIC and the on-board Wi-Fi NIC. In order for all of the Peer-to-Peer and network enabled features to work, you have to forward a number of ports to your device, so for most users, the device’s MAC address is already exposed. Why not maintain a MAC ACL for all of their manufactured devices that protects access to core services. Users connecting to their account on the website or mobile phone will have to connect via reverse proxy and Sony could implement MAC Address tracking via cookies, etc just like your bank. First time you hit the authentication proxy it says we do not recognize this device. Now we are going to text or email you a code to make sure this device is you. Then that device’s MAC is added to your Bank’s ACL.
Allows users to still connect with Web browsers and phones, allows users behind a strict firewall to still be able to register their connection, and gives users with the open ports instant access to the core services because that device’s MACs were added to the ACL at the time of manufacture.
Can the DDoS’ers MAC spoof? Absolutely, but it wouldn’t be hard for Sony to impending some basic geographic testing of IP origination. If my device is connecting from Chicago and now its MAC turns up in Shanghai, then there is probably something wrong and they may want to shoot me an email to verify that I decided to pack my Playstation on my trip to China lol! Similar to credit card theft detection. Unusual purchases or purchases in unusual places get flagged.
Ok, I’m done now. Sony, you don’t have to thank me for the solution. Just make it happen!
Right on target Tim, brilliant solution!
MAC addresses are not exposed beyond the nearest router. They are only applicable/visible within the context of a single L2 segment.
Yeah I immediately tune out anyone talking about how simple problems like this are to solve. Companies like Sony and Microsoft certainly have issues but they’re not idiots.
The whole bandwidth / MAC thing doesn’t make any sense. That’s not how the Internet works. Neither solution would solve anything.
MAC addresses are never exposed beyond the next hop, as you said, and rate limiting has no effect on this type of attack.
The problem with mitigating a DDOS is isolating the malicious traffic without impacting the legitimate stuff. Implementing rate limiting during an amplification attack, for example, would do more harm than good. For a layer 7 attack, like it sounds like this was, rate limiting would have effect.
A lot of these attacks are reflection-based to increase the overall payload of the attack. If ISPs would simply stop accepting packets for transit that contain a source address could not have possibly come from that port, we would be much better off as spoofing becomes instantly harder. A packet coming from Comcast with a source address of a Korean network should be dropped at the border.
I believe you’re talking about reverse path forwarding (RPF). If so, it’s not quite that simple. There are quite a few reasons why ISPs and large corporations would allow RPF. For example, networks that large have multiple ingress and egress points all over the globe. Packets that ingress a certain node often will not egress on the same node. RPF can (and often does) break stuff. It has its purposes like any other tool, but it’s not something that makes all your problems go away. Quite the opposite, in fact.
I mean no disrespect, but one of my pet peeves as a network engineer is that people take their knowledge of home or small business networks and extend that to global Enterprise networks like Sony, Microsoft, ISPs, etc. The fact is that Enterprise networks have very little in common with a typical home or small business network.
I agree. It isn’t how the Internet works, but this is not an open system. It is very much controlled and managed to the Nth degree. The only randomness in this situation is the public IP from which the client is connecting. MS and Sony both have proxied and in many cases direct access to the devices. They do not have to rely on basic authentication factors. They have the potential to create (and should) a BlackBerry BES style authentication scheme. They have not gone in that direction yet, but the management capabilities are already in place.
“Companies like Sony and Microsoft certainly have issues…”
On a related and expanded note:
Quote from the article: “…located at legitimate companies that have been compromised by miscreants… According to Akamai, most of the malicious sources were Windows-based servers [keyword: servers] powered by Microsoft’s IIS Web server technology. The top five industries where those compromised systems reside are in entertainment, banking, hosting providers [sort of lends credence to how well network engineers are doing that job], software-as-a-service providers, and consulting services.”
Continuing the quote: “Even …[a] handful of attacking systems that appear to hail from major Fortune 500 companies…launching attacks against this blog have come from Internet space owned by Adobe, Cisco, Costco, Expedia, Experian, Honeywell, IBM, KPMG,Lockheed Martin, Opera Software, Sony, Symantec Corp., and the U.S. Federal Home Loan Bank of Dallas.”
So, Sony is on another “owned” list, for DDOS”. To the other network engineers of these companies on this list: That’s not good being associated, in a list with Sony, being “owned” for DDOS usage.
In normal operation the MAC in a packet is the address of the previous device, whatever that device hapens to be, but there’s no reason not to embed the origin MAC in a higher level packet.
Thank you Trip! That is exactly my point. MS and Sony have complete vertical control over the ecosystem. They can put whatever they want in the auth payload. Sure, it isn’t part of the TCP/IP packet structure, but it can certainly be added and used as an instant filter. The people arguing otherwise are networking purists and miss the glaringly obvious reality that systems can and do operate well beyond layer 3 traffic 🙂
full disclosure, I’m an MS employee, but I have nothing to do with XBL, email is my specialty, I just use XBL and other MS products a lot. That being said, were the consoles the only thing affected? I connect to XBL from my phone, my iPhone, my Surface, and various browsers in addition to xbox 360, xbox One. I don’t know about PSN, but I thought XBL is more of a general cloud service and not something that could be filtered like Tim suggested.
It is a general cloud service. That is very much true. However, the consoles, whether XB360 or XBOne, are still the most vital endpoints because these are the consumers paying for the Live subscription, it is where most of the revenue is generated, and downtime renders the device nearly useless. You can connect from your PC, phone, and many other devices along with the consoles. The difference is that my phone and tablet are not completely lacking their primary function if I cannot connect. I suppose that I’m advocating a separate authentication mechanism that is specific to the consoles and is not generally available to generic clients. It is definitely an outside of the box idea. Heck, it might even be pie-in-the-sky impossible, but I think it is certainly doable given the level of control MS has over the console ecosystem.
I’m an email guy myself, so I suppose the equivalent would be something like EOL SMTP connectors using TLS with SSL certificate name validation to establish direct communications with Hybrid configurations, on-prem Exchange, or external trusted orgs. Mail that passes through the connectors is trusted via originating IP, delivery scope, and DNS name matching against a validated SSL cert. These connections and the mail transferred between them bypass the standard EOP rules that process untrusted messages, directly forwarding mail to the server / database hosting the mailbox.
This obviously isn’t a direct translation and the process probably isn’t scalable to millions, but my thought is that a separate connection type that utilizes core attributes unique to the consoles would help keep those devices online even if the generally available authentication are bombarded by a DDoS. Just the existence of a separate auth system for the consoles would reduce the appeal of a DDoS because it would be much more difficult to attack and attacking the general authentication web services would not affect the millions of people trying to play games, watch movies, etc. I can’t log into XBL from my Windows 8 laptop today, no big deal.
I for one am a little happy that my 13 year old geek of a son gets to see the misery that these “hackers” have caused, and has been cheering on the grey hats that have been looking to take them down.
It’s all fun and games until you end up in jail. DDoS is still against the law, and these guys are hardly smart enough to avoid getting caught. Hope the few minutes of fame is worth the few years in jail that will inevitably follow. Just ask Lulzsec.
The truth is that they generally don’t put these kids in jail for a number of reasons. There are a lot of them. The media might paint them as victims – “…10 year old is jailed for hacking…”
It’s there parents that should be tagged with a large fine & the threat of jail time. This might help.
+1
Im still down xbox live on my one and 360
Doesn’t really seem “cowardly” – they didn’t run anywhere. They might not have brains but, they do have some audacity.
That said, I think the word “troll” is a much more accurate term.
True. Or how about out-of-control, unmonitored, juvenile cyberdelinquents. ;^)
hackers are just a bunch of loser looking for some attention there is alot of things they can do with the knowledge they have but they choose to be idiots and make people live harder yes i agree beeing on the network is not everything but they need to use their know how and be productive not idiots and i am saying idiot to be polite
Anonymously Threatening to blow up an airplane is very cowardly.
And definitely more than just anonymous sociopathic trolling.
Anonymous denial of services, is pretty cowardly and very lame.
Sociopath:Having a callousness that could be shown by not caring about others’ feelings, having no remorse when actions harm others, being aggressive, or being sadistic;
They are cowards because they remain anonymous.
On the topic of parents; why are these teens able to do these attacks? How are their parents not keeping an eye on their web activity. I realize that many parents are too busy or not computer literate enough to track everything their kids do but they still bear some responsiblity for what their kids are doing online.
I mentioned this earlier. Go after the parents with a huge fine & a threat of jail time, for aiding & abetting, & I think it would probably be more effective.
Find out what your kids are doing or face the consequences would work better.
Also, a facility to house juvenile cyberdelinquents that has no TV, internet, cell phone, gaming units, or other electronic gadgetry & keep them there until their addiction subsides might be effective. ;^)
The target of a DDoS attack has a list of the IP addresses of all the computers attacking. So if they know who is doing it, why don’t they go round them up?
Because those attackers are actually zombified computers which have become infected with malicious software. There are millions of such computers. They belong to people exactly like most of the families that couldn’t get their games to play on Christmas day — they know how to find downloadable stuff on the internet, but not how to evaluate it for threats. They download with abandon, as long as it’s “free.” Their computers harbor trojans that allow the real criminals to execute control remotely, hiding their own identities.
Because so many of those computers are in exactly the same places as the legitimate customers, it’s tough for companies like Sony to filter it.
The only way to reduce these attacks is to stop people from downloading malicious software and to stop them from connecting to the internet with infected computers. Handling complaints about IP addresses being used in a DDoS or similar illegal activity is an expensive and thankless job for an ISP. Most don’t devote nearly enough effort, because they’d have to raise their prices to pay for the extra staff and customer hand-holding. So they give customers a free subscription to an antivirus program and hope for the best.
I’m not sure that you can stop them without completely controlling the internet, which at this point in time is not a possibility because of the lack of international cooperation.
Do you think Russia is going to agree with anything the West proposes right now?
Go after the parents. If the kids won’t listen to their parents, have a special police taskforce that deals with suspected juvenile cyberdelinquents that can be contacted by the parents of out of control kids.
As a former jail guard let me say this – some kids don’t ever understand their criminal actions until the minute they are sitting in a cell for the first time. I’ve seen ‘tough’ kids break down and cry for mommy once they are alone and around a more menacing criminal element. And the same goes for many parents – they too don’t seem to always understand that their underage kid is on a one-way trip to prison later in life until they come and pick them up from jail/courthouse.
The Lizard Squad would be the types to cry for mommy within minutes of the door slamming behind them. A kid smart enough to launch an amplified attack is smart enough to know the difference between right and wrong.
Imagine if one of those little miscreants ends up in jail with Buba and the tells him why he is there , Poor Buba’s Christmas was ruined when his Xbox stopped working
They did good I can get access to all files except military under 5 min.
The code to everything that is technology is 01010101. If this code was not created then probley we wouldn’t even have to worry about none of this, because no technology would’ve been made.
My son can not get his profile to download
“My son can not get his profile to download”
Poor baby, sob. How’s he doing otherwise?
A new game box can’t talk to the mothership, why’s this a tragedy again? Have you considered speaking to him to teach him …
Naaaaaahh!
It should be a respected billion dollar industry like athletic sports. There is no reason its not except for anonymous trolls that noone can respect. I’m still laughing at the fact Kim Dotcom was ranked #1 in MWO 3. what a joke.
What these hackers are doing is taking food out of babies mouths.
I agree with you 100% hackers should stop their childish games and should stop messings with people feelings , this is really immature and innapropriate , there is no reason for this! (this imformation is really helpful by the way ill be sure to stay updated on this website)
1) Manually close down KrebsOnSecurity.com for 30 minutes
2) Infiltrate LizardSquad as “BryanKrabs”
3) ???
4) PROFIT
Why are parents buying such expensive presents for their little brats?
What’s wrong with a box of lego or meccano for a tenth of the price?
At first I thought the brats you were talking about were the brats at LizardSquad, and the expensive presents you were talking about was the broadband that these kids were using to get to the internet.
Maybe as punishment, those kids ought to be restricted to AOL dialup for 30 days.
I agree about the comment others have made here about upstream bandwidth. There is no technical reason why most customers would need that large of an upstream pipe – it is all sales and marketing so the broadband providers can “prove” that their service is superior.
My son requested an uplink speed of 5 Mbps or more to reduce lagging. With Time Warner Cable, the minimum downlink speed is 30 Mbps for 5 Mbps up. My son is paying the extra cost. I don’t see any problem with this.
I am not a Sony or Microsoft gamer, but I hope these kids get arrested and serve a proper sentence for attacking networks, leveraging systems flaws and creating huge transport costs to Telecom providers. I also hope that more and more systems get screened and close their misconfigured NTP. DNS and other services, because they offer free support to such stupid kids.
The blame needs to be put on the ISPs and corporate entities for allowing this traffic. The ISPs should be moniring for and stopping these attacks, and the corporations should be implementing better security.
Actions like this can always be traced to their roots, given access to all necessary logs. It is just a matter or time before one in the group gets caught, then the rest will follow. I’m going to “lolz” when I see the video of one of these pimply kids in handcuffs.
What, and do away with net neutrality? It’s not any of the ISP’s business what goes over the connection. They are not the Internet police.
The ISPmay be shutdown instead: http://en.wikipedia.org/wiki/Bulletproof_hosting (last paragraph).
It appears that Kim Dotcom gave the Lizard Squad group , 3000 Mega premium vouchers to stop the DDos attacks around Christmas day
—
Asking Mega management to approve 3000 @MegaPrivacy premium vouchers for @LizardMafia if they stop attacking XBOX Live and PSN immediately.
— Kim Dotcom (@KimDotcom) December 26, 2014
—
This article and comments bring to mind that any product or service that depends on an Internet domain for function or delivery is vulnerable to attack from stolen or compromised bandwidth anywhere in the world. A little Googling on DDoS found claims for many DDoS defense providers but none that actually guarantee anything because everything can be spoofed.
A company that provides an Internet-dependent product or service could contract with the major ISPs for its own DNS, transport, and content delivery services which would include robust ingress and egress filtering and network management to resist DDoS attacks. This would provide not just revenue, but a real “more reliable with…” argument for those ISPs. Continued consolidation of the cable industry would make such arrangements easier, but Net Neutrality rules that don’t provide for paid, prioritized carriage might make them impossible.
At present, a potential buyer of any Internet-dependent product or service must consider it potentially unreliable at the hands of a few bored Script Kiddies. Not a good prospect for the “Internet of Things.”
Interestingly, greater and faster adoption of IPv6 will solve many of the problems for the Internet of Things. It gives us enough public IP addresses to give every device a static IP address. This eliminates the need for NAT and allows for direct direct access management at the firewall level. Instead of many devices with unique MACs connecting to the Internet through a translated public address at the router / firewall, each device can have it’s own assigned public address. This will make MAC to IP pairing much, much easier. Basically, the company that runs the soda vending machine that accepts credit card payment will be able to give the 5,000 machines that they own a permanent IP. They will then register the IP and MAC pairing with the credit card processing company. The credit card processing company restricts access to only registered IP / MAC pairs. Sure, the MAC and IP can be spoofed, but it would be extremely difficult to obtain the thousands of valid pairs required to cause a disruption. If they need to take it a step further, the second layer will be ISP and/or geographic validation. Basically, they will keep an historic record of the ingress ISP and basic geographic location for each MAC / IP pair. If a particular valid / registered node starts to display abnormal numbers of connections / requests, then then it gets flagged and compared against the historic record of ingress ISP and geographical location. It would be nearly impossible to spoof a large number of devices at that point because they would not only have to have valid MAC / IP pairs, but the traffic would have to originate from the same ISP and come from the same basic geographical region. Unfortunately, IPv4’s limited number of addresses forces us to conduct the vast majority of transactions using Dynamic IP addresses (for consumers) and Network Address Translation for almost all networks (home or corporate) with more than one node behind the firewall. Smart Internet if Things vendors know this and are building their devices to leverage IPv6 as the default addressing scheme.
You keep talking about mac addresses as if they weren’t clear text? Tie them to credit cards what? I’m no hacker, but I imagine they probably only need to spoof one computer to penetrate a network, not many.
My home IP has always been static unless i manually change it. Its never been dynamic when I had DSL or FIOS.
For a home user, using public blacklists i can block 80% of the web, I know alot of hackers and companies nowadays say they are useless, but I wonder about their motives because the internet hasn’t changed as far as I can tell. Even if the bad guy change their ip address chances are they will end up on another blacklisted network. I cringe at the thought of trying to make whitelists or blacklists with ipv6.
But IPV6 scares me, because HTTP is overhwleming as it is. Trying to temporarily allow scripts and identify ip’s for webpages especially, is turning into a joke. We are lying to ourselves. I don’t care who you are.. IP4 alone is ridiculous to protect yourself from now. IPV6 will be worse.
And oh wow so many ip’s one can change to to stay unlisted with ipv6. No longer will i just be able to spot IP’s on paper and know what network they are from lol.
I used MAC addresses because I was responding to a comment about MAC addresses. It clearly put peoples attention in the wrong direction. I was simply implying that they are a unique identifier that I’d already built into every machine that can be used in combination with other identifying factors like passwords, etc as part of the factor. Let me change MAC address to unique client SSL certificate that is embedded within the system and rolls over on a scheduled basis. The reason I said MAC is because they already have it and can use it to create a unique connection pairing as a first level filter. Clearly it would not be the only filter man! Simply a way of dumping traffic originating from junk devices before it ever gets to the encryption, authentication, and processing systems. I apologize for leading in my argument. I should have gone into greater detail =p
Very literal audience on this blog! I used MAC addresses because I was responding to a comment about MAC addresses. It clearly put peoples attention in the wrong direction. I was simply implying that they are a unique identifier, any unique identifier, that is already built into every machine that can be sent in clear text, are not highly secretive, can be easily tracked, and can be used in combination with other identifying factors like passwords, etc as part of the factor.
Let me change MAC address to unique client SSL certificate that is embedded within the system and rolls over on a scheduled basis. The reason I said MAC is because they already have it and can use it to create a unique connection pairing as a first level filter. Clearly it would not be the only filter man! Simply a way of dumping traffic originating from junk devices before it ever gets to the encryption, authentication, and processing systems. I apologize for leading in my argument. I feel like the audience responding to this topic has never heard of a web application firewall; a device or virtual appliance that can offload Layer 7 traffic and inform core security devices of actors, thus blacklisting IPs and denying connections from entire geographic regions should issues escalate. I should have gone into greater detail.
I think most readers of this blog are seriously sick people. Just as the author. That’s what I think when I read all this rubbish comments about getting those KIDS really to prison. People, who really think that kids doing cyberstuff deserve real prison, live such a life of pure fantasies behind their computer screens and imaginary foes, cyberwars and cybercrime, that they actually became completely fallen out of reality.
And you’re not only reading but making an effort to submit an acerbic and snobbishly supercilious comment on BK’s blog about him or those who don’t consider hackers simply as misguided youth out for some innocent fun like you apparently do … why?
Perhaps that definition of “seriously sick” requires an honest look in a mirror on your part.
If you really believe people who cause massive disruption and downtime for companies and millions of people don’t deserve to pay for that activity when it’s done intentionally, then you live in a fantasy world.
Interesting choice of targets…not people I would want to have as an enemy online.
why is there no volume anymore on my Sky News on my iPad retna
All other stations play fine
Please help