There are still many unanswered questions about the recent attack on Sony Pictures Entertainment, such as how the attackers broke in, how long they were inside Sony’s network, whether they had inside help, and how the attackers managed to steal terabytes of data without notice. To date, a sizable number of readers remain unconvinced about the one conclusion that many security experts and the U.S. government now agree upon: That North Korea was to blame. This post examines some compelling evidence from past such attacks that has helped inform that conclusion.
The last time the world saw an attack like the one that slammed SPE was on March 20, 2013, when computer networks running three major South Korean banks and two of the country’s largest television broadcasters were hit with crippling attacks that knocked them offline and left many South Koreans unable to withdraw money from ATMs. The attacks came as American and South Korean military forces were conducting joint exercises in the Korean Peninsula.
That attack relied in part on malware dubbed “Dark Seoul,” which was designed to overwrite the initial sections of an infected computer’s hard drive. The data wiping component used in the attack overwrote information on infected hard drives by repeating the words “hastati” or “principes,” depending on which version of the wiper malware was uploaded to the compromised host.
Both of those terms reference the military classes of ancient Rome: “hastati” were the younger, poorer soldiers typically on the front lines; the “principes” referred to more hardened, seasoned soldiers. According to a detailed white paper from McAfee, the attackers left a calling card a day after the attacks in the form of a web pop-up message claiming that the NewRomanic Cyber Army Team was responsible and had leaked private information from several banks and media companies and destroyed data on a large number of machines.
The message read:
“Hi, Dear Friends, We are very happy to inform you the following news. We, NewRomanic Cyber Army Team, verified our #OPFuckKorea2003. We have now a great deal of personal information in our hands. Those includes; 2.49M of [redacted by Mcafee] member table data, cms_info more than 50M from [redacted]. Much information from [redacted] Bank. We destroyed more than 0.18M of PCs. Many auth Hope you are lucky. 11th, 12th, 13th, 21st, 23rd and 27th HASTATI Detachment. Part of PRINCIPES Elements. p.s For more information, please visit www.dropbox.com login with joseph.r.ulatoski@gmail.com::lqaz@WSX3edc$RFV. Please also visit pastebin.com.”
The McAfee report, and a similarly in-depth report from HP Security, mentions that another group calling itself the Whois Team — which defaced a South Korean network provider during the attack — also took responsibility for the destructive Dark Seoul attacks in 2013. But both companies say they believe the NewRomanic Cyber Army Team and the Whois Team are essentially the same group. As Russian security firm Kaspersky notes, the images used by the WhoisTeam and the warning messages left for Sony are remarkably similar:
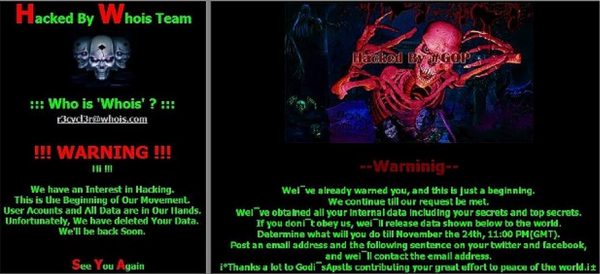
The defacement message left by the Whois Team in the 2013 Dark Seoul attacks (left) and the message left for Sony (right).
Interestingly, the attacks on Sony also were preceded by the theft of data that was later leaked on Pastebin and via Dropbox. But how long were the attackers in the Sony case inside Sony’s network before they began wiping drives? And how did they move tens of terabytes of data off of Sony’s network without notice? Those questions remain unanswered, but the McAfee paper holds a few possible clues.
A LENGTHY CAMPAIGN
McAfee posits that, based on the compile times of the backdoor malware used to upload the drive-wiping malware, the targets in the Dark Seoul attacks were likely compromised by a remote-access Trojan delivered by a spear-phishing campaign at least two months before the data destruction began. More importantly, McAfee concludes that the data-wiping and backdoor malware used in the Dark Seoul attack was but a small component of an elaborate cyber-espionage campaign that started in 2009 and targeted only South Korean assets.
“McAfee Labs has uncovered a sophisticated military spying network targeting South Korea that has been in operation since 2009. Our analysis shows this network is connected to the Dark Seoul incident. Furthermore, we have also determined that a single group has been behind a series of threats targeting South Korea since October 2009. In this case the adversary had designed a sophisticated encrypted network designed to gather intelligence on military networks.
We have confirmed cases of Trojans operating through these networks in 2009, 2010, 2011, and 2013. This network was designed to camouflage all communications between the infected systems and the control servers via the Microsoft Cryptography API using RSA 128-bit encryption. Everything extracted from these military networks would be transmitted over this encrypted network once the malware identified interesting information. What makes this case particularly interesting is the use of automated reconnaissance tools to identify what specific military information internal systems contained before the attackers tried to grab any of the files.”
The espionage malware was looking for files that contained specific terms that might indicate they harbored information about U.S. and Korean military cooperation, including “U.S. Army” and “Operation Key Resolve,” an annual military exercise held by U.S. forces and the South Korean military.
The Dark Seoul attacks were hardly an isolated incident. In 2011, the same Korean bank that was attacked in the 2013 incident was also hit with denial-of-service attacks and destructive malware. On July 4, 2009, a wave of denial-of-service attacks washed over more than two dozen Korean and U.S. Government Web sites, including the White House and the Pentagon. July 4 is Independence Day in the United States, but it also happened to be the very day that North Korea launched seven short-range missiles into the Sea of Japan in a show of military might. By the time the third wave of that attack subsided on July 9, the assailants had pushed malware to tens of thousands of zombie computers used in the assault that wiped all data from the machines.
The co-founder of CrowdStrike, a security firm that focuses heavily on identifying attribution and actors behind major cybercrime attacks, said his firm has a “very high degree of confidence that the FBI is correct in” attributing the attack against Sony Pictures to North Korean hackers, and that CrowdStrike came to this conclusion independently long before the FBI came out with its announcement last week.
“We have a high-confidence that this is a North Korean operator based on the profiles seen dating back to 2006, including prior espionage against the South Korean and U.S. government and military institutions,” said Dmitri Alperovitch, chief technology officer and co-founder at CrowdStrike.
“These events are all connected, through both the infrastructure overlap and the malware analysis, and they are connected to the Sony attack,” Alperovitch said. “We haven’t seen the skeptics produce any evidence that it wasn’t North Korea, because there is pretty good technical attribution here. I want to know how many other hacking groups are so interested in things like Key Resolve.”
Security firms like HP refer to the North Korean hacking team as the “Hastati” group, but CrowdStrike calls them by a different nickname: “Silent Chollima.” A Chollima is a mythical winged horse which originates from the Chinese classics.
“North Korea is one of the few countries that doesn’t have a real animal as a national animal,” Alperovitch said. “Which, I think, tells you a lot about the country itself.”
The “silent” part of the moniker is a reference to the stubborn fact that little is known about the hackers themselves. Unlike hacker groups in other countries where it is common to find miscreants with multiple profiles on social networks and hacker forums that can be used to build a more complete profile of the attackers — the North Koreans heavily restrict the use of Internet communications, even for their cyber warriors.
“First of all, they don’t have a ton of Internet infrastructure in North Korea, and they don’t have forums and social media which typically helps you identify, for example, whether an attack is from Russians or the Chinese,” Alperovitch said. “In general, the North Korean regime is one of the hardest intelligence targets for the intelligence and cyber attribution communities.”
On Monday, the folks at Dyn Research — a company that tracks Internet connectivity issues around the globe — said its sensors noted that North Korea inexplicably went offline on Monday, Dec. 22, at around 16:15 UTC (01:15 UTC Tuesday in the North Korean capital of Pyongyang). But the researchers stopped short of attributing a reason behind the outage.
“Who caused this, and how?,” wrote Jim Cowie, chief scientist at Dyn. “A long pattern of up-and-down connectivity, followed by a total outage, seems consistent with a fragile network under external attack. But it’s also consistent with more common causes, such as power problems.”
Interestingly, this pattern of downtime also was witnessed directly following the above-described 2013 attacks that targeted South Korean banks and media firms. According to Jason Lancaster, a security researcher at HP, the entire North Korean Internet space suffered a similar outage around the same time as the 2013 offensive against South Korea.
“When they came back online, one of those four [North Korean Internet address blocks] was routing through an Intelsat satellite connection,” Lancaster said. “What caused the 2013 outage? They never determined the cause. The speculation was that they were under attack, but there was never any proof of that happening.”
Additional reading:
US-CERT analysis of the computer worm used in the attack on Sony.
TaoSecurity Blog: What Does ‘Responsibility’ Mean for Attribution?
McAfee report on Dark Seoul attacks (PDF)
HP Security: Profiling an Enigma – The Mystery of North Korea’s Cyber Threat Landscape (PDF)







Current release of IOCs is not enough for attribution. Using the “we think it was NK” in 2013 and this attack is similar is circumstantial. Not proof. Using an old theory to prove a new theory.
This has become “trust the IC has evidence they aren’t releasing” and that’s how the White House and the FBI can come out strongly. Hard to be a skeptic of evidence you aren’t allowed to view.
One of the more interesting stories you’ve written. I’m still not fully convinced as the first request was for money not for the movie to be taken down.
According to the site “Digital Attack map” , North Korea has four fiber optic lines going into their
capitol ,Pyongyang
From the website Computerworld posted today.
“Ofer Gayer, security researcher at Incapsula, estimated North Korea’s total bandwidth at 2.5 Gbps, far under the capacity of many recent DDoS attacks, which typically are in the 10Gbps to 20Gbps range. “Even if North Korea had ten times their publicly reported bandwidth, bringing down their connection to the Internet would not be difficult from a resource or technical standpoint,” Gayer said, also in an email.
Almost all of North Korea’s Internet traffic passes through a connection provided by China Unicom, the neighboring country’s state-owned telecommunications company. North Korea has just a single block of IP (Internet protocol) addresses, or just 1,024 addresses, another vulnerability; in comparison, the U.S. boasts 1.6 billion I.P. addresses.”
Brian, do you have any speculation (or knowledge) on what the FBI’s classified evidence is about on the attack? Their press statement claims that they do indeed have more info but are not willing to publicize it.
“We haven’t seen the skeptics produce any evidence that it wasn’t North Korea […]”
What a hilariously ludicrous statement. It’s not up to skeptics to (impossibly) prove a negative, it’s up to people making claims to prove their claims.
The public evidence is not compelling. Try harder.
Several points:
1) MOST of the IT security people I follow on Twitter do NOT believe North Korea was behind the Sony Hack.
2) Many of the infosec people I’ve read make it clear that the previous attacks you cite were NEVER concretely attributed to the North Korean STATE,
3) Yesterday a story in the press reported that the Chase Manhattan break-in access point was finally identified. The story mentions that the FBI originally speculated that a Russian group – possibly state-sponsored – was behind it as a reaction to US sanctions on Russia. The FBI was later forced to rule that out. Sound familiar?
As for Beitjich’s post, this is one of the more egregious that he has done, for several reasons:
1) First, he is deliberately obfuscated what “attribution” means with his bogus list of multiple “meanings”.
2) Secondly, he recommends that people not even ASK for attribution, as that might entice the US government to institute some sort of “ID schemes”. This is just BS.
3) Third, he recommends Bruce Bennet as a “North Korea expert”, the Rand Corporation associate who consulted with Sony on the Interview movie, and who was responsible for convincing Sony to leave the actual assassination scene in. This man believed that once the DVD of the movie is smuggled into North Korea that it would motivate someone to actually assassinate the NK leader. Bennett is a known “hawk” on North Korea, and obviously a lunatic. Given that Beitjich is known to be hawk on China, his recommendation of Bennett throws his credibility completely out the window.
I am sad to see you buy into this NK bullcrap.
Richard, I’m going to go out on a limb here and say you might want to consider re-reading Brian’s post in light of the final sentence of your post.
Far be it from me to speak for Brian but my sense in reading his post was that his purpose was to objectively present the case being made by those who believe NK did the Sony hack, not to present it as something he himself has bought into.
I just re-read his post myself and I sure did not see anything in it indicating Brian himself necessarily agrees with any of the case being made by the “NK did it” faction.
Caveat – I have been known to completely misread things.
I for one appreciate being presented with all sides of a matter and being allowed to use my own judgement to make up my own mind.
1. Flase flag operation to pass Cyber legislation
2. Why was the State Department advising Sony
3. Initial emails did not mention anything to do with the move but only after the press mentioned it.
4. someone copied the released 200GB of data over 5-6 hours on the night of November 21st. Transfer rate equate usb 2.0 based on timestamp the very night that the very same day that Sony Pictures’ head of corporate communications,executive, publicly resigned from a $600,000 job wiith previous connections with NewsCorp
5. God’sApstls relates more to Japanese Anime ‘The Drops of God’ than DPRK ”
6. spoofed gmail account–frank1973.david@gmail.com
could reference Jerome D. Frank (the second edition of whose seminal work Persuasion and Healing was published in 1973) was a critic of nuclear weapons.
7. The compile language and timestamps are so damn easy to set manually when you compile the code..
8. Someone really knew the the network really well or they took a long time learning it.
If this indeed what SPE declared a week ago, why the sudden reversal knowing that the worst is still to come? Does that sense?
BostonGlobe writes that it was a publicity stunt by SPE to recoup money on bad film? Doubt as it would violate many local, state and federal criminal laws and SPE executives would be doing some serious time.
I think we have to go with there are still many unanswered questions.
OK, both my posts finally made it!
Dan’s post above lists just some of the issues with the FBI theory. There are plenty more. And ALL of the evidence publicly produced by the FBI has been debunked by any number of infosec people. So if there is ANY evidence of North Korean hackers involvement, let along North Korean STATE involvement, the FBI needs to produce it.
Otherwise in my opinion this is another case of the FBI jumping on a nation-state theory because it’s a nice way to produce a conclusion without ever having to prove it and it serves the US political interests.
“the warning messages left for Sony are remarkably similar”
Look at those two images again. WHAT “similarity”? That they are images with skeleton figures? Seriously?
This is like the alleged “malware similarity”, which most experts consider to be completely irrelevant as malware is acquired by various groups from other groups with regularity in the hacker community.
I mentioned Beitjich to Robert Graham, and he replied, “You mean the guy that gets simple things wrong, like the sophistication of the hack?” This is exactly the problem. The Sony hack was not terribly sophisticated, the malware used was not terribly sophisticated. Nothing in the hack points to nation-state level resources.
The main interesting component of the Sony hack was the amount of data exfiltrated – approaching several hundred GB at this point, and the hackers claim as much as 100TB (a claim I doubt – but 1TB or more seems very possible.) This again makes it much more likely that an insider physically exfiltrated the data rather than over the Internet.
AS131279
(peers)
4837 China Network Communications Group
22351 INTELSAT Global BGP Routing Pol
51040 PIRATE Piratpartiet
175.45.176.0/24 131279
175.45.177.0/24
175.45.178.0/24
175.45.179.0/24
aut-num: AS131279
as-name: STAR-KP
descr: Ryugyong-dong
descr: Potong-gang District
country: KP
Don’t you think that if the FBI/whoever released substantive proof of North Korean involvement that it would tell the adversary something about U. S. technology, capability, and other important information that might be useful to the adversary?
Regards,
Movie studios send and receive dailies over the pipes all the time. I would say sending terabytes of data for a massive movie/music/media company such as Sony is a daily or weekly occurrence. No one is shipping reels of tapes around anymore. Quite honestly I doubt they even noticed anything out of the ordinary (Obviously..lol)
Now another point is the majority of Koreans don’t like the Japanese. Japan invaded and ruled Korea many times throughout history and did awful and horrible things to Koreans while they were there. Look it up for yourselves. One of the worst insults you can say to a Korean national involves the Japanese. They really dislike them… My point is Sony is a Japanese company in the US making a movie that trashes NK’s ruler. This is hard to ignore. It leads to motive
I don’t know why people would think those pictures aren’t similar. are all hackers using same colors and same templates on their warning pages now? lol
I was a skeptic at first too, but the gov’t seems pretty convinced. And there is nothing to rule it out. I imagine they have more info they don’t want to share.
All this talk that North Korea doesn’t have the capablility or the attack wasn’t sophisticated enough for a state actor. Really? I disagree on both points. Besides backdoors built into software and hardware for gov’ts, or hardware on backbone lines like prism deciphering noise, I don’t really see the difference between state actors, hacktivists, or cyber criminals. The one thing that disturbs me though, is it always seems to be all of them vs society, instead of vs each other…..
They might not have said anything about the movie at first, but strangely it wasn’t on any torrent sites with all the stolen movies that were released.
And As for the terabytes in data stolen, I don’t know Sony’s network, but movie data is large and who knows how much they transfer daily. Might not be as noticeable as we think. Although, I wouldn’t rule out inside help.
N. Korea did not do the hack it was GOP Guardians Of Peace…
GOP – Guardians Of Peace
Want more go to YouTube… “David Wilcock Comments on Ben Fulford 12-16-14”
Very Interesting!
Good summary of all that is nonsense in the North Korean attribution of the Sony attack. Marcus Ranum’s point is particularly relevant: “[The Interview] movie angle only cropped up 3 days into the attack, at which point the attackers latched onto it like a bunch of gamergaters who’d found another excuse for misogyny. Prior to the movie angle, there was no North Korea evidence, then it starts popping up.”
http://fabiusmaximus.com/2014/12/20/rebuttal-holes-fbi-north-korea-sony-attack-74873/
Brian, after reading your article and all of the other analysis out there, I am beginning to wonder if Occam’s razor would apply here: Is it possible they used Dropbox to exfil data over a long period of time? I know, 100TB is a lot……. But, it would be convenient.
I do not see it being too far out of the realm of possibilities that SPE allowed Dropbox on their network.
Please see this blod post by arbor networks. seems the lizard squad did the ddos?
http://www.arbornetworks.com/asert/2014/12/north-korea-goes-offline/
I’m never a fan of XOR logic for things like the Sony hack (and global climate change).
It can be both: maybe North Korea paid others to hack Sony recently and/or South Korea in 2013. So maybe NK order the hack and used outsiders.
I assume there must be numerous hackers happy to vandalize for serious coin. NK may not have tons of cash on hand but surely enough to entice some outside help.
I can confirm that SPE did not block IRC; Dropbox is possible.
Who could trust North Korea or put past them any atrocious act were they capable. I am sure they would love nothing more than to have perpetrated this and it does not seem to have been too sophisticated.
What still makes me wonder is how they could be capable of this. How does one learn to hack a large company fairly successfully and undetected for months when they hardly have internet? I know that Sony does have at least the bare minimum of security practices. Do we have a profile of this “Cyber Army” ? I would greater fear my two year old’s abilities. Do North Koreans even know what ’email’ is?
Now do they have cash reserves and abilities to buy hackers from more capable nearby nations? That would be more believable, though I have not seen any info on that angle.
Does anyone care to explain to me why the U.S. is so intent on keeping the North Koreans out of South Korea? What’s in it for us?
Thanks for the coverage Brian, great reading!
“why the U.S. is so intent on keeping the North Koreans out of South Korea? What’s in it for us?”
Very simple. For the US, North Korea is a very convenient trouble spot to divide and conquer. Reconciling North and South Koreans would remove a big threat to South Koreans and Japanese, and the US would lose its role of protector that it uses as an excuse for having a lot of military bases on the south korean and japanese territory. Russians would can to build pipelines to South Korea through North Korea, expand their trading with the Far East, decreasing their dependence from the West and increasing their influence in the region.
The desperate, loony north korean regime pose some danger for Russia and China too due to a possible nuclear incident near their borders.
So the US govt intentionally bullies North Koreans with perpetual military provocations, accusations, etc.
The concern for amateur onlookers is that North Korea is an easy scapegoat. This is exacerbated by the early comments saying “no, it does not look like North Korea”, and then “the FBI has announced that it has indications that Sony was hacked by North Korea”.
Now all of a sudden industry experts seem to be rushing to validate the FBI announcement, without access to the ‘secret materials’ and using the same information that they had previously used to argue against North Korean involvement.
We, the people… are confused. We have learned the hard way that ‘intelligence’ is only as good as the person using it to justify wars in an attempt to finish what his father started (and make lots of money for a few). We also learned then that ‘experts’, journalists and politicians are often more than willing to jump onto a band-wagon that will later turn around and bit them (actually, I am not entirely sure that wagons bite, but will leave the metaphor as written). We even learned that some journalists and publishers see it as their civic duty to withhold information from the public when asked politely by a government official.
More recently we have learned that ‘intelligence’ agencies lie to ‘we, the people’ as a matter of course – even when under oath. We have found that at least some ‘intelligence’ agencies are totally unable to be trusted, and now we are being told to just trust this pronouncement.
Sorry, but I find myself doubting what I am being instructed to believe by ‘authoritative sources’ – because they have lied to me too many times. Our ‘leaders’ are reaping what has been sown, while people like me find ourselves behaving like abused children, who want to believe in hope but have been lied to too often.
I also disagree with the articles conclusion. NK is a proxy state for the big boys in the region. They are nothing but a giant zombie (host) state. Their main supplier of technology, food, fuel etc. is China. China’s capabilities are on par with the attack, and past attacks where advanced sophisticated attacks have been confirmed to originate from. Do I have proof? No, no one does. Just speculation. Bread crumbs….
I used to be responsible for a IBM midrange computer AS400. When I was not supporting user my spare time was spent on watching who was doing what and if necessary adjusting security or contacting the person running the job asking them why. Sony having a larger organisation than my 3 person team did not have a person seeing what was going on??
Hi Brian, good article but you don’t really seem to comprehend the technoligy you are writing about.
First off, the first blocks of a drive are called Sectors, not sections. Secondly, all data isn’t wiped because a few blocks are overwritten and they system remains running until reboot, as the MBR is only read during the boot. A simple equivalent to “fdisk /mbr” would have returned the hundred of thousand machines to their prior glory.
Like many stated compile time, compile paths and anything that can be found in the binary can easily be altered both prior and past the moment of compilation, so timelining the attacks like this, rather than using IDS data captured inside of their network to conclusivly tell when the attack started does not make any sense.
Additionally, i have never seen a weaker forensic analysis of a malware from McAfee until now. Out of 29 pages only 7 “cover” this specific hack, and a lot of is is repeating the same information over and over. The rest refers to other hacks with similaritys, but nothing conclusivly pointing it out to be the same group.
A forensic analys normally looks like: “hackers used a phinishingattack to distribute trojan.exe, which using a buffer overflow in Adobe flash managed to do a privilige escalation.” and a bunch of screenhots of IDA Pro which shows how admin users are created, firewalls are disabled and remote networking enabled. In McAfee’s report the first time we even see the IDA, they are already leaping backward in time looking at the other malware, making me think they didn’t even have the binary.
The last part is the amount of data stolen. I am not sure where the number of 20TB of data came from. Looking at the hackers own statements they seem to have gotten a bit over 50MB. I am curious to how long it would taken to pull 20TB over their links. Just pinging ANYTHING inside of the Korean ip-space is a weekend job, never the less getting all that data out.
I am reading up on the rest of the reports to see if i missed anything but for now this screams Flase flag operation.. If anyone has THE binary of the Sony hack i would really like to have a look at it myself.
This is the sort of research i was expecting, but then you want a sony movie
https://www.youtube.com/watch?v=kzLyvgMwgUU
FWIW Bruce Schneier recently blogged an interesting contrary view, expressing skepticism that North Korea did it. Worth reading for those interested in the subject.
https://www.schneier.com/blog/archives/2014/12/did_north_korea.html