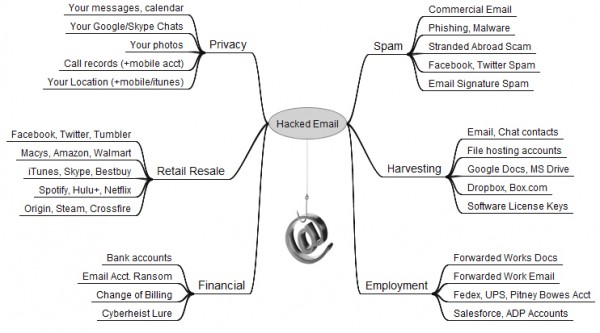
It’s time once again to update my Value of a Hacked Email Account graphic: According to a recent alert from the FBI, cyber thieves stole nearly $215 million from businesses in the last 14 months using a scam that starts when business executives or employees have their email accounts hijacked.
Federal investigators say the so-called “business email compromise” (BEC) swindle is a sophisticated and increasingly common scam targeting businesses working with foreign suppliers and/or businesses that regularly perform wire transfer payments.
According to new data from the Internet Crime Complaint Center (IC3) — a partnership between the National White Collar Crime Center and the FBI — the victims of BEC scams range from small to large businesses that may purchase or supply a variety of goods, such as textiles, furniture, food, and pharmaceuticals.
One variation on the BEC scam, also known as “CEO fraud,” starts with the email account compromise for high-level business executives (CFO, CTO, etc). Posing as the executive, the fraudster sends a request for a wire transfer from the compromised account to a second employee within the company who is normally responsible for processing these requests.
“The requests for wire transfers are well-worded, specific to the business being victimized, and do not raise suspicions to the legitimacy of the request,” the agency warned. “In some instances a request for a wire transfer from the compromised account is sent directly to the financial institution with instructions to urgently send funds to bank ‘X’ for reason ‘Y.'”
The IC3 notes that the fraudsters perpetrating these scams do their homework before targeting a business and its employees, monitoring and studying their selected victims prior to initiating the fraud.
“Fraudulent e-mails received have coincided with business travel dates for executives whose e-mails were spoofed,” the IC3 alert warns. “The subjects are able to accurately identify the individuals and protocol necessary to perform wire transfers within a specific business environment. Victims may also first receive ‘phishing’ e-mails requesting additional details of the business or individual being targeted (name, travel dates, etc).”
The advisory urges businesses to adopt two-step or two-factor authentication for email, where available, and/or to establish other communication channels — such as telephone calls — to verify significant transactions. Businesses are also advised to exercise restraint when publishing information about employee activities on their Web sites or through social media.
For more info on how to rethink the security of your inbox, check out this post.





We almost got hit with this two weeks ago, with a minor variation.
They criminal was not able to compromise our executive, so they created a similar email address (registered to visa print in an island nation) with an email address of executive@co rather than executive@com.
Unfortunately she sent the $70,000 on its way, and emailed the executive that the wire transfer was initiated. He responded with “what wire transfer”. She then was able to call the bank and get the transfer canceled.
Almost word for word what happened to an affiliate company of ours. Slightly altered domain name appearing as someone’s VP, email request to wire funds, funds were sent, fund transfer frantically reversed at the 11th hour.
Image: IC3 ??
Missing image?
The image is there, John, it just looks a lot like the surrounding text.
Ah, now I see…
Most, if not all of these kinds of attacks could be prevented by using the Guardog key which verifies the legitimacy of both the sender and the recipient.
Authentication does not stop at login. Instead, it continues throughout every iteration. Each time a user makes a request of the service provider – any monetary transaction or any transmission of information – Guardog institutes another confirmation. Guardog repeatedly verifies the user’s and service provider’s identity.
More information can be found at fortknoxdigital dot com.
Not only is two-factor authentication a good idea, but two person requirements for wire transfers over a certain amount. I.E. both the CEO and the accounting dept. professional both need to authorize the transactions; which would stop this type of attack in it’s tracks.
This is a great example of small businesses suffering from lack of procedures, security policy of the lack of enforcement of said policies.
Small businesses have very limited resources, and many times even more limited understanding of information security policies.
Instead of creating breach laws which make research hard to impossible, the government should be investing in educational and granted consulting resources to help small business put in place basic security measures which a surprising number of small businesses don’t have.
The situation on the ground right now is the doors are open security wise at most small businesses, and the bad guys are literally laughing all the way to the bank.
Sad, and true…
“two person requirements for wire transfers over a certain amount. I.E. both the CEO and the accounting dept. professional both need to authorize the transactions; which would stop this type of attack in it’s tracks.”
If they hacked one email account, how hard could it be to hack two of them? 2FA is the only way to prevent this electronically, and that’s if the 2FA system is a physical key or hard linked to a mobile phone (not a silly app that sits on the desktop waiting for someone to run a RAT and get all the 2fa codes they want.) Alternately, some sort of solid callback protocol (i.e. dial the exec’s cell # on file and ask for verbal confirm) would also mitigate it.
Thinking backwards, if a Invoice for payment comes in, one would (hopefully) THINK that this would not be the first email communication from this supposed company asking for payment.
Everyone is scared to pick up the phone and ask some SIMPLE questions to avoid fraud. Call them and ask what were the services you provided to us? If they give you a line of BS, like we were the company that maintained your landscaping, and we typically get paid in advance for our services….. And you rent the 11th floor of a Tower …. then MAYBE some one would question the legitimacy.
Its easy to be a couch commentator on this and blow holes in theories. The reasons the crooks are getting away with such antics is that everyone has an opinion and that takes away all hope for any sort of due care, due diligence or what a prudent man would do.
terms of agreement for services renders, a quote, a business card with a potentially valid point of contact, email communication prior to services rendered….Approval from someone to allow the services to be conducted…. visitor logs listing employees from that company actually on site…… something should be there prior to ignorantly throwing a payment out of the window.
As for the email addresses that are closely related, it boils down to attention to detail. I wont go down the IT road of how it should be done, because every IT situation is different.
Commmon, all it takes is a little bit of communication between offices to make sure the pots of gold are tapped by legit sources.
Taking extra steps in order to protect your company and/or job from any adverse action is number 1. That “O” in the front office would rather have a 5 minute conversation with a co-worker from the finance department, rather than answer why they sent a payment off to a place they never dealt with.
But the crooks hang up really fast when I tell them that they are not the provider of that service and that I have never heard of them…
Saying to call the person is not a good option. It is too easy to fraudulently forward a phone number, especially land lines.
Nothing’s bulletproof. But a verbal phone conversation (especially with a fellow employee, who’s voice and mannerisms are known) does add significantly more security.
I think the idea is that the CFO and bean counter would be on familiar enough terms to recognise distinct mannerisms and vocal cadences.
A Shibboleth nonetheless!
#1 item stolen in data breaches last year was email username and passwords. With the advent of big data, hackers are stealing different PII with each on, holding it and creating synthetic identities. This is a great article that shows how it start and how the funnel works. Nice job.
The part that is really quite scary is that they were targeting when they were out of the office (OOTF responder) and that there were 2100+ that fell for it…..how many received it and didn’t report it.
Great reporting….love your stuff!
There are times I need Xanax after reading your column. This one is scary.
And if you want a few simple scenarios, CSO stood up this post of Jan 22;
http://www.csoonline.com/article/2874166/identity-theft-prevention/fbi-and-irs-warn-of-pervasive-maddening-business-consumer-scams.html#tk.rss_news
Brian, I would be curious to know your opinion on which countries these scams originate. The banks are in Hong Kong. Where do you think the culprits are? And where does the money finally end up?
My major bank when we did wire transfers always got secondary verification, either a pass-code or they’d call directly a number on file and got a verbal. Many times the person calling you dealt with before so they knew you. Just sending out wires based on an email won’t do it.
You say businesses lost $215m. Clearly the glass is half empty. On the other hand, someone earned $215m as well.
Simple trickle down job creation.
$215 million…. as bad as that is, I can honestly say I wouldn’t have been surprised had the figure been higher.
I see your point.
These crooks simply send companies a bill, and the people who pay the bills act like the movie “Andromeda Strain” actors – staring at a screen and whacking each bill “paid” without investigating – or even calling to see if a five-to-six-figure invoice is even legitimate.
Crazy. Sure some of the spoofed emails from an “O” in the front office may knee jerk an immediate payment, but records typically would show some sort of correspondence, written and signed agreement for the services to be provided, no ?
In this scenario, it seems like it is more profitable for the crooks to use this method instead of messing around with CC’s.
It is becoming more and more painfully apparent that old school security is no longer keeping up with new school technology. Repeating verification, such as that offered by Fort Knox Digital, is one new school solution.
http://www.fortknoxdigital.com/#!
hehehe the problem with “old school” technology is, that “old” people use those technologies, and….Old habits die hard”.
many institutions don’t want to wander too far from their “tried and true” methods. Only after an awakening, like a breach will they understand the ways they have been doing business is outdated.
Brian wrote up an article a while back about the age of some of the PoS terminals out there which could be way out of date, or near end of life. That’s just one small example of people using a technology they feel comfortable with, and may run it into the ground until they are forced to change.
Situational awareness in the business realm should be mandatory. Train the people in the trenches, prove to the government that you have done so and receive a small tax break for doing so. The small talk I create at registers about breaches, skimmers, fake CC’s, and other things when checking out seems to be news to the employees.
Something has to change to thwart some of the approaches the bad guys are using.
Some how I can feel an incident of a fake 500.00 Obama Bill getting cashed at a major retailer real soon.
; P
Brian, for the home user and later versions of Windows, there is a direct connection between compromised email and logging into the home computer with the email account.
Another update for the graphic, the value of hacked email, is home stability that can be tied to categories of home utilities like trash pickup, cable/internet, water, home monitoring. I’m thinking once the Google driverless car gets released, that will also be part of your graphic. I believe engineers are tying the car to a ‘drivers’ mobile device as part of the convenience to summon a car.
Any company that actually sends a wire based on an “email” exchange from the CEO has some serious internal control problems.
I blame a lack of rigid procedures by companies that allow this to happen.
What people are describing would be an impossibility at my company even if the spoofer was actively responding to clarification via emails which is quite common.
Criminals are just taking advantage of companies weak internal controls, its been happening forever.
The fake CEO fraud is quite common in France. If you speak french, Google «fraude au président». and read on (if you don’t speak that language, Google Translate might be of some use) – there are loads of news stories and I bet you might be amazed as to what companies have fallen for this scam (the tire maker Michelin and a French football club are the latest victims) that wire very substantial sums to the bank accounts controlled by the criminals. In one recent case a West European company lost nearly 20 millions.
The @lizzard how to hack someones facebook account with greasemonkey – http://palhacker.org – was however active a few hours immediately after this story arrived out.