Hospitality giant Hilton Hotels & Resorts recently started offering Hilton HHonors Awards members 1,000 free awards points to those who agreed to change their passwords for the online service prior to April 1, 2015, when the company said the change would become mandatory. Ironically, that same campaign led to the discovery of a simple yet powerful flaw in the site that let anyone hijack a Hilton Honors account just by knowing or guessing its valid 9-digit Hilton Honors account number.
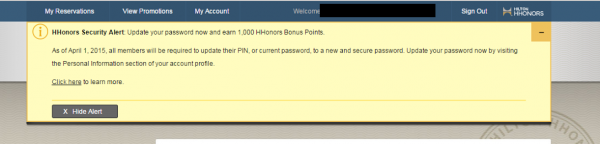
Until it was notified by KrebsOnSecurity about a dangerous flaw in its site, Hilton was offering 1,000 points to customers who changed their passwords before April 1, 2015.
The vulnerability was uncovered by Brandon Potter and JB Snyder, technical security consultant and founder, respectively, at security consulting and testing firm Bancsec. The two found that once they’d logged into a Hilton Honors account, they could hijack any other account just by knowing its account number. All it took was a small amount of changing the site’s HTML content and then reloading the page.
After that, they could see and do everything available to the legitimate holder of that account, such as changing the account password; viewing past and upcoming travel; redeeming Hilton Honors points for travel or hotel reservations worldwide; or having the points sent as cash to prepaid credit cards or transferred to other Hilton Honors accounts. The vulnerability also exposed the customer’s email address, physical address and the last four digits of any credit card on file.
I saw this vulnerability in action after giving Snyder and Potter my own Hilton Honors account number, and seconds later seeing screen shots of them logged into my account. Hours after this author alerted Hilton of the discovery, the Hilton Honors site temporarily stopped allowing users to reset their passwords. The flaw they discovered now appears to be fixed.
“Hilton Worldwide recently confirmed a vulnerability on a section of our Hilton HHonors website, and we took immediate action to remediate the vulnerability,” Hilton wrote in an emailed statement. “As always, we encourage Hilton HHonors members to review their accounts and update their online passwords regularly as a precaution. Hilton Worldwide takes information security very seriously and we are committed to safeguarding our guests’ personal information.”
Snyder said the problem stemmed from a common Web application weakness called a cross-site request forgery (CSRF) vulnerability, a type of attack that occurs when a malicious Web site, email, blog, instant message, or program causes a user’s Web browser to perform an unwanted action on a trusted site for which the user is currently authenticated.
The CSRF flaw was doubly dangerous because Hilton’s site didn’t require logged-in users to re-enter their current passwords before picking a new one.
“If they have so much personal information on people, they should be required to do Web application testing before publishing changes to the internet,” Snyder said. “Especially if they have millions of users like I’m sure they do.”
Snyder said attackers could easily enumerate Hilton Honors account numbers using the company’s Web site, which relies on a PIN reset page that will tell you whether any 9-digit number is a valid account.
“There are a billion combinations, but this testing on the PIN reset page could be easily automated,” Snyder said.
Hilton no longer allows users to pick a PIN as a password, and those who try to reset their password after logging in with the their PIN are told to pick a password of at least eight characters in length, containing at least one uppercase letter and a number or special character. Subsequent password changes, however, still do not require users to enter their existing password.
It is likely that the offer of 1,000 points for customers who voluntarily changed their passwords before April 1, 2015 was an effort to get more customers to ditch their 4-digit PINs. Hilton’s reliance on a 4-digit PIN to secure customer loyalty accounts was blamed last year for a spike in account takeovers in which customers logged in to find that thieves had cashed out or otherwise stolen their award points.
Many airlines that offer awards programs also still allow customers to log in with nothing more than a member number and a PIN, including Qantas and United.




“Many airlines that offer awards programs also still allow customers to log in with nothing more than a member number and a PIN, including Quantas and United.”
I want my left toe from my big toe to be used for indentification. Then I want my left nostril hair (of my choosing) plucked from my nose and then used for identification.
Lastly, I want my left cheek on my rear end to be scanned and that used for identification.
In short, lets get rid of all Internet use by any business. Like now.
For what it’s worth, I would argue that those are identifiers, not authenticators. Fingerprints, iris, retina, i.e, ‘what you are’ are just the equivalent of a username and should not be considered password-level. But that’s just me. 🙂
+1
and note: whatever you’re using to measure these can record the digital information, we can be retransmitted later, so it really isn’t particularly meaningful for more than an ID tag.
e.g. If I produce a “copy of my birth certificate” and someone scans it and sends it as proof of something. Someone else can later repurpose the scan for something else. — It’s just about as valuable as a number.
Your left cheek ( rear ) print would probably get replicated in a matter of hours with the cpu power these days.
Add the following lame-o companies to the PIN as password list:
– coop dot ch 4 digit numeric
– IHG dot com 4 digit num
– Lufthansa dot com 5 digit num
– miles-and-more dot com 5 digit num
Not quite as lame as the above but with room for improvement:
– ft dot com 5 character mixed case alpha and numeric
I’m sure after these companies are breached they will also say “we are committed to customer privacy and security” too…
most 401ks managers use the same.
“…they could hijack any other account just by knowing its account number…” Wow, what a hack…you only need to know an acct. no.l
With the page
https://hhonors.com/services/memberrequestpin.aspx
Hilton also unwittingly provides a tool that makes it easy to programmatically enumerate HHonors account numbers.
“Wow, what a hack…you only need to know an acct. no.”
Or guess at it. As noted in the post, the hack was such that it could have been automated. I know that a large number of very important people have accounts with this particular chain. And having their personal info out there (especially stay history and preferences) could cause some major headaches for them.
That 1 night in Paris will cost ya….
I guess it’s time to change the password for the chastity belt: “P4rty_G1rl” is no longer secure.
The description of the attack sounds much more like a horizontal escalation than a CSRF…
A CSRF typically requires user interaction, abusing the session cookie available in the logged in users browser.
If all they needed was an account number, it sounds like this was stored in a cookie or used directly in a URL or something, without checking that the logged in user was actually the holder of the account.
These kind of companies focus more on earning and less on protecting their customers
Until Security is directly tied to the bottom line it will remain an after thought. Compliance is basically a joke. We should forget about Pass/Fail compliance and start grading companies on ISO. Hey, Company A is a 94 company and Company B is an 84 company. Company A can now charge more for there service. You can save money with company B but your getting less security value.
+1
These guys deserve mad props for exposing the vulnerability and seeing it get fixed rather than exploiting it for personal gain. If they weren’t so upstanding, they could really have cashed out.
Does HHonors allow conversion of points to cash, gift cards or other value medium? Consider the cost if one bad actor (among the thousands of staffers world-wide with access to an account number list) teamed with a proficient script-kiddie who automated the process.
ka-CHing!
Jonathan
…or they could just enumerate all valid account numbers using the HHonors PIN Reset page as described in the article – no “insiders” required.
A minor point of correction: The CSRF did not require modification of the site’s HTML, which would have been difficult. It only required creation of a simple local HTML file that did a “Cross Site Request.”
I think what this is is “Broken Authentication and Session Management”, as well as “Insecure Direct Object References”, and not quite “Cross Site Request Forgery”.
No?
Thanks for the reclassification; it’s helpful, though the two are closely related. The broken auth / session management flaws were simply not explored in-depth by Krebs as this is just a quick disclosure and by no means a complete technical analysis.
Some “security consultant”…
This is not a CSRF attack, but rather an Insecure Direct Object Reference. CSRF attacks occur when you force a victim browser to make an unrequested state change. CSRF attacks require some form of input from the victim (IE the victim has to click your link or visit your website).
Insecure Direct Object References do not require input/action from the victim.
Key difference.. IDOR are much greater threat than CSRF.
Came here to say this. It doesn’t sound like any input was required of the user. Much more likely an IDOR.
I was going to say this too. If they are going to get the technical details wrong, then they probably shouldn’t post about them at all. I expected better from Krebs.
LOL. You guys are too much. If they create a page that forwards parameter requests to a victim to allow the hacker access, then it is CSRF. They found a way to combine this with an enumeration vector to circumvent that requirement, so you want to redefine it to IDOR. Great. “It’s not to-MAY-toh, it’s to-MAH-toh.” Actually, it’s both or either, sophomores.
If they wanted to target a PARTICULAR user, it’s CSRF – unless they are psychic.
Interesting article, other security websites are already starting to report about this topic
Fort what it’s worth, I updated my Hilton account to a more secure username and complex password as soon as I discovered they allowed something stronger than the member number + PIN option.
But the old login credentials still work too. They need to pull the plug on the old system …. now.
Therre are other problems with hilton.com and HHonors.com.
What would the easiest way to fix a security flaw like this be? (I’m new to the industry, sorry if it seems obvious!)
Interesting to hear what was going on behind what appeared to be a simple fail to the lay person.
Two points: The deadline for changing the password to earn 1,000 points is 25 March. Otherwise, it’s 1 April, without regard to the points. Second, a couple of weeks ago, Club Carlson went out with a requirement to change password with the same requirements — e.g., minimum eight characters, upper case, lower case, number, punctuation mark. Any connection – e.g., were/are their accounts similarly vulnerable – especially as the demand went out so close in time? Thanks.
N.b. I believe Qantas is number, surname and pin – not just number and pin. The addition of surname makes it significantly stronger if you are not targeting a known individual.
“Hours after this author alerted Hilton of the discovery, the Hilton Honors site temporarily stopped allowing users to reset their passwords. The flaw they discovered now appears to be fixed.”
This is why we need more Krebs type of people. It says a lot when getting a call from Brian incites more action than regulators and law enforcement. I’ve been in positions where I’ve had to visit FBI offices or I get calls from regulators saying there is a problem with something in our security posture and senior levels still only allow me to take minimal action. Yet, a call from Brian would be so bad my job security would be in danger as they start wondering why something happened and beginning a hurricane of activity to fix whatever is wrong.
Obviously, I never want Brian to bring bad news to any office I work for (nothing against you Brian 🙂 but sometimes when management just isn’t listening to security concerns it would be nice to be able to have that kind of backing.
It has been said the worst morning a business executive can have starts with “60 Minutes is in the lobby.” Yet, there was some time before whatever CBS found made it on air.
Today it might even worse to hear “Brian Krebs is on the phone.” Rarely good news and KOS hits the ‘net a lot faster.
Maybe a new VMWare can make several virtual instances of Brian?
Jonathan
I found a very similar IDOR in a very similar type of site for another company while working there. I am currently looking for work. In January, I applied directly to Hilton to work in an allegedly [long] open Vulnerability Assessment req (through that infamously awful Taleo* site) and even had 2 or 3 recruiters directly contact me about the same role, and then 2 of them allegedly investigated my resume submission with the hiring manager–and I never got a single bite from Hilton. And I have a decent looking and relevant senior tier resume.
Meanwhile, I am getting plenty of calls and interviews from other companies, especially ones where third party recruiters explicitly contact me, like they did for Hilton. I know this is not irrefutable evidence of Hilton having a poor or even just a slow moving security team, maybe they just disliked my resume. But I am personally pretty convinced of it, given that every other direct recruiter contact I have had led to at least an initial phone screen with the company/client. More importantly, if you use the tiniest bit of Google-Fu, you can discern that the requisition has been open in at least one form or another since early September, 2014.
I surely hope they are fast-tracking it now, but I won’t be responding if contacted!
* You could argue that the very use of Taleo itself constitutes a security exposure because the site is so awful and archaic that it probably drives 50% of the talent away to begin with, in an era of “instant applications” via Dice, Indeed, or LinkedIn.
Looks as if they are having more problems. After receiving an email this morning advising me to “update my Hilton Honors password”, their web site is responding “Due to technical difficulties, we cannot access customer profiles at this time.” after any attempt to change passwords.
Thanks a lot for sharing this with all people you actually recognise what you are speaking about!
Bookmarked. Please also consult with my site =). We
could have a hyperlink exchange arrangement between us