Many news sites and blogs are reporting that the data stolen last month from 37 million users of AshleyMadison.com — a site that facilitates cheating and extramarital affairs — has finally been posted online for the world to see. In the past 48 hours, several huge dumps of data claiming to be the actual AshleyMadison database have turned up online. But there are precious few details in them that would allow one to verify these claims, and the company itself says it so far sees no indication that the files are legitimate.
Update, 11:52 p.m. ET: I’ve now spoken with three vouched sources who all have reported finding their information and last four digits of their credit card numbers in the leaked database. Also, it occurs to me that it’s been almost exactly 30 days since the original hack. Finally, all of the accounts created at Bugmenot.com for Ashleymadison.com prior to the original breach appear to be in the leaked data set as well. I’m sure there are millions of AshleyMadison users who wish it weren’t so, but there is every indication this dump is the real deal.
Original story:
A huge trove of data nearly 10 gigabytes in size was dumped onto the Deep Web and onto various Torrent file-sharing services over the past 48 hours. According to a story at Wired.com, included in the files are names, addresses and phone numbers apparently attached to AshleyMadison member profiles, along with credit card data and transaction information. Links to the files were preceded by a text file message titled “Time’s Up” (see screenshot below).
From taking in much of the media coverage of this leak so far — for example, from the aforementioned Wired piece or from the story at security blogger Graham Cluley’s site — readers would most likely conclude that this latest collection of leaked data is legitimate. But after an interview this evening with Raja Bhatia — AshleyMadison’s original founding chief technology officer — I came away with a different perspective.
Bhatia said he is working with an international team of roughly a dozen investigators who are toiling seven days a week, 24-hours a day just to keep up with all of the fake data dumps claiming to be the stolen AshleyMadison database that was referenced by the original hackers on July 19. Bhatia said his team sees no signs that this latest dump is legitimate.
“On a daily basis, we’re seeing 30 to 80 different claimed dumps come online, and most of these dumps are entirely fake and being used by other organizations to capture the attention that’s been built up through this release,” Bhatia said. “In total we’ve looked at over 100GB of data that’s been put out there. For example, I just now got a text message from our analysis team in Israel saying that the last dump they saw was 15 gigabytes. We’re still going through that, but for the most part it looks illegitimate and many of the files aren’t even readable.”
The former AshleyMadison CTO, who’s been consulting for the company ever since news of the hack broke last month, said many of the fake data dumps the company has examined to date include some or all of the files from the original July 19 release. But the rest of the information, he said, is always a mix of data taken from other hacked sources — not AshleyMadison.com.
“The overwhelming amount of data released in the last three weeks is fake data,” he said. “But we’re taking every release seriously and looking at each piece of data and trying to analyze the source and the veracity of the data.”
Bhatia said the format of the fake leaks has been changing constantly over the last few weeks.
“Originally, it was being posted through Imgur.com and Pastebin.com, and now we’re seeing files going out over torrents, the Dark Web, and TOR-based URLs,” he said.
To help locate new troves of data claiming to be the files stolen from AshleyMadison, the company’s forensics team has been using a tool that Netflix released last year called Scumblr, which scours high-profile sites for specific terms and data.
“For the most part, we can quickly verify that it’s not our data or it’s fake data, but we are taking each release seriously,” Bhatia said. “Scumbler helps accelerate the time it takes for us to detect new pieces of data that are being released. For the most part, we’re finding the majority of it is fake. There are some things that have data from the original release, but other than that, what we’re seeing is other generic files that have been introduced, fake SQL files.”
Bhatia said this most recent leak is especially amusing because it included actual credit card data, even though AshleyMadison.com has never stored credit card information.
“There’s definitely not credit card information, because we don’t store that,” Bhatia said. “We use transaction IDs, just like every other PCI compliant merchant processor. If there is full credit card data in a dump, it’s not from us, because we don’t even have that. When someone completes a payment, what happens is from our payment processor, we get a transaction ID back. That’s the only piece of information linking to a customer or consumer of ours. If someone is releasing credit card data, that’s not from us. We don’t have that in our databases or our own systems.”
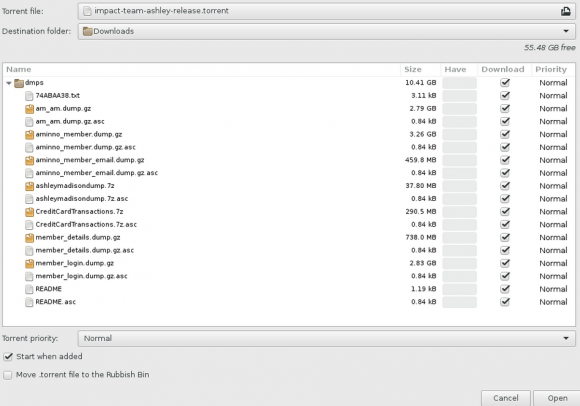
A screen shot of the archive released recently that many believe is the leaked AshleyMadison database.
I should be clear that I have no idea whether this dump is in fact real; I’m only reporting what I have been able to observe so far. I have certainly seen many people I know on Twitter saying they’ve downloaded the files and found data from friends who’d acknowledged being members of the site.
Nearly every day since I first reported the exclusive story of the Ashley Madison hack on July 19, I’ve received desperate and sad emails from readers who were or are AshleyMadison users and who wanted to know if the data would ever be leaked, or if I could somehow locate their information in any documents leaked so far. Unfortunately, aside from what I’ve reported here and in my original story last month, I don’t have any special knowledge or insight into this attack.
My first report on this breach quoted AshleyMadison CEO Noel Biderman saying the company suspected the culprit was likely someone who at one time had legitimate access to the company’s internal networks. I’d already come to the same conclusion by that time, and I still believe that’s the case. So I asked Bhatia if the company and/or law enforcement in Canada or the United States had apprehended anyone in relation to this hack.
Bhatia declined to answer, instead referring me to the written statement posted on its site today, which noted that investigation is still ongoing and that the company is simultaneously cooperating fully with law enforcement investigations, including by the Royal Canadian Mounted Police, the Ontario Provincial Police, the Toronto Police Services and the U.S. Federal Bureau of Investigation.
“This event is not an act of hacktivism, it is an act of criminality. It is an illegal action against the individual members of AshleyMadison.com, as well as any freethinking people who choose to engage in fully lawful online activities,” the statement reads. “We know that there are people out there who know one or more of these individuals, and we invite them to come forward. While we are confident that the authorities will identify and prosecute each of them to the fullest extent of the law, we also know there are individuals out there who can help to make this happen faster.”
Readers should understand that if this dump does turn out to be legit, that just finding someone’s name, email address and other data in the archives doesn’t mean that person was a real user. As the above-mentioned Graham Cluley points out, AshleyMadison never bothered to verify the email addresses given to it by its users.
“So, I could have created an account at Ashley Madison with the address of barack.obama@whitehouse.gov, but it wouldn’t have meant that Obama was a user of the site,” Cluley wrote. “Journalists and commentators would be wise to remember that the credentials stored by Ashley Madison must be considered suspect because of their shonky practices, even before you start considering whether any leaked databases are falsified or not.”




Yep! You’ve nailed it. I’m looking over the alleged “data dump” now, because I was seeking a bit of adventure today (I actually intended just to try parsing it as an exercise – and “Google myself”).
It’s complete junk. You guys are the only ones that I could find that called it out as fake – every other media outlet in this viral scheme is going around screaming “Haahahaha! They dumped it! Ahh! Their pants are down! Ahh!”.
I hate that site as much as anyone else does, but I hate the lying attention whores even more.
The “news” is a business and they don’t get viewers / readers with good news. There is a profit motive in making us afraid, very afraid. In the past the populace has been subjected to this form of influence, making us afraid so we’d accept massive actions that were not necessarily in our best (or even good) interests.
Most people barely understand how, or even when, they are being manipulated. The manipulators are very good.
Recommended reading
Influence: The Psychology of Persuasion
by Robert B. Cialdini, revised edition
http://www.booksamillion.com/p/Influence/Robert-B-Cialdini/9780061241895
Jonathan @nc3mobi
OK, it looks like I grabbed the wrong damn dump. Some legitimately bogus piece of garbage. That torrent has info_hash FF5C7AFB3F456FD327B39FBC8416E23756ED1692 (FAKE, FAKE, FAKE!).
The real torrent is 40AE8A90DE40CA3AFA763C8EDB43FC1FC47D75F1.
Once I opened up the dump of “emails”, boom… that’s it. I found what I was looking for – other “falcon”s. In a real data set, there are always a few good birds. 🙂 Tons of what appear to be real, “organic” email addresses, in a MySQL dump format.
I think there’s some validity to this after all.
You sir, are as culpable as the person/persons who dumped this data. There needs to be legislation introduced that holds your criminally responsible
for participation in the reporting/distribution/solicitation/dissemination of stolen data of a sensitive nature. Your intentions may be founded in curiosity, but providing specific hashes of what you purport to be the actual data set of stolen information is out of line and akin to knowingly receiving stolen property.
You, sir, sound like you’re on the list. Someone get kickout of the house and is sulking at starbucks?
Absolutely not. As a whitehat who has devoted his life to protecting organizations from the very set of circumstances AVID has faced, it belittles me to see the torrents of folks who feel the need to procure this data. What angers me beyond that is the ones who are willing to assist others to seek out this data, effectively paving the way for other like-minded individual digital terrorists to conduct similar operations that undermine our collective good.
Wait. How does this undermine the collective good? I sure wouldn’t be sharing and laughing if this were anyone other than Ashley Madison. Though I’d be laughing, sharing, posting, and contributing if it were, say, Westboro Baptist Church. That whole Sony thing, though? Hands off, not my game. It depends on the target. Social justice, karma, that kind of thing.
I figure I’ll do my little part in the interest of karma, and maybe some day, as I keep doing things — arguably, most things FAR less ethically grey-area than this — and maybe some day something nice might happen, for once in my damn life. Like a scholarship. Or a job opportunity for a guy with no education. sigh
Emphasis on the “if this were anyone but Ashley Madison” part.
Matt Falcon, your comments, in my own little world, truly gave me cause to laugh out loud. I agree with you on many levels. Thanks for the honest and inquisitive approach. People, you may not like what he said, but it rings true. Also, his sharing of the link is nothing but that. It’s your choice to investigate it…or not. Seems to me this article is on fact finding. I’m not condoning the hacking of AM, right to privacy and illegal obtaining of personal information is top priority in this day and age, however, if this in in fact true, putting the brakes on it now are slim to none. It’s really difficult not to smirk a little that it’s AM. 😉
“I agree with you on many levels”
Name three.
Lower Ground
Upper Ground
Level 1
I still don’t see it as a crime. If it was ANYONE else other than Ashley Madison I’d be for convicting but one guy in tech went to 3 of his tech savvy hacking buddieds and they say what was released is the real deal and Ashley Madison is attempting to pooh-pooh it to save face. Forget about suicides because no one put a un to a cheaters head to join their site.Hopefully some women who are still married to cheaters and good men too can get themselves rid of the person who could be a murderer and get a divorce. Yeah I said it. How many people out there married were told “You’re crazy, I’m not cheating!” that have an std or worse one they can’t cure or one that will eventually kill them. Cheating husbands and wives can pass HIV/AIDS while cheating too. Not sorry for that company. NOT. ONE. BIT.
Your white hat isn’t so white when u in a area with no sun!
While this high and mighty stance is all well and good, if a company’s security is so lax that a single person (or even a group of people, doesn’t really matter) can easily obtain it, then that company has no business handling sensitive data.
The fact of the matter is, hackers make the internet a safer place. While this is counter intuitive, and probably beyond your scope of understanding, hackers push companies to actually try and develop. This is why most leaps in cyber security and technology have been caused by small groups of hackers.
I guess the US Government, then, has no business handling sensitive data!
😀
White hat my arse. If you were, you’d be helping the poor women that the cheaters are bringing home STDs from the online brothel. Not wanting to protect the johns like you think you are. Information just wants to be free. Expose the scum of the earth if you want to be a white hat – steal if you want to be a black hat. But don’t think that if you work for a company and obey the law that you’re a white hat, at BEST that would make you gray.
Haha… ^^ this.
The data’s out there. All over the place. Right in the open. The URL to find it (as I did) is spammed all over the internet. I just used the wrong keywords to find it, originally – believing that there was only one.
Drowning in curiosity at this point, actually. It’s an interesting case study in the mechanics of the internet and society. 🙂 And your comment, freaking out about wishing that information was illegal? I’ll bet Ashley Madison – and all their messed-up members- are SO seriously wishing that were the case right now.
Ha, the guy hiding behind Empire is on the list, haha!
i have a theory for what is going on – the company Ashley Madison is dumping tons of fakes to make the real data harder to find. Thoughts?
In order to reduce the impact of the data being leaked, ALM could engage various third parties to actively dump several fake databases a day in this fashion themselves.
Once the real dump happens (if ever), who would know the difference, apart from ALM themselves?
Maybe they already are doing this…
It’s legit – I was on there a number of years ago, as a single guy I should add, and I am accurately listed in the data.
The article says this:
“The former AshleyMadison CTO, who’s been consulting for the company ever since news of the hack broke last month, said many of the fake data dumps the company has examined to date include some or all of the files from the original July 19 release. But the rest of the information, he said, is always a mix of data taken from other hacked sources — not AshleyMadison.com.”
That refers to the transaction Excel spreadsheets that were made available. Those are likely accurate on the whole. Yet the rest of the data may not be.
Have you read the content of the rest of it? It seems pretty legit.. if it’s not, where is it from?
Easy way to find out – log in and compare to real profiles – you can do that without paying.
Ditto. My throw away account I use for spam and other sites I don’t trust is in there. Also single guy and it was from like 4-5 years ago. I can’t understand why someone wouldn’t be smart enough to use a throw-away. My personal is for friends and legitimate accounts only…
There is a lot of talk about email addresses but the real issue will be credit card details? Email addresses can be false but a credit card transaction log, with a name, is more demaging. Are there actual billing details, such as name and address include in the files?
When the story broke a few weeks ago, I had a buddy tell me “Oh crap I was on there”. I found him in the data today. No way this is fake. Even his postal address was right.
I downloaded the files, and best file was actually the smallest zipped file ( ashleymadisondump.7z ). It had stuff that could easily be read ie. doc’s/ppt/xls/pdf’s.
The rest were just massive server logs, and when unzipped were even more massive single file text files, which really could only be read by programs that can handle 1GB+ text files such as VIM.
How do you check to see if someone is on there?
Download the torrent and grep through the archives.
How do I know if I’m downloading the right torrent and not a virus?
I would warn anyone who tries to access any dump of sensitive data that a major corporation with some of the most advanced security teams the world over on their payroll to monitor and contain a breach of this scale. If we learned anything from ES, its that there is no such thing as anonymity anymore and I would advise to let this blow over and move on with your life. If you were a member, chances are your spouse is already aware you are a scumbag POS and maybe you should re-evaluate why you’re looking to ruin your marriage in the first place. I’d be very surprised that AVID isn’t introducing false dumps themselves, creating a “rabbit-hole” of false data to pad actual stolen SQL dumps with rubbish. Let the appropriate authorities identify these “hacktivist” losers who continue to chose to waste what could be otherwise brilliant talent to introduce fear and to promote their own agendas without weighing the consequences of their actions in regards to our collective right to personal privacy and anonymity. Promoting or distributing stolen sensitive material that has the potential to ruin lives is a zero sum game that ought not to be played.
“Promoting or distributing stolen sensitive material that has the potential to ruin lives is a zero sum game that ought not to be played.”
As a purely technical nitpick, it seems like you’re misusing the term “zero sum game”. It implies that by greatly hurting many people, the hackers are greatly benefitting themselves (or at least that SOME participant is benefitting). (In a “zero sum game”, the sum of all players’ payoffs is zero.) … when I’m guessing you meant to say that the hackers hurt other people while gaining no good for themselves, right?
Looks like there are some competitors pretty interested in looking at the dump too 🙂
https://i.nyr.es/Captura-de-pantalla-2015-08-19-a-las-6.02.27-m3usonN8Iw.png
You bet, it’s a free prospect list! Just email them all with a chance to get laid to change their mind.
I see some other interesting files in that screenshot 😉
I am with an organisation that had quite a few emails listed. After a quick search I would say 90% of the emails in the list were to people who do not exist. Given that fake emails are being shown, we can’t really have any faith that the real email addresses were actually used and that someone else just entered their email address. There is likely a real John.Smith @ many domains used. The whole 32M + users seems improbable to me anyway as legit users. I seriously doubt Bill Clinton signed up using a whitehouse.gov email address before he left in 2001. I pity anyone whose name shows up this way. There could be suicides etc…
The onion site mentioned a key that lets you differentiate between real and fake accounts. Did you notice whether that seems to work or not?
The Onion? Ah, yes, with the key “f001ed100” you’ll only get legitimate data.
As @Brian noted, Ashley Madison didn’t verify email addresses (nor do most cellular providers).
It’s common practice for people to enter various addresses (PotUS variants, john.smith variants, ….) into databases for fun. Beyond the people actively entering junk information, many people don’t seem to know what their email address is, and manage to enter someone else’s….
In theory it was possible to walk into the Ashley Madison office, speak to their security chief, and ask him to wipe out an email address from a bogus account…
Here’s the key question: Does Ashley Madison really get rid of your site history for $19? Or do they pocket the money and do nothing? Anybody got any proof of the facts?
It’s hard to prove…
Someone claimed that the credit card records included the payment to wipe out the records. If that’s the case, then….
One problem is that I don’t think anyone has established the beginning and ending dates for the breach.
Imagine that your records existed on date 3, and on date 4..10 the compromise was ongoing. On date 6 you pay to have your records removed. If they’re removed on date 7, but the breach has already exfiltrated your data, then it might seem like your payment didn’t work, even though, perhaps it did…
I can’t speak to any of these versions, although I can speak to a different version if @Brian wants to. … Companies really should be fined 90% of their gross income for taking email addresses without validating then properly…
I’d like to check if my ex boyfriend was ever registered but I don’t have the technical expertise to do the whole torrent thing. Is there any other way to check? Any other place I can get the file?
He’s your ex… move on, lol.
Who cares… If he is your ex, move on. Clearly not someone you need to be hung up on if you think he was using the site. Let it go, don’t waste your time.
If you have doubts in the first place, seeking resolution by grepping through what are most likely fake data dumps at this point is your least likely path to resolving your doubts. If you’ve reached the point where you no longer trust his word, and are seeking to confront him with “evidence” gleaned from the net, the relationship is already DOA. Move on, and find someone who you can trust and who appreciates you and earns your trust so you aren’t constantly worrying about where or who he is with when you aren’t together.
Yes, thank you for the advice everyone, but he’s still my friend and I’d like to know if it should stay that way.
What does one thing have to do with the other? You’re being over dramatic for absolutely no reason.
I can understand why she might want to do this. The issue about cheating isn’t the sex, it’s the dishonesty. I’ve dumped platonic friends for less.
I’m sure if this dump turns out to be legit, it will be added to https://haveibeenpwned.com/, wait a month.
Edit, Actually Troy said this regarding the AshleyMaddison hack:
“only those who have subscribed for notifications and verified their email address will be able to discover if they were in the breach due to the sensitivity of the data” Oh well.
I checked the dump and your friend is in the list.
Lulz.
If he’s only your friend, why you worry about it, he is free to do as he pleases, just like you
If he was really your friend I doubt you’d be trying to dig up past dirt on him out of suspicion. Maybe reconsider your priorities and the kind of friend you want to be to people. And whether you’d want him or any other friend digging through all your past potential misdeeds.
Leslie,
The only problem with your question is that you are asking it on an InfoSec site and the IS industry is predominately male. Thus the majority of the readers/commenters are men (exception noted for Stefanie – if it’s a real name — above). Men and women think differently, so the men can’t understand why you would want to know if your ex-boyfriend (now ‘friend’) possibly cheated on you when the two of you were dating… or if he possibly cheated on someone else and is just a sleaze in general. My guess is you would find it hard to remain friends knowing that fact. Follow Jeffrey’s advice and check haveibeenpwned.com.
Okay, I’ll get back to my Gender Studies class now. 😉
https://ashleymadisonleakeddata.com/
Also note that AM has existed for a long time, so no proof that he’d been cheating while he was your friend. Also, you can also sign up to the site as as single.
Oh god no… my name has been found in that database and someone has already emailed my wife about it. She freaked out and said she is divorcing me and taking the kids and the house. MY LIFE IS FINISHED! I am going to kill myself
Wondering if the hackers could make backpage.com their next target? Saw the story on Al Jazeera story on tv: http://america.aljazeera.com/watch/shows/Ali-Velshi-On-Target/2015/8/child-sex-trafficking-in-america.html
I just downloaded part of the torrent that’s on Pirate Bay, specifically the one that has details of credit card transactions. I then went back through my credit card statement and found a date on which I’d made a payment to Ashley Madison, and checked it against the relevant date in the downloaded file – and it didn’t include my details. I’m going to keep on trawling through the files manually, but since there are 2700ish of them, it’ll take time. My initial impression, however, is that if the credit card file is real, there are omissions from it.
It’s a MySQL dump, and forget about trying to import it onto a local server, it will take forever. On OSX, use the Console app and filter by specific keywords until you find the user ID. Console app is designed for large files, but you’re gonna need to do some scrolling as it only loads about 200 MB into memory at any time. Still, it’s the fastest way to comb the data that I found. Faster than grep.
The data is real. Found my cheating ex-wife on there. Too bad my divorce trial ended a few weeks ago, this could have been useful to my attorney. The most interesting bits are the sign-up date, profile text, and “preferences/turn-ons”. The last one… Yuck!
There is a lot of talk about email addresses but the real issue will be credit card details? Email addresses can be false but a credit card transaction log, with a name, is more demaging. Are there actual billing details, such as name and address include in the files?
I downloaded the torrent. I had actually set up the account for my spouse and my credit card information is there, along with our address, the type of credit card, and the last four digits. It was tough to find as there is a separate file for each calendar date and I couldn’t remember the exact date we created the account.
Before anyone gets all judge-y, we are actually in an open relationship (but not really swingers and not very kinky) so it was one of the few options available to us to meet other opens in our community. If I was actually a cheater I would probably be in tears right now. I’m still not in any way thrilled because I’m not too keen on professional connections knowing our private business.
If this data is put into a format that is easily searchable, a lot of people will be screwed.
I am assuming that the users name (from the credit card) is also included?
I can see how your concern is warranted in a conservative community (so screw those guys), but I certainly hope that any progressive or sensible person would have no qualms about others’ actions in consenting adults’ private life. Loyalty is a virtue and hypocrites are unpleasant, you do not seem unpleasant and have not betrayed anyone.
It undoubtedly will be searchable, so resign yourself to that already. As far as your situation, this is a perfect example of why all the moralizing assholes on the internet crowing about this hack as karma are in the wrong. Even if it was all cheating spouses that could be compromised this would still be a terrible thing, but it’s going to fuck with the personal lives of a lot of people who did nothing whatsoever wrong.
As a silver lining, you should also expect that it won’t JUST be you and your spouse in your social circle on that list. A whole lot of other people you know are going to be on there to. Once the dirt starts to come out about everyone, maybe, hopefully, most people will take a step back from their moral grandstanding and acknowledge that nobody’s perfect and everybody’s private business is their own.
I’m cool with the open relationship thing, provided all parties are consenting. Absent consent, it’s just cheating cloaked in a different wrapper.
Hopefully you exercise due diligence to ensure that the partners you hook up with are single or also in consenting open relationships. Otherwise, you’re signing up for some nasty karma if you are aiding and abetting someone else to cheat through your own willful blindness.
I’m cool with open relationships provided all parties are consenting. Absent consent all around, it’s just cheating cloaked in a pretty wrapper.
Hopefully you exercise due diligence to ensure that your hook up partners are either single or also in fully consenting open relationships. That way, you keep your hands clean and don’t invite any nasty karma into your life. Aiding and abetting a cheater is not something to be proud of, nor is willful blindness.
Someone explained which details you could forge somewhere when talking about how to sign up for AM without giving real details (perhaps it was on /.?).
It’s something like this:
1. Get a pay-as-you-go disposable cellular subscription (or free short term VoIP number) — using cash (disposable phone is better so that the IMEI isn’t tied to any other IMSIs, although you want the other phone to not travel with you — or else two IMEIs are seen following the same tower path — which for long enough periods of times hints at correlation).
2. create a credit card w/ real info
3. then add a secondary user with a bogus name, to get another card.
4. create card transaction against the secondary user’s name and the disposable cell number. Enter any street name they like, but the street number needs to match the card information (I think this is because people are very inconsistent in how they write street names [X, X av, X ave, X avenue, avenue X, ex ave, exx av., …]). Along with the right postal code. If the street number is common, then you don’t learn much…
There are three general categories of accounts:
1. Real person with real data
2. Real person cleverly masking data (as poorly recounted above)
3. Person faking data to embarrass someone else (as with 2)
I don’t think it’s possible to distinguish these cases using just a dump.
If you can get access to Real person’s credit card transactions and can identify an AM transaction, that’s probably fairly good evidence, but that shouldn’t require the AM dump (if it’s even possible to get/identify said dump).
Well some of the passwords are safe. Bcrypt doesn’t offer much protection if your password is on a list of the 10,000 most-common passwords:
http://www.passwordrandom.com/most-popular-passwords
Ashley Madison’s highest priority should be to tell users to change their password on the Ashley Madison website, and any other website where they have used the same password.
What is the Quantum Magazine posted there? I know of the old mathematics magazine, but not this.
The ex-CTO of AM (now its consultant) claims that AM did not store credit card information, only a transaction ID provided by their payments vendor. He claims that all credit card information is therefore false. Can somebody verify this? I don’t worry about email addresses, I always use throw away ones for this sort of stuff. And no, I am not a scumbag, I am just a normal person who for reasons of my own (which I consider private AND NOT amoral) uses sites like this. No one has the right to judge me, and no matter what people think of my actions re AM, no one has the right to intrude in my privacy, not least of all the scumbags who hacked the site.
The last 4 digits of the cc, your mailing address and full name are all visible in their transaction database dumps. I verified this by x-reffing the time I signed up last spring. I believe even my paid delete transaction from like a week later was even in there [facepalm] ALM messed up bad.
^^this. I did the same. My data was there.
you can tell who the real pro cheaters are when you see “gift card” as the cardholder name, lol.
Ok. I also downloaded the files and checked in the credit card transaction files. I paid with Paypal so it was easy for me to check the transaction dates. So I looked at the appropriate files and I did not find myself. Is there a separate transaction file for Paypal users? Is it possible that I got lucky by using Paypal?
Did you “get lucky”? I certainly hope not. Your cheating/ intent to cheat is not “normal” behavior and yes, it makes you a scumbag, however weakly you try to justify it.
Someone stealing the data isn’t right, but it doesn’t diminish your douchebaggery at all.
Sure. I did. And my sympathies on being the victim of gov and church sponsored morality Stereotyping.
Casting judgement on what other people do in their personal relationships is a far clearer sign of a broken moral compass than somebody cheating on their spouse. The louder someone harangues others for their supposed personal sins, the more certain I am they have far worse skeletons in their own closet.
I paid through Paypay as well, and having checked my most recent payment date I don’t appear in the credit card database (see above). When I have more time later I’m going to find dates for all my past transactions (all Paypal), and check them individually. Will update later
Can anyone who has the technical knowhow confirm whether or not the dump includes details of people who paid with paypal? I definitely registered with a fake name etc, but I did pay with paypal. I have no recollection of what details I had to provide at the time, but I’m hoping to god my details are not in there. If they are, I clearly have nobody to blame but myself. I’d also like to say that while it’s easy for people not caught up in this to make fun etc, I am in no doubt that there will be suicides as a result of this if the information becomes mainstream.
Nah, if you paid with a third party service such as Paypal and did not enter your real email address or your real name on the Ashley Madison side you are fine.
Thanks for confirming! So glad I paid with PayPal and never used their crappy app.
People have every right to judge you in, quite literally, the exact same way you judge the people who did the hack as “scumbags”.
What? One is my personal life, my personal decisions that do not affect anyone but me and my spouse; the other is a scumbag intruding in it. If you believe in God, let him judge me and send me to hell if you want. Don’t let scumbag hackers play the role of God!
I’m an atheist, so I don’t play by that rulebook. If someone walks and quacks like a douchebag, they are probably a douchebag.
I typically leave them to their own fate unless they try to rationalize their way out of their douchebaggery. At that point, they are not only douchebags, they are hypocrites.
Dishonesty merits judging, IMO. And cheating is dishonesty. It tears families apart and leaves lasting psychic wounds on both children and betrayed spouses alike. Then there is the STD issue, as most married couples have unprotected sex with each other. A cheating spouse risks the health of their partner and deserves to be called out as a scumbug.
I’m single, kinky, and in multiple open relationships that are fully consenting. I see this crap go down all the time in my extended social circle, and know the heartache it causes for those whom I care deeply about.
I agree with you douchbag. So why don’t you leave us “unfaithful douchbags” alone and stop passing judgement. Just leave us alone to deal with our own personal issues; I did not ask for your judgement or opinion, and we certainly don’t need your insults. Now what the hackers did is indeed criminal and I have the right to call them scumbags.
Oh the leak is 100% real. Just check the CC dump csv files.
My marriage seemed to be at its end and signed up hoping to find someone to chat with in the same sort of scenario. After about a week of seeing the kind of creatures lurk there, I peaced out. Did the whole paid delete option. Came to my senses and decided it was time to give it one last big shot and we have been working on things since. But hey guess what? Now I get to undo all of that because I caved early on at a time of weakness. ALM still kept the transaction logged in their db. So tonight’s gonna make for interesting conversation…The last thing I want is for my loved ones to discover this crap on their own. Best to come clean now people. Every transaction from 3/21/2008 thru 6/28/2015 is in the dump. Whether you paid for deletion or not means jack.
At the end of the day though, the hackers are just as bad as the millions of us they just doxxed. The world isn’t black and white. To paint something such as this with broad strokes is a dangerous game. Let alone the fact it is nobody’s place to impose their own moral compass on the rest of the world.
As bad as those doxxed?? Hardly – they are orders of magnitude worse.
There are women in that dump. Not many, but there are. And there are women on that site (truly, I met several of them). Have the Impact Team never heard of domestic violence?? Or do cheating sluts deserve what they get?
There are also single people on that site. Met some of them, too. “Cheaters” aren’t always married. Should they also be painted with the same Scarlet Letter as the marrieds?
No, the Impact Team are in fact scum. Pissed lonely pathetic wankers. Lots of lives are going to be ruined by this doxx (not mine, thankfully). The Impact Team really better hope none of them are resourceful, powerful, or deranged enough to find them and return the favor.
MJ,
Are you finding CC details? Thx for your research.
How do I download these files? I accessed this site a couple of times, a few years back, and now I am panicking. Things were not good at home and we were living apart at the time. I never met anyone from the site but it’s going to be difficult to convince my wife that I’m being honest. I need to know what is on there as she will ask a hundred questions and I don’t remember what I did on the site.
I’m proud of you for coming clean. Perhaps your chat with your wife will lead to a new direction in your marriage.
If you didn’t actually chat or hook up with anyone from the site, it probably doesn’t matter what you browsed there. That you visited the site at all is likely to be the only issue that counts for her. So it’s probably okay not to remember the details, which you probably don’t anyway.
I just finished combing through a large portion of the dump, it definitely seems real. I verified with multiple people who i knew had accounts on there and their emails were there. Also went deeper and looked at their profiles, usernames and descriptions which are also in the files. its pretty extensive.
Regarding the credit card details, while the whole credit card number is not there, it does contain verification email addresses, last few digits, type of credit card, transaction dates and billing addresses and more. so if any of you did use a card on there, i would probably play it safe and simply cancel it.
On a positive note the passwords are not plaintext, and actually secured using a fairly secure hashing algorithm (bcrypt) as opposed to the usual MD5/plain text usually seen in most dumps. I have not examined the hashes carefully but as of right now i do not believe a salt was used and therefore It is probably just a matter of time before they are cracked.
Also fun fact, theres a couple of @whitehouse.gov addresses in there, which doesn’t mean they are real but pretty amusing to find them in there.
Would data dumps of this sort be likely to include the IP address associated with the anonymous email address used to login to the site?
Could someone speak to the technology here, and whether this is plausible? I’ve often wondered just how anonymous throwaway email addresses are, especially when all used by the same internet connection.
salt or not any pass can be cracked. bcrypt is slow as fuck though, i can do like 300K/sec with md5, with bcrypt it’s more like 1K/sec.
Can you link CC transactions to profiles? I accessed the site a couple of times during a bad patch in my marriage. I never met anyone from the site. And now I have to tell my wife. I am hoping my CC is linked to my profile so I can at least prove it was a short lived thing. Thanks.
Yes. CC transactions have the user emails associated w/ them in the dumb. Just need to x-ref tables and run some pretty basic SQL queries.
A transaction number alone does not contain the charge card information. It is linked first at the payment site then at the provider. So, associating a transaction number with an email does not confirm the user.
Remember, the emails were not verified. Some could use yours, deliberately or accidentally.
I created an account to look for my cheating father last August using my real email address since I didn’t have any reason to hide anything. After the fact, I got to thinking about it and didn’t want my email address associated with this site, so after a week of looking for him, I went to close my account and got all the delete options, so I chose paid delete. My email address is not in the dump, so I can only assume my CC info isn’t either, since you say they are tied.
Stange i do the banking for my paraplegic brother and he has been meeting married women. Nice try guys but where did you get his email and the first part of hid credit card.
Move on, and find someone who you can trust and who appreciates you and earns your trust so you aren’t constantly worrying about where or who he is with when you aren’t together.
I have little sympathy for those caught out in this hacking. Sites like this one broke up my 37 year marriage. Well, that and a scumbag husband who couldn’t keep it in his pants.
But, as far as those who use the site, you reap what you sew, cheaters never prosper, pick out a platitude. I call it karma.
you’re so right peaches!
your husband was so fascinated by your class & intelligence – he would never have cheated on you if it were not for the internet (and other men & women).
Got caught, did you? How much did you lose in the divorce?
Are Paypal transactions recorded? This is how I paid and the credit card files do not include Paypal as far as I can tell.
This release of data is criminal and will lead to more criminal activity. In the form of blackmail and fraud. Two wrongs do not make a right.
There is nothing like privacy while you are saving your all personal stuffs online. Be careful ! do not share personal things online
I can’t believe that after the hack, AM refused to shut the sites down.
What did they have to lose? The brand was built on discretion.
Once they’ve lost that – they have nothing. It’s like they failed their customers twice.