AshleyMadison.com, a site that helps married people cheat and whose slogan is “Life is Short, have an Affair,” recently put up a half million (Canadian) dollar bounty for information leading to the arrest and prosecution of the Impact Team — the name chosen by the hacker(s) who recently leaked data on more than 30 million Ashley Madison users. Here is the first of likely several posts examining individuals who appear to be closely connected to this attack.
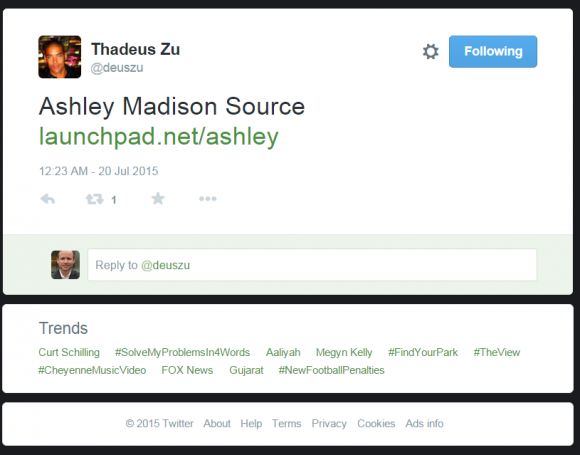 It was just past midnight on July 20, a few hours after I’d published an exclusive story about hackers breaking into AshleyMadison.com. I was getting ready to turn in for the evening when I spotted a re-tweet from a Twitter user named Thadeus Zu (@deuszu) who’d just posted a link to the same cache of data that had been confidentially shared with me by the Impact Team via the contact form on my site just hours earlier: It was a link to the proprietary source code for Ashley Madison’s service.
It was just past midnight on July 20, a few hours after I’d published an exclusive story about hackers breaking into AshleyMadison.com. I was getting ready to turn in for the evening when I spotted a re-tweet from a Twitter user named Thadeus Zu (@deuszu) who’d just posted a link to the same cache of data that had been confidentially shared with me by the Impact Team via the contact form on my site just hours earlier: It was a link to the proprietary source code for Ashley Madison’s service.
Initially, that tweet startled me because I couldn’t find any other sites online that were actually linking to that source code cache. I began looking through his past tweets and noticed some interesting messages, but soon enough other news events took precedence and I forgot about the tweet.
I revisited Zu’s tweet stream again this week after watching a press conference held by the Toronto Police (where Avid Life Media, the parent company of Ashley Madison, is based). The Toronto cops mostly recapped the timeline of known events in the hack, but they did add one new wrinkle: They said Avid Life employees first learned about the breach on July 12 (seven days before my initial story) when they came into work, turned on their computers and saw a threatening message from the Impact Team accompanied by the anthem “Thunderstruck” by Australian rock band AC/DC playing in the background.
After writing up a piece on the bounty offer, I went back and downloaded all five years’ worth of tweets from Thadeus Zu, a massively prolific Twitter user who typically tweets hundreds if not thousands of messages per month. Zu’s early years on Twitter are a catalog of simple hacks — commandeering unsecured routers, wireless cameras and printers — as well as many, many Web site defacements.
On the defacement front, Zu focused heavily on government Web sites in Asia, Europe and the United States, and in several cases even taunted his targets. On Aug. 4, 2012, he tweeted to KPN-CERT, a computer security incident response team in the Netherlands, to alert the group that he’d hacked their site. “Next time, it will be Thunderstruck. #ACDC” Zu wrote.
The day before, he’d compromised the Web site for the Australian Parliament, taunting lawmakers there with the tweet: “Parliament of Australia bit.ly/NPQdsP Oi! Oi! Oi!….T.N.T. Dynamite! Listen to ACDC here.”
I began to get very curious about whether there were any signs on or before July 19, 2015 that Zu was tweeting about ACDC in relation to the Ashley Madison hack. Sure enough: At 9:40 a.m., July 19, 2015 — nearly 12 hours before I would first be contacted by the Impact Team — we can see Zu is feverishly tweeting to several people about setting up “replication servers” to “get the show started.” Can you spot what’s interesting in the tabs on his browser in the screenshot he tweeted that morning?
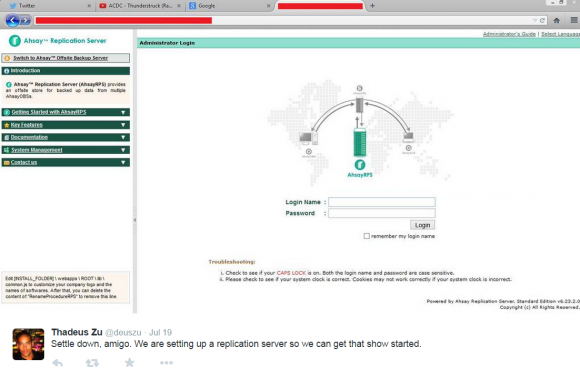
Twitter user ThadeusZu tweets about setting up replication servers. Did you spot the Youtube video he’s playing when he took this screenshot?
Ten points if you noticed the Youtube.com tab showing that he’s listening to AC/DC’s “Thunderstruck.”
A week ago, the news media pounced on the Ashley Madison story once again, roughly 24 hours after the hackers made good on their threat to release the Ashley Madison user database. I went back and examined Zu’s tweet stream around that time and found he beat Wired.com, ArsTechnica.com and every other news media outlet by more than 24 hours with the Aug. 17 tweet, “Times up,” which linked to the Impact Team’s now infamous post listing the sites where anyone could download the stolen Ashley Madison user database.
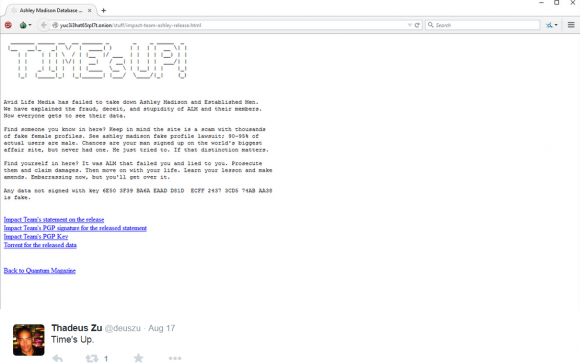
ThadeusZu tweeted about the downloadable Ashley Madison data more than 24 hours before news outlets picked up on the cache.
WHO IS THADEUS ZU?
As with the social networking profiles of others who’ve been tied to high-profile cybercrimes, Zu’s online utterings appear to be filled with kernels of truth surrounded by complete malarkey– thus making it challenging to separate fact from fiction. Hence, all of this could be just one big joke by Zu and his buddies. In any case, here are a few key observations about the who, what and where of Thadeus Zu based on information he’s provided (again, take that for what it’s worth).
Zu’s Facebook profile wants visitors to think he lives in Hawaii; indeed, the time zone set on several of his social media accounts is the same as Hawaii. There are a few third-party Facebook accounts of people demonstrably living in Hawaii who tag him in their personal photos of events on Hawaii (see this cached photo, for example), but for the most part Zu’s Facebook account consists of pictures taken from stock image collections and do not appear to be personal photos of any kind.
A few tweets from Zu — if truthful and not simply premeditated misdirection — indicate that he lived in Canada for at least a year, although it’s unclear when this visit occurred.
 Zu’s various Twitter and Facebook pictures all feature hulking, athletic, and apparently black male models (e.g. he’s appropriated two profile photos of male model Rob Evans). But Zu’s real-life identity remains murky at best. The lone exception I found was an image that appears to be a genuine group photo taken of a Facebook user tagged as Thadeus Zu, along with an unnamed man posing in front of a tattoo store with popular Australian (and very inked) model/nightclub DJ Ruby Rose.
Zu’s various Twitter and Facebook pictures all feature hulking, athletic, and apparently black male models (e.g. he’s appropriated two profile photos of male model Rob Evans). But Zu’s real-life identity remains murky at best. The lone exception I found was an image that appears to be a genuine group photo taken of a Facebook user tagged as Thadeus Zu, along with an unnamed man posing in front of a tattoo store with popular Australian (and very inked) model/nightclub DJ Ruby Rose.
That photo is no longer listed in Rose’s Facebook profile, but a cached version of it is available here. Rose’s tour schedule indicates that she was in New York City when that photo was taken, or at least posted, on Feb. 6, 2014. Zu is tagged in another Ruby Rose Facebook post five days later on Valentine’s Day. Update, 2:56 p.m.: As several readers have pointed out, the two people beside Rose in that cached photo appear to be Franz Dremah and Kick Gurry, co-stars in the movie Edge of Tomorrow).
Other clues in his tweet stream and social media accounts put Zu in Australia. Zu has a Twitter account under the Twitter nick @ThadeusZu, which has a whopping 11 tweets, but seems rather to have been used as a news feed. In that account Zu is following some 35 Twitter accounts, and the majority of them are various Australian news organizations. That account also is following several Australian lawmakers that govern states in south Australia.
Then again, Twitter auto-suggests popular accounts for new users to follow, and usually does so in part based on the Internet address of the user. As such, @ThadeusZu may have only been using an Australian Web proxy or a Tor node in Australia when he set up that account (several of his self-published screen shots indicate that he regularly uses Tor to obfuscate his Internet address).
Even so, many of Zu’s tweets going back several years place him in Australia as well, although this may also be intentional misdirection. He continuously references his “Oz girl,” (“Oz” is another word for Australia) uses the greeting “cheers” quite a bit, and even talks about people visiting him in Oz.
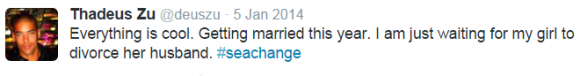
Interestingly, for someone apparently so caught up in exposing hypocrisy and so close to the Ashley Madison hack, Zu appears to have himself courted a married woman — at least according to his own tweets. On January 5, 2014, Zu tweeted:
“Everything is cool. Getting married this year. I am just waiting for my girl to divorce her husband. #seachange
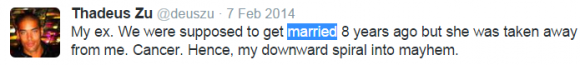
A month later, on Feb. 7, 2014, Zu offered this tidbit of info:
“My ex. We were supposed to get married 8 years ago but she was taken away from me. Cancer. Hence, my downward spiral into mayhem.”
To say that Zu tweets to others is a bit of a misstatement. I have never seen anyone tweet the way Zu does; He sends hundreds of tweets each day, and while most of them appear to be directed at nobody, it does seem that they are in response to (if not in “reply” to) tweets that others have sent him or made about his work. Consequently, his tweet stream appears to the casual observer to be nothing more than an endless soliloquy.
But there may something else going on here. It is possible that Zu’s approach to tweeting — that is, responding to or addressing other Twitter users without invoking the intended recipient’s Twitter handle — is something of a security precaution. After all, he had to know and even expect that security researchers would try to reconstruct his conversations after the fact. But this is far more difficult to do when the Twitter user in question never actually participates in threaded conversations. People who engage in this way of tweeting also do not readily reveal the Twitter identities of the people with whom they chat most.
Thadeus Zu — whoever and wherever he is in real life — may not have been directly involved in the Ashley Madison hack; he claims in several tweets that he was not part of the hack, but then in countless tweets he uses the royal “We” when discussing the actions and motivations of the Impact Team. I attempted to engage Zu in private conversations without success; he has yet to respond to my invitations.
It is possible that Zu is instead a white hat security researcher or confidential informant who has infiltrated the Impact Team and is merely riding on their coattails or acting as their mouthpiece. But one thing is clear: If Zu wasn’t involved in the hack, he almost certainly knows who was.
KrebsOnSecurity is grateful to several researchers, including Nick Weaver, for their assistance and time spent indexing, mining and making sense of tweets and social media accounts mentioned in this post. Others who helped have asked to remain anonymous. Weaver has published some additional thoughts on this post over at Medium.




Really interesting work. Did you try to reach out to Thadeus Zu for comment? If so, that would be good to add to the post.
Yes, I did. Thanks for the reminder. I’ll do that now.
Brian,
Old friend here applauding your work as usually. I have a analytic database I think you would be very interested in viewing regarding the the Twitter handle investigation yours running.
Drop me a line or send me yours. The source is not “public” per se. But its rich with content.
In case your interested check out the Keyhole analytics offering. There is of course my engine we can trace the historical trends of this guy over the past 4 years. Im willing to share it but want to pass to you directly first.
I, for one, support the use of heavy metal in future high profile attacks. While I would argue that the Bon Scott years were perhaps the most interesting from AC/DC, it is hard to claim that their late 1980s material did not have its charms.
you, sir. are a genius
I couldn’t agree more. Power to the metal.
interesting to note that his august 4 2012 reference to thunderstruck is just a week or two after news broke about thunderstruck being played on computers in iranian nuclear enrichment facilities.
not that i think he would be connected to that in any way, but perhaps he was impressed by that and adopted the idea of it.
This person is either a poser, or just another dumb criminal — either way, this is why you do not brag about your accomplishments. If you are lucky enough to accepted in the underground, you keep it quiet, or people will uncover you.
Bravo. I would expect someone who commits such hacks and uses Tor to distribute them to use a less public medium than Twitter for communication.
Obvious and no doubt implied, but I don’t think you explicitly said that AC/DC is Australian. Guy sure is trying hard to place himself Down Under.
Good catch, Jeff. I will update the story with that reference. Thank you!
there’s allot of references to the ocean in his twits. if i were a gambling man, and I’m not, it appears he does most of if not all of his ‘dirty deeds’ from a sea faring vessel.
did you see what i did there! ¯\_(ツ)_/¯
the most interesting man in the world
but if i did gamble, I’d own the universe.
i already own the interwebs!
Figured. Ocean’s an unforgiving place for those sorts of actions.
He likes his INMARSAT, too – you notice that?
Very interesting autopsy of a case and very informative. Thanks.
This is even better than a scripted novel!
I recall a piece of malware that hit the Iranians a few years back that play thunderstruck.
http://www.cnet.com/news/thunderstruck-a-tale-of-malware-acdc-and-irans-nukes/#!
I wonder if mikko ever figured out who wrote it?
@Brian: It would be way cool if you’re able to claim the bounty.
Better investigating than Mr. Acfee of IBT
Hey Brian Krebs, the other person in the cached Facebook photo with Ruby Rose (other than the black man) on the right is Australian musician Bernard Fanning – so I’m guessing you think Thadeus is on the left.
There is no chance that is Bernard Fanning mate. Soz.
The guy on the right is actor Kick Gurry.
I’m pretty certain the guy on the left is a musician or lesser-known actor. I know I’ve seen him in something, just can’t yet place what.
“uses the greeting “cheers” quite a bit”
We say this in America, too.
cheers,
Man, that was one of the most fascinating stories I’ve read in a while. Not just for the conclusions, but the methodical breadcrumb tracking. Like an Agatha Christie novel crossed with a William Gibson short story, but real. I especially appreciate that you stick to facts without pretending conjecture is fact and offer possible alternate explanations. Thank you for existing and giving me hope for the future of Journalism. You’re a national treasure.
Just to add some random detail to the above post:
The Facebook photo of him tagged in Hawaii is from Steve Aoki. Aoki (pictured holding the child) is a Grammy nominated musician and DJ who travels the world playing to many thousands of people at raves and festivals in clubs and stadiums.
Note the Facebook posting has 17,000+ likes.
Hey Brian, you should look at the times of the users tweets and graph them with a scatter plot. You should be able to see if the user did indeed go to Canada some time in the life of their Twitter account by the shift in their sleeping patterns. I’ll have a go at it if I can find an easy way to download their tweets in bulk, Twitter has messed up their API requirements since I last saw them.
Yeah, I’m not having much luck finding easy tooling to delete the 100,000 tweets the dude has made. The API seems to cap out at 300, which means screen scaping the rest? If someone knows how to do that faster I’d definitely like to have a go at plotting out the times. Given there’s screenshots in there of him having a go at Australian government sites it seems fairly likely thats where he is based, rather than the US.
To *download* them rather.
Yep. Twitter makes it tough to do that analysis. That’s why I had to manually download all of his tweets by month and save the HTML, then go back and search them for interesting stuff.
Working on it, heavily rate limited so the scrape will take a few hours.
Good investigative article, to bad that a lot of it may be speculation. Then again Krebs could end up with the $500k
I’m going to go with Thadeus definitely being Australian or a New Zealander after looking through his tweets. His vernacular is definitely from those countries – he uses the term “chur chur” in one of his tweets which is New Zealand slang for thank you and I’ve never heard it outside of that region.
Hmm, what would be the twitter password of somebody who loves ACDC?
I sure hope he uses 2FA.
But, if he uses 2FA, an interesting thing would be to find out the details of the associated SMS enabled phone number.
nb: UK land phones can receive SMS messages, and various VoIP services can too, it isn’t strictly limited to “Cellular” providers.
If he doesn’t use 2FA, then I’d expect him to not have any direct messages — under the assumption that someone would eventually compromise the account and be able to read them — which would be compatible w/ @Brian’s note about seeming to omit the addressee in his conversations.
Some excellent sleuth work here. I am not convinced the person who holds the Twitter account did the hacking, but it’s pretty clear from the analysis that the person knows who did.
What struck me immediately when seeing his nickname was that “Thadeuszu” is very similar to the Polish word “Tadeuszu” which is a vocative case of the Polish name “Tadeusz”(Thaddaeus – one of the 12 apostles). Funny thing is that adding “h” after “T” completely changes the English pronunciation of the word (“Tadeus” pronunciation is very similar to Polish “Tadeusz” – but adding the “h” as in “Thadeus”changes the English pronunciation a lot – at least when my Mac pronounces it :-).
Does the above matter – is he playing games with hiding/hinting ? Or this might be just coincidence …
And just like that, ThadeusZu has deleted all tweets that remotely reference the attack. I hope you guys had the sense to keep screenshots for law enforcement…
As noted in the story, I have a comprehensive index of his tweets. I.e., all of them going back to when he joined twitter in Nov. 2010.
check this out
https://twitter.com/Doutzen
He followed her on twitter. Her last comment july 19 ( the day the news broke) is interesting
I just checked: His tweets are still there. It’s just Twitter limits how far back you can go on the main page of a profile. You can still find the old tweets if you search by date range. I find searching by months works best.
https://twitter.com/search?q=from%3Adeuszu%20since%3A2015-03-02%20until%3A2015-03-31&src=typd&lang=en
You are correct Brian Kreb; search by month currently works. Sorry for providing you incorrect data.
Deleting a tweet hides it from public view, it doesn’t delete it for this very reason. No company would actually have a literal “delete” button if they have any sense of self preservation.
Relevant since AshleyMadison was apparently targeted for their ‘delete’ account racketeering.
Except maybe if you do have a “Delete” button, especially one that costs, say, $19, you should probably actually do what you say and delete the records.
Great detective work Brian! Where’s there’s smoke, there’s often fire…. this trail should be followed up on by the FBI/NSA, there’s undoubtedly some sort of link here…
Brian, as always – a GREAT READ!! Thanks for making my morning interesting. See you up in Vancouver the end of September!
Coop
As always your investigative work is exemplary. You are on the hunt matching the correct leads with the correct associations, but what next? The AMSaga (my coined phrase for this situation) has reached critical mass but to what resolve?
The unchecked hand of trust the internet users have placed in Internet Sites should have bandages and 3rd degree burn treatment by now but I feel this is far from the case. Recently I took it upon myself to review the actual dump and found it appalling that the data elements contained within the data-dump were so categorized and content rich.
An indication that could illuminate 2 serious issues. One being that as the infamous “Impact Team”statement regarding the “lack of security and open doors” which they mention in the manifesto could be true. The other being there are other levels of intrusions “3rd party affiliates” that were used to facilitate such a powerstorm of exploitation.
Hopefully this paves the way for a new wave of Social Application Companies taking security a bit more serious. Myself a owner of the Counter Social Intelligence Agency “bits&digits”, find it so hard to grasp how these attacks are successful. By successful I mean the evident lack of basic security best practices when dealing with Personal Information.
We can thank one standard PCI in this case for not allowing Payment Card information to accompany these data elements but more concerning is the lack of encryption use in these environments. Canada and California (SB1386) have clear rules on encrypting data elements with specific certifiable algorithms which obviously were not leveraged in this case.
I digress, thank you Brian for a very informative expose on the incident. The BD team is following suit in developing a solution to protect the plenty of fish ==no pun intended”) that still play in this market. As I can only imagine this is the first of many as we saw in the HealthCare market last year.
The matter of fact is sys and network admins are lazy – and often unexperienced when it comes to the world of network security and best practises. Companies still do not place a great deal of importance in network security – even at the most basic of levels.
The amount of incompetance I’ve seen at so many different companies that I’ve worked at is beyond astounding. It’s common place. Companies don’t want to spend the money and they don’t want to train their employees to ‘fix’ these issues often until it’s too late. Good security and properly experienced and trained individuals costs a decent chunk of change. Money that could say, be put into marketing their products. A lot of companies still seem to view IT as an afterthought, even if they’re a tech sector company. It doesn’t generate income (so they think) and appears on paper as nothing more than a gaping cost centre, so a lot of IT departments operate on just keeping the lights on budgets.
While I am by no means a security expert, my time spent in a Security Operations Centre for a mobile phone manufacturer known for their security infrastructure was a real eye opener on just how lazy people really are when it comes to security – even within that particular company – and large chunks of their security team were ex-Secret Service/ex-military.
How would encryption help if credentials were compromised? They were in the database. (Hansel voice)
I had been following Thadeus in twitter. He sounded like a crazy person. Tweeting all the time. It got old real quick.
It looks like Ruby Rose has been deleting some tweets and photos. Even the archived items mentioned in the article are no longer available.
So they’re both deleting things from the internet to remain anonymous or trying not to incriminate themselves…the irony in that is astounding.
Cry havoc and let slip the dogs of war.
Fascinating.
Great work. Hopefully the authorities asked you to share this information with them.
Omg omg omg …
Cheers is a really really common goodbye in the toronto area as well. Usually downtown to Mississauga.
Is it possible the married girl he is waiting for is Noels wife ?