The FBI today warned about a significant spike in victims and dollar losses stemming from an increasingly common scam in which crooks spoof communications from executives at the victim firm in a bid to initiate unauthorized international wire transfers. According to the FBI, thieves stole nearly $750 million in such scams from more than 7,000 victim companies in the U.S. between October 2013 and August 2015.
In January 2015, the FBI released stats showing that between Oct. 1, 2013 and Dec. 1, 2014, some 1,198 companies lost a total of $179 million in so-called business e-mail compromise (BEC) scams, also known as “CEO fraud.” The latest figures show a marked 270 percent increase in identified victims and exposed losses. Taking into account international victims, the losses from BEC scams total more than $1.2 billion, the FBI said.
“The scam has been reported in all 50 states and in 79 countries,” the FBI’s alert notes. “Fraudulent transfers have been reported going to 72 countries; however, the majority of the transfers are going to Asian banks located within China and Hong Kong.”
CEO fraud usually begins with the thieves either phishing an executive and gaining access to that individual’s inbox, or emailing employees from a look-alike domain name that is one or two letters off from the target company’s true domain name. For example, if the target company’s domain was “example.com” the thieves might register “examp1e.com” (substituting the letter “L” for the numeral 1) or “example.co,” and send messages from that domain.
Unlike traditional phishing scams, spoofed emails used in CEO fraud schemes are unlikely to set off spam traps, because these are targeted phishing scams that are not mass e-mailed. Also, the crooks behind them take the time to understand the target organization’s relationships, activities, interests and travel and/or purchasing plans.
They do this by scraping employee email addresses and other information from the target’s Web site to help make the missives more convincing. In the case where executives or employees have their inboxes compromised by the thieves, the crooks will scour the victim’s email correspondence for certain words that might reveal whether the company routinely deals with wire transfers — searching for messages with key words like “invoice,” “deposit” and “president.”
On the surface, business email compromise scams may seem unsophisticated relative to moneymaking schemes that involve complex malicious software, such as Dyre and ZeuS. But in many ways, the BEC attack is more versatile and adept at sidestepping basic security strategies used by banks and their customers to minimize risks associated with account takeovers. In traditional phishing scams, the attackers interact with the victim’s bank directly, but in the BEC scam the crooks trick the victim into doing that for them.
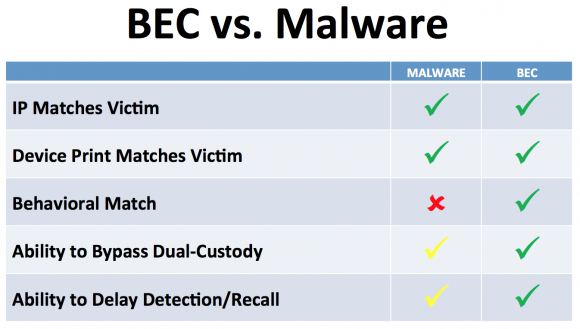
Business Email Compromise (BEC) scams are more versatile and adaptive than more traditional malware-based scams.
In these cases, the fraudsters will forge the sender’s email address displayed to the recipient, so that the email appears to be coming from example.com. In all cases, however, the “reply-to” address is the spoofed domain (e.g. examp1e.com), ensuring that any replies are sent to the fraudster.
The FBI’s numbers would seem to indicate that the average loss per victim is around $100,000. That may be so, but some of the BEC swindles I’ve written about thus far have involved much higher amounts. Earlier this month, tech firm Ubiquiti Networks disclosed in a quarterly financial report that it suffered a whopping $46.7 million hit because of a BEC scam.
In February, con artists made off with $17.2 million from one of Omaha, Nebraska’s oldest companies — The Scoular Co., an employee-owned commodities trader. According to Omaha.com, an executive with the 800-employee company wired the money in installments last summer to a bank in China after receiving emails ordering him to do so.
In March 2015, I posted the story Spoofing the Boss Turns Thieves a Tidy Profit, which recounted the nightmarish experience of an Ohio manufacturing firm that came within a whisker of losing $315,000 after an employee received an email she thought was from her boss asking her to wire the money to China to pay for some raw materials.
The FBI urges businesses to adopt two-step or two-factor authentication for email, where available, and/or to establish other communication channels — such as telephone calls — to verify significant transactions. Businesses are also advised to exercise restraint when publishing information about employee activities on their Web sites or through social media, as attackers perpetrating these schemes often will try to discover information about when executives at the targeted organization will be traveling or otherwise out of the office.
Consumers are not immune from these types of scams. According to a related advisory posted the FBI today, in the three months between April 1, 2015 and June 30, 2015, the agency received 21 complaints from consumers who suffered losses of nearly $700,000 after having their inboxes hijacked or spoofed by thieves. The FBI said it identified approximately $14 million in attempted losses associated with open FBI investigations into such crimes against consumers.





I work for a somewhat small IT firm amd we saw 3 attempts like this but only one of our clients lost money. After examining the emails it was clear it wasn’t legit emails simce the reply email was to an AOL account. Had to tell the client the only way to stop it is education and SOPs.
Trust me, the sheeple cannot be educated.
Sheep can be educated. It’s the thick and hard-headed people that don’t have a cry of hope.
incorrect
advertisers and media have know for years that public opinion can be manipulated by propaganda presented as news.
Indeed just look at (insert cable news channel here).
Manipulation != Education
Manipulation generally means trying to get someone to do what the manipulator wants, and typically something which is NOT in the best interest of those being manipulated.
Education, OTOH, when done well, encourages people to think for themselves, and gives them techniques that allow them to see through the common logical fallacies used by the manipulators, which typically makes educated individuals far less susceptible to manipulation.
You validated my comment, social media and advertisong ARE able to sway the thoughts of ignorant hard headed people who accept things at face value and dont think for themselves.
Wouldn’t it help to authenticate email?? Here’s a website that can show if your email can be trusted. http://www.humanexploit.com Are you a human exploit waiting to happen?
Apparently the scammers are more sophisticated than their targets.
If your company facilitates large wire transfers without any kind of personal contact (NOT ELECTRONIC) then it’s run by morons…
As part of the education of executives and money managers, they should learn to set up a code word/phrase when the executive travels (different each time). Then when a request for transfer is emailed, the first response will be “what’s the code word/phrase? Maybe even use a one time pad in the case of multiple requests per trip.
While not a silver bullet, it’s worth noting that if a company fully authenticates its email using SPF, DKIM, and DMARC, spoofed domain phishing attacks will be blocked. That doesn’t stop the cousin domain attacks or display name abuse, but it significantly degrades the virulence of spear phishing that can lead to BEC attacks.
Some of the attacks come in from legitimate domains that are simply one character off from the actual domain. The only way to block email from them through SPF, etc. is to only allow a whitelist of domains to send mail to you, which is completely untenable.
The remainder, and sadly most that I’ve seen, are simply gmail, aol, etc. accounts and the individuals in question simply didn’t pay any attention whatsoever to the from: address. Most include grammatical errors which would have raised my suspicions, but apparently I see more 419 emails than most people.
Gilb’s Law:
Any system which depends on human reliability is unreliable.
Any company that falls for this deserves to lose money. If the education system is not teaching how to fix then go to a different school.
In the Malware vs. BEC chart, not clear why ‘Behavioral Match’ is green in the chart under BEC – wouldn’t the destination and/or amount in a scam be outside the customer’s normal behavior, and thus may be caught?
No, because it is the customer who is requesting the wire, and ultimately the bank won’t refuse the wire if it is authorized. From the story: “In traditional phishing scams, the attackers interact with the victim’s bank directly, but in the BEC scam the crooks trick the victim into doing that for them.”
But it can still be strange behavior for the customer, wiring a large amount of money to an unknown beneficiary.
Authorizing a transfer, doesn’t mean by default that this transfer can be trusted.
nice post I have a lot of scam emails posted at http://georgegotscamed.blogspot.com/
let me know what you think
I think you wasted 10 euros or so by misspelling ‘scammed’?
Driving while blind on the information super highway.
((0))_((0))
I’ve seen a number of these attacks against my company. Are there any good ways to report these types of scams to someone who can track down the account numbers or domain registrations? I’d like to find a way to take part in stopping these attackers.
The Nigerian scammers are doing this now. They deal in volume though, with personal e-mails, as opposed to CEO/Business e-mails.
Unlike frauds where outsiders using computer viruses or basic forgeries of checks are used, the banks do not replace these funds, since you are the scam victim and not the bank.
Education
Security check words/phrases for wire transfers
Blocking and reporting abused domains to domain hosts and IC3.
We (50 employee international company) have been targeted by the “CEO Fraud” unsuccessfully at least 4 times. A carefully crafted email appearing to originate with our CEO, through our CFO to our Controller directing wire transfers.
A number of tells become apparent but the criminals are clever. They’re creating domains with minimal investment that reverse an i & e, drop a letter, or like-character substitution. They generate email from this disguised puppet CFO email account and I hope we remain vigilant. It’s not always the case – even quarantined suspicious email is “released” just in case it really came from the CFO and CEO.
Folks tend to become immune to the warnings of IT so raise the alarm sparingly.
Reporting? Authorities don’t seem to care so much if a crime and money lost didn’t take place. I will report it as an IC3 complaint nonetheless as time permits. http://www.ic3.gov/
I also notify domain hosts and registrars via web form or abuse email addresses – I typically get a solid response that the domain has been shut down.
No real method to stop it but some satisfaction of addressing it. … Maybe they will go elsewhere.
…get your game face on.
hi BrianKrebs , i have long time research Nigerian scammers teams working under BEC they target malware and ATP by exploit hunter CEO and small company , how to catch it’s if FBI can’t fly to Nigerian? or cop in Nigerian will help we catch it’s?they theft money easy by stupid small company , you can help me reports to FBI or where for catch all it’s? when i have full info about it’s!
Todays enduser will never take online threats serious because our goverment and banking system return most if not all loses. We have become the piggy bank of the world for every want to be hacker, who has all the time he needs to master his craft thousands of miles away.
We need to remove this incentive so people will wake up and protect themselves.