Before purchasing an “Internet of things” (IoT) device — a thermostat, camera or appliance made to be remotely accessed and/or controlled over the Internet — consider whether you can realistically care for and feed the security needs of yet another IoT thing. After all, there is a good chance your newly adopted IoT puppy will be:
-chewing holes in your network defenses;
-gnawing open new critical security weaknesses;
-bred by a vendor that seldom and belatedly patches;
-tough to wrangle down and patch
In April 2014, researchers at Cisco alerted HVAC vendor Trane about three separate critical vulnerabilities in their ComfortLink II line of Internet-connected thermostats. These thermostats feature large color LCD screens and a Busybox-based computer that connects directly to your wireless network, allowing the device to display not just the temperature in your home but also personal photo collections, the local weather forecast, and live weather radar maps, among other things.
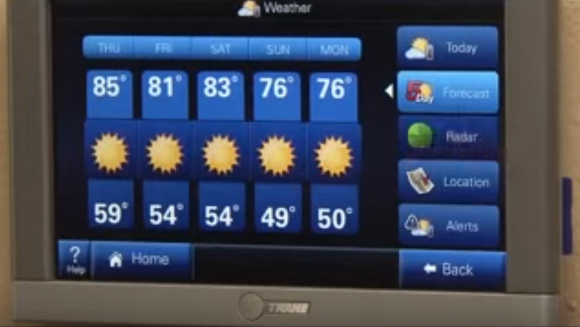
Trane ComfortLink II thermostat.
Cisco researchers found that the ComfortLink devices allow attackers to gain remote access and also use these devices as a jumping off point to access the rest of a user’s network. Trane has not yet responded to requests for comment.
One big problem is that the ComfortLink thermostats come with credentials that have hardcoded passwords, Cisco found. By default, the accounts can be used to remotely log in to the system over “SSH,” an encrypted communications tunnel that many users allow through their firewall.
The two other bugs Cisco reported to Trane would allow attackers to install their own malicious software on vulnerable Trane devices, and use those systems to maintain a persistent presence on the victim’s local network.
On January 26, 2016, Trane patched the more serious of the flaws (the hardcoded credentials). According to Cisco, Trane patched the other two bugs part of a standard update released back in May 2015, but apparently without providing customers any indication that the update was critical to their protection efforts.
What does this mean for the average user?
“Compromising IoT devices allow unfettered access though the network to any other devices on the network,” said Craig Williams, security outreach manager at Cisco. “To make matters worse almost no one has access to their thermostat at an [operating system] layer to notice that it has been compromised. No one wakes up and thinks, ‘Hey, it’s time to update my thermostats firmware.’ Typically once someone compromises these devices they will stay compromised until replaced. Basically it gives an attacker a perfect foothold to move laterally though a network.”
Hidden accounts and insecure defaults are not unusual for IoT devices. What’s more, patching vulnerable devices can be complicated, if not impossible, for the average user or for those who are not technically savvy. Trane’s instructions for applying the latest update are here.
“For organizations that maintain large amounts of IoT devices on their network, there may not be a way to update a device that scales, creating a nightmare scenario,” Williams wrote in an email explaining the research. “I suspect as we start seeing more IoT devices that require security updates this is going to become a common problem as the lifetime of IoT devices greatly exceed what would be thought of as the typical software lifetime (2 years vs 10 years).”
If these IoT vulnerabilities sound like something straight out of a Hollywood hacker movie script, that’s not far from the truth. In the first season of the outstanding television series Mr. Robot, the main character [SPOILER ALERT] plots to destroy data on backup tapes stored at an Iron Mountain facility by exploiting a vulnerability in an HVAC system to raise the ambient temperature at the targeted facility.
Cisco’s writeup on its findings is here; it includes a link to a new Metasploit module the researchers developed to help system administrators find and secure exploitable systems on a network. It also can be used by bad guys to exploit vulnerable systems, so if you use one of these ComfortLink systems, consider updating soon before this turns into a Trane wreck (sorry, couldn’t help it).




The risk of IoT devices (sensors) is growing daily. While we all speak to the importance of security and privacy by design, we equally need to look at the long-term and lifecycle impact of the device. How is it supported post warranty” how is ownership transferred and who owns the data? Combined this is what the IoT Trustworthy working group has called ‘sustainability” More details on the emerging code of conduct is posted at https://otalliance.org/IoT.
Join us on MArch 2 at RSA for our session, “Diffusing the IoT Time Bomb.
Shouldn’t that be “Defusing the IoT Time Bomb”?
I’m thinking unintentional irony or Freudian slip, because IOT really *does* diffuse the threat from a few places to everywhere!
Have you covered router options, such as AP isolation and guest access? It would seem prudent to isolate any IoT devices from your network. I would be interested in knowing what is available in the consumer market (at reasonable prices) that can effectively keep these devices isolated from home computers.
Barry,
I was wondering about that myself. That would help protect your home network from rogue IoT devices in your house, but still leaves the problem of a malware infested device being used to launch DDOS attacks, against devices not on your network.
It seems like it might be prudent to set up a second router configured for Access Point Isolation just for these devices. That way they can’t access anything else. They would need to be manually set for channels which are far from each other in frequency, since otherwise they are likely to try to sit on the same channel. Since these devices are not so expensive, it seems like a financially good way to go. My TP router which was not expensive does have the AP isolation feature. It seems like it would scale to larger networks too, with some thought.
As with everything security related, this becomes a managed-risk scenario. Some home-grade routers have the option to place devices into a DMZ outside of your firewall by either IP address or MAC address.
Your consumer-grade all-in-one router may offer some isolation through a “DMZ” setting, but it may not be as robust as an small business router/firewall configured for an isolated VLAN to host just IoT devices. These sorts of setups can be had for $0 with a pfSense firewall and an old desktop or a Ubiquiti EdgeRouter Lite for ~$95.
Not that I feel any more safe being protected by a Ubiquiti device….
In my experience, the biggest issue with this sort of setup is that, in most cases, it defeats part of the purpose of the device – home integration. For devices that ONLY need internet access, and nothing more, this would be a great setup, but when you think about things like Smart Lights, Media streaming devices, etc, it becomes much harder, because part of the convenience is being able to use your phone / tablet / computer at home to access these devices.
I was going to do this for my AppleTVs, for QoS not security, but it became a pain to have to jump from one SSID to another any time I wanted to control or stream with the device. And these devices are going to become more and more integrated with other devices, making segmentation harder.
@CJD: This. The more you lock down a “Smart” device, the less useful it’s “Smart” features become. (Apart from the fact that applying security is only feasible for more technically/security minded people.)
Why should I pay for a snazzy thermostat that will tell show me pictures (or turn on lights or fans, or start my car for me, or etc) if I’m just going to turn around and lock it down tightly so it can’t do any of that? Why not install a cheap, stupid & very secure bi-metal switch?
Agreed. It wouldn’t make much sense to isolate everything this way, but for only-needs-internet devices that can be controlled from a cloud platform, it works pretty well.
For other devices such as smart TVs and lights, they can be left on your primary secured network and allowed in/out by a good stateful firewall and carefully written rules.
Your mileage may vary based on how much technical experience you have, what your firewall is capable of, and how many hours you want to spend cursing in order to get it to work.
And don’t forget the common factor. How to teach grandma grandpa how to safely operate this same device. Or the police, or any ordinary visitors. What about the perv in WiFi range now getting the pictures of your kids, or your private information, that the system could have because you allowed it onto your device for controls.
Actually, I’m surprised there is no fisheye camera, open to the iot devices. But, I have read of impedience devices in iot lights, to detect when something comes in range. Almost as good. Is anyone there awake to possibilities.
If you’re going to allow IoT gizmos on a network, the minimum one should is to isolate those devices as much as possible. Honestly, as long as the manufacturers are so deeply clueless about security fundamentals, I can’t think of a good reason to allow them on a network I cared about at all. We keep hearing about one stupid gaff after another. It’s inexcusable, but there it is.
The easiest to implement and audit is this:
1. Use three routers.
2. The first router is your DSL/Cable modem connected to the outside. WiFi should be disabled.
3. The second router is your home/secure router. Use WiFi and don’t connect any IoT devices
4. The third router is your IoT router. Connect all IoT devices. Enable WiFi, but only connect to it when you must.
This setup segregates your devices and protects from Ethernet-based vulnerabilities like ARP-Spoofing. If you have an infected IoT device on the IoT router, it will not be able to see any Ethernet traffic on your secure network, or any TCP/IP, UDP, or ICMP traffic between the secure router and the router that connects to the internet. NAT at each router stops bad devices from looking into peer networks.
I’m debating what to do with devices like Sonos or AppleTV that may be robust, and that I would like to connect to frequently.
Routers are cheap these days. You could do the same with a feature-rich device and vLANS, but this way is easier and much easier to be certain.
yep was just gonna say use three routers. Steve Gibson had an interesting podcast on security now last week called “three dumb routers” regarding the only way for real network isolation.
Ever tried setting up multiple routers on Verizon FiOS? Good luck with that.
You can turn the FiOS router into a bridge:
http://www.hanselman.com/blog/SimplifyingYourNetworkWithABridgeMakingAnFIOsActionTecMI424WRANetworkBridge.aspx
I have a Trane thermostat, but not this model, that has the ability to connect to the internet via wifi that is currently NOT connected and will remain not connected for precisely these reasons.
My brother also has a Trane thermostat on his new HVAC system and it might be this model. I will be contacting him to see if he has this model and help him get it updated if he does.
Thanks for the heads-up on this!
Sure glad I don’t have an IoT home security system.
Interesting article Krebs.
By the way, almost half way done in your book (the Audible version). Great stuff!
Thanks, DS! Hope you like the rest of it!
He will love the rest of the book. It was recommended to me by a professor where I am getting my M.S. in Economic Crime Management and I couldn’t put it down once I started. The things you wrote about vs. what I had seen in my line of work was stunning.
Insecure Internet-connected thermostats may be the first of many IOT devices being brought into the connected home, so the problems of lack of management in the form of updates and fixes from the manufacturer will not just be confined to Trane or other HVAC vendors, it will become much, much bigger. Internet connected refrigerators that email you with your shopping list, home cameras that alert you to activity, alarm systems hooked up to your Internet rather than the POTs line you got rid of… these are just the tip of the iceberg of what is to come!
While a separate untrusted or semi-trusted wireless AP and SSID connected to a firewalled DMZ off of your home router may be a stop-gap measure, (provided that ports and destination IPs can be locked down for device communications at the DMZ firewall), what happens when the average home has 5 or 10 IOT devices, all communicating in different ways to different destination IPs? Swiss Cheese not only for lunch but also for the Firewall! Isolation BETWEEN IOT devices will become necessary to stop one taking out another, and that’s putting aside the whole DOS attack on your home network and that of your neighbors.
While prudence may help to reduce risk, most homeowners don’t have the wherewithal or knowledge to setup a robust security infrastructure and will simply connect these devices to their internal (secure) WiFi. Most homes don’t even have a Guest WiFi SSID, and many are still wide open.
Cisco estimates that there will be 30 billion IOT devices by 2020 worth an estimated US $3 trillion in business. With that kind of expansion predicted, you KNOW that certain criminal elements are licking their lips in anticipation at a target-rich environment, and are busy developing exploits already.
Given a largely unaware and clueless public, maybe the legal / contractual onus should be placed on device manufactures to secure, test and make updates remotely to their devices, i.e. to ‘manage’ devices rather than merely manufacture, market, sell and abandon, as seems to be the case with many. As Craig points out above, we need a code of conduct for IOT vendors, if not some form of regulation to ensure that the inter-network doesn’t grind to a complete halt as a result of their lack of diligence.
add this to the things such as toasters and vacuum cleaners that spit out spam and the world of corrpution is complete. Its pretty pitiful when you have to site there with a wireless sniffer to see if the devices you buy are actually doing what they say they will…. Toast, vacuum or otherwise, WITHOUT any additional “bonus” features. =\
I do wired networks for more than one reason. This is one of them.
LOL!!!! Love the puppy analogy. So true!!!! We just adopted a rescue puppy and he’s like the Tasmanian Devil. Chewing everything, doesn’t listen to anything/anybody. Escaped 3 times already and we chase him all over our neighborhood. We are enrolling him at a local K9 school that trains police dogs. He is way out of our ability to try to train him…….
Internet of Things: Just because you can, it doesn’t mean you have to.
…..or even that you should.
I have a Honeywell smart thermostat. The manual specifies it MUST be connected to your “regular” wifi network, not your guest network. And indeed, it does not seem to work when connected to the guest network. I was able to get around this by doing initial setup on my secure wifi, and then moving it to solitary confinement in its own VLAN.
So Honeywell seems to be aware that people might want to run their thermostat on a separate network and to have gone to some effort to prevent that.
Sooooo…..why does Trane make it mandatory to be on the main network, not the guest access? That’s seems unreasonable in my book. If it only needs access out to its “appropriate” connections (whatever those are construed to be), why full network access? Trane needs to provide more information on this requirement, I wouldn’t allow mine to connect. As long as it does what it’s supposed to do, run my HVAC, it doesn’t need to be tattling or allow snooping on any other electronic systems in my household. Be that from all the other devices that aim to connect to my network.
Sorry, I meant Honeywell….
Looking at Honeywell’s FAQ (http://yourhome.honeywell.com/en/faqs/thermostat/7-day/wi-fi-smart-thermostat), it appears that they want to connect in on port 443, a standard port used for secure http. A guest network shouldn’t allow incoming connections, so that’s probably why.
Of course, this begs the question: What if my thermostat wants the same port as my water softener? (Yes, there is an IoT water softener out there: It’s junk, but it’s connected!)
Thanks for the analysis, Doug! I wasn’t sure what to make of that requirement. It’d be really nice if there was a mechanism for local control of the device without talking to their central server… after all I usually only care about the precise temperature of my house while I am in it.
Ugh. IoT devices should NOT be servers!
You know, I’m sorry, but if you can’t remember to lock your own front door and set your own thermostat, at least until the security issues are resolved, you might have a problem.
If it’s exists, somebody is going to exploit it. I can do without IoT as my grand parents did for years and years – if it works, don’t fix it.
Sure, they’re handy gadgets, but ‘Do You REALLY Need This?’. Talk about being lazy!
Probably not a big deal in a home setting. In a corporate environment energy savings can be significant if you can do climate control over the internet. It also can save maintenance staff a trip out to the workplace on the weekend if someone is there or an event is going on and room temperatures need to be adjusted.
Tell that to Target. And stand by for an earful.
Hell Brian,
A few questions for clarification:
1. In the Mr. Robot episode, the main character used a raspberry pi to gain remote access to the thermostat. But this thermostat already allows remote access via the customer or company WiFi network. So it’s really just a matter of checking to see if it’s patched and if it’s not they use the hard coded default passwords?
2. The second attack vector would require a hacker to have physical access to the device if this was going to be their first “foothold” on someone’s network, correct? This would then be the only way to put Malware directly on to the device? (assuming these holes were also not patched)
3. Does the device show up as some type of service account on the WiFi network? Wouldn’t there be a way to lock down this account so that it could only have read access? Why does a thermostat need to send information back to the WiFi network? Maybe that’s not possible, I’m just asking the question. Could home users or companies block incoming network traffic form the thermostat? And why doesn’t the themostat (and other internet of things) just do that as a factory default that can’t send information? (cell phones?)
Hi Brian,
You’re touching on two critical challenges with security that are huge problems for the progress of IoT:
Complexity and Configuration.
Both of those product dimensions open up tremendous security vulnerabilities, and are counter to one of the few trends that I feel must happen to solve the wave of security challenges that are coming, and that is Simplicity.
Progress happens when challenges are either simplified or those challenges must be solved in order to survive. The producers of new technology need to design for simplicity, and that is even more critical for IoT. Rather than push challenges off onto the consumer, the product must come with security that has already been solved. Much easier said than done, but something that must be aspired to. It’s very easy to add feature after feature and then ask the customer to manage those features with complex configurations (that are themselves solved with bad defaults), but we’ve seen where that has put us.
The main problem appears to be that fools and their money are soon parted by the latest flashy gadget that comes along. It seems to be a symptom of affluenza.
I find it mildly amusing that the very people everyone thought would be the market are the nay-sayers! And with good reason.
Even ignoring the little issue of security, the number of incompatible interfaces between these products makes them somewhat lemon-flavoured to begin with. Each manufacturer has gone out and invented a standard that nobody else story’s and which you know they’ll drop after a couple of years, once the first sale revenue has gone.
I think that it is time that we establish a corporation and certification standard so that all of these devices can be rated. Otherwise, the consumer has no clue.
Also, it would be nice to the routers that we use in our homes automatically split the network for untrusted and trusted devices. Two subnets. Untrusted devices can talk to the internet but not get to your trusted devices.
You could then blindly plug in your Blu-ray player, cable box, receiver, and any other IoT device into the untrusted subnet and keep your home computes on the trusted subnet.
Well, many consumer routers have the ability to setup a guest network, just join the devices to the guest network. The problem is that many guest network setups are designed not to have a passkey, which wouldn’t work since then all someone would have to do is drive up and join your unsecured WiFi. But for the ones that give you the option to have a passkey set, then it’s just as secure as your main network… just segmented off into its own network and unable to communicate with the main network.
This is where having the ability to load third party firmware onto the router comes in handy, since guest networks are simply a matter of setting up an additional network… with a third party firmware you could even setup a secured network for your main systems, a secured network for your untrusted IoT devices, then a unsecured WiFi guest network… this is what not locking yourself into a vendor (or, god forbid, an ISP’s vendor) lets you do.
Interesting. We have exactly this model of thermostat, and I have always wondered about the security aspects of the thing. There is an old addage that companies that make hardware oftentimes write crummy software.
The one use case that I can think of which would be useful is if there were a fault in the system, that the thermoststat could notify our service person directly and not depend upon me to read the fault codes and phone them in. Other types of devices (such as some business grade copiers) have this sort of capability, but the ones I have seen use a simple phone line. And in *theory*, this thermostat has this capability, but as best I can tell, they don’t use it.
One final point – with this thermostat, one can register it with Nexia (essentially Ingersoll-Rand’s home automation portal, where I-R is Trane’s parent company – Schlage at one time was another I-R child company, but their products are still compatible). And in theory this allows you to adjust/monitor your thermostat from a smartphone. But the same interface would allow you to unlock your front door if you had an automate-able lock on your front door.
Steve Gibson covered the 3 router solution in a “Y” configuration. It’s a bit long but decent explanation.
Security Now episode 545 on the TWIT.TV
Paul
A much easier method than relying on a VLAN router, and more secure as well! Excellent!
The only reason they didn’t teach this in IT schools was because routers used to be SO expensive. Now that you can get them for 20 bucks or so, it is just easier to build your network as a root to the gateway(router), and separate your networks by their own router. The “Y” network diagram would commonly be all you’d need! – simples!
Just put the IoT devices on one bottom leg of the “Y”. VOILA!
Gibson Research Corporation (GRC) always was a good place to learn a lot about net security, and also test it in REAL time! All for free! They only hawk one product there, and there is no pressure to buy anything!
I’m deploying a Pfsense firewall with multiple network ports so I can run a DMZ or secondary LAN for my IoT devices. Single firewall behind FIOS…
A secure home network will need many of those $20 routers like the 700-series from TP-Link. Several of those routers are supported from http://www.gargoyle-router.com/. I set up separate networks for IoT’s (Lifx lights, control over the cloud using Echo); unimportant tablets, phones, Echo, and FireTV (Fire TV needs to be on the same network as the phone to use the app); the Xbox (game playing only); and one for each computer. There ain’t any file sharing directly between any computers but all can reach the primary router which serves music & video). The main computer uses the VPN service that comes with TinyHardware Firewall (expensive). Nothing inside the network can see that data. The current THF is a TP-Link 7003N running a hardened (closed) version of the Gargoyle. The TP-Link’s are users up-gradable. Nope, am not a rep or otherwise associated with them, I just like modern, highspeed, reliable routers that cost under $20. And, don’t use the normal router SID’s, instead of ‘ASUS166’ use fun stuff like, ‘submissive_woman_wanted’; and ‘get_your_malware_here’.
Yep, that’s the way. Create a separate network for each group of devices you don’t mind talking together. This may mean 2, 3, 4, or more. Luckily, they don’t all talk at the same time…..
Wow, so how does one exploit an ssh vulnerability when every wifi router blocks ssh by default?
>“SSH,” an encrypted communications tunnel that many users allow through their firewall.
Um Since, when?? only security guys, noones grandma does this.
So, inorder to compromise the thermostat, you need access to the home network. But once you have that, who cares about a thermostat?
This sounds like sensationalism simply to attract readers.
You leave me with the impression that you are assuming the device (said thermostat), hasn’t been compromised before it was installed. I’m sure you don’t mean this. We’ve all found many installation discs, hardware, and firmware that was embedded with malware, or malicious intent, well before it left the factory floor.
I really appreciate the insight shared here. Commonly choosing any IoT device requires some homework to be done in context of security.
The internet of things really just becomes another form of trojan. One that has alot more appeal and that is actually what makes it so much more dangerous.
I see no point in the Nest thermostat. The best thermostat ever made is the electronic programmable. The whole idea is to set it to what you want then walk away and forget it. What people seem to be forgetting is that it’s usually when they are constant adjusting the temperature settings that the electric bill goes up. Just set it and leave it alone.
To be honest, I see very little point in any IoT device anyway. It’s all just more stuff to have to worry about. More stuff to raise the overall price of things. More stuff to connect to the network. More stuff to maintain. All for what? Technology was supposed to make life easier and more enjoyable. I see no joy in any of this. Refrigerators that email you when your out of milk become more of a nuisance.
IoT thermostats are used by many utilities to control peak electric load, the price of electricity for every consumer, is based on the system peak. Therefore, controlling residential and commercial electric use via thermostats is a means to reduce peaks and reduce costs is a legitimate use of these devices.
“legitimate”?
Curious word to attach to something that can be used to gain entrance into a business network (thinking Target). There are reasons why so many businesses are getting hacked, breached, and targeted. The intension is certainly one I can agree with. This just isn’t the way to do it.
Steve Gibson, host of the Security Now Podcast, had a recent episode where he suggested connecting three routers in a Y configuration in order to achieve network isolation. The head router only serves to connect two secondary routers. The first secondary router is to be used exclusively for more secure device traffic while the second secondary router is to be used for potentially insecure IoT devices. This isolation would help to mitigate the severity of issues like this.
The problem I’ve always had with the IOT is the use case for them. I’m going to stand in front of my thermostat, going thru my pictures? Really?
I’m going to receive an email when my toast pops up? Really? I won’t see it?
For the refrigerator, I know what the use case is. It’s taking the shopper loyalty card to the next level. The manufacturer is collecting and I’m the product being sold to whomever the manufacturer can get a buck from.
Same story for the Microsoft game consoles, & Smart TVs. The manufacturer is collecting data on my use habits, and then selling my personal life to anyone with a buck. And the manufacturers will fight you if you try to keep your personal data private. As was noted with the Honeywell thermostat above, try not plugging your device into the internet, and discover how it doesn’t work (how many normal users would figure a way around the restriction).
I’ve got a Honeywell digital thermostat with NO internet connection, and “it just works”. There is something to be said for devices that just work, and can’t be hacked, because there isn’t anything to be hacked.
I’ll give you my use case: Seasonal homes up North and in Florida. Allows me to monitor/adjust temperature/humidity when I’m away. E.g. raise temperature a couple of days before my return from 55F to 68F to arrive to a comfortable home. Alerts for when heat or A/C go out are also quite useful.
I know, 1st world problem!
Sigh…
Stephen Vincent Benet gave us ample warning in 1947
Nightmare Number 3
http://allpoetry.com/poem/8513591-Nightmare-Number-Three-by-Stephen-Vincent-Benet
I am awaiting delivery of an IOT bog. Exploits could have messy consequences.
No mention of Cisco hard coding back doors into their spam appliances?
typical!
It would be nice if OpenWRT, Tomato, and other router firmware supported an arbitrary number of separate VLANs, or better, a matrix of what could talk to what (including the Internet port) & how, with the default being “NO”
Side note on the topic of “IoT devices lasting longer than a normal software lifetime of 2-10 years”. Take a look at the update instructions for the Trane device in question; it depends on an SD card. Now is that card reader SD or SDHC, or SDXC? As things stand today good luck finding an original SD card. 10 years from now? Good luck finding an SDHC card to do the update with.
Why couldn’t it just be USB?