Last week, KrebsOnSecurity broke the news of an ongoing credit card breach involving CiCi’s Pizza, a restaurant chain in the United States with more than 500 locations. What follows is an exclusive look at a point-of-sale botnet that appears to have enslaved dozens of hacked payment terminals inside of CiCi’s locations that are being relieved of customer credit card data in real time.
Over the weekend, I heard from a source who said that since November 2015 he’s been tracking a collection of hacked cash registers. This point-of-sale botnet currently includes more than 100 infected systems, and according to the administrative panel for this crime machine at least half of the compromised systems are running a malicious Microsoft Windows process called cicipos.exe.

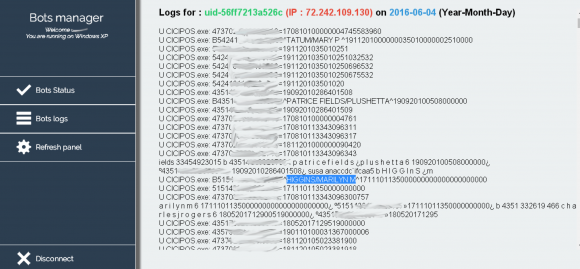
This admin panel shows the Internet address of a number of infected point-of-sale devices as of June 4, 2016. Many of these appear to be at Cici’s Pizza locations.
KrebsOnSecurity has not been able to conclusively tie the botnet to CiCi’s. Neither CiCi’s nor its outside public relations firm have responded to multiple requests for comment. However, the control panel for this botnet includes the full credit card number and name attached to the card, and several individuals whose names appeared in the botnet control panel confirmed having eaten at CiCi’s Pizza locations on the same date that their credit card data was siphoned by this botnet.
Among those was Richard Higgins of Prattville, Ala., whose card data was recorded in the botnet logs on June 4, 2016. Reached via phone, Higgins confirmed that he used his debit card to pay for a meal he and his family enjoyed at a CiCi’s location in Prattville on that same date.
An analysis of the botnet data reveals more than 100 distinct infected systems scattered across the country. However, the panel only displayed hacked systems that were presently reachable online, so the actual number of infected systems may be larger.
Most of the hacked cash registers map back to dynamic Internet addresses assigned by broadband Internet service providers, and those addresses provide little useful information about the owners of the infected systems — other than offering a general idea of the city and state tied to each address.
For example, the Internet address of the compromised point-of-sale system that stole Mr. Higgins’ card data is 72.242.109.130, which maps back to an Earthlink system in a pool of IP addresses managed out of Montgomery, Ala.
Many of the botnet logs include brief notes or messages apparently left by CiCi’s employees for other employees. Most of these messages concern banal details about an employee’s shift, or issues that need to be addressed when the next employee shift comes in to work.
In total, there are more than 1.2 million unique credit and debit card numbers recorded in the botnet logs seen by this reporter. However, the total number of card accounts harvested by the cybercrooks in charge of this crime machine is probably far greater. That’s because the botnet logs go back to early April 2016, but it appears that someone reset and/or cleared those records prior to that date.
Only about half of the 1.2 million stolen accounts appear to have been taken from compromised CiCi’s locations. The majority of the other Internet addresses that appear in the bot logs could not be traced back to specific establishments. Others seem to be tied to individual businesses, including a cinema in Wallingford, Ct., a pizza establishment in Chicago (the famous Lou Malnatis), a hotel in Pennsylvania, and a restaurant at a Holiday Inn hotel in Washington, D.C.
This particular point-of-sale botnet looks to be powered by Punkey, a POS malware strain first detailed last year by researchers at Trustwave Spiderlabs. According to Trustwave, Punkey includes a component that records keystrokes on the infected device, which may explain why short notes left by CiCi’s employees show up frequently in the bot logs alongside credit card data.
Although CiCi’s has remained silent so far, the company’s main point-of-sale service provider — Clearwater, Fla.-based Datapoint POS — told KrebsOnSecurity last week that the hackers behind this botnet used social engineering to trick employees into installing the malware, and that the breach impacted multiple other point-of-sale providers.
“All of these attacks have been traced to social engineering/Team Viewer breaches because stores from SEVERAL POS vendors let supposed techs in to conduct ‘support,'” said Stephen P. Warne, vice president of service and support, in an email to this author. “Nothing to do with any of our support mechanisms which are highly restricted and well within PCI Compliance.”
Point-of-sale based malware has driven most of the credit card breaches over the past two years, including intrusions at Target and Home Depot, as well as breaches at a slew of point-of-sale vendors. The malware usually is installed via hacked remote administration tools. Once the attackers have their malware loaded onto the point-of-sale devices, they can remotely capture data from each card swiped at that cash register.
Thieves can then sell the data to crooks who specialize in encoding the stolen data onto any card with a magnetic stripe, and using the cards to buy gift cards and high-priced goods from big-box stores like Target and Best Buy.
Readers should remember that they’re not liable for fraudulent charges on their credit or debit cards, but they still have to report the phony transactions. There is no substitute for keeping a close eye on your card statements. Also, consider using credit cards instead of debit cards; having your checking account emptied of cash while your bank sorts out the situation can be a hassle and lead to secondary problems (bounced checks, for instance).




“he used his debit card to pay for a meal he and his family enjoyed”
Sorry, I need a little more evidence, this is a VERY sketchy claim
Are you making a joke about the quality of Cici’s Pizza? Because if you’re actually talking about the malware infection there seems to be plenty of evidence supporting it.
Low quality food while making a huge profit
The quality of the food is a subective issue. Of course the complaintant’s issue is with them making a profit.
Because god forbid capitalism actually works.
He probably posted it from an Apple device.
It’s not a claim, it’s a statement. What exactly do you find so sketchy about it?
Pretty sure it’s a joke implying that no one would enjoy a meal at Cici’s Pizza
For sure a joke about the quality of CiCi’s pizza. Pretty good one at that.
Ah, I see. Apologies.
Easy to miss if you haven’t partook at any of the chain pizza buffet restaurants… Reminds me of “pizza” day in elementary school haha
Sorry, it was a low brow joke about CiCis soaked cardboard buffet. I do take this site and your work seriously but this was too easy to pass up. Having eaten there a few times back in college I can say from experience that $5.29 does not buy all the pizza you can eat, it buys just enough to disappoint you.
I needed a good laugh today and I thank you for that!
The only rebuttal I have for that is that when we had one in town, I was able to use my college ID to get a discount and only ever paid $4 for the buffet and a drink.
Is CiCi’s good? Not particularly. Was it worth the price? Definitely.
Sadly it seems the rest of the town didn’t agree with me and they closed 5 years back.
Thanks, Joe. Having eaten at CCs once (and that’s all it took), I got the joke the first time around but your second one is even better. You missed your calling.
If Brian supported upvotes, I would give you one.
I too thought the takeaway was ‘Another reason NOT to eat at Cici’s, as if you needed one.’
I don’t think comedy and nerdery go together 🙁 I enjoyed your post, Joebob2000
Excellent work as always Brian. I’m frankly shocked that there is not more POS Malware out in the wild.
I’m afraid, there is more to be discovered
Company should be held reliable and fined. For lack of security measures. Then company’s will have top notice security.
Forget Datapoint’s support mechanisms, how is it that unencrypted card data can be read from a Windows PC and that be PCI compliant?
Steve,
Great question. PCI does NOT require card data to be encrypted in transit on private networks. It requires card data to be encrypted at rest. This is where PCI fell and continues to fall way short. If PCI would have required encryption upon acceptance (Swipe, Dip, Tap, Key), this would have pushed down prices on End to End/Point to Point encryption solutions and would have led to higher of adoption and a significant reduction in these massive data breaches.
Unfortunately EMV does not address this issue either. Full card data is still passed through to the POS system where these POS based Malwares collect card data.
PCI compliance issues would actually be the case if these POS machines can actually establish connections to unlimited/unfiltered internet without a man-in-the-middle machine proxy making this happen; so, if these infected machines are directly calling out to the malware site via the internet, there are definitely PCI concerns, as this should not be possible. This is where most compliance failures occur at the POS.
I feel very strongly that there should be a firewall in or in front of every POS that Only allows very few IP connections. To their transaction service, update service, maybe a support IP if different than the update connection.
$100 solution to a billion dollar problem.
My question is- how hard is it to just put the POS on a VLAN, and “blackhole” the VLAN from all but the valid destination address?
The Target breach involved an HVAC company that had their credentials stolen, the crooks used them to get into Target’s network and apparently found their environment relatively flat and thus exploitable.
Am I wrong?
Unfortunately, encryption won’t solve the issues. The POS Malware is able to steal card numbers at the point of swipe or in the case of EMV at chip read. This is only going to grow. I guearantee there are numerous cases of POS breaches that go unreported each year.
Encryption at the credit pad level DOES solve this issue. The transaction should be tokenized before it ever touches the computer. This effectively eliminates the impact of malware. However, one thing that pad-level encryption doesn’t solve for is physical card skimmers.
RTW made a great point that PCI-DSS falls short in this area – instead of requiring Point-to-point Encryption, they require that companies to commit untold numbers or resources to secure data at rest. Meanwhile, the majority of breaches occur right at Point-of-Sale… attackers don’t even need to break into a card database to get exactly what they want.
When pursuing PCI, your first priority should be to bring every system you can out of scope by ensuring that plain text card data is never transmitted or stored on the same network. A retailer can even advance to the level where PCI doesn’t apply to them directly, because their entire network is out of scope. This requires that every single transaction is encrypted at the credit pad level – no exceptions.
Some other posters brought up the point that POS systems should never have open internet access – and that’s also true. But this is only effective if those POS stations are also completely firewalled away from the rest of the network, so the attacker isn’t able to move that data to a jump box (that does have internet access) and extract it.
You are all missing the point here, and a couple responses are just flat out incorrect. PCI does mandate encryption in transit. The two primary issues are not encrypting at swipe on the POI device leaving that process up to the lane which vulnerability to Malware scraping. The second issue is compliance based. Making the assumption Wendy’s is a franchise based business the card transaction count probably isn’t going to meet the 6 million limit to require QSA validation of controls – it’s a self assessment questionnaire.
Everyone always wants to bash PCI, but the issue isn’t the controls, it’s the implementation.
compliance =! secure
There are card readers that encrypt as the data is read, which would protect this data.
As to PCI compliance, we would have to take the statement at its word. Let’s see the ROC (which won’t happen). Even then, remember the bank hack where the perps opened accounts with a high profile institution, logged into their account, and then substituted other account numbers into the string their browser sent to the bank? They were able to drain accounts because their session was able to access other accounts. I guarantee you the institution had passed an audit, but was not compliant.
Seems like the data should be encrypted with DUKPT all the way to to their credit card processor.
Brian
Without giving exact details could you explain how it was possible for you to find and view a botnet manager? Can you tell us why the DOJ is not able to do the same thing and use that information to find out who is responsible?
There are a few ways to figure out, reverse engineering the piece of malware usually will point you to the server and then some basic detective work. But I too would like to know how he did this one.
About the DOJ they should be able to do this easily, FBI usually works pretty close with people and I am sure Brian included about passing the information on to them.
PLOT TWIST: Krebs is Botnet, Botnet is Krebs! (actually I’m sure B has people on the inside that he can go to privately for this). Also I too appreciate all the work and risk you go through, doing what you do. It’s appreciated!
‘risk you go through’ what are those risks?
Have you read his articles besides just this one? He’s gotten attacked by swatting, sent heroin in the mail (from someone buying through silk road) to try and frame him, he’s gotten his accounts social engineered (I forget who it was, maybe paypal or his phone company) and more. He gets specifically targeted by malicious actors.
So yeah, there ARE risks, not just risk to his money, but his freedom and his very life.
All of this is detailed in his past articles, including some of them referenced in articles within the last 30 days or so.
http://www.bleepingcomputer.com/ yeah, that’s the question I was also about to raise, also those folks got pretty much insight into the things that seem to be private. But I believe that they do white hacking, if any, no scam.
So does Stephen P. Warne == Todd from the last article’s comment section? His comments seem very similar to the ones you mentioned, but I find it odd he needed to use a false name.
Any person who is stupid enough to eat food at CiCi’s should haven their credit card numbers taken.
Tell me again, who made you a food critic?
Oh it’s so much fun getting around Krebs comment filters
Anyway, to many stores employee’s including management are highly ignorant when it comes to technology and protecting their equipment and customers from cyber threats. I found many coffee shops in my area are like this. I was able to gain full access to their WIFI routers and the people who worked their where clueless.
I don’t believe there’s any comment filters here. I think it’s just that some behaviors trigger the “send this post to moderation” behavior (as opposed to the normal post immediately behavior). Sometimes mine get sent there, but Brian seems to always post them (at least mine).
So wait a bit and your comments will likely show up after he approves them
He does “censor ” and that’s coming from a former New York Times journalist.
dead gorilla !
It’s not censorship to keep people like your from commenting and being a jerk. There’s no first amendment right that gives anyone here the right to say whatever they please, and certainly no reason for me not to block comments from people like you. Most of your comments are obnoxious and insulting to me and to others here. As long as you continue to do that, I’ll continue to get rid of your asinine and inane comments.
It’s a private blog, you have no rights here. I don’t like censorship either, but this blog is popular because of how Brian handles it.
You have every right to write something about Brian Kreb’s blog on NYT, but you won’t. As long as it’s not a government stopping you from publishing, I don’t care.
This is how I make a living. Your coming on here just to urge readers to block ads on my site — as you’ve done countless times — is the surest way to get banned. Unlike the vast majority of web sites that run ads from third parties and unnecessarily exposed their visitors to malvertizing, all of the ads here are run in-house.
“Can’t fix stupid”
Brian, thank you for your diligent work. Also, thank you for keeping the comments civil.
Good article by the way
Chris, I agree wholeheartedly with your DKTPT comment. Encrypted card readers (DUKPT) back to gateway processor would seem to be the answer here. While the malware can still do bad deeds like steal corporate and the like, no card data would compromised in this case when using a aP2PE or E2EE solution.
It would seem these problems will continue until these older POS systems are have been completely replaced, because it is so easy with social engineering to break into older POS systems where the card data us there in the open.
Excellent as always. Raising even more questions.
From one above, why is credit card data available to the machine, to verify. The machine is not encrypted, it has to connect to a certain site to get credit data, so it has to know where to contact. There is more then one card credit bureau, to verify. Example, MC/visa/ diners. They are verified, and sent to the agency, and a charge held. During that, they credit track you, experian, and the others use the raw data, say, stopped at Dick’s diner, so which part should be encrypted, really, all three, but, they would have to use easy encryption, something a CD/Android powered, or so powered machine could do in milliseconds. Remember it takes longer to print the receipt then do the charge. But then ,
Social engineering, blame the lowest common denominator. No managers on site? No verification of the programs loaded by the machine? Interestingly, even ce did that, imbed xp, does that, and all the newer stuff, needs up to more then a few minutes to do it. Looking for signatures that need to be verified. So someone spoofed and spidered the system, I wonder if there is a propagation program looking for names, or certain hardware’s to bypass. Certain routers, certain readers after a router?
Story reads like “Bullseye Breach” by Greg Scott. Clearly CiCi didn’t read the book, or thought: “that can’t happen here!”
Brian – I don’t recall Malnati’s disclosing a breach. Did you let them know you found some ‘bot running around their place?
They make great pizza. Gino’s / Uno’s / Due’s were better, but that was decades ago. Like too many other merchants they might be without a cyber-clue.
1+ million exposures? Under-reporting runs rampant.
Jonathan
They didn’t. I did. And no, I didn’t contact them, nor did I call the other 200 victims in the botnet. I outsourced that to someone who gets paid to do that kind of thing 🙂
Ha, I was going to ask the same thing. I’ve loved Lou’s even before I lived in Chicago. Hopefully somebody’s looking at it.
Hi Brian,
Interesting to note that half of the numbers listed on your screenshot are EMV enabled. It has always perplexed me as to why America still allows for encryption to be done at the point of sale rather than the eftpos unit itself. Please note that I understand that there are plenty of instances where there may be a keyboard / POS track2 reader however that should be cut out.
Can someone explain why businesses think this is a viable approach to security. The fact that the POS provider is staying within their “PCI guidelines” yet has exposed plenty of card data is laughable. It shouldn’t matter if the POS is compromised, if the POS see’s no sensitive card data then the malware is useless. All the malware can read is encrypted traffic.
These payment systems need to get with the times!
I believe such systems are available, but in order for a merchant to take advantage of those systems, the merchant needs needs new hardware, his payment processor must have the equipment to handle those transactions, and the transaction costs for those types of encrypted transactions are triple or quadruple the cost of current EMV and non-EMV transactions.
If I’m a merchant and my POS system is currently accepting EMV transactions, why would I increase my cost of doing business with no return on my investment?
@Brian: Debit Cards do have some liability…
http://www.bbb.org/blog/2013/11/do-debit-cards-and-credit-cards-hav-the-same-protection/
My bank, 5/3 Bank in Cincinnati, offers a debit card that has a separate balance from my checking account. If an attempt is made to withdraw or charge more than the available balance in the card’s account, the request is denied with no fee charged to me. I keep $240 in this account, so if it is compromised, that is the limit of the amount that can be charged with that card. Transferring money into the debit card from my checking account can be done online or through a smartphone app.
Other banks surely already have a similar product or will have one soon.
Anyone noticed in the screenshot, that the “bots manager” is running XP? not good. Don’t get infected while you do your research on the panel…never know, what these criminals are up to…
I believe a lot of POS solutions were only certified with XP, and are still running it.
I use Robtex, and it goes a bit deeper sometimes. One can hope the records are kept up to date, and if so, this is what I see:
CustName: THE LONGSHORE MEDIA DEVELOPMENT
Address: 603 MARTHA ST
City: MONTGOMERY
StateProv: AL
PostalCode: 36104
Country: US
RegDate: 2005-11-23
Updated: 2016-01-30
Ref: https://whois.arin.net/rest/customer/C01227250
“Higgins confirmed that he used his debit card to pay for a meal he and his family enjoyed at a CiCi’s”
Well now we know he’s a liar. No one has ever actually enjoyed a meal at CiCi’s.
sorry, just realized i was a day late to this joke.
End-to-end encryption, from the credit card terminal to the bank would only be possible if the banks themselves controlled the entire process, which they don’t.
“Stephen P. Warne, vice president of service and support, in an email to this author. “Nothing to do with any of our support mechanisms which are highly restricted and well within PCI Compliance.””
Every time an executive says their company was “within PCI Compliance” a puppy dies. Being compliant does not mean you are secure.
Agree totally, Mark. Until management is properly educated on security risks, they will believe that compliance equals security.
We security pros has been trying to get this point across, but it seems to keep falling on deaf ears.
True, although I suspect it was more a legal blanket CYA statement as the executives and their high pay are realizing their chain restaurant credit card processing system has been compromised and its coming out in public (with associated liability and large customer falloff).
It would be better if CiCi’s execs had said they turned off the “infected” POS systems or something, instead it just sounds like they’re trying to figure out what to do while letting their customers credit cards get stolen…and now nobody will want to go there.
Mark, Sasparilla, Baz K, others:
As a customer raising a question, since nothing at the POS says anything about the security of the card processing, what question could be asked to the store manager (that would be answered) as to the assurance that a payment card I use wouldn’t be compromised? It may be more of an annoyance question than expecting any trustworthy, good answer.
Maybe this is too obvious to be stated: The implication of this post is that the breach is continuing and that CiCi’s, or whoever is running the POS systems, has not made any effort to end the breach. A Google news search on this seems to confirm that the breach is ongoing. Hmmm…
Here is the key to a lot of security breech’s if we are to believe this defense: “All of these attacks have been traced to social engineering/Team Viewer breaches because stores from SEVERAL POS vendors let supposed techs in to conduct ‘support,’” said Stephen P. Warne, vice president of service and support, in an email to this author. “Nothing to do with any of our support mechanisms which are highly restricted and well within PCI Compliance.”
The initial report seemed to mention that DataPoint POS customers were targeted. CiCi’s just seems to be the only company aware or admitting they were impacted from their own volition. Is it possible a merchant like Subway or other major DataPoint users were impacted but are admitting it or aware? Due to the allegations please don’t post this, I don’t need Subway’s version of Todd or DataPoint Todd 2.0 commenting on the defensive. I am concerned for consumers not the CYA of companies. I value your input, understanding, and objectivity.
Apologies I thought the comment would be pending review. (Also correction…I meant are not admitting it or are not aware)
Actually, as stated in the article, CiCi’s has not yet acknowledged a breach (at least not to me).
Oh I see, thank you for pointing that out. I apologize for being mistaken. I sincerely hope that any and all impacted merchants identify and rectify this as soon as possible. So impacted consumers can take the necessary steps to protect themselves before fraud occurs and purchase in peace.
More and more I am glad I use cash for in person purchases. Gas, grocery, restaurant, etc. Seems I only use CC for Amazon and Frontier bill.
I would like to get in the habit of doing that. However, I just really love the convenience of the plastic and I have a bit of a habit to lose things..and all the liability of real paper money is on me.
>>More and more I am glad I use cash for in person purchases
I still carry little cash, just have two cards that have decent rewards. If something happens I use the other until the card co sends me a replacement. Doesn’t bother me in the slightest if the card # gets compromised, truly doesn’t affect me.
Why are these POS devices or the hosts they are connected to even allowed to communicate with anything other then card transaction services and internal to business systems. If you put your systems that interface with customer PI on the DMZ its like leaving the front door open. Am I wrong? I want to know.
You’re not wrong, it would make the theft more complicated. But I think that even the Target theft used internal business systems as a staging point for outgoing data. And it would eliminate the possibility for remote support without a trip – thus increasing the cost for the merchant. Hard to justify perfect security until there have been many breaches.
I am glad I use cash for purchases
Thank you so much for this article , i found this panel since 6 months ago , ther’s an SQLi in “login.php” , if you need it , i can share with you my python script to exploit it automaticaly .
You’re helping the world with your articles . this is my first comment 😉
The Company should consider improving its security measures.
great security Idea