Hackers of all stripes looking to test their mettle can now legally hone their cyber skills, tools and weaponry against any Web property operated by the U.S. Department of Defense (DoD), according to a new military-wide policy for reporting and fixing security vulnerabilities.

Security researchers are often reluctant to report programming flaws or security holes they’ve stumbled upon for fear that the vulnerable organization might instead decide to shoot the messenger and pursue hacking charges.
But on Nov. 21, the DoD sought to clear up any ambiguity on that front for the military’s substantial online presence, creating both a centralized place to report cybersecurity flaws across the dot-mil space as well as a legal safe harbor (and the prospect of public recognition) for researchers who abide by a few ground rules.
The DoD said it would “deal in good faith” with researchers “who discover, test, and submit vulnerabilities or indicators of vulnerabilities in accordance with these guidelines:
“Your activities are limited exclusively to –
(1) Testing to detect a vulnerability or identify an indicator related to a vulnerability; or
(2) Sharing with, or receiving from, DoD information about a vulnerability or an indicator related to a vulnerability.”
The Department of Defense also issued the following ten commandments for demonstrating compliance with its policy:
- You do no harm and do not exploit any vulnerability beyond the minimal amount of testing required to prove that a vulnerability exists or to identify an indicator related to a vulnerability.
- You avoid intentionally accessing the content of any communications, data, or information transiting or stored on DoD information system(s) – except to the extent that the information is directly related to a vulnerability and the access is necessary to prove that the vulnerability exists.
- You do not exfiltrate any data under any circumstances.
- You do not intentionally compromise the privacy or safety of DoD personnel (e.g. civilian employees or military members), or any third parties.
- You do not intentionally compromise the intellectual property or other commercial or financial interests of any DoD personnel or entities, or any third parties.
- You do not publicly disclose any details of the vulnerability, indicator of vulnerability, or the content of information rendered available by a vulnerability, except upon receiving explicit written authorization from DoD.
- You do not conduct denial of service testing.
- You do not conduct social engineering, including spear phishing, of DoD personnel or contractors.
- You do not submit a high-volume of low-quality reports.
- If at any point you are uncertain whether to continue testing, please engage with our team.
In return, the DoD said it commits to acknowledging receipt of a report within three business days, and that it will work to confirm the existence of the vulnerability to the researcher and keep the researcher informed of any remediation underway. There are some restrictions, however. For example, researchers who report vulnerabilities will be expected to refrain from publicly disclosing their findings unless and until the DoD provides written consent that it’s okay to do so.
“We want researchers to be recognized publicly for their contributions, if that is the researcher’s desire,” the DoD stated. “We will seek to allow researchers to be publicly recognized whenever possible. However, public disclosure of vulnerabilities will only be authorized at the express written consent of DoD.”
The DoD said if it couldn’t immediately fix or publicly acknowledge reported vulnerabilities, it might be because doing so could have life-or-death consequences for service members.
“Many DoD technologies are deployed in combat zones and, to varying degrees, support ongoing military operations; the proper functioning of DoD systems and applications can have a life-or-death impact on Service members and international allies and partners of the United States,” the agency observed. “DoD must take extra care while investigating the impact of vulnerabilities and providing a fix, so we ask your patience during this period.”
HACK THE ARMY
The Defense Department made the announcement via Hackerone.com, a company that helps organizations build and manage vulnerability reporting policies. HackerOne also helps customers build out “bug bounty” programs that remunerate and recognize researchers who report security flaws.
HackerOne currently is coordinating an upcoming bug bounty program called “Hack the Army,” in which some 500 qualifying contestants can earn cash rewards for finding and reporting cybersecurity weaknesses in the Army’s various online properties (incidentally, Hack the Army runs from Nov. 30 through Dec. 21, 2016, and interested/eligible hackers have until Nov. 28, at 17:00 EST to apply for a shot at one of those 500 spots).
Alex Rice, HackerOne’s co-founder and chief technology officer, said most organizations don’t have an official policy about how they will respond to reports about cybersecurity weaknesses and liabilities, and that the absence of such a policy often discourages researchers from reporting serious security holes.
“The default is terribly unfriendly to researchers,” Rice said. “The Computer Fraud and Abuse Act (CFAA) allows almost any company to go after researchers as hackers, and this happened far too many times. What this does is carve out a safe harbor from the CFAA, and begin to create a safe place that is really powerful and important.”
Rice said HackerOne last year took an inventory of vulnerability disclosure policies at the Global Forbes 2000 list of companies, and found that only six percent of them had published guidelines.
“You cannot run an effective public vulnerability disclosure program or a bug bounty program without having competent security professionals internally,” Rice said. “The problem is, the vast majority of organizations don’t have that.”
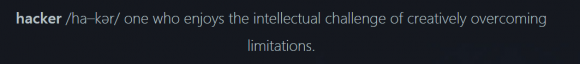
Image: Hackerone.
And when you start asking people to find and report gaps in your cybersecurity armor, you’d better be ready for them to do just that, said Jeremiah Grossman, chief security of strategy at anti-malware firm SentinelOne.
“I’ve seen people try to launch these vulnerability disclosure programs and then fail spectacularly because they don’t have the resources to handle the response,” said Grossman, who also serves on the advisory board for Bugcrowd — one of HackerOne’s competitors. “When you’re really mature in security, and not before then, is about the right time for a bug bounty program. If the organization can handle one to five vulnerabilities reported each month and can fix each of those in a few days, then they’re probably ready.”
Rice said one reason he’s so excited about bug bounty programs is that they offer would-be security professionals a way to demonstrate their skills in a safe and controlled environment.
“If you’re a security professional looking to challenge yourself and your skills, there are very few real world opportunities to do that, to test your mettle and improve,” Rice said. “But that real-world experience is so unbelievably critical in this industry, and we need to be creating more opportunities for people to improve that. The more we can do that and share what we learn out of it, the more we can raise the talent and education of security professionals worldwide.”
Hardly a week goes by when I don’t hear from a young or career-changing reader asking for advice about how to carve out a living in cybersecurity. This happened so often that I created an entire category of posts on this topic: How to Break Into Security. I’ll be revisiting that series soon, but for the time being I want to encourage anyone interested in building their skills through legal hacking to consider creating relationships with companies that have already sanctioned — and in many cases financially reward — such activity.
For starters, Bugcrowd has a nice list of bug bounty and disclosure programs from across the Web, broken down according to whether they offer various benefits such as financial reward, swag or public recognition. Hackerone maintains a searchable directory of security contacts and vulnerability reporting policies at various corporations.




First comment
Now, how did you beat IRS ITUNE cards?
Hehehe…
That aside, it is a great article. Similar to what many corporations already deploy.
Good article !
Third to last paragraph:
“If you’re a security professional looking to challenge yourself and you skills…”
Should it be “your skills”?
Thanks for checking that, Krabs!
Only racists make fun of ebonics.
The DoD intrusion detection systems are going to get swamped with scanning activity, which will blind them to actual scans of malicious intent. I wouldn’t be surprised if this bounty is cancelled quickly.
That is almost always the case anyway. Malicious attackers usually know better than to fire up a scanner and start ringing every alarm bell possible. They didn’t just float this idea without gaming out most concievable scenarios.
Let the games begin! This reminds me of the DARPA Shredder Challenge:
http://archive.darpa.mil/shredderchallenge/
Sweet!
If you’re going to pen-test web sites operated by the military, please don’t forget three things:
1. “There’s always somebody who doesn’t get the word” — a statement of how hard it for the army to make changes in policy known to everybody.
2. A simple claim of a threat to national security gives people in the military extrajudicial powers and freedom from accountability for abuse of those powers.
3. They have lawyers, guns, and money. More of those assets than you do.
So, be careful. You could run afoul of some major someplace and find yourself with a lifetime of trouble.
As we all know the very same who control banks and goverment
And internet….google jp morgan chase and all others like facebook the very same people organising cyber crime the very same people creating and maintaining carding forums its simple
So world will move from capitalist regime to communism.
Needless to say but who cares? Nobody dont cares. Anyways
Humanity is sick!
Right now its big mess big chaos… so when there will be order
Like laws rules and everything will be survalinced….them people
Start cry like nwo and all that. People not happy they cant hide they earnings anymore or cheating others. Then they cry…. why police state why military so strong tgey cry. But when they have freedom tgey acting like some wild brainless animals.
Humenity need to learn hard way how to live together like higher creatures of universe…with peace and hapiness..not like some wild grazy animals. First thing people need to learn is drop down selfisness and ego. Start think what u do it to others its all to do with aswell. Our actions is relatwd with others.
When this animal like humens start to undestood this????
Men overboard! US Navy spills data on 134k sailors
http://www.theregister.co.uk/2016/11/24/in_the_navy_we_sink_thanks_hpe_in_the_navy_we_lose_data_with_ease/
Great article. Thank you Mr. Krebs.
Earlier this month, the NTIA Safety Working Group posted a draft document on how to write a Vulnerability Disclosure Policy. The 10-page guide provides a sample template as well as specific ideas for developing an adaptable, lightweight vulnerability disclosure policy. Although this is probably not as robust as the DoD or bug bounty administrator guidance, it could help organizations start to think about the process.
https://www.ntia.doc.gov/other-publication/2016/multistakeholder-process-cybersecurity-vulnerabilities
make great american again
I see where they going with this .You Give them away everything for free ,so they can hack you later /: (
I’m sorry, your comment has a syntax error. Please fix the error and try again. If you discover a vulnerability in the military’s systems, why would you allow that same vulnerability to remain unpatched on your own systems?
So , to be clear, I can just get onto some .mil website and start fuzzing?
Offhand, I think the devil is in the details:
> You do not conduct denial of service testing.
If your fuzzer results in a DoS, or they decide to categorize it as a DoS, you’re in trouble.
Further, one would hope that .mil is already using standard testing suites/fuzzers. So, IMO doing so is a waste of resources.
Basically, any pre-packaged system that anyone can run will probably be run by someone, so why should you spend the resources doing that?
“In 2006, the Coverity Scan service was initiated with the U.S. Department of Homeland Security as a public-private sector research project, focused on open source software quality and security.” [1]
Given that DHS offers Coverity to major Open Source projects, one would hope that Purify / Coverity / other major tools are already being used for DoD services…
[1] http://www.coverity.com/press-releases/coverity-scan-open-source-report-shows-commercial-code-is-more-compliant-to-security-standards-than-open-source-code/
Interesting link. It makes me wonder about all those major sites getting hacked and takin down over these last few years (things like target, ashley madison, adult friendfinder, the DNC, various hotel chains, the playstation network, etc.) It certainly sounds quite the opposite. It doesn’t seem like ‘commercial code’ is all that good at thwarting issues.
There are two things that people seem to be missing here:
a) Hacking has already been made a federal offense. Any attempt on any .mil site (regardless of method, intent, or even effectiveness) would be all that is needed to get a person in trouble. This whole idea is nothing more than entrapment.
b) It is a two-way street. If you can get in to see what’s inside, it would be a fair bet that they can see you too.
The only way this might be worth it is if you are getting paid by the US government to do this. Anything else comes with a high degree of probability that the future will be prison, unless you are a hacker for a foreign government (which could be how they are trying to find out who has been doing things).
We all already know that many government websites are vulnerable. This kind of activity doesn’t actually mean anything for ‘testing’. This is just a part of all this non-sense regarding Snowden. What we are witnessing is a group of government leaders running around like chickens with their heads cut off trying to show the world they know something when they know nothing. There is absolutely NOTHING that Snowden ever said that we did not already know. Yet he is treated as if he unveiled a universe of so-called secrets to wake everyone up. Snowden is not a hero. He is not a traitor either. Neither label applies in his case and it’s NO different here with this article. It’s just like how we will see ISP commercials advertising for MS office as some new product. This is just craziness.
Just do it ethically, and then there will be no jail time for you. Break the rules of engagement by not following the guidelines, and then there will be jail in your future. So again remain ethical, and unlike Snowden you would be in the clear. Whereas Snowden acted unethically and therefore is a traitor by aiding and abating the enemy with his release of classified information to the global media complex.
“…with his release of classified information to the global media complex.”
lol…..that’s what I’m talking about.
He did not release anything. You are being told that he did. But he never released anything. All the stuff he has said publicly was already out there for the world to see for themselves (and many did). The only issue with him is that he greatly upset his superiors (which happens to be the US government) through breach of contract. But everything he’s said, we already knew. So it’s all just b.s. for people in high places to make a fuss over.
As for ethics:
That is a trap. It is a lie. This isn’t about ‘ethics’ at all. Ethics does not change wether or not something is illegal to do. Committing a crime is still a crime even if done with the purest ethics. This is why the Clinton email server issue is such a big deal that never seems to go away.
You have been drinking the kool-aid far to much to be commenting on national security matters that you know nothing about. So please educate yourself, as I was there when he started to release information. So please stop drinking the kool-aid and come back to reality. He impacted a lot of peoples lives by his treasonous acts, and my life included. Nearly lost my house as I was unemployed for nearly 7 months because contracts were being cut left and right as this traitor released more and more information, and the clearance vetting process is now taking longer then it should because of this traitors selfish thoughts and acts. So please stop drinking the kool-aid.
you seem like a sensible fellow. However as the man says the devil is in the details. I’m a security researcher but I’m reasonably new to the field. In a sense it would take a maturer worldview to interpret the guidelines and err on the side of safety regarding the researchers personal freedom. A list of no-no’s and possible avenues would be advantageous. Like for example is testing cookies for buffer overflows / sql injection on a piecemeal basis ok. And if thats ok well where does that leave something like scanning with nikto or looking for dom based insecurities with automated tools? or running all the known sql injections and js vulns in a script? I know this is not the forum for such discussion but where is? Extradition is not a pleasing prospect for me. Maybe there is a hidden assumption here that fuzzing is not allowed as its been done during the security audit and thus only ‘special’ avenues like viewstate vulns and zero days that require specific treatment are within the confines of proceeding?
You personally experienced issues only because of how nervous and genuinely angry this situation made people. It is THAT situation that sparked him to do what he did.
If you want to talk about reality:
NSA spying did not start with Snowden and will not end with him either. Plenty of people have commented, written books, and have well documented videos based on fact with regard to government spying on people. The truth is that the world nearly came unglued during the second Bush’s first term specifically because of organizations in the federal government taping into everyone’s phone calls. We all know they do it. We have all known about this for many years BEFORE Snowden ever came on the scene. For that matter, even the History Channel has broadcast full length documentaries regarding what they spy on. The only real differences between what happened in the 60’s vs. what happens now is that it’s a lot easier to process a much larger foot print because of advances in technology and that simple fact that everyone uses smartphones.
I am NOT a fan of his. But it’s hardly drinking kool-aid to see all the well documented issues that did happen well before he did what he did.
This foolishness is just like being upset at Google for possibly listening in through your microphone when it isn’t about Google at all. It’s about HTML5.
Think about it. If this whole thing amounted to nothing more than someone with access ‘coming out’, it would all end there. What do you think this website is all about? There are issues. Many of them are big issues. It does no good to be upset at Krebs. Krebs just does not have a non-disclosure agreement that the government gets to hold over him. If there were no issues, Snowden could never have THAT MUCH impact. Him commenting about those issues is NOT that same thing as creating those issues…..anymore than commenters on this website.
Then explain to me why all the dates for all the documents revealed modern day sources and methods of collection, explain to me why they didn’t release the documentation of policies and legal and oversight compliance that individuals are put under upon being granted access to such programs, explain to me why these Snowden leaks amounted to over 17,000 system administrators including myself to lose access to systems we administrated that provided crucial time sensitive reporting to the war fighters deployed overseas in hot combat areas where intelligence mattered and where these soldiers and diplomats relied upon time sensitive reporting to protect the forward operating bases and convoys of supplies to people who were impacted, explain to me why ISIS and the Global War on Terror was halted by these releases of information pertaining to our sources and methods, and from my experience in working the intelligence community you assessment is downright ignorant and downright disgraceful when it comes to the National Security of 330 million people and our allies fighting against ISIS. You truly are drinking from the kool-aid that has brainwashed you into thinking these releases do not jeopardize the safety of over 330 million people. So continue to think what you want, because quite frankly you are wrong when it comes to the Snowden Releases and how damaging they were.
As far as the other issues you expressed: If you do not understand the ethical hacking procedures then you shouldn’t really be commenting on this article at all. The rules of engagement are clear, and if they are followed then you will not go to jail regardless of what you think. The rules of engagement are as follows and I quote the article:
23
Nov 16
DoD Opens .Mil to Legal Hacking, Within Limits
Hackers of all stripes looking to test their mettle can now legally hone their cyber skills, tools and weaponry against any Web property operated by the U.S. Department of Defense (DoD), according to a new military-wide policy for reporting and fixing security vulnerabilities.
hackthearmy
Security researchers are often reluctant to report programming flaws or security holes they’ve stumbled upon for fear that the vulnerable organization might instead decide to shoot the messenger and pursue hacking charges.
But on Nov. 21, the DoD sought to clear up any ambiguity on that front for the military’s substantial online presence, creating both a centralized place to report cybersecurity flaws across the dot-mil space as well as a legal safe harbor (and the prospect of public recognition) for researchers who abide by a few ground rules.
The DoD said it would “deal in good faith” with researchers “who discover, test, and submit vulnerabilities or indicators of vulnerabilities in accordance with these guidelines:
“Your activities are limited exclusively to –
(1) Testing to detect a vulnerability or identify an indicator related to a vulnerability; or
(2) Sharing with, or receiving from, DoD information about a vulnerability or an indicator related to a vulnerability.”
The Department of Defense also issued the following ten commandments for demonstrating compliance with its policy:
1 You do no harm and do not exploit any vulnerability beyond the minimal amount of testing required to prove that a vulnerability exists or to identify an indicator related to a vulnerability.
2 You avoid intentionally accessing the content of any communications, data, or information transiting or stored on DoD information system(s) – except to the extent that the information is directly related to a vulnerability and the access is necessary to prove that the vulnerability exists.
3 You do not exfiltrate any data under any circumstances.
4 You do not intentionally compromise the privacy or safety of DoD personnel (e.g. civilian employees or military members), or any third parties.
5 You do not intentionally compromise the intellectual property or other commercial or financial interests of any DoD personnel or entities, or any third parties.
6 You do not publicly disclose any details of the vulnerability, indicator of vulnerability, or the content of information rendered available by a vulnerability, except upon receiving explicit written authorization from DoD.
7 You do not conduct denial of service testing.
8 You do not conduct social engineering, including spear phishing, of DoD personnel or contractors.
9 You do not submit a high-volume of low-quality reports.
10 If at any point you are uncertain whether to continue testing, please engage with our team.
You adhere to all 10 points and do not stray from the rules of engagement, then you are clear. if you stray from the rules of engagement, then you will potentially face some sort of punishment. I would highly recommend you go and take a class on Ethical Hacking and learn what it means to be an Ethical Hacker aka White Hat. So please go re-educate yourself and stop drinking from the kool-aid, you have diluted your intelligence.
I find it interesting that you feel it necessary to essentially chastise me talking to me about putting people’s lives in danger when that is exactly what the military has specifically chosen to do with this action. There are reasons why prostitutes have no credibility. The US government has opened itself up to all kinds of things. Why? You want to tell me about ‘ethical hacking’ with everything that has happened in recent years? Running on the honor system is exactly why so many things are so badly wrecked?
With Snowden:
The truth is actually quite simple. If government were not acting with such malice against everyone else, there would never be a Snowden to deal with.
@Mike,
The assertion “it was all publicly out there” is simply not true. The disclosure of the PRISM program occured on 06/06/2013. Find any earlier credible public disclosure of this program when stating something like “We Already Knew”. Oh, you did?
And to describe what one in IT would accept as “credible”, think reputable Infosec types of sources, and reputable news outlets. Not Infowars and Breitbart.
I’d lay 1/1 odds that Obama pardons Snowden in the last days of his term just to burn old Donald’s leather ass. =)
I never made any claim anywhere that anyone already knew about a specific thing called “PRISM”. That is not what I said. If you go back and actually read what I did say, you will NOT find that anywhere.
“A rose by any other name would smell just the same.”
You can call it anything you want. The particular label put to it does not change what it is. That is just a marketing technique.
Are you really going to suggest that NOONE ever knew anything until Snowden said something? Come on!
I’ve been hearing this stuff since I was a kid.
I agree with you about duplication of effort. But in terms of any fuzzer; the in/out data transmission rate will be bottlenecked by the throughput of your network interface, and again by your ISP’s capped speed. Even being liberal with this throughput and one machine running a fast fuzzer like Skipfish in Linux, you would not be even remotely approaching 1 Gb/s.
I wonder if they’ve resurected dockmaster.navy.mil as their gateway machine?
Why hack the DOD when all you need is external contractors who loose laptops?
http://www.forbes.com/sites/leemathews/2016/11/24/one-laptop-has-leaked-private-data-on-130000-navy-sailors/#70b6b1614199
It is an interesting story, but the story itself answers your own question. 130,000 leaked dox is by the authors own admission, ” a drop in the bucket”. The real answer of course, is to see if you can. People pay hundreds of dollars for time using networks setup specifically for penetration test challenges; setup their own home labs with servers running DVL or Metasploitable, or VM the NIST Windows images; etc to learn and practice legally. Surely, the DOD offers a much more challenging topography and such a diverse attack surface, for free.
can i actually hack the U.S. army?
Brian, are you endorsing hacking as a legitimate activity? Are you legitimizing “hacker” as an honorable profession? The definition you include for “hacker” is exactly what they use to justify and glamorize their crimes. The money they steal from my grandparents is the reward they seek for “discovering” vulnerabilities.
@anna,
Hacking is absolutely a legitimate professiinal activity, whether it is labelled “Certified Ethical Hacker, IT Security Researcher, BugHunter, Penetration Tester, External Infosec Auditor, Proactive IT staff members” etc. You are talking about Grey and Blackhat activity. Activity dealing with systems either not owned enitrely by the actor, or systems which the actor has not been granted expressly and written permission to perform specific tests upon. Clearly illegal activities.
Without ethical actors also working in this space to develop proper vulnerabilty disclosure channels with software vendors and their end customers; the unsuspecting public would be dealing with Illegal activities beyond what they could even imagine.
You could read something like: https://en.m.wikipedia.org/wiki/Certified_Ethical_Hacker
But if you read this site regularly, it’s really very obvious Mr.Krebs goes as far as anyone to expose bad actors and illegal activity for what it is.
“…the unsuspecting public would be dealing with Illegal activities beyond what they could even imagine.”
This is exactly what we are seeing.
@mike, I try to keep any technical writing,exactly that. I’m almost embarassed by the little typo in that post. I read “news” websites and often wonder if anyone is proofreading any of them or if they simply just rely on auto-completion and non-contextual spell/grammar checks.
But I stand by my assessment about the Unsuspecting Public. It is why Americans should be made aware of the specific Russian interference Activities in a US election; and why Trump will ultimately be found to have been in collusion,illegally: with foreign nation state fraud,conspiracy, and probably worse.
Great article!
Recently in Jakarta, Indonesia, A Man arrested after allegedly stealing billions in ATM using “exit shutter fraud” method
http://jakarta.coconuts.co/2016/12/13/man-arrested-after-allegedly-stealing-billions-atm-exit-shutter-fraud