Less than six hours after Donald Trump became the presumptive president-elect of the United States, a Russian hacker gang perhaps best known for breaking into computer networks at the Democratic National Committee launched a volley of targeted phishing campaigns against American political think-tanks and non-government organizations (NGOs).
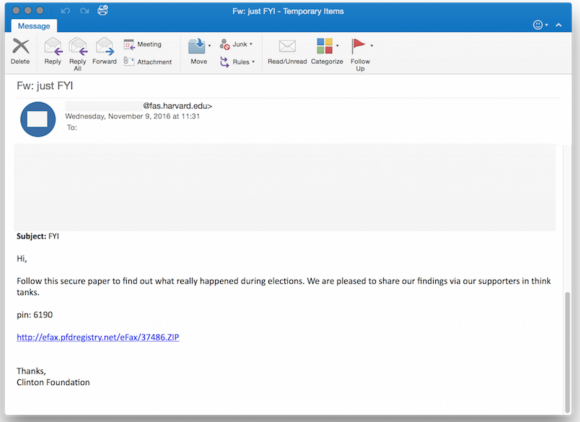
One of the phishing emails in the latest political espionage attack launched by The Dukes. Source: Volexity.
That’s according to a new report from Washington, D.C.-based cyber incident response firm Volexity. The firm’s researchers say they’ve been closely monitoring the activities of an well-established Russian malware development gang known variously as Cozy Bear, APT29, and The Dukes.
Hacking attacks launched by The Dukes were thought to be connected to intrusions at the Democratic National Committee (DNC), as well as cyber break-ins at multiple high-profile United States Government organizations, Volexity reports in a blog post published Thursday morning.
Last month, the Obama administration publicly acknowledged for the first time that it believed that the Russian government was responsible for stealing and disclosing emails from the DNC and a range of other institutions and prominent individuals, most recently Hillary Clinton’s campaign chairman, John D. Podesta. The emails were posted on WikiLeaks and other sites.
Volexity CEO Steven Adair said The Dukes have launched at least five sorties of email-based malware phishing attacks since Trump’s acceptance speech, and that the malware campaigns are ongoing.
“Two of the attacks purported to be messages forwarded on from the Clinton Foundation giving insight and perhaps a postmortem analysis into the elections,” Adair wrote.”Two of the other attacks purported to be eFax links or documents pertaining to the election’s outcome being revised or rigged. The last attack claimed to be a link to a PDF download on “Why American Elections Are Flawed.”
According to Volexity, in July 2015 the Dukes started heavily targeting think tanks and NGOs.
“This represented a fairly significant shift in the group’s previous operations and one that continued in the lead up to and immediately after the 2016 United States Presidential election,” Adair wrote.
Prior to the election, The Dukes were active on August 10, 2016 and on August 25, 2016, launching several waves of highly targeted spear phishing attacks against several U.S.-based think tanks and NGOs.
“These spear phishing messages were spoofed and made to appear to have been sent from real individuals at well-known think tanks in the United States and Europe,” Adair wrote. “These August waves of attacks purported to be from individuals at Transparency International, the Center for a New American Security (CNAS), the International Institute for Strategic Studies (IISS), Eurasia Group, and the Council on Foreign Relations (CFR).”
Adair said the more typical attacks from The Dukes come in the form of slightly less-targeted email blasts — often to just a few dozen recipients at a time — that include booby-trapped Microsoft Office documents.
When launched, the tainted Excel or Word document opens an actual file with real content, but it also prompts the target to enable “macros” — a powerful functionality built into Office documents that hackers can use to automatically download and run malicious code on a Windows system.
The Dukes prefer to launch the attacks using hacked servers and email inboxes belonging to unsuspecting, trusted workers at NGOs and U.S. government systems, Adair explained. Most often, he said, the intruders will repurpose a legitimate document found in one of these hacked inboxes and inject a sophisticated backdoor “trojan horse program.”
If the phishing target opens the document and has macros enabled in Microsoft Office — or allows macros to be run after the decoy document is shown — a malicious script embedded in the macro installs on the target’s system a powerful foothold for the attacker.
Adair said The Dukes have a well-earned reputation for coding and constantly improving their own custom backdoor trojans, but that they’re not known for using so-called “zero day” threats — previously unknown security weaknesses in software and hardware that knowledgeable attackers can use to remotely compromise a target’s computer just by loading a Web page or opening a document.
“In some ways, these guys seem kind of low-budget, but their macros are well-obfuscated and will sail right through just about any [antivirus] tool, appliance or cloud service,” Adair said in an interview.
The Dukes also take great care not to phish security personnel at targeted organizations. For example, if the phishing target has macros enabled in Microsoft Office or allows them to be run after the decoy document is shown, a malicious script embedded in the macro executes a busy little program that scours the target’s computer for signs that it is running on an network administrator’s machine.
If the malicious script detects the user is “admin” or “administrator,” the infection goes no further and the malware shuts down. Likewise, it checks many other signs that it might be running in a “sandbox” environment — a test lab often used by security and malware researchers.
Adair said his although his research team doesn’t have specific insight into to how successful these latest espionage attacks may have been, The Dukes are an effective information- and resource gathering machine.
“My opinion is that if this group got access to a zero-day and it’s something they can embed in a document, they could devastate anyone they target,” Adair said. “This is a well-funded and in some respects professional organization. What they’re doing takes time and effort, and for eight plus years now they’ve been in continuous development of new backdoors. They’re continually targeting different verticals — universities, NGOs and governments — and they learn from others, retool and modify their attacks constantly.”
As The New York Times reported last month, “President Obama is weighing a ‘proportional’ response to Russia’s efforts to interfere with this fall’s election campaign through hacking.
Thursday morning, security vendor Kaspersky Lab warned that a massive cyberattack hit five of Russia’s largest banks. Kaspersky said in a statement that the distributed denial of service attacks (DDoS) began Tuesday at 1830 IST and targeted “the websites of at least five well-known financial institutions in the top 10” in Russia.
It remains unclear who launched the bank cyberattacks, which are reportedly ongoing. Kaspersky said the attack on Russia’s banking system is apparently being launched by a network of more than 24,000 hacked Internet of Things (IoT) devices, and that more than half of the hacked things were in the United States, India, Taiwan and Israel.
Further reading on the storied hacking history of The Dukes:
F-Secure calls them CozyDuke (PDF). FireEye‘s take (PDF). Crowdstrike on Cozy Bear.




This has nothing to do with Donald Trump–no reason to mention his name. The author must be an anti-Trump fool.
And if the article had gone out of its way to not mention anyone by name, you wouldn’t have said the exact same thing?
The author is a well known and widely respected expert in his field… good morning.
Hey! Never let pesky facts interfere with an…uh…errr……opinion! And be ready for lots more of the same!
The phishing email mentioned the election as being rigged, this message baits the user into opening the trojan, so it actually does have something to do with the election of Donald Trump.
Brian Krebs is not injecting politics into this blog, but @RC and @Lets the WW3 begin seem to have an agenda unrelated to net security.
Lets all leave politics out of this excellent site and specifically this informative post from Mr Krebs.
The only fool here is you.
The emails in question used the results of an election that placed Trump in the Presidency and were launched by an organization both the US government and many cybersecurity experts believed to be at the very least “fans” of his.
I don’t know what’s worse, the amount of Trumpettes who find it hard to believe a former KGB guy would do stuff like that.
Reagan truly is rolling over in his grave watching you dolts fall for the old “useful idiot” gambit.
Did you just call Trump Putin’s Jar Jar?
I lolled
Hey you won, stop whining
The lures used in the phishing mails contained a lot of “Trump _____” subject lines. And “Elections Rigged” sort of subjects.
The timing and targeting have to do with the election results. The spearfishing would mention to these groups something about the effect of Trump on xyz to entice the user to open the file. Given the amount of chatter about Trump’s victory the attack could exploit their surprise and shock.
Some understand it, many don’t…. But, “everything has to do with everything”. Everything’s a chain reaction. Just like/comparable to skipping a small stone onto the surface of a body of water and hoping for ripples.
Agree, I know you’re from the Washington Post Brian, but can’t you refrain from the typical left position of using “Russia and Trump” in your headlines, so misleading and exploitative, thought you were above that. Headline should read-
“Hackers jump on Hillary loss, Obama administration at odds with how to curtail relentless hacking and the wreckless use of personal mobile devices and email at the State Dept”.
*reckless*
say what you will about the state of modern journalism but even the Washington Post wouldn’t make that misteak
Good article
All kinds of vague statements in this such as “perhaps best known” and “thought to be connected” highlights the fact that the source of the compromise at the DNC is unknown. Given the security practices we’ve seen by the government in general, I have little faith in their ability to know where a particular attack came from. Our main take away from this whole thing should be to figure out more secure methods for communication in government and to actually use them rather than try to circumvent what little security is in place. Leaders should be held accountable for the security or lack of it in their organizations. Having worked in government, I’ve seen just how little accountability there is in this area. Hopefully this will serve as a big wakeup call for them.
Good to hear a voice of reason. I find it appalling that our government would go out and point fingers at the Russian government when John Podesta fell victim to a phishing attack any little script kiddie with time and interest could have pulled off. If he were my colleague I highly doubt he would keep his job after that. And furthermore, the very rudimentary security training that is required throughout my entire org (I happen to be a developer on a security team but this extends to all non-engineering folks as well) would suffice for avoiding an attack like that. It’s amazing that you can hold a position where you are a high profile target and not be held accountable for upholding even the most rudimentary of security practices.
Beyond that I find it amazing that people would even consider voting for someone who openly admits to being completely negligent with regard to security (even though she obviously wasn’t, just an excuse for her deliberate criminal activity) but even if you view it in that light it should be disqualifying. Hopefully in a few election cycles a younger demographic of voters will demand that those in public office are technically proficient, as an end user at the very least. These people can’t even use their fucking gmail without being a major security risk 😐
LOL. Perhaps if the Republicans had nominated someone who didn’t reveal his profound ignorance of national security issues every time he opened his mouth, you might, just might have a point.
Buckle up, the next four years are going to be an extremely bumpy ride.
You are right Brad, I like your view..We need tack an legal step but we are at zero level…
Why doesn’t the US welcome “The Dukes” to defect, (indeed offer them a job), to America, (just like good Cuban baseball players) if they are that good! Certainly, the US could use “their” talents in protecting their own systems, as obviously, they are at severe risk. Reminds me of a Bruce Willis movie, just can’t remember the name of it! You, Brian, can’t do it all! Cheers!
Frank our Government hires hackers all the time. They have to want to work for us, and most of the time they do not and that is why they are doing what they do. Arrest them and then maybe they will flip or change their minds.
I Bet you 1000 bucks that Brian was voting for KILLARY CLINTON .
And Now he is a bit upset and butthurt , but its ok he will get over it soon .
muahahaha
I would just not use Microsoft Office. There must be other programs the Government departments can use. A new President MAY be able to influence the bureaucracy, who knows.
Hackers appear to be non political.
Getting away from MS Office is possible but requires some effort. Also, Microsoft is a major contributor to political campaigns and few politicians will risk their campaign war chest just to improve security
Indeed, this time around it appears most of the groups don’t really care about the politics, it’s just about money.
Step 1) Hack political group’s donation server
Step 2) Hack opposition group’s email/data/etc. servers
Step 3) Sift through, edit, then leak data to patsy
Step 4) People donate money to political group due to outrage over leak
Step 5) Profit! Profit! Profit!
Dear Brian,
In this article you
1) Describe the activities of what seem to be private citizens of Russia as opposed to Russian government operatives, 2) Cite both Obama and the NYT as stating or strongly implying that the Russian government is responsible for hacking in the US, and
3) Make NO attempt to clarify that the known “Russian” hacking you are reporting on is NOT the proven work of the Russian government.
Please do not do that. It is irresponsible for you to allow the implication to stand that the Russian government perpetrated these hacks. Even if your sources for that supposition are US intelligence agencies, it is only fair to point out that those same sources have agendas and are willing to lie and distort intelligence to further their goals. Remember WMD and the lies about the aluminum tubes.
I would suggest you read Bill Browder’s “Red Notice” for a clearer understanding how Putin and the Russian government works.
Browder used to be a fervent Communist. That’s a reason to disbelieve him. Putin merely worked for his country during Communism.
They can think or suggest or claim the Russians were involved all they want. I am from the show me state, I need to see validated proof, not a bunch of hot air claims and no back up
so wtf did the show-me state go for the unregistered sex offender-elect, who _refused_ to show his tax returns?
fucking hypocrite confederates, should hung’em all 151yrs ago:-\
LOL
Don’t be a sore loser. And don’t prefer opinion over fact.
@airdrummer – Aren’t you a tad bit late on complaining about Missouri voting for an ‘unregistered sex offender’ ?
https://www.britannica.com/event/United-States-presidential-election-of-1992
https://www.britannica.com/event/United-States-presidential-election-of-1996
Since no one I know has seen Obama’s birth certificate I guess we could say he’s the current presumptive president.
Jay, buddy! The whole birther thing is over! Way to prove you’re a moron.
FYI, the unregistered sex-offender in chief would be Don “Grab ’em by the pussy” Trump.
I would suggest you read Bill Browder’s “Red Notice” for a clearer understanding how Putin and the Russian government works.
It isn’t just nation state bad actors that are proficient in attacking targets related to various government activities; I’d say there was already an even more “professional” pool of groups that were doing industrial espionage, some for hire by anyone including governments. I pose a theory that nation states began learning from such pools, and picking and choosing when they want to pay for it, or simply take individuals working in them to dedicated national teams bent on whatever national interests they were bringing forward.
I really think it was independent crackers that got enough attention from governments that seeded this accelerated push from nation states. I point the finger at no one state, as I’m sure they’ve all been in it for a long while. I have my doubts that the US government is competent enough to pull from these “talented” pools – however. They should be hiring from them post haste.
“My opinion is that if this group got access to a zero-day..”
Interesting facts, but the commentary is a little hollow.. I’d like the explanation for why one would assume such a group doesn’t have access to such exploits…
Postings since my original, mention that the source of intrusion into DNC et al has not been definitively determined.
I agree – no actual proof of the source of wikileaks’ hacked emails has been provided by the administration or us government security apparatus, or anyone else for that matter.
Therefore attributing the source of the DNC hacks without supporting evidence would also fall under politics vs. facts and probably should be avoided, to prevent this blog from descending into a maelstrom of political argument.
breitbart.com or huffingtonpost.com are the apropriate venues for your respective political commentary.
Brian:
“Likewise, it checks many other signs that it might be running in a “sandbox” environment ”
Does running everything in a VMWare or VirtualBox machine count as a sandbox for these nasties?
Is there any way to trick them into thinking they are sandboxed without too much complication for an end user?
Thanks for all you do to keep us safe.
No two attacks are guaranteed to use the same checks.
Personally, instead of pretending to be sandboxed, I’d encourage people to live in sandboxes. Brian occasionally notes that he does…
What this can mean is that you create a VM, install a limited set of software, and create a snapshot. If you want to persist a document, you share it and retrieve it from the sandbox. If you fear your sandbox has been infected, you can snapshot the infected instance and roll back to an earlier point in time.
For more protection, your Browsing sandbox should be distinct from the one with Office installed, and your email sandbox should be distinct from the browsing and Office sandboxes.
It’s even easier then that. Ever heard of a live disk? Try it. I would recommend Linux live, and you can use it anywhere. With wine, it even runs most win stuff.
Every political system has its weaknesses, even democratic ones. Several of the political commenters on this article are good examples of the weaknesses our founding fathers were concerned about.
Thanks for all your great work, Brian.
It’s amazing how little it takes to make some people hostile. I’m glad I stay away from social media.
I don’t doubt the reports I’ve read from reputable security companies that Cozy Bear, APT 29, whatever is in Russia. Whether they are supported by the government, who knows? You’d need a security clearance to know, and no one with a clearance and half a brain would tell you…
Keep up the good work Brian!
My apologies for being repetitive but I would suggest reading Bill Browder’s “Red Notice” about Putin and how the Russian government works. The threat is very real.
What we do in the shadows they do in the light.
I’ll get it on my Kindle today. Thanks!
Yes, you’re being repetitive. Thanks for the book recommendation but would you like us to come to the conclusion that, because Russia is so corrupt, the hack was carried out by Russia? Why not China? Or why not some GOP-leaning hacker group in the US?
All we can ever say is that after investigation we have a, I don’t know, 75% confidence that Russia was responsible. But we must not convict anyone without solid proof.
“If the phishing target opens the document and has macros enabled in Microsoft Office”
Again we come to the scenario of MS having a built-in weakness, along with the wetware being a weakness. We may not be able to do anything about the wetware, but we should be able to prevent any weaknesses in MS, especially MS Office Suite, by now. NOTHING should be allowed to execute in any OS as administrator by default (primary MS weakness). NOTHING should be allowed to install unless administrator privilege in invoked. NO EMBEDDED SCRIPT or MACRO should be able to run off of just a click or keystroke. How many more times will we get burned before we stop touching the stove?
Though Obama and the UK government are on the right track with their measured response, what we need is back-hacking that delivers the “Kiss of Death”, not just an inconvenience. Remember, what’s good for the goose is good for the gander and both can be cooked in a pot in the oven…
Good article. Of course they’d relate it to the election – wouldn’t matter who won. Guaranteed to have someone open the e-mail. Unless we start paying attention to the policy end of cyber, nothing will change.
Please don’t politicize Krebs. You don’t need to defend anyone here. Let the reporter report.
Its not their fault, really. All the websites they normally go to are politicized, so therefore when they happen to stumble across a non-politicized website they just drag their normal behavior along for the ride.
Just flush it….and again and again flush it all”)
All this on toilet
After goverment together with fellow mob… done alll dont forget to flush it flush it… dont leave your sht..
Flush again and flush..flush b4 u using toilet always flush it
Flush always rember this:)
Big guys i reprat dont forget to flush…and if the flushing bottom does not work try to fix it…if still not help and thing is too big
Wait when nobody around leave..loo and put the blame on some smaller poor fish…but rember flush it:)
I can find no specific reference to the Podesta hack in the Volexity blog post. That attack was carried out as follows:
Emails show how Clinton campaign chair was apparently hacked – 28 Oct 2016
WASHINGTON (AP) — New evidence appears to show how hackers earlier this year stole more than 50,000 emails of Hillary Clinton’s campaign chairman, an audacious electronic attack blamed on Russia’s government and one that has resulted in embarrassing political disclosures about Democrats in the final weeks before the U.S. presidential election.
The hackers sent John Podesta an official-looking email on Saturday, March 19, that appeared to come from Google. It warned that someone in Ukraine had obtained Podesta’s personal Gmail password and tried unsuccessfully to log in, and it directed him to a website where he should “change your password immediately.”
Podesta’s chief of staff, Sara Latham, forwarded the email to the operations help desk of Clinton’s campaign, where staffer Charles Delavan in Brooklyn, New York, wrote back 25 minutes later, “This is a legitimate email. John needs to change his password immediately.”
But the email was not authentic.
On the mechanisms used: “…each of the e-mail messages from the August attacks contained a Microsoft Office Word (.doc) or Excel (.xls) attachment. These attachments, when viewed, contained legitimate report content from each of the organizations they appeared to have been sent from. However, the attackers inserted macros into the documents designed to install a malware downloader on the system… Volexity has dubbed this backdoor PowerDuke.”
Why weren’t the macro actions flagged as attacking malware? If this was all known during the campaigns, why wasn’t it countered via malware definitions updates? I’d think that the attacked parties would have been very careful about having proper AV protection via updates.
Antivirus and Antimalware frequently work by looking for signatures of samples known to be malicious. Unfortunately, coverage (like what you get with a flu vaccine) is achieved by distributing the signatures to all clients. Anyone planning to distribute malicious software first adjusts their software such that it doesn’t match the current signatures. There are even sites people use to verify their malicious code isn’t detected.
There are a number of methods to avoid detection, for a while such software tended to use compression and encryption.I’m not sure what the state of the art is today.
Russians have been hacking, as have Chinese.
This doesn’t mean Russia is hacking, nor China.
Yes it’s politically convenient to blame “RUSSIA”, but the fact the hackers are in Russia is coincidence.
Until I see proof that the hackers are working for Russia instead of themselves…this is a non-story..other than to be certain not to open any emails that arrive from john.podesta@clintonemail.com
They are definitely in Russia, China, Ukraine, France, Vietnam, South Korea, and the US. I’ve got probably 12MB of saved emails with whois information from fail2ban over two years, on attacks from those origin countries. Mostly from SSH attacks trying root, admin, ubnt, support for the most part, and a few other odd accounts. IMHO, the Chinese ones are probably state sponsored due to origin, and possibly the Vietnam ones also as a proxy for China. The rest appear to be botnets correlated by timing and account attempts. Sadly I can’t log passwords tried because that would help see what they are using…
I fully agree, Eric R. Being a Russian hacker doesn’t mean you represent the Russian government.
Tell, ’em Brian. Most hackers are in the US .
Does that mean all those hackers are working for the United States government? Or are they con artists trying to make a fast buck?
U dont see evidence couse they flush….
Tgey good at flushing… flush flush
Lol..
What they did put jail some alcholics and said this man is behind all the crimes lol
Its same like drug trade…small criminals in prison lol
In rusdiaand ukraine money can buy everything..so no punishment for rich.
Hello Brian, we can’t say if the scam comes from the Russian Group. But what we know is that the Phishing e-mails look the same as our own best practice DIY phishing simulation templates which we provide together with LUCY Server! Obviously the cyber criminals are using best practices too: Our customers and partners say that the eFax Attack is a scenario with a high penetration rate! See our article on http://www.lucysecurity.com/phishing-cozy-bear-post-election-simulation/
I respect you Brian, however by using the term “presumptive president-elect”, you are conveying subtle undertones that Trump was not proven to be elected. Let’s take politics out of your articles and just get to the facts. Using those terms only ends up distracting from the main point of the article.
Brian was correct using “presumptive president-elect”. Donald Trump will not be elected President until the electoral college votes. So it was not a political statement, but one of fact.
And the truth shall make you free, except if you are an American citizen, among others. Then you seek asylum in Russia. So don’t do or say anything on line you wouldn’t want attributed to yourself, seen on the evening news, or seen on the front page of the newspaper, as long as those last. Although Mrs. Clinton did capitulate, what with all the shenanigans thus far in this election, nothing would surprise me. I sure am hoping for some younger blood next time around. Too bad old Bernie didn’t go down swinging though. After him The Donald will have to do. Haters gonna hate, what better way to fool those gullible Americans. Having a good reason to believe that something is true means that it is presumptive.
Why do people do crazy, off the wall stuff?
To make money? Who has the money? Snowden or the people he exposed?
To get power? Who has power? Snowden or the Bush/Cheney crowd?
To be admired? Who does the media condemn daily and who is on the fast track to being sent to jail for 30+ years? Bush et al or Snowden?
To reveal the truth? The neolib silence is deafening.
Writeup on the drop top disk method used in the volexity article.
https://penetrate.io/
I don’t like what’s happening now at days. If I have to dig into other peoples data, I would. And I did contact codekhakerR_U at protonmail dotcom and he has helped me with so much. There are many ways to succeed in life!
I’d hoped that Brian wouldn’t fall into this.
The FACT is this scheme was set to go into motion no matter who won.
Nobody “pounced” on anything. This was a predetermined course of action with both outcomes scripted.
But hey…. nothing grabs clicks like a good Trumpet bashing.
Russian Hackers Target NGOs with Clinton Foundation Emails
http://www.infosecurity-magazine.com/news/russian-hackers-target-ngos/
BOTTOM LINE, in 2016 – if you open an email with a zip attachment, extract the zip and run an .exe file – you need to throw away your computer, have yourself sterilized so you cannot reproduce, strap yourself to a rocket and launch yourself at the sun.