KrebsOnSecurity recently featured the story of a Brazilian man who was peppered with phishing attacks trying to steal his Apple iCloud username and password after his wife’s phone was stolen in a brazen daylight mugging. Today, we’ll take an insider’s look at an Apple iCloud phishing gang that appears to work quite closely with organized crime rings — within the United States and beyond — to remotely unlock and erase stolen Apple devices.
Victims of iPhone theft can use the Find My iPhone feature to remotely locate, lock or erase their iPhone — just by visiting Apple’s site and entering their iCloud username and password. Likewise, an iPhone thief can use those iCloud credentials to remotely unlock the victim’s stolen iPhone, wipe the device, and resell it. As a result, iPhone thieves often subcontract the theft of those credentials to third-party iCloud phishing services. This story is about one of those services.
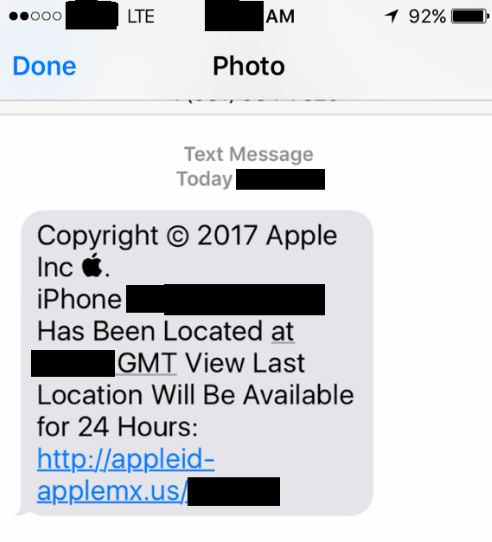
Recently, I heard from a security professional whose close friend received a targeted attempt to phish his Apple iCloud credentials. The phishing attack came several months after the friend’s child lost his phone at a public park in Virginia. The phish arrived via text message and claimed to have been sent from Apple. It said the device tied to his son’s phone number had been found, and that its precise location could be seen for the next 24 hours by clicking a link embedded in the text message.
That security professional source — referred to as “John” for simplicity’s sake — declined to be named or credited in this story because some of the actions he took to gain the knowledge presented here may run afoul of U.S. computer fraud and abuse laws.
John said his friend clicked on the link in the text message he received about his son’s missing phone and was presented with a fake iCloud login page: appleid-applemx[dot]us. A lookup on that domain indicates it is hosted on a server in Russia that is or was shared by at least 140 other domains — mostly other apparent iCloud phishing sites — such as accounticloud[dot]site; apple-appleid[dot]store; apple-devicefound[dot]org; and so on (a full list of the domains at that server is available here).
While the phishing server may be hosted in Russia, its core users appear to be in a completely different part of the world. Examining the server more closely, John noticed that it was (mis)configured in a way that leaked data about various Internet addresses that were seen recently accessing the server, as well as the names of specific directories on the server that were being accessed.
After monitoring that logging information for some time, my source discovered there were five Internet addresses that communicated with the server multiple times a day, and that those address corresponded to devices located in Argentina, Colombia, Ecuador and Mexico.
He also found a file openly accessible on the Russian server which indicated that an application running on the server was constantly sending requests to imei24.com and imeidata.net — services that allow anyone to look up information about a mobile device by entering its unique International Mobile Equipment Identity (IMEI) number. These services return a variety of information, including the make and model of the phone, whether Find My iPhone is enabled for the device, and whether the device has been locked or reported stolen.
John said that as he was conducting additional reconnaissance of the Russian server, he tried to access “index.php” — which commonly takes one to a site’s home page — when his browser was redirected to “login.php” instead. The resulting page, pictured below, is a login page for an application called “iServer.” The login page displays a custom version of Apple’s trademarked logo as part of a pirate’s skull and crossbones motif, set against a background of bleeding orange flames.
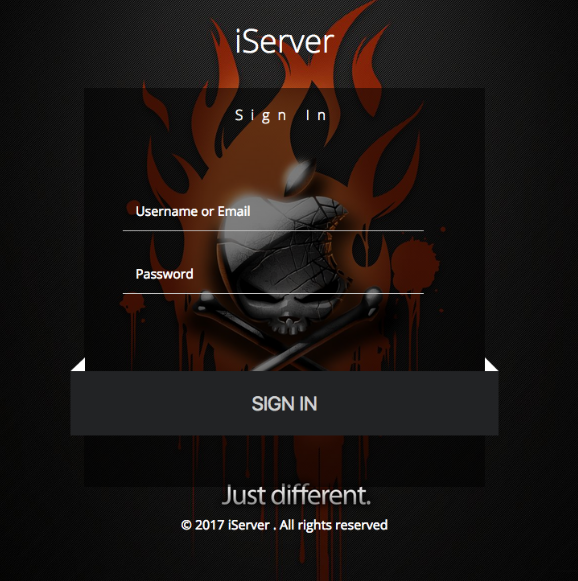
The login page for an Apple iCloud credential phishing operation apparently used to unlock and remotely wipe stolen iPhones.
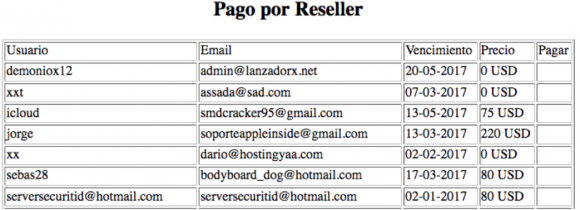
John told me that in addition to serving up that login page, the server also returned the HTML contents of the “index.php” he originally requested from the server. When he saved the contents of index.php to his computer and viewed it as a text file, he noticed it inexplicably included a list of some 137 user names, email addresses and expiration dates for various users who’d apparently paid a monthly fee to access the iCloud phishing service.
“These appear to be ‘resellers’ or people that have access to the crimeware server,” my source said of the user information listed in the server’s “index.php” file.
John told KrebsOnSecurity that with very little effort he was able to guess the password of at least two other users listed in that file. After John logged into the iCloud phishing service with those credentials, the service informed him that the account he was using was expired. John was then prompted to pay for at least one more month subscription access to the server to continue.
Playing along, John said he clicked the “OK” button indicating he wished to renew his subscription, and was taken to a shopping cart hosted on the domain hostingyaa[dot]com. That payment form in turn was accepting PayPal payments for an account tied to an entity called HostingYaa LLC; viewing the HTML source on that payment page revealed the PayPal account was tied to the email address “admin@hostingyaa[dot]com.”
According to the file coughed up by the Russian server, the first username in that user list — demoniox12 — is tied to an email address admin@lanzadorx.net and to a zero-dollar subscription to the phishing service. This strongly indicates the user in question is an administrator of this phishing service.
A review of Lanzadorx[dot]net indicates that it is a phishing-as-a-service offering that advertises the ability to launch targeted phishing attacks at a variety of free online services, including accounts at Apple, Hotmail, Gmail and Yahoo, among others.
A reverse WHOIS lookup ordered from Domaintools.com shows that the admin@lanzadorx.net email is linked to the registration data for exactly two domains — hostingyaa[dot]info and lanzadorx[dot]net [full disclosure: Domaintools is currently one of several advertisers on KrebsOnSecurity].
Hostingyaa[dot]info is registered to a Dario Dorrego, one of the other zero-dollar accounts included near the top of the list of users that are authorized to access the iCloud phishing service. The site says Dorrego’s account corresponds to the email address dario@hostingyaa[dot]com. That name Dario Dorrego also appears in the site registration records for 31 other Web site domains, all of which are listed here.
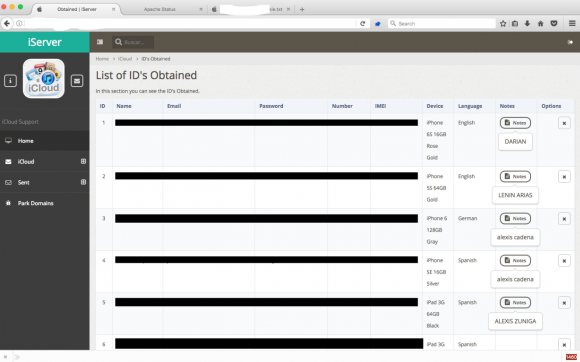
John said he was able to guess the passwords for at least six other accounts on the iCloud phishing service, including one particularly interesting user and possible reseller of the service who picked the username “Jonatan.” Below is a look at the home screen for Jonatan’s account on this iCloud phishing service. We can see the system indicates Jonatan was able to obtain at least 65 “hacked IDs” through this service, and that he pays USD $80 per month for access to it.
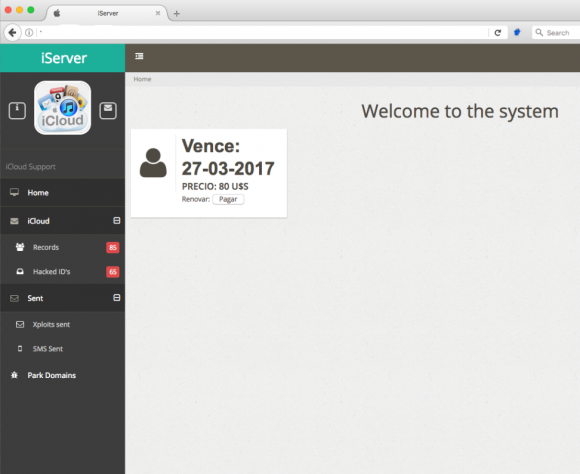
“Jonatan,” a user of this iCloud account credential phishing service. Note the left side panel indicates the number of records and hacked IDs recorded for Jonatan’s profile.
Here are some of the details for “Tanya,” one such victim tied to Jonatan’s account. Tanya’s personal details have been redacted from this image:
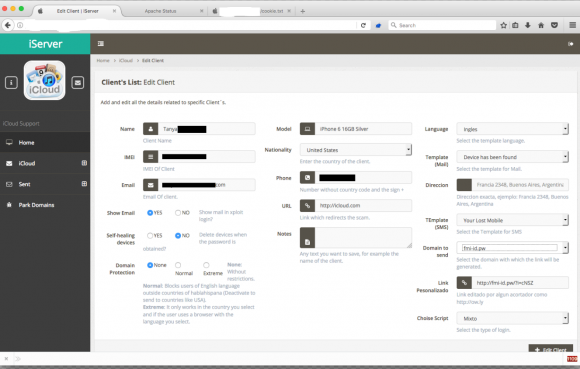
This page from the iCloud phishing service shows the redacted account details phished from an iPhone user named Tanya.
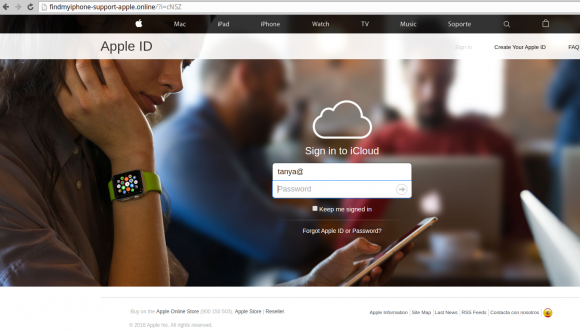
Here is the iCloud phishing page Tanya would have seen if she clicked the link sent to her via text message. Note that the victim’s full email address is automatically populated into the username portion of the login page to make the scam feel more like Apple’s actual iCloud site:
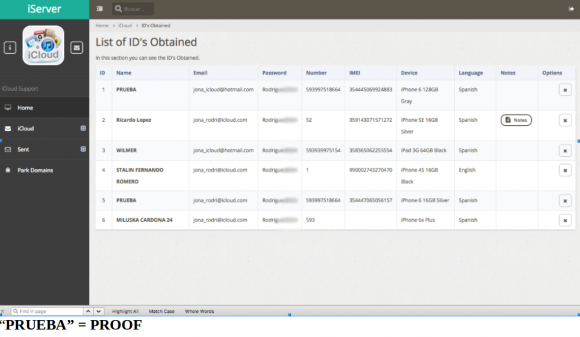
The page below from Jonatan’s profile lists each of his 60+ victims individually, detailing their name, email address, iCloud password, phone number, unique device identifier (IMEI), iPhone model/generation and some random notes apparently inserted by Jonatan:
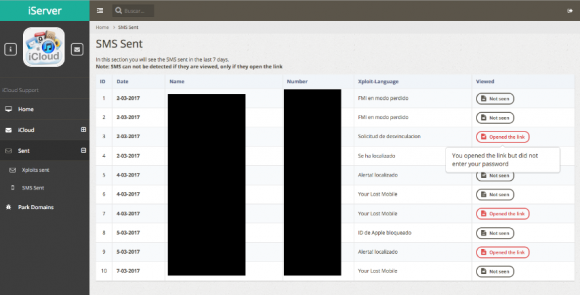
The next screen shot shows the “SMS sent” page. It tracks which victims were sent which variation of phishing scams offered by the site; whether targets had clicked a link in the phony iCloud phishing texts; and if any of those targets ever visited the fake iCloud login pages:
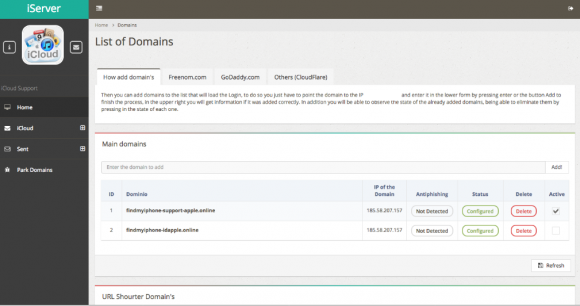
Users of this phishing service can easily add a new phishing domain if their old links get cleaned up or shut down by anti-phishing and anti-spam groups. This service also advertises the ability to track when phishing links have been flagged by anti-phishing companies:
This is where the story turns both comical and ironic. Many times, attackers will test their exploit on themselves whilst failing to fully redact their personal information. Jonatan apparently tested the phishing attacks on himself using his actual Apple iCloud credentials, and this data was indexed by Jonatan’s phishing account at the fake iCloud server. In short, he phished himself and forgot to delete the successful results. Sorry, but I’ve blurred out Jonatan’s iCloud password in the screen shot here:
See if you can guess what John did next? Yes, he logged into Jonatan’s iCloud account. Helpfully, one of the screenshots in the photos saved to Jonatan’s iCloud account is of Jonatan logged into the same phishing server that leaked his iCloud account information!
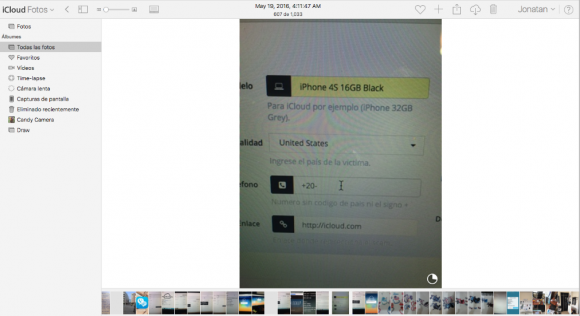
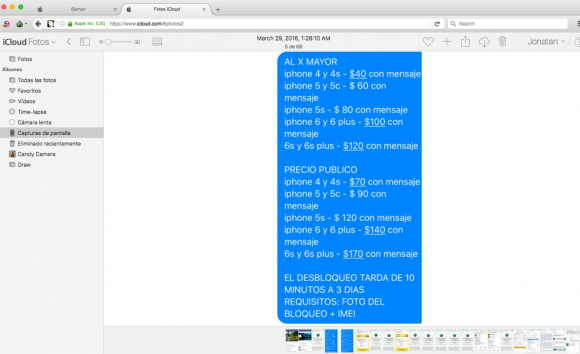
The following advertisement for Jonatan’s service — also one of the images John found in Jonatan’s iCloud account — includes the prices he charges for his own remote iPhone unlocking service. It appears the pricing is adjusted upwards considerably for phishing attacks on newer model stolen iPhones. The price for phishing an iPhone 4 or 4s is $40 per message, versus $120 per message for phishing attacks aimed at iPhone 6s and 6s plus users. Presumably this is because the crooks hiring this service stand to make more money selling newer phones.
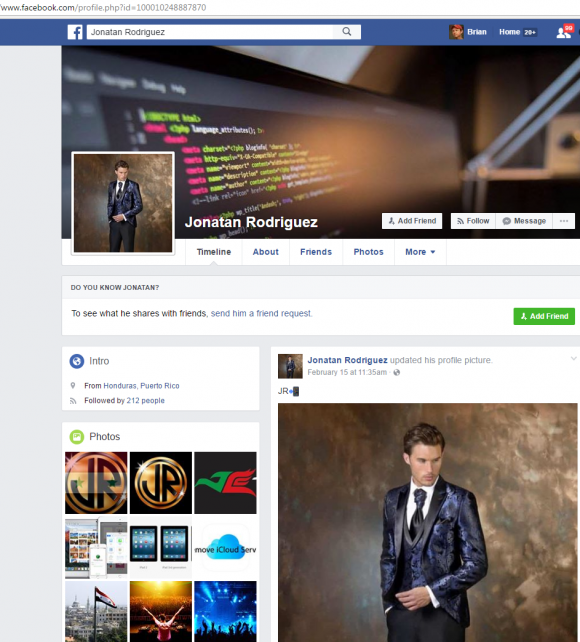
The email address that Jonatan used to register on the Apple iPhone phishing service — shown in one of the screen shots above as jona_icloud@hotmail.com — also was used to register an account on Facebook tied to a Jonatan Rodriguez who says he is from Puerto Rico. It just so happens that this Jonatan Rodriguez on Facebook also uses his profile to advertise a “Remove iCloud” service. What are the odds?
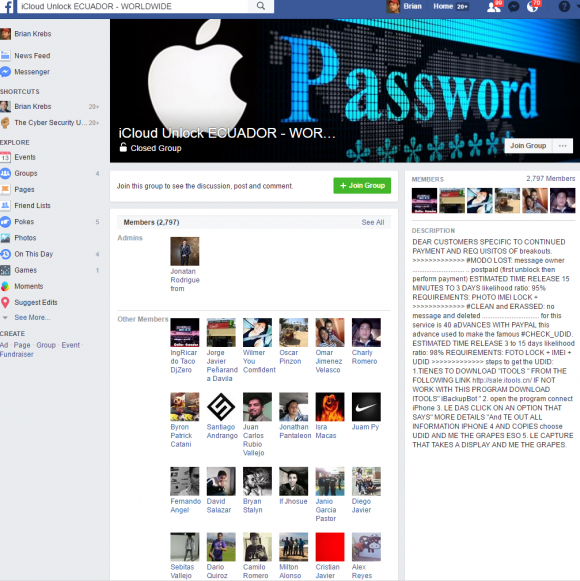
Well, pretty good considering this Facebook user also is the administrator of a Facebook Group called iCloud Unlock Ecuador – Worldwide. Incredibly, Facebook says there are 2,797 members of this group. Here’s what they’re all about:
Jonatan’s Facebook profile picture would have us believe that he is a male model, but the many selfies he apparently took and left in his iCloud account show a much softer side of Jonatan:
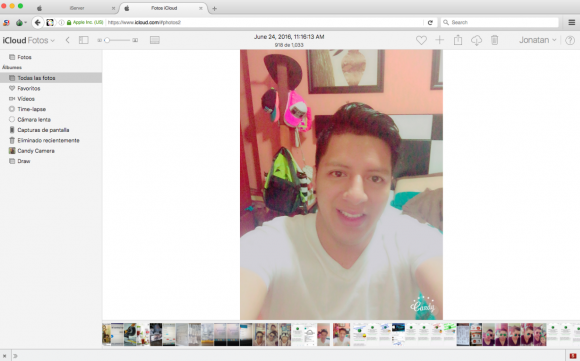
Jonatan, in a selfie he uploaded to his iCloud account. Jonatan unwittingly gave away the credentials to his iCloud account because the web site where his iCloud account phishing service provider was hosted had virtually no security (nor did Jonatan, apparently). Other photos in his archive include various ads for his iPhone unlocking service.
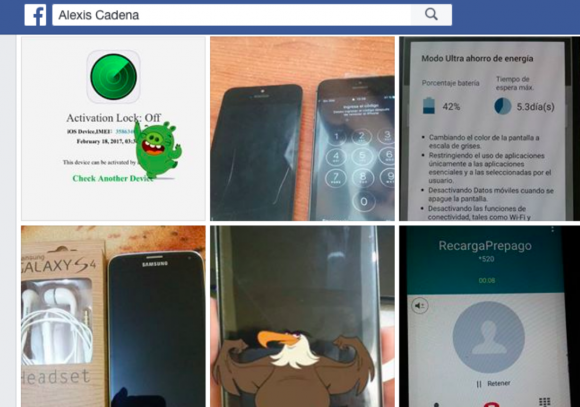
Among the members of this Facebook group is one “Alexis Cadena,” whose name appears in several of the screenshots tied to Jonatan’s account in the iCloud phishing service:
Alexis Cadena apparently also has his own iCloud phishing service. It’s not clear if he sub-lets it from Jonatan or what, but here are some of Alexis’s ads:
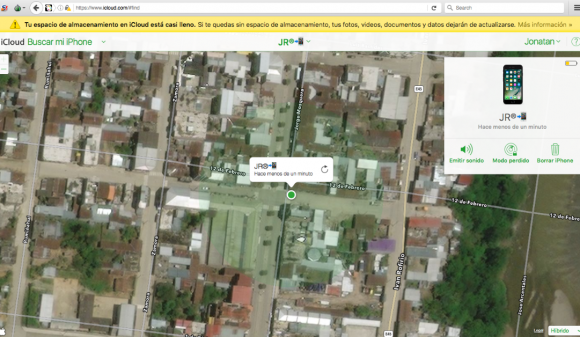
Coming back to Jonatan, the beauty of the iCloud service (and the lure used by Jonatan’s phishing service) is that iPhones can be located fairly accurately to a specific address. Alas, because Jonatan phished his own iCloud account, we can see that according to Jonatan’s iCloud service, his phone was seen in the following neighborhood in Ecuador on March 7, 2017. The map shows a small radius of a few blocks within Yantzaza, a town of 10,000 in southern Educador:
Jonatan did not respond to multiple requests for comment.





Another fascinating read. Great sleuthing, John and Brian, way to go!
Thank you for this article! I’ve shared it. Informative and super scary. So easy to do. I would have fallen for it.
My sister fell victim to a similar phishing scheme when she had her phone stolen in a shopping centre.
I informed her not to do anything (respond to any emails etc), but unfortunately she couldn’t resist when she got an email saying her phone had been located in Johannesburg.
Safe to say that phone was never seen again….
Good stuff as usual. I bet when he gets wind of this article he will be pooping in his pants and claiming he has been hacked!
Really? tgats a lot efforts ….c mon fraudsters there is some better ways to make money. Thats insane.like this is nonsense.
and how much money they gona get from this bs ?
I dont think its enought.
i have great question!!! Wtf…guys smart talented people waste their btain and skills for nonsense like this ?????
need to make money not baby money
Thank you for this really interesting article!
Great article. Lost my phone in Mexico and have been getting these messages for weeks. The next question is: what can I do to stop the messages?
Use the Block Sender feature. When text is opened (similar for phone calls), there is a little “i” in the upper right. Tap it. On new page, where sender’s info is displayed is a “>”. Tap it. Then from sender’s card choose “Block Caller/Sender”. Keep doing to every pishing text. Eventually they will run out of numbers to contact you with, or over the long run lose interest.
great article
If all criminals were as careless they would put themselves out of business. Good work again, this site will just move though and hopefully have another lazy stupid user.
It’s that same mindset we see time and time again. “I are smarter than everyone else. No one is ever good enough to catch me.” No matter how good you think you are, there is always someone better.
Do these criminals operate in Columbia, Missouri or Columbia, South Carolina?
I understood the article as Colombia, South American nation-state.
How does this fake AppleID page interplay with Apples 2FA?
Speculating:
– if the victim doesn’t have 2SA/2FA enabled, it is a straight capture of u/n and p/w ;
– if either 2SA/FA are enabled, it would seem trivial for the miscreants to spoof the 2FA map and PIN pop-ups (or more frighteningly, not spoof at all because most victims probably don’t expect these pop ups so never note their absence.)
Seems to me that we are looking at the “petty” theft insult and overlooking the major injury these well-organized perps are capable of visiting upon their victims because IMHO (and assuming that Apple doesn’t have some secondary verificarion features unknown to me) the real risk here is NOT that your iPhone gets unlocked and sold, its that with a bit of real-time coordination, the criminals could pish the 2FA PIN code sent by Apple to a victim’s other trusted devices (assuming they have more than one device connected to their iCloud account and they use that device to log into their AppleID page.)
If a perp can gain entry to a victim’s iCloud Keychain (via these social engineering methods), either directly on the stolen device, or by adding another device into the victim’s constellation of trusted devices, then the perp would have access to all of the victim’s accounts, u/n and p/w authentication data.
It would be nice to see more discussion of the above points and concerns.
In the meantime, everybody, including iCloud Keychain users like myself, would be well advised to enable 2FA everywhere possible (see twofactorauth dot org*, or turnon2fa dot com ) and to pay strict attention to the domain part of any site address you go to to deal with credentials or lost devices.
* also has buttons which you can use to lobby companies, via tweet or email, by asking them to offer 2FA.
I nearly fell for a scam, not the stolen iPhone scam but a simple legit looking apple ID email sent to my email, which I use often and very rarely get spam too. Safe to say as soon as I saw the URL in Safari I exited quicker than you can say ‘iPhone scam’.
Maybe you already know this but if not:
– in iOS, you can see the actual domain behind a hyperlink (iirc also bitly shortened hyperlinks) by holding your finger on the link and waiting for a box to pop up. The box will then display the full address and offer options from open to cancel.)
Since the average person knows nothing about url’s……how would people know how to decifer this one in such a way to know if it’s good or bad?
https://www.google.com/maps/place/Iv%C3%A1n+Riofr%C3%ADo,+Yantzaza,+Ecuador/@-3.825873,-78.7681746,16z/data=!4m5!3m4!1s0x91cb7a0841760e33:0xbd8c4992b7922555!8m2!3d-3.8301121!4d-78.7605786
Mike, since you insist on reposting this question which ruins the sidebar, allow me to answer it. Starting from the left side of the link, you look for the first backslash “/” after the “www:” and work right to left from there. The domain immediately to the left is the domain where the click will take you.
Unless there’s an open redirect at — in this case, Google.com — in which case all bets are off.
I’m sorry it messes with the side bar. I consider it a valid question. I’m not looking for an explanation of it. I understand it. But most people are not going to. Allowances must be made for the broader scope of visitors and readers.
FYI: A bit of css would fix that for most users. Check out the word-wrap property (word-wrap was renamed to overflow-wrap, but the new name isn’t as broadly supported as the old).
Mike, it’s fine. I actually had fun thinking that one through, as I realized I hadn’t explained this to readers before exactly.
Not a bad explanation. I’m glad you covered the risk of open redirects.
Note that there are a couple of other problems:
1. Someday someone will get a Punicode domain that looks like it has a slash, but where that’s actually not an ASCII slash, and this is still part of the domain.
2. Someone will use Punicode with bidirectional text to make it very very hard for someone to use their eyes to calculate character order. (Arabic and Hebrew and some others normally write their letters from right to left, but they write grouped numbers 0-9 from left to write asking with stole punctuation– which means that browsers flip runs of text around according to very complicated rules)
3. Just being able to figure out which part of a URL is the domain isn’t particularly helpful if you can’t figure out if the distinct is trustworthy. (Is Apple.mx trustworthy? Apple.store?)
4. In addition to open redirects, there are of course cases where a sure has been hacked (either secretly such that foreign software is running on it, out mildly such that it’s serving some injected content).
5. If the URL isn’t https, then if there’s a MITM attack, that attacker could redirect the content anywhere or replace the content with anything. — here’s a good place to note that Google just released an automatic VPN for its later version of Android.
/ is not a backslash; \ is a backslash.
In short: you can’t. It’s essentially impossible:
Even if a site is using https, and no one is highjacking BGP/DNS, and the site was checked yesterday and found not to be evil, nothing prevents it from being hacked/injected right before your visit.
Projection comes from:
1. Updating your operating system to the latest supported version.
2. Updating your web browser to the latest supported version.
3. Ensuring your hardware isn’t vulnerable/obsolete
4. Not entering data that could be compromising.
5. Performing out of band checks before providing information.
6. Enabling 2FA everywhere.
7. Using very long (20+) random passwords that are unique for each account.
8. Never acting is response to a panic induced situation (otherwise, your brain tends to overlook red flags).
Update: I was wrong about link shorteners, unfortunately iOS does not expand them. Also, thanks to Brian below for explaining how to read/verify a domain name address.
Actually thank you, I did know that. I use a 3rd party app for my mail and have done ever since I’ve had an iPhone. You can click and hold on the link and it will show it without opening it. In this instance, I didn’t and I should have. My mistake really.
Fascinating in one way how organized they are using presumably bulletproof hosting in Russia and a full on web application to do this, I wonder where that’s got – the deep web?
I also wonder how much money they made from this. Imagine the admin – assuming he’s reselling it for $80 to 100 people that’s $8k per month for just hosting an application, perhaps with minimal costs of sending SMS messages. Not bad..
And the users of this, it’s funny how they advertise themselves in the open as a white-hat type of service. I guess some could be making more than 8k/month reselling the service. They could be running online ad campaigns or posting on classified ads sites, who knows.
$8k/month they’d live like kings in their countries, I imagine they don’t pay tax on that.
Quite entrepreneurial but what comes around goes around.
Well written as always, Brian. As a student, I find reading articles like this really helps me learn.
How are they getting the details of who owns the phone and related contact info, if the found/stolen phone is locked?
Often people send a message in case it was just lost and folks want to return it – giving a phone number etc..
Then they can send you these links to try and phish your iCloud ID.
https://krebsonsecurity.com/2017/02/iphone-robbers-try-to-iphish-victims/
Totally awesome Mr. Krebs – what an article.
Too bad Jonatan didn’t reside in the U.S. or the fuzz would be coming down on him shortly. Amazing how these bozos have been trying, somewhat successfully, to get around Apple’s smartphone locks…
The article was very interesting. Liked the obvious tracking ability. The redirects to cover. Legally, I would wonder what jurisdiction he would fall under.
About the browsers, all the major browsers allow previewing of the embeds. Same with the email readers allowing full header view. It’s just a matter of finding the switch and allow viewing. They all have different terms for that view.
Great job again Brian. I hope you sent this info to the Ecuadorian authorities. Until kids like these start spending some serious time in jail, these scams will continue to grow. I work for a (let’s say “very large”) security company and every time I see Brian pinpoint these miscreants, I check to make sure our company has not actually hired one of these morality free cheats.
Thank you for this, Brian! It was, indeed, a great read. Good work!
May be a dumb question, but I know nothing about iPhone’s ..could the thieves themselves not just use the “erase your device with recovery mode” technique in the link below for bypassing the passcode, negating the need for remote unlocking?
https://support.apple.com/en-us/HT204306
Someone correct me if I am wrong, but I think the first thing after you do that is to log in with the account the phone is slaved to.
It’s a good question, and I would venture a guess that the answer is in the first sentence: “If you’ve never synced with iTunes or set up Find My iPhone in iCloud, you’ll need to use recovery mode to restore your device.”
I’ve never tried to unlock a stolen iPhone, but I’d bet that if it had ever been synced with iTunes or set up with Find My iPhone in iCloud, you won’t be able to use this method.
That will not work.
iCloud credentials are required when setting up a new iDevice. Find My iPhone is enabled by default. I would guess that 95% of iPhones are cloud locked.
Basically thieves are SOL hence these shady “services”. I wonder if Android has anything remotely comparable. It seems that with Android you just unlock bootloader and do whatever you want with device.
NB If you (like me) are not comfortable about privacy, GPS access can be revoked for Find My iPhone while leaving Find My iPhone on. That will ensure that device is cloud locked. You won’t be able to GPS locate it via icloud.com but all other Find My iPhone features (like display message in screen, see last time it was on) will work.
Do you happen to know what year was Jonatan born? Just for… academic, purposes.
That was a fun read. Thank you!
Was there any attempt to have law enforcement follow up on this? (I know, it is to laugh….)
When you read one of these, and get to the end, you almost want to jump out of your seat clapping as if Brian was on stage and just got finished a very tricky part on the violin !
Thanks for a great article. I’m always further educated by the items posted here. Thank you to “John” for sharing what he found out.
Great story!
A hat tip to the researcher for the great amount of self control it must have taken not to “Remote Wipe” Jonatan’s iPhone – after changing Jonatan’s iCloud password of course. I’m not sure that I could have resisted.
Great coverage! Great job Brian and great job “John”.
Best live EVAR
“Jonatan did not respond to multiple requests for comment.”
People in these comments occasionally ask about why someone would waste such talent on criminal activity. It’s not surprising that scumbags like Rodriguez and Cadena waste talent by engaging in extortion rackets like this because it’s not about the talent. It’s about personality. These people see us as commodities, not as humans. In the straight world, the legal parallel is usually in corporations, like Apple for example, that view their customers as money trees that exist FOR the corporation (Peter Drucker’s fascism in the business world), rather than the business existing to serve the customer. In the criminal world, the only difference is that the enterprise itself is illegal. Listening to my law enforcement acquaintances, some people are just scum, period. Joe Navarro’s book, Dangerous Personalities, is a lay-level enlightenment along these lines, but I digress twice now.
Back to scumbags and how this isn’t about talent, take an old acquaintance of mine for example. We’ll call him Allen or Bryce or Carl, or just ABC. Mr. ABC is a talented kid. He was also conniving and selfish. He viewed everything through “The Art of War.” I mean everything! There was nothing where you could actually relate with him that he didn’t try to turn into a competition. It was pretty sick. Sure, some people are competitive, but this was combined with a mentality that was, “If I can do it, then both it IS ethical AND I should do it.” His upbringing kept him clean, looking like a “good boy,” but he treated others as test machines, play things. This is the definition of a monster. Out of college, he eventually moved to Hawaii, got married, and later got hired by the FBI. I think he’s a plain employee, not an agent and not a contractor. His clean upbringing, staying off drugs, and knowing how to game people in order to look good, all paid off.
ABC & I weren’t so close, but stopped getting along at some point before he left town. Whatever very minor disagreement that was, our mutual friends (who wre much closer to ABC than I was) agreed he was in the wrong for behavior and attitude. So, he started hating me, I’m told. I didn’t notice. He’s the kind of guy I don’t trust to remember that I exist. And by that, I mean that if he remembers I exist, i can see him using his position at the FBI to track me IF and ONLY IF he thinks he could hide it and get away with it. See, disliking me isn’t enough. Disliking me makes me a target for being played with by someone with a Competitive Overlord complex like ABC has.
So, about 18 months ago, I was chatting with an older friend who knew ABC and his peers. They’re all slightly younger than me. ABC had been to a backyard bbq type party shortly before the older guy and I chatted. ABC was “running around” telling people, “no photographs,” and, “no social media.” Ok, I don’t want to be on facebook either, in any form. My older buddy explained. The issue wasn’t facebook photos per se. The issue was that he wasn’t supposed to be drinking AT ALL under the terms of his employment with the FBI. ABC wasn’t concerned with being honest or trustworthy, nor honoring others. He was concerned with getting caught.
There are scumbags everywhere. This is an example of someone like the guys we read about on Mr. Kreb’s blog, except in a “straight” job. Thanks for reading. I hope Mr. ABC never thinks of me again.
I agree with your assessment. I’ve noticed a several times that many of the miscreants that Krebs has reported on started off by cheating at games, moving to hacking game servers, then to exploiting people in other ways as they discover opportunities.
I liken it to mentally ill with excessive greed. The same illness that brings many people to dominant positions in companies and politics.
So if this article were the first half of a “Scorpion” episode, what would the second half be? Let’s see, Jonatan turns out to be the unwilling pawn of Ecuadorian strongman Juan Valdez, who is holding Jonatan’s 12-year-old sister hostage in (coincidentally) Los Angeles. The team uses some technical razzle-dazzle to find Valdez and lure him to an empty warehouse (or maybe an airplane hangar, yeah) where there is a tense confrontation, verbal sparring, and one last techie twist involving using his own scheme against him that leaves Valdez in FBI custody and Jonatan reunited with his sister.
Almost writes itself.