Last month Yours Truly got snookered by a too-good-to-be-true online scam in which some dirtball hijacked an Amazon merchant’s account and used it to pimp steeply discounted electronics that he never intended to sell. Amazon refunded my money, and the legitimate seller never did figure out how his account was hacked. But such attacks are becoming more prevalent of late as crooks increasingly turn to online crimeware services that make it a cakewalk to cash out stolen passwords.

The elusive Sonos Play:5
The item at Amazon that drew me to this should-have-known-better bargain was a Sonos wireless speaker that is very pricey and as a consequence has hung on my wish list for quite some time. Then I noticed an established seller with great feedback on Amazon was advertising a “new” model of the same speaker for 32 percent off. So on March 4, I purchased it straight away — paying for it with my credit card via Amazon’s one-click checkout.
A day later I received a nice notice from the seller stating that the item had shipped. Even Amazon’s site seemed to be fooled because for several days Amazon’s package tracking system updated its progress slider bar steadily from left to right.
Suddenly the package seemed to stall, as did any updates about where it was or when it might arrive. This went on for almost a week. On March 10, I received an email from the legitimate owner of the seller’s account stating that his account had been hacked.
Identifying myself as a reporter, I asked the seller to tell me what he knew about how it all went down. He agreed to talk if I left his name out of it.
“Our seller’s account email address was changed,” he wrote. “One night everything was fine and the next morning our seller account had a email address not associated with us. We could not access our account for a week. Fake electronic products were added to our storefront.”
He couldn’t quite explain the fake tracking number claim, but nevertheless the tactic does seem to be part of an overall effort to delay suspicion on the part of the buyer while the crook seeks to maximize the number of scam sales in a short period of time.
“The hacker then indicated they were shipped with fake tracking numbers on both the fake products they added and the products we actually sell,” the seller wrote. “They were only looking to get funds through Amazon. We are working with Amazon to refund all money that were spent buying these false products.”
As these things go, the entire ordeal wasn’t awful — aside maybe from the six days spent in great anticipation of audiophilic nirvana (alas, after my refund I thought better of the purchase and put the item back on my wish list.) But apparently I was in plenty of good (or bad?) company.
The Wall Street Journal notes that in recent weeks “attackers have changed the bank-deposit information on Amazon accounts of active sellers to steal tens of thousands of dollars from each, according to several sellers and advisers. Attackers also have hacked into the Amazon accounts of sellers who haven’t used them recently to post nonexistent merchandise for sale at steep discounts in an attempt to pocket the cash.”
Perhaps fraudsters are becoming more brazen of late with hacked Amazon accounts, but the same scams mentioned above happen every day on plenty of other large merchandising sites. The sad reality is that hacked Amazon seller accounts have been available for years at underground shops for about half the price of a coffee at Starbucks.
The majority of this commerce is made possible by one or two large account credential vendors in the cybercrime underground, and these vendors have been collecting, vetting and reselling hacked account credentials at major e-commerce sites for years.
I have no idea where the thieves got the credentials for the guy whose account was used to fake sell the Sonos speaker. But it’s likely to have been from a site like SLILPP, a crime shop which specializes in selling hacked Amazon accounts. Currently, the site advertises more than 340,000 Amazon account usernames and passwords for sale.
The price is about USD $2.50 per credential pair. Buyers can select accounts by balance, country, associated credit/debit card type, card expiration date and last order date. Account credentials that also include the password to the victim’s associated email inbox can double the price.
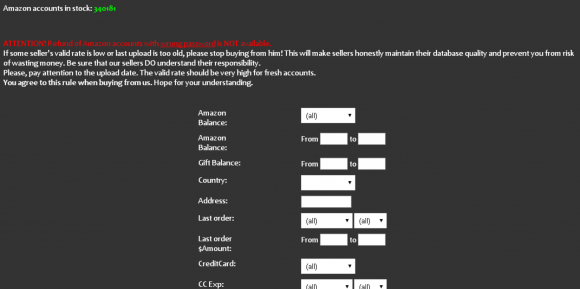
The Amazon portion of SLILPP, a long-running fraud shop that at any given time has hundreds of thousands of Amazon account credentials for sale.
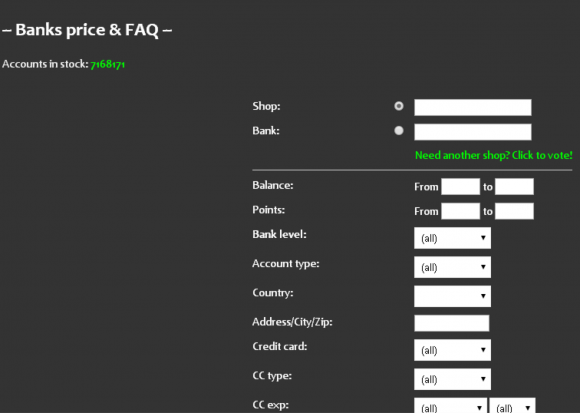
If memory serves correctly, SLILPP started off years ago mainly as a PayPal and eBay accounts seller (hence the “PP”). “Slil” is transliterated Russian for “слил,” which in this context may mean “leaked,” “download” or “to steal,” as in password data that has leaked or been stolen in other breaches. SLILPP has vastly expanded his store in the years since: It currently advertises more than 7.1 million credentials for sale from hundreds of popular bank and e-commerce sites.
The site’s proprietor has been at this game so long he probably deserves a story of his own soon, but for now I’ll say only that he seems to do a brisk business buying up credentials being gathered by credential-testing crime crews — cyber thieves who spend a great deal of time harvesting and enriching credentials stolen and/or leaked from major data breaches at social networking and e-commerce providers in recent years.
Fraudsters can take a list of credentials stolen from, say, the Myspace.com breach (in which some 427 million credentials were posted online) and see how many of those email address and password pairs from the MySpace accounts also work at hundreds of other bank and e-commerce sites.
Password thieves often then turn to crimeware-as-a-service tools like Sentry MBA, which can vastly simplify the process of checking a list of account credentials at multiple sites. To make blocking their password-checking activities more challenging for retailers and banks, these thieves often try to route the Internet traffic from their password-guessing tools through legions of open Web proxies, hacked PCs or even stolen/carded cloud computing instances.
PASSWORD RE-USE: THE ENGINE OF ALL ONLINE FRAUD
In response, many major retailers are being forced to alert customers when they see known account credential testing activity that results in a successful login (thus suggesting the user’s account credentials were replicated and compromised elsewhere). However, from the customer’s perspective, this is tantamount to the e-commerce provider experiencing a breach even though the user’s penchant for recycling their password across multiple sites is invariably the culprit.
There are a multitude of useful security lessons here, some of which bear repeating because their lack of general observance is the cause of most password woes today (aside from the fact that so many places still rely on passwords and stupid things like “secret questions” in the first place). First and foremost: Do not re-use the same password across multiple sites. Secondly, but equally important: Never re-use your email password anywhere else.
Also, with a few exceptions, password length is generally more important than password complexity, and complex passwords are difficult to remember anyway. I prefer to think in terms of “pass phrases,” which are more like sentences or verses that are easy to remember.
If you have difficult recalling even unique passphrases, a password manager can help you pick and remember strong, unique passwords for each site you interact with, requiring only one strong master password to unlock any of them. Oh, and if the online account in question allows 2-factor authentication, be sure to take advantage of that.
I hope it’s clear that Amazon is just one of the many platforms where fraudsters lurk. SLILPP currently is selling stolen credentials for nearly 500 other banks and e-commerce sites. The full list of merchants targeted by this particularly bustling fraud shop is here (.txt file).
As for the “buyer beware” aspect of this tale, in retrospect there were several warning signs that I either ignored or neglected to assign much weight. For starters, the deal that snookered me was for a luxury product on sale for 32 percent off without much explanation as to why the apparently otherwise pristine item was so steeply discounted.
Also, while the seller had a stellar history of selling products on Amazon for many years (with overwhelmingly positive feedback on virtually all of his transactions) he did not have a history of selling the type of product that thieves tried to sell through his account. The old adage “If something seems too good to be true, it probably is,” ages really well in cyberspace.




For passwords, at a minimum you can use a scheme like commonString + unique-tokens. Make a string for example Ak48mK073K1j – commit that to memory. Modify it for various services, perhaps on MySpace you use MySpace#Ak48mK073K1j while for FB you use Ak48mK073K1j%FB.
This will protect you from a majority of attacks although an actual human reviewing your credentials might recognize the pattern and then try Ak48mK073K1j#bank at every online banking site they can think of to get into that account. This will still help you in the majority of cases because 1) the hashes for all your passwords will be unique so without an unencrypted password the attacker will have no chance of gaining access to other services that use a similar pass and 2) if a cybercriminal downloads a large list of credential pairs then employs a piece of software like the one mentioned above, it will not have the intuition to modify your password from service to service and will find no matches.
Lastly, the greater your need for security and the more services you use, the more common strings you should add. For example, the common string used for the wide variety of services I have at work is one thing, the one for low level accounts like social media crap is another, the one for financial accounts is another, and the one for my email is unique to my email.
A better solution (good password, but easier to remember) would be creating a diceware password and using that for your password manager and for any passwords you absolutely cannot afford to store anywhere, then leave it to the password manager to generate and store the rest of your passwords.
Evan, I respectfully disagree with your password – generation method.
If a cybercreep manages to get your MySpace#ayF2$dGhC password, you’re completely pwned. All the creep has to do is try Google#ayF2$dGhC and the rest, and will probably have some success.
The point of using different passwords on different services is to force the creeps to start over with their password-guessing. Be paranoid, because smart, motivated, and unscrupulous people are plotting against you.
As for Brian, if sixty of his readers give him ten bucks he can get that nice wireless speaker. Seriously. Can we do that for him?
In general, don’t use patterns. No matter how smart you (think :-)) you are, someone else will have come up with the *same* logic. And so have the crooks.
In fact that is the common method of hacking the last few years. Forget rainbow tables, brute cracking or dictionairies. Billions of passwords have been leaked and used to perfect the pattern matching algorithms.
Don’t use patterns!
Don’t take my word for it, but e.g. read up on the now already 2+ year old Ars Technica article.
Excellent point here. With databases linking all of these leaked accounts to identities, all it takes is two accounts to start seeing a pattern.
It’s still going on (checked today 04/21/17)… On multiple seller accounts (not one) and on almost every department. It happened to me twice and almost happened thrice (during this month alone), but now I keep a good eye… To avoid it: usually it’s the cheapest and it’s a “just launched” seller… Amazon does not seem to be doing anything about it. It’ been going on for a month (at least).
Wow…Thanks for this insightful article…Great work!
Amazing job
Brian – Thank you for your willingness to share your mistakes so that we can learn from them.
Paul
Happens to the best of us!
Glad your story had a reasonably happy ending.
Thanks for the heads-up.
A better solution is to take a password you know and remember and encode it with base 64. Then use that base 64 encoded password for your accounts
So the password “password123”
becomes
“cGFzc3dvcmQxMjM=”
There are already rainbow tables for encoded password strings, such as Base64 and uuencode.
Still nothing beats pure, random bits values–and lots of them.
Maybe you missed the part where Brian said “password length is generally more important than password complexity”
Yes you are right , when you use Base 64 encode you can get some real long password results from simple word combinations and numbers.
The complexity of “”“cGFzc3dvcmQxMjM=” ( 16 charters ) is very hard to crack using a brute force attempt.
Note-The above is NOT my password
Except that nobody uses brute force in 2017, but patterns to crack password.
And yours is a trick by the book, so probably gets cracked in the first 24 hours after a database compromise.
Rule: if you can think of it, one of the other 7 billion people on this planet probably also has done the same thing already.
“A better solution is to take a password you know and remember and encode it with base 64.”
That’s close to a good idea, but turns out to be a BAD idea.
The format of the encoding makes it recognizable, therefore decodable:
echo cGFzc3dvcmQxMjM= | base64 –decode
password123
Basically, the base64 part is the problem: use a hash instead, if you want to use your technique.
I agree with you but using encoded base 64 is a lot better then just using words and charters that can be used in a dictionary attack
I tried your idea, it’s great but a lot of websites won’t accept the encoded output as a password because of the special charters. I know a lot of websites won’t accept the charter “=” in the password
Another great report, Brian. Thank you.
One additional potential adverse consequence you should consider from this event is that the fake merchant now has your name, shipping address, and probably your email and phone number as well. Add to that the criminal can reasonably infer you are relatively affluent due to the type of high-end products you buy and you can probably now expect to be added to a target list for more scams.
Of course, as you have previously mentioned your occupation has already put on you on these lists anyway.
Worse yet, with just a name, the email you use to sign into Amazon, and a street address [N.B — items typically at the top of every resume], anyone can call into Amazon’s customer service and find all sorts of things — prior orders, last-4-and-exp of all the credit cards on the account, wish list items, etc.. IIRC, they may even be able to reset your password.
You should use a separate email for Amazon and use it nowhere else.
I think the clever part is the crook discounted the item just enough to sound legitimate. Half off…nah can’t be real. A third off…yeah that could happen.
Identity is the only security boundary that matters anymore
Yeah me again. I’ve long given up on any password scheme. I use this high entropy generator and a manager:
https://www.grc.com/passwords.htm
The only time I got hacked was though a Roundcube exploit. No password required. The event lead to PayPal security changes and me running my own email server. Needless to say, I don’t use any program like Roundcube, but rather tried and true Postfix and Dovecot, with geographic firewall blocks on all email ports except for 25.
What is the impetus behind sharing all of that info on a public forum, monitored by hackers, which you now can’t delete? I’m genuinely curious.
Question: did anyone (you? the merchant? Amazon?) actually lose any money on this “transaction”? If yes, who? Yes, I read the post and then skimmed it again, but I didn’t note this question being answered. Perhaps I missed it.
I’m not belittling loss of time and inconvenience, but actually incurring a monetary loss is a strong incentive to Do Something about it.
Which leads to: thanks for writing about this.
If Amazon is paying sellers by direct deposit (ACH), and this fraud was discovered after only a week, I don’t see why the Amazon would have any trouble reversing the ACH.
Did the crooks actually get any money from Amazon? Maybe if Amazon sent funds to a foreign bank, that would greatly increase the chances of Amazon losing money permanently.
With all this skills knowledge and efforts can’t they do it anything better then sccams?? are fraudaters crooks mentally unstable or what ??
Amazon will not ship to a new account address without confirming a credit card number. So I don’t see any value for Amazon credentials, unless it’s a seller account.
If a hacker wants to add something to my wish list, fine, but they will not be buying anything from my account if they get my “Amazon-only” credentials.
These problems of password phishing and hacking are going to continue to persist until networks cease using credentials that are interpreted using standard tables and as BK has the courage to admit any of us can be fooled if the scam appears sufficiently legitimate. The mistake is to believe that the people who think these things up are fools and there is no problem when the opposite is more likely to be the case. I am surprised at how slow these large companies have been to implement changes that have been available for many years to make it much harder for credentials to be compromised.
Thanks for telling us about this, Brian. I’m sure it will help us all be safer web users. Glad you got your money back. Hopefully, Amazon will come up with some way to minimize this.
Regards,
I think that it’s now nearly impossible to manage passwords without some software services help to manage them.
To make the password managers more secure, I’d suggest that all of these companies add another service: Alert users that have any passwords that are in the PWNED databases. It wouldn’t be complete or foolproof, but it would help.
I’d also like to know from your story:
Who lost any cash? The credit card issuer would have protected you, but since you got a refund, did Amazon, or that hacked vendor lose?
The vendor lost weeks of legit sales while his hacked account was sorted out. Plus all the good will from his customers.
@DaaBoss
LastPass will monitor your credit report for free via Transunion.
Ref: https://helpdesk.lastpass.com/lastpass-credit-monitoring/
It would be great if LP also monitored email addresses too. The recommendation can and should be made to them.
Also you can manually check whether your email has been pwned here: https://haveibeenpwned.com/
Thanks JPTX! I checked one of my email addresses from the console link you posted, and ironically the site said it was pwned 1 time from a breach of a site that hosts a forum for a malware product!! Wouldn’t ya know? :/
Fortunately it is one of my junk email accounts.
I agree with Arbee above:
What’s the scam? What is the scammer getting? It’s been speculated that they are after your name and address. True?
They are after your money. You pay and as soon as the fake tracking number is uploaded, the crook can process payment from Amazon and wire it to his/her account. Amazon refunds and hence loses.
And so does the legit seller as it may be on the hook for some of the charges, but at least will be rewarded with a set of 1-star reviews potentially huring its rating for months if not years to come.
Two weeks ago I advised Amazon I was being blocked by Bitdefender AV on my Seller Account pages because there was a Trojan on the page. I informed them (five calls and multiple emails) that I received the alert using three different browsers whose caches had been cleared and got the same warning on a completely separate computer. I only received the alert on Amazon Seller Account pages as well as email links Amazon sends me to report any further issues.
The responses:
– I have a virus on my computer(s)
– I should hire someone who does “text support”
– Disable my AV software
– A Microsoft update is the cause (no reply as to which one)
– Greetings from Amazon FBA Support (FBA: Facebook account?)
– “please contact to your system administrator so that they can provide you with the further steps”
_ “have a happy selling on Amazon.”
– send screenshots (to a mailbox that would not accept incoming email)
Not once was I asked what the alert said. I have not had any further responses despite stating the issue is not resolved. (I use a workaround which I won’t divulge here). I’m keeping a closer eye on transactions and deposits and holding my breath. I’ve also started selling on different websites.
I have always found buyer support to be excellent, but the crew doing Seller Account support leave a lot to be desired. I suspect the accounting team convinced management not to invest a lot of money for that department (the same sort of advice Home Depot got a few years ago, and we know how well that worked out).
BT, you shouldn’t fault yourself for jumping on a 32% discount. Amazon often has legitimate deals with discounts much greater.
@Red Rose
Perhaps you were communicating with an alpha version of Siri?
Was one of their responses, “”I’m sorry, Dave. I’m afraid I can’t do that.”?
Most likely you were dealing with a 3rd party outsourced company based in Bangalore.
At least with AI, there is an expectation it will get better and better. Not so much with Bangalore CS, as all the smart ones there are running phone scams as MS tech support.
Bezos needs to address this before Amazon really is just another eBay, as Eric alludes.
Sadly, this CS is based in the USA. Maybe someone with Amazon read my post because my “virus” seems to have fixed itself.
I went down sort of a similar road with Amazon. In my case, it it was a brand-new marketplace seller with too-good-to-be-true prices. Knowing that my financial exposure was zero, I gave it a shot as a science experiment. Like Brian, my product “shipped” (with a fake tracking number). After a few days of watching to see what would happen, I reached out to Amazon. Turns out, and this addresses Brian’s “Suddenly the package seemed to stall, as did any updates about where it was or when it might arrive. This went on for almost a week.” that the fraudulent seller’s goal is to delay the buyer from seeking a refund for 2+ weeks. Less than 2 weeks, the seller hasn’t been paid yet. More than 2 weeks and the seller’s been paid so Amazon has to credit you out of their pocket.
I got one too. I ordered something, and they came up with a tracking number showing something as having shipped from China, which surprised me. Ultimately the thing arrived in the U.S. and was delivered to someplace in Florida, while I was in a different state entirely. I assume the tracking number was for some unrelated item that someone else purchased.
Amazon refunded all of my money, so I am not out anything. I assume that the fake tracking numbers basically let the crooks buy some time so they could siphon off the money before Amazon could reverse the payment – using a tracking number for something coming from China bought them a couple of weeks..
It used to be that I held Amazon in much higher regard than eBay, but that’s no longer the case. There is all kinds of hinky stuff going on there now.
Yeah, it’s getting to the point where it’s hard to trust any Marketplace seller these days. It’s out of control, and there’s no sign the criminals are being reigned in. It’s probably another case of the cost of the fraud is less than the cost of the remediation of the fraud.
These Amazon scams have been going on for quite some time. Instead of fighting back, Amazon (like credit card companies) just eats the loss in favor of preserving simplicity. Besides, the added cost is ultimately passed on to the customer anyway, yet another reason why Amazon just doesn’t care. I no longer patronize Amazon. If more followed my example, Amazon might actually do something about this.
I used to use parts of the site in my password
E.g. PassAwordm
For Amazon
Now I just use a password manager and 18 random characters nearly everywhere
I used to use parts of the site in my password
E.g. PassAwordm
For Amazon
Now I just use a password manager and 18 random characters nearly everywhere
Brian, my already high opinion of you and your work increased significantly. It shows real class to reveal that even a guru like you can be taken advantage of. Nice to see that at least here everything doesn’t revolve on just appearances. All the best to you.
Hi Krebs. Years ago something similar happened to my eBay account. Some chinese cybercrooks stole my account and started selling craps. I’m still trying to figure how they stole my account, since the password was a poem of symbols and numbers and non-sense words (at that time no 2-step auth was in place).
Its only usa customer problem ? Or it can other coubtries tooo?
I wanted to leave a good review, but it seems I can’t..says it was already said
I cut and pasted a fraudulent seller’s account name from the American Amazon site, and got a hit on the Amazon Italy site..
so the answer is yes..it’s world wide.
That’s weird; the link to the long list of websites that I saw yesterday seems to have been removed. Now the link that I thought I had used to access that list goes to another article, about ebay. I’d like to see that list again; where can I find it?
The link in the article seems to work (22APR at 1745 UTC), although the list is not explicitly identified except by the link.
(Easily find the link by searching for “txt” without quotes.)
By the way, Brian, there is at least one error in that list::
DICKSSPORTINGGODS.COM
Sporting >> Gods << ?!
@Michael- That is straight from the store’s database, so the error is on their side, just copied here.
The comment by “davidbolenge” appears to be automated…
https://krebsonsecurity.com/2017/04/how-cybercrooks-put-the-beatdown-on-my-beats/#comment-430479
I’m sorry to be so dense, but I still can’t find that list. I expected to find it using the link starting with the words “happen every day …”, but clearly that’s the wrong link. Can you point me to the correct link to the list? TIA
My apologies; I was looking in the wrong place. Have found the correct link now.
Amazon is being seriously hacked on several fronts.
We, Amazon 3rd party sellers have been reporting the scam accounts for 2 years with minimal results. It appears Amazon either does not wish to clean up it’s marketplace or it’s so vulnerable, it cannot.
Look at our seller forums – you will learn the background details where we try our best to report the scams. This particular thread is also shedding some light how Amazon might be hacked from inside:
https://sellercentral.amazon.com/forums/thread.jspa?messageID=3953303�
This link leads to especially enlightening post by another Amazon Seller, here is a digest of it in case you wanted to read it here:
Since I have accumulated some data to run stats for the past three months of scammer activity, I spent a couple hours today playing with it.
The entire theory is premised on the fact that scammer needs to sleep, eat, drink, go out with friends, and perhaps even has a family with wife and kids…., so the scammer follows the same kind of daily cycles as any of us – wake up in the morning, go to “work”, sleep at night.
Based on the data, the scammer activity picks up just before midnight central time and lasts for about 10-12 hours, that puts the scammer location somewhere in the Eastern European time zone and nowhere close to China as many people here think.
Amazon has a development center in Eastern Europe, http://international-tech.amazon-jobs.com/locations.html , but only one development center deals with marketplace technologies – the center in Romania.
So this is what I would put my money on.
It is not “scammers”, but a SINGLE scammer group of programmers – a few guys with good working knowledge of Amazon AWS API technologies, Amazon software policy implementations and their weaknesses. The accounts they are loading with inventory are not purchased and not broken into – somebody inside Romanian development center is feeding the scammer group inactive seller accounts and helping them to bypass Amazon security procedures.
The same person potentially is selecting tracking numbers for tracking uploads potentially even from Amazon’s database of tracking numbers uploaded by legitimate sellers to create appearance of legitimate shipments for a few weeks since Amazon tracking verification process does not check if the tracking shows delivered to the correct zip code, but instead just checks for item being “shipped” and “delivered” within the delivery window.
So Eastern Europe is my bet…
+1
+1
Lately, I ordered twice from Amazon on the same weekend. On Saturday, I ordered something from Amazon directly. On Sunday, I ordered an item from a 3rd party seller on Amazon Marketplace. Both items shipped on Monday morning. Received confirmation e-mails few hours apart. Fishy part is both packages show the same tracking number! 3rd party seller and Amazon combining items in one shipment was suspect. When the package arrived, it contained only the Amazon item, not the 3rd party item. Contacted Amazon immediately and they refunded me in a heartbeat. Seller has is no longer listed.
Even though I’m in the authentication business, I’ll pass on auth comments (well covered) and go straight to the good stuff – Sonos. Brian, do not pass go, splurge a bit and pay the price, you will not be disappointed! I’m a huge Sonos fan since they came out despite being a bit pricey. Play5’s (latest version) are awesome. Enjoy.
I am still stunned to this day how many times I have watched people creating a new account on any type of site, enter the required email address and then when it asks them to put in a password, they put in the password for THAT email account, when I explain that this is both wrong and VERY insecure, they then explain that they ALWAYS do that…. as it makes it easy for them to remember what they have done…. “light bulb dims” and click
I might be willing to contribute a buck or two to Brian’s wish list. I have certainly learned quite a bit here and am grateful for the sharing.
I didn’t see anyone else post to XKCD’s old cartoon about using longer pass phrases rather than cryptic passwords so I will:
https://xkcd.com/936/
And I have been using a two tiered password strategy for a while now: For non-financial sites that are not that important if they get hacked is use a formula that uses elements found on every web site. If I can’t remember the password, I just recreate it from the elements on the site. For more important sites, I use a difficult password and keep the list in the most secure place I know of: my wallet. And yes, the password list also has simple encryption so the information is not easily understood by anyone but me.
Except that this ‘trick’ has been debunked years ago. Don’t do it! Long sentences composed of words are easy to crash despite their length, as the individual componts are easy to guess words and computer crach programs can assembly sentences from words just as quick as words from characters.
Password hackers know this trick and hence have been using countermeasures for years.
If it has a pattern, it can be easily cracked. Unfortunately if it is easy to remember it likely has a pattern. But dont’ think you can outsmart the crooks. They do this – literally – for a living.