At least 16 hospitals in the United Kingdom are being forced to divert emergency patients today after computer systems there were infected with ransomware, a type of malicious software that encrypts a victim’s documents, images, music and other files unless the victim pays for a key to unlock them.
It remains unclear exactly how this ransomware strain is being disseminated and why it appears to have spread so quickly, but there are indications the malware may be spreading to vulnerable systems through a security hole in Windows that was recently patched by Microsoft.
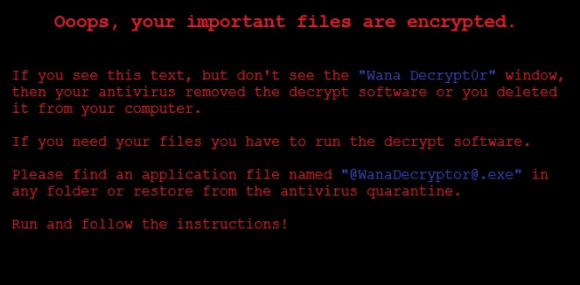
The ransom note left behind on computers infected with the Wanna Decryptor ransomware strain. Image: BleepingComputer.
In a statement, the U.K.’s National Health Service (NHS) said a number of NHS organizations had suffered ransomware attacks.
“This attack was not specifically targeted at the NHS and is affecting organizations from across a range of sectors,” the NHS said. “At this stage we do not have any evidence that patient data has been accessed.”
According to Reuters, hospitals across England are diverting patients requiring emergency treatment away from the affected hospitals, and the public is being advised to seek medical care only for acute medical conditions.
NHS said the investigation is at an early stage but the ransomware that hit at least 16 NHS facilities is a variant of Wana Decryptor (a.k.a. “WannaCry“), a ransomware strain that surfaced roughly two weeks ago.
Lawrence Abrams, owner of the tech-help forum BleepingComputer, said Wana Decryptor wasn’t a big player in the ransomware space until the past 24 hours, when something caused it to be spread far and wide very quickly.
“It’s been out for almost two weeks now, and until very recently it’s just been sitting there,” Abrams said. “Today, it just went nuts. This is by far the biggest outbreak we have seen to date.”
For example, the same ransomware strain apparently today also hit Telefonica, one of Spain’s largest telecommunications companies. According to an article on BleepingComputer, Telefonica has responded by “desperately telling employees to shut down computers and VPN connections in order to limit the ransomware’s reach.”
An alert published by Spain’s national computer emergency response team (CCN-CERT) suggested that the reason for the rapid spread of Wana Decryptor is that it is leveraging a software vulnerability in Windows computers that Microsoft patched in March.
According to CCN-CERT, that flaw is MS17-010, a vulnerability in the Windows Server Message Block (SMB) service, which Windows computers rely upon to share files and printers across a local network. Malware that exploits SMB flaws could be extremely dangerous inside of corporate networks because the file-sharing component may help the ransomware spread rapidly from one infected machine to another.
That SMB flaw has enabled Wana Decryptor to spread to more than 36,000 Windows computers so far, according to Jakub Kroustek, a malware researcher with Avast, a security firm based in the Czech Republic.
“So far, Russia, Ukraine, and Taiwan leading,” the world in new infections, Kroustek wrote in a tweet. “This is huge.”
Abrams said Wana Decryptor — like many ransomware strains — encrypts victim computer files with extremely strong encryption, but the malware itself is not hard to remove from infected computers. Unfortunately, removing the infection does nothing to restore one’s files to their original, unencrypted state.
“It’s not difficult to remove, but it also doesn’t seem to be decryptable,” Abrams said. “It also seems to be very persistent. Every time you make a new file [on an infected PC], it encrypts that new file too.”
Experts may yet find a weakness in Wana that allows them to way to decode the ransomware strain without paying the ransom. For now, however, victims who don’t have backups of their files have one option: Pay the $300 Bitcoin ransom being demanded by the program.
Wana Decryptor is one of hundreds of strains of ransomware. Victims who are struggling with ransomware should pay a visit to BleepingComputer’s ransomware help forum, which often has tutorials on how to remove the malware and in some cases unlock encrypted files without paying the ransom. In addition, the No More Ransom Project also includes an online tool that enables ransomware victims to learn if a free decryptor is available by uploading a single encrypted file.
Update, May 13, 9:33 a.m.: Microsoft today took the unusual step of releasing security updates to fix the SMB flaw in unsupported versions of Windows, including Windows XP, Windows 8, and Windows Server 2003. See this post for more details.




> MS17-010
From EQGRP tools to hospital ransomware, how the mighty have fallen.
Thanks for this article – always interesting to see how these campaigns get rolling
Good article , the ransomware attacks keep coming.
Some fraud wave hitting currently uk,i guess its like fraud season in uk now.
A lot of schools in California were hit with ransomware last year. There were a handful of clues that led some of the admins to believe it was of Russian origin. Is this a campaign from the same Russian hacking group, or are the ransomware tools so widely available there are a number of different bad actors at play?
Yes offcourse Russians but dont you think they are Russians coz their passport is Russian. Indeed orginally Russians dont do crimes…Tsar was killed then everything went bad in Russia
Can’t find the exact article I was referencing, it may have been from an internal csea website. But the origin of most of the ransomware is pretty well established:
https://securelist.com/analysis/publications/77544/a-look-into-the-russian-speaking-ransomware-ecosystem/
“One of the findings of our research is that 47 of the 60+ crypto ransomware families we’ve discovered in the last 12 months are related to Russian-speaking groups or individuals.”
That’s from a Kaspersky report, which according to Bloomberg has worked with the Russian government on several occasions (despite his denials yesterday). Some of the ransomware was probably sold as a service, but it’s hard to imagine such a wide spread attack being accomplished by an affiliate. Even the attack I mentioned last year was far more widespread than I think could be accomplished by an affiliate user.
So the question still stands.
Yeah I wouldn’t jump to that conclusion. It’s certainly possible, perhaps even probable but the spread of malicious software is inevitable. It doesn’t really matter if 75% of ransomware was created in Russia. Making the software requires far more effort than utilizing it, a very basic and rough estimate based on statistics would still lead you to the conclusion that there are at least tens of thousands of users in the US. We have 300 million people living here after all.
To answer your question more succinctly, yes there are thousands upon thousands of bad actors at play and they’re not all Russian. If the admins found clues pointing in that direction then it makes it more likely but obviously they’re not certain or they wouldn’t be using that language. Attribution is very difficult and most attackers are going to make some effort to mislead you. I’m not going to operate a ransomware scheme from my home, I can however lease a server in pretty much any developed country in the world with practically no effort or budget ($10/month Linode instances for example with colo options in Europe and SE Asia).
Now they know the specific tool used, which was released by the shadow brokers the day after the U.S. response to Syria’s chemical attack. I can’t see individual Russian hackers caring enough about Syria to release it and then taunting the U.S. in that fashion. At the time I thought that was a dead give away of Russian government involvement, still do. Interesting how fast and how thoroughly they are drilling down on wannacrypt.
Russian’s didn’t do crime before the tsar was killed??
Ever heard of a guy named Raskolnikov? Some dude named Dostoyevsky wrote about him…
Reported to be affecting many worldwide now:
http://www.bbc.com/news/technology-39901382
If “300 bitcoins” is not a typo, that’s a ransom amount of $527.340.00 based on the current exchange rate of 1 bitcoin = $1757.80.
That’s a lot of coin!
It’s a typo. The actual ransoms are running about $300 to $600 “worth of bitcoins”. In other words, about an eight to a half of a bitcoin
300$ ? How much this guy earned maybe maximum like
few thousends $$ its not even worted…i wonder why tjis kids wasting their talent and time for suche bs
Sorry i tought its 300$ …wow 300 btc its solid ammount
It’s not 300 btc or a “300 Bitcoin ransom”. The wording is “$300 worth of bitcoin”, I’ve see it also as “$600 worth of bitcoin”.
In any case, you are correct, this is going to cause a lot of damage for a $300 ransom.
$300 *per machine* quickly adds up to real money as the attack easily scales to many, many, many machines.
Back up, back up, back up. It’s the highest defense against this type of attack.
Backup & update!
Any kind of automatic backups are still vulnerable to ransomware. For example, if you have an external hard drive which windows runs a backup to, ransomware will encrypt that drive along with the C drive.
To be safe, backups need to manually, which is honestly too much of a pain unless you’re doing it at scale, i.e. for a cloud service or a large IT department.
Ideally, any kind of documents should be kept in the cloud and backups should not need to focus on a whole hard drive image. The cloud provider then needs to have versioned documents available going back in time. For example, Google Drive has the option to “show drive as it was an hour/day/week ago.” This protects for the case of ransomware encrypting your files and then those files being synced.
Healthcare IT News is reporting that the ransom demand on the UK/Scotland attack exceeds $500,000.
That would lead me to think that each computer is encrypted independently, and thus requires separate de-encryption keys. The article didn’t mention that.
I think the ransomware author is going to find out the definition of “too much success”. Getting $300 from a single PC owner or a small business is not going to cause much notice from law enforcement. Ransoms in the many thousands is going to bring out the heat. Let’s see if the ransomware author has flameproof suit.
If each computer is independently encrypted, then that means that there is an algorithm to generate the encryption keys from something that resides in the affected computer, some serial number or computer ID string, or there is a database that keeps track of said computer ID and keeps track of encryption keys. Both are discoverable, but maybe not quick enough to be helpful to the affected hospitals.
It also means that there is a C&C server that has to interact with the malware, and that should be traceable. Look at what shodan.io has done recently with their malware category.
Not really. E.g. if you simply generate a random symmetric key; encrypt files with it, encrypt *that key* with a standard RSA by Bob’s public key and then delete the unencrypted key, everything seems to work.
Everyone has a unique key; Bob can decrypt any and all of those keys; knowing the plaintext and ciphertext of n keys doesn’t help you decript n+1st key; and no C&C is needed, any mechanism to send Bob the encrypted key and get back the usable key will work – websites, email, snailmail, carrier pigeons.
Scary thing is that attacks on hospitals turn this into an act of war.
Arab/Muslim freedom fighters have been targeting and attacking hospitals for a number of years. They view hospitals as tools of their enemies and oppressors.
Brian,
Today in Spain, the same happened to Telefónica and other comopanys institutions. (http://tecnologia.elpais.com/tecnologia/2017/05/12/actualidad/1494585889_857386.html, in Spanish)
Not at all familiar with ransomware.
Does each separate infection (each computer) generate a new key that requires payment to receive in order to unencrypt the files, or does the malware use the same key to encrypt all the files on all infected machines?
In other words, could the UK NHS pay the $300 ransom and use the key on all infected computers or would they need to pay $300 for each machine?
I’m assuming it’s the first option, but don’t know.
Hi Joe. Yes, the ransom is calculated on a per-machine basis. What we’ve seen in cases past is the bad guys have a good sense of how many systems within a victim organization may be infected, and they then set the price accordingly. Some of them are willing to bargain, even.
See: https://krebsonsecurity.com/2016/11/san-francisco-rail-system-hacker-hacked/
Anybody have a packet capture? would love to have on released so it can be analyzed globally.
Thanks Brian. How long can I give you to find the delinquents that are responsible? 🙂
It’s not a surprise really considering that many systems within the NHS are still running Windows XP. I wonder if they will now take updates more seriously?
Forget the attacks; it’s terrifying that British hospitals can’t take emergency patients during a cyber attack! COOP Planning?
The ransomware has reached Brazil.
This ransonware has reached Petrobras, Several Civil Courts of Appeals, some bank agencies (Caixa), Brazilian Social Securtity Agency (INSS), and São Paulo’s Public Justice Department (MPSP).
Source in portuguese: http://g1.globo.com/tecnologia/noticia/hospitais-publicos-na-inglaterra-sao-alvo-cyber-ataques-em-larga-escala.ghtml
Sophos has a ransomware killer called Intercept X. You can get a 30 day trial here.
https://secure2.sophos.com/en-us/lp/sophos-central/free-trial.aspx?id=00130000019KNq4
What makes you think or assume that the current victims had no antivirus installed on their systems?
What makes you think or assume that just any other antivirus (like the one you shamelessly advertise) would have detected this malware and inhibited its destructive work?
What makes you think that antivirus is not (a big) part of the problem at all? Companies which make such snakeoil lull their customers into thinking that they are protected, now and forever … something that no antiXXX is able to.
OTOH Windows provides a means to control what software users are allowed to run: its called Software Restriction Policies and is available for more than 15 years on all editions of Windows!
Compare todays website https://www.sophos.com/en-us/lp/nhs.aspx
with yesterdays website
https://webcache.googleusercontent.com/search?q=cache:cQOpZWYen_UJ:https://www.sophos.com/en-us/lp/nhs.aspx
Today: “Sophos understands the security needs of the NHS”
Yesterday: “The NHS is totally protected with Sophos”.
What this “total protection” means should be known by now!
JFTR: I told you so!
https://mobile.twitter.com/GossiTheDog/status/863185030595710977/photo/1
Its up to 33 organisations and trusts will have multiple hospitals.
Time to resurrect offline backups. Just need to dust off my old external HD that must be in garage somewhere. Not looking for plugs or recommendations, but can anyone weigh in or link on the security of cloud storage services? I have been reluctant to go there for safety and privacy concerns, but it would be easier than regularly performing offline backups.
I’m not surprised, a large percentage of the NHS are still using XP. Some of the smaller groups are still using Win98.
Does anyone have information on how these infections are happening? Are users going to malicious websites and downloading the malware or are they clicking on malicious email links?
Thanks.
Soca will deal with it. And London Metropolitan Police.
and uk security will be tightened..
total internet survailance will be placed.
Uk will deal with security 100% seriously now.
goverment will act now police will have more power.
“…It remains unclear exactly how this ransomware strain is being disseminated and why it appears to have spread so quickly…”
Brian, look at the Jaff ransomware being spread by the Necurs botnet. Anybody looked into potential connections between the two? I don’t see it as a coincidence that 2 different ransomware strains come out in the same week and are getting wide dissemination.
https://www.bleepingcomputer.com/news/security/jaff-ransomware-distributed-via-necurs-malspam-and-asking-for-a-3-700-ransom/
It’s hard to blame Russians in this situation. Most infected computers are in Russia and it’s a sign that WannaCry is a planned cyber-attack against Russian organizations and institutions, including Ministry of Internal Affairs of Russia and Investigative Committee of Russia as it’s said there https://malwareless.com/wannacry-ransomware-massively-attacks-computer-systems-world/. In the past Russian hackers never attacked computers inside their country with ransomware in order
to avoid further problems with police and FSB
Can you create a healthcare tag for things like this? It would be nice to see all healthcare related articles (whether hospital or insurance related) in one place.
This looks like a State attack, and on Russia? Hmmm. It’s not the humble $300 ransom that’s the attack: it’s the method of infection that is the real attack. How can we be certain that the creator of this “bug” is actually responsible for its proliferation: that is much bigger than WannaCry. And isn’t that the best way to hide yourself- use someone else’s malware?
It has to be either e-mail or websites with malicious codes. However, my bet is on just a e-mail spamming campaign and perhaps utilizing paid malicious spamming services. You only need to get one or two people in a network for it spread.
However, I would like to see the conditions in which it spread and executes.
El Jorge
If the malware exploits a vulnerability in SMB1 as Brian has reported, it would not necessarily need to be via email or malicious code on websites. A small amount of initially infected machines could very quickly scan subnets for vulnerable IPs and payload and remotely execute the malware with no user interaction at all. Resulting in a very rapid distribution of the malware, much like you suggest occurs when it is mass-mailed/spammed. The speed and scope of this spreading could suggest something much more automated than a lot of stupid people clicking things they shouldn’t have.
Unsupported windows xp- this isn’t attack on anyone but the stupid. Patients suffer – SHOCKING ?!?
The patch came out days ago & there are so many ways to protect against this –
Why didn’t they do them?
Money and politics ?
Failure to understand risk?
I read something that NHS did not spend money on cyber security – that is not what was needed – this was basic hardware software updating …
If they had a modern pc even windows 7 with auto updating – no issue, as things have been presented so far …
I feel for the impacted people – however 3 years to update the hardware / software – where was the failure that lead to this “massive hack”?
Telephone companies / governments – how hard is it to patch? Really?
My organistaion is Texas based chain of hospitals and clinics. We too were hit by the malware. However the infection was detected by our security vendor and we were able to limit its impact
You don’t need support from ANY security vendor at all!
You can stop the primary attack vector since 15+ years on every edition of Windows with Software Restriction Policies: deny execution of every user-writable file for all users, allow execution only in safe directories only administrators are allowed to write!
See for example https://skanthak.homepage.t-online.de/SAFER.html
But: beware of the loopholes, see http://seclists.org/fulldisclosure/2017/Mar/69 and the fix available from https://skanthak.homepage.t-online.de/appcert.html
Why are our serious work networks still attached to the internet? When one computer was all anyone could afford it made sense for it to do every job. But today computers are cheap. There’s really no reason for the outward facing network to be connected to the internal network, where the serious work gets done. Something that can do email and web surfing and maybe some light document processing can be acquired for about $200. And it can have an OS that isn’t compatible with common malware. People can click on the spank the monkey ad all they want and it’s not going to harm the network were the real work gets done. As a bonus, from the IT department’s perspective it’s zero maintenance.
Of course there still needs to be some way to transfer data from one network to another, but it’s rare enough that it can be a somewhat cumbersome process. Like transferring it to a central server, where it will get scanned and then re-routed to a location on the internal network. That’s two way protection: harder for malware to get in, harder for sensitive data to get out.
For what it’s worth, this was written on a chromebook. I have a Windows 10 computer for my heavy number crunching, because that’s what the software is written for. But I don’t need the full power of a fully general operating system for websurfing, so there’s no reason to expose that fancy computer to the risks of the internet on a regular basis.
Because most companies upper management do not understand InfoSec. All it is to them is added red to the P&L. (Until something happens). They rarely even take into account the loss of productivity from their workers who spend more time web surfing than they do performing their actual job functions. Everything about air-gapped and non-net facing machines is perceived additional cost.
Hi Brian,
If the computer is already encrypted with another encryption software like PGP or McAfee then will the wannadecrypt again encrypt or not??
Are android phones affected??
Imagine a picture. You can turn the picture by 1 degree and you now have another picture. You can turn the picture two more degrees, and you now have another picture.
The fact that your system is “encrypted” doesn’t prevent someone from rewriting the data with another layer of encryption. The same applies to compression. You can try to compress an object multiple times, but typically additional compression attempts won’t make the object more compressed, it’s still be compressed, it’ll just have an extra layer.
Since this malware targets Microsoft’s SMB stack (afaict), Android (which is Linux and shouldn’t have SMB in general) should be immune.
But, if your Android device isn’t running 7+ and receiving updates directly from Google, it’s probably vulnerable to something.
This malware targeted computers that were more than 1 month out of date wrt security updates (or in some cases years, if they were running wXP). Android phones can easily be in a similar position, and will eventually be at risk to similar attacks if someone chooses to invest the time+effort to do so.