A new strain of ransomware dubbed “Petya” is worming its way around the world with alarming speed. The malware is spreading using a vulnerability in Microsoft Windows that the software giant patched in March 2017 — the same bug that was exploited by the recent and prolific WannaCry ransomware strain.
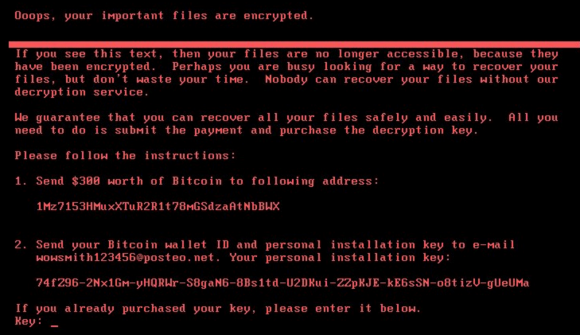
The ransom note that gets displayed on screens of Microsoft Windows computers infected with Petya.
According to multiple news reports, Ukraine appears to be among the hardest hit by Petya. The country’s government, some domestic banks and largest power companies all warned today that they were dealing with fallout from Petya infections.
Danish transport and energy firm Maersk said in a statement on its Web site that “We can confirm that Maersk IT systems are down across multiple sites and business units due to a cyber attack.” In addition, Russian energy giant Rosneft said on Twitter that it was facing a “powerful hacker attack.” However, neither company referenced ransomware or Petya.
Security firm Symantec confirmed that Petya uses the “Eternal Blue” exploit, a digital weapon that was believed to have been developed by the U.S. National Security Agency and in April 2017 leaked online by a hacker group calling itself the Shadow Brokers.
Microsoft released a patch for the Eternal Blue exploit in March (MS17-010), but many businesses put off installing the fix. Many of those that procrastinated were hit with the WannaCry ransomware attacks in May. U.S. intelligence agencies assess with medium confidence that WannaCry was the work of North Korean hackers.
Organizations and individuals who have not yet applied the Windows update for the Eternal Blue exploit should patch now. However, there are indications that Petya may have other tricks up its sleeve to spread inside of large networks.
Russian security firm Group-IB reports that Petya bundles a tool called “LSADump,” which can gather passwords and credential data from Windows computers and domain controllers on the network.
Petya seems to be primarily impacting organizations in Europe, however the malware is starting to show up in the United States. Legal Week reports that global law firm DLA Piper has experienced issues with its systems in the U.S. as a result of the outbreak.
Through its twitter account, the Ukrainian Cyber Police said the attack appears to have been seeded through a software update mechanism built into M.E.Doc, an accounting program that companies working with the Ukranian government need to use.
Nicholas Weaver, a security researcher at the International Computer Science Institute and a lecturer at UC Berkeley, said Petya appears to have been well engineered to be destructive while masquerading as a ransomware strain.
Weaver noted that Petya’s ransom note includes the same Bitcoin address for every victim, whereas most ransomware strains create a custom Bitcoin payment address for each victim.
Also, he said, Petya urges victims to communicate with the extortionists via an email address, while the majority of ransomware strains require victims who wish to pay or communicate with the attackers to use Tor, a global anonymity network that can be used to host Web sites which can be very difficult to take down.
“I’m willing to say with at least moderate confidence that this was a deliberate, malicious, destructive attack or perhaps a test disguised as ransomware,” Weaver said. “The best way to put it is that Petya’s payment infrastructure is a fecal theater.”
Ransomware encrypts important documents and files on infected computers and then demands a ransom (usually in Bitcoin) for a digital key needed to unlock the files. With most ransomware strains, victims who do not have recent backups of their files are faced with a decision to either pay the ransom or kiss their files goodbye.
Ransomware attacks like Petya have become such a common pestilence that many companies are now reportedly stockpiling Bitcoin in case they need to quickly unlock files that are being held hostage by ransomware.
Security experts warn that Petya and other ransomware strains will continue to proliferate as long as companies delay patching and fail to develop a robust response plan for dealing with ransomware infestations.
According to ISACA, a nonprofit that advocates for professionals involved in information security, assurance, risk management and governance, 62 percent of organizations surveyed recently reported experiencing ransomware in 2016, but only 53 percent said they had a formal process in place to address it.
Update: 5:06 p.m. ET: Added quotes from Nicholas Weaver and links to an analysis by the Ukrainian cyber police.




Eternal Blue is based on a Windows vulnerability that the NSA discovered (or purchased) 5 years ago. They kept it secret, in spite of industry-government agreements to share information on vulnerabilities, because it was useful to them. It is doubtful that the intelligence benefit of keeping it secret outweighs the direct damage caused by keeping it secret, as well as the indirect damage to the reputation of the US. Just based on what has been affected so far it’s highly likely that deaths will occur as a result of NSA’s decision.
Larry, not necessarily true, nsa does discover exploits, but they also submit them to a “board” that includes industry (msft) and all come to a consensus on whether or not the exploit is “high priority”. If eternal blue was never “set loose” in the wild, to this day no one would be the wiser.
To think no one would have found this vulnerability had it not been leaked is misguided at best. There are thousands, or more, well funded researchers out there that spend their life looking for these. To think the only people capable of finding something like this is the NSA borders on delusional. NOBUS risks lives, period.
Just because a mistake is never uncovered doesn’t make it any less of a mistake. Keeping this potentially exploitable and obviously destructive and life-threatening weakness a secret was a bad choice, and in hind sight, obviously the wrong choice. I would love to think that there would at least be learning from the mistake, but the responses such as the one(s) from “Jess tess” show that this is probably not going to be the case. There’s always someone who will find a way to justify doing the wrong thing.
I was explaining Wannacrypt to my ten year old son a few weeks back in simplistic terms.
He asked why didn’t the spy company (the NSA) use the kill switch (register the domain) when they seen infection began to spread.
I had no answer
That’s because NSA did not develop WannaCry malware. They simply had (and accidentally leaked) the exploit that WannaCry used to infect network shares. NSA did not know about the Kill Switch domain… is was stumbled upon by a researcher. I think your (obviously smart) 10 year old can understand that.
NSA developed the intrusion method, not the payload.
Consider that NSA is the locksmith that opens the door. But they have nothing to do with the criminals that go through that door. Or what the criminal do once they are in.
They spy company didn’t create the malware that spread around encrypting files. They created/bought a way to execute arbitrary code on a vulnerable system.
This was used by another party to execute code that would encrypt files and ask for ransom. This party created the kill switch as part of their scheme.
Contrary to popular opinion, NSA isn’t out there “looking” for this stuff..it comes to them and they conduct analysis.
“… and they conduct analsys.”
And then what did they do? Call Microsoft 5 years later and say ‘Hey, someone stole our attack database. You guys need to patch.’
You blame the government for hiding it, why not blame the companies for failing to update their systems after being made aware after the fact? Just because it’s a hassle, doesn’t mean you blame the government.
If they wouldnt update after, probably wouldnt had updated even if they were told up fron.t
The companies that failed to update aren’t even related to the comment that he made.
Please read a bit better. The comment was attacking the original poster on his point. Yes, he didn’t reference those companies and is blaming the NSA. The commenter is totally right that anyone who gets infected with this malware after March 2017 has no right to blame the NSA since there has been a patch for the problem from that time. Should I blame Mircosoft for having buggy software even though they issued a patch for it and I failed to use it?
It’s worth noting that Kaspersky is reporting that the email address in the ransom demand has been disabled by the provider in Germany, so there is no point at all in paying the ransom in this case.
Oh, there’s a point — namely, to recover your system if you don’t have a recent backup (or any backup at all) from which to reload. However, since the extortionist’s e-mail has now been disabled, there’s just no practical way by which that payment can be accomplished.
One small notice. Not a National Bank (it’s a separate organization), but some commercial banks. National Bank of Ukraine hasn’t been affected by this attack.
Oh wow. We’re early in analyzing this latest attack, but since it appears to use the same exploit as WannaCry, plus others, here is a link to a bunch of WannaCry information I collected you can use with end users.
http://dgregscott.com/ransomware-will-make-wannacry-can/
– Greg Scott
Oh wow – We’re still early analyzing this latest attack, but since it apparently uses the same exploit as WannaCry, here is a link to a bunch of WannaCry information I collected for end users that should also be relevant to this attack.
http://dgregscott.com/ransomware-will-make-wannacry-can/
– Greg Scott
Thanks for the article. I was piecing together this info from other news sites. Nice to have in one concise post.
Aw nuts! Sorry Brian – The first few times I posted my comment, nothing came back, even after refreshing. And now I see three of them posted. And I don’t have a way to delete the extra ones.
– Greg
Great reporting Brian !
‘Petya’ ransomware makes me ‘WannaCry’
Scott
http://www.HackedAgain.com
Nice Job! Brian
You are The Best Security Expert 100%
I am a Tech Guy myself and check out my Facebook
https://Facebook.com/roberto.hellman
and I am good friends with Leo Laporte
As always, KrebsOnSecurity on point. Thank you.
Maersk confirms that they are hit by Petaya:
https://mobile.twitter.com/Maersk/status/879810135467720705/photo/1
The Danish news channel TV2 reported earlier today that the top management was assembled in the “situation room” – so this is serious business.
I just like posting stuff so
I’ll be cool -in my mind
-Greg
Really? As if I’m not already embarrassed enough for accidentally double-posting, now another commenter has to impersonate me and rub salt in the wound?
– the real Greg Scott
geez yeah this is really embarrassing. double posting and constant whining.
– the real no-one-else-but-me Greg Scott
I wouldn’t call it constant whining; more like observing.
I have a theory on what happened with my double-post.
When I posted my comment for the first time, Brian was also updating the article. Brian uses Akamai hosting, which maintains copies of this blog all over the place. Looking back, it seems my comments were right around the time Brian was doing updates and I probably got caught in the middle of a replication cycle. The lesson learned is, when posting a comment and it doesn’t show up, wait about 10 minutes and refresh again.
I wonder if my impersonator in this comment thread really does share my name, or just somebody having fun? It’s probably run its course.
– The real Greg Scott
Greg, sometimes comments land in moderation for reasons that I can’t easily control. It happens. I try to approve valid comments as soon as I’m able but sometimes that can take hours.
Interesting Read
While my kids complain that we don’t have Windows OS at home I am so glad that we use Linux. Mostly use it at work as well. Integration and file sharing can be a bit of a hassle at times, but worth it. Yes there are occasional exploits, but nothing on this scale.
Not wishing to come over as smug, just relieved.
I won’t even let my kids use Linux. They use Chromebooks.
I can “Powerwash” in less than a minute. Even if the OS could be hacked, I can reload the OS from a USB drive in five minutes.
Chromebooks are based on Linux.
Love my Chromebook!
Infection is usually a case of scale and profit, and as Linux catches up in terms of industry use, so does the malware:
https://blog.knowbe4.com/web-hosting-provider-pays-1-million-to-ransomware-attackers
Looks like the kill switch was found about 90mins ago
by Amit Serper (@0xAmit)
https://twitter.com/0xAmit/status/879789734469488642
“Create a file called perfc with no extension in %windir%”
I can’t confirm.
I’ve heard that kill switch is not reliable info or didn’t work for some. Vet all potential solutions carefully
The file name needs to be the same as the name of the DLL file it dropped on that computer without an extension. EternalBlue is #3 in the list of methods it uses to spread. It only uses it when the other two methods fail to allow it to spread laterally.
A number of sources are saying that this appears to have originated in a malicious update to a Ukrainian accounting software called MeDoc that was published after an alleged attacker gained access to the network of the company that makes it:
https://www.bleepingcomputer.com/news/security/petya-ransomware-outbreak-originated-in-ukraine-via-tainted-accounting-software/
Ironically, just last month Ukrainian president ordered a ban on competing accounting software company 1C (http://1c.ru/eng/). See http://www.economist.com/news/europe/21722360-blocking-websites-may-be-pointless-it-could-help-president-poroshenkos-popularity-ukraine, search for 1C.
Brian or anybody please.
I have been putting”CryptoPrevent on my clients’ computers now for about 10 months.
At it’s highest level of protection it prevents any program from being installed that tries to install executables in certain locations.
Does anybody have an opinion re: CryptoPrevent?
Most of what I know is that it prevented one ransomware attack in my honeypot lab. So I can attest it worked with at least one vector. We learned in MCSE school that the tools you can use in the Microsoft Management Console are a very powerful way to configure your system to use the best security practices available.
As I understand it, this is what CryptoPrevent does – it runs a batch file or script, that configures the MMC for the optimum settings ( and I assume also snap-ins) to prevent unauthorized access, and hopefully also using encryption without permission.
I see no reason not to congratulate Foolish IT for coming up with the idea – most IT nerds don’t know half the settings they need to go through to do it themselves.
“I see no reason not to congratulate Foolish IT for coming up with the idea…”
How about “I congratulate Foolish IT for coming up with the idea…” You’re welcome.
More recent analyses suggest that this malware variant is more sophisticated than originally thought. It attempts propagation via Psexec, WMI, and then EternalBlue
ref:
http://blog.talosintelligence.com/2017/06/worldwide-ransomware-variant.html#more
It must have been a slow news day in cable land – because they were all over the news with shrill shrieking, like the whole world was on fire – and that it just started today.
Good thing I can get the straight poop on Kreb’s on Security! Thanks for the hard work Brian!
Can you please confirm the versaity of the said kill switch discovered by Amit Serper? Your expert opinion of the kill switch would be most valuable before I start deploying it system wide. Thank you!
I’m wondering if there is any information on who spread Petya. People in Ukraine I talk to think it’s the Russians, and yet Rosneft is also affected. It would be extremely useful to know who the prime suspects are in this case, and what is being done to take them down.
If you are a betting person or a fan of detective stories, North Korea might be the “best bet” because there is a very clear standard of “means, motive and opportunity” at play.
Does it even matter who let this loose?
Trying to find some nefarious Dr. Evil who is “behind” these kinds of things is like looking for the bicycle thief in a town full of unlocked bicycles.
The -primary- fault here lies with all of the exceptionally dumbass people, companies, and organizations who -neither- patched -nor- made routine backups. (Failing to do one or the other is arguably a forgivable sin, but failing to do both/either is just colossal idiocy that amounts to personal and/or professional negligence.)
“We have met the enemy, and he is us.”
— Pogo
The least surprising fact is that this attack has been refined and sculpted to be reused the most surprising is the sheer number of organisations, institutions and individuals who didn’t take the warning of the original WannaCry and protect their Windows systems by upgrading. Sloppy! Some IT & security company heads will roll…
Keep up the good work Brian.
Not necessarily. The initial infection vector is not WannaCry (EternalBlue) this time. The malware downloads PsExec and tries to use it and WMIC to spread laterally (to other computers). It scans the local subnet, i.e. the one defined by the subnet mask of the infected PC. It only falls back to EternalBlue to spread itself id the other two methods have failed. You can be fully patched and still get nailed.
It also sets a scheduled task to reboot the infected computer one hour after infection to reload the now-encrypted Master Boot Record. This is just someone using the Ukraine and others for target practice in preparation for their real targets.
“You can be fully patched and still get nailed.”
Ummm… What if all of those ports that were open on all those internal network interfaces had been closed? Then the thing could not have spread internally, yes?
Let’s face it, people and organizations leave s*itloads of ports open, even to the outside world, that don’t need to be open and that shouldn’t be open (as it increases the attack surface). Do we think that the same isn’t true, times ten, when it comes to unnecessarily open ports on internal network interfaces?
Trivial security audits could and would pick up unnecessarily open ports… on *both* internal and external interfaces. But nobody cares, at least not until all of their data finally gets up one day and goes walkabout.
The latest infrmation about this :
1. It’s not Petya, although it may be by the author of Petya. It’s even being called “NotPetya”.
2. There is no kill switch, but the program checks for the presence of a file called “perfc” in c:\windows. If the file is present, the ransomware at least does not run.
3. Posteo in Germany have closed the email account that was the sole point of contact for those infected. So now victims don’t have any hope of getting their files back unless they have a complete backup.
4. As well as ETERNALBLUE the authors are using a second NSA exploit, ETERNALROMANCE.
The panic is somewhat overdone unless of course you’re working for a large organisation with thousands of endpoints. The infection phase is almost certainly over now and it won’t spread outside infected networks.
See BleepingComputer for more info
1 – As Breaking News :-
https://www.bleepingcomputer.com/news/security/wannacry-d-j-vu-petya-ransomware-outbreak-wreaking-havoc-across-the-globe/
2. Posteo removes email account
https://www.bleepingcomputer.com/news/security/email-provider-shuts-down-petya-inbox-preventing-victims-from-recovering-files/
3. Origin + Infection routine
https://www.bleepingcomputer.com/news/security/petya-ransomware-outbreak-originated-in-ukraine-via-tainted-accounting-software/
4. “Vaccine”
https://www.bleepingcomputer.com/news/security/vaccine-not-killswitch-found-for-petya-notpetya-ransomware-outbreak/
I want to thank the commenters providing substantial information about this, especially Mike. At the same time, I want to express my frustration with the commenters who must give their 2 paisa worth about Windows vs Linux, NSA, admin practices etc. 2 paisa is much much less than 2 cents.
Antivirus detect it and delete this ransomeware virus, but people still pay:
https://bitaps.com/1Mz7153HMuxXTuR2R1t78mGSdzaAtNbBWX
Last transaction 15 minutes ago.
To me the Petaya attack looks more like a deception to hide the real taget – Ukraine – than actually trying to make money from ransom. Why attack some of the largest company’s in Europe and ask for petty 300 USD to unlock the computers?
On the day of the Petya attack, high-ranking Ukrainian military intelligence official Col Maksim Shapoval, head of a special forces unit, was killed in a car bombing. Of course, the public would not be privy as to whether there is any connection.
Interesting timing of ” the attack”. Especially, if looked at over a three month period. Taking down records of certain banking systems? I wonder if there is a handle to a Cyprus bank? Covering tracks. Interesting.
But, a good informative article.
“The best way to put it is that Petya’s payment infrastructure is a fecal theater.”
Gold.
Also, it’s difficult to make backups regularly and cheaply at home. I’d use the cloud but we sorely lack encrypted storage services.
A 3-4Tb external drive is increasingly affordable, even pretty cheap these days — so unless you’ve got a sizeable (e.g., humongous or really bigly) backup load exceeding that size, it’s not something which is that much of a problem if set to do so automatically at a convenient time each week.
This is important – if your home computer knows how, when, and where about your backups, then so does the malicious software inside your home computer. Which means, using the cloud without a layer in-between your home computer and your backups only provides an illusion of safety.
Buy a second home computer whose only job is backups. It pulls everything from your working computer and sends it to the cloud. Turn on its personal firewall. Now, when somebody compromises your working home computer, it won’t have a way to reach out and destroy your backups and you can give an appropriate finger gesture to your ransomware attackers.
– Greg
I agree with the other comments concerning backups. I suggest many small businesses and most at home computers can easily be “backed-up” using a external hard drive and using a “system image” and a valid Boot Disk / System Disk. No Special Software required if you are running Windows 7 or newer, Including the most recent Windows 10 versions.
Why is Kaspersky saying it is “notpetya” or “ExPetr” but everyone else is claiming it is Petya?
“… the ransomware is based on old code that some people called Petya, but the ransomware is sufficiently different to be in its own class”.