Sonic Drive-In, a fast-food chain with nearly 3,600 locations across 45 U.S. states, has acknowledged a breach affecting an unknown number of store payment systems. The ongoing breach may have led to a fire sale on millions of stolen credit and debit card accounts that are now being peddled in shadowy underground cybercrime stores, KrebsOnSecurity has learned.

The first hints of a breach at Oklahoma City-based Sonic came last week when I began hearing from sources at multiple financial institutions who noticed a recent pattern of fraudulent transactions on cards that had all previously been used at Sonic.
I directed several of these banking industry sources to have a look at a brand new batch of some five million credit and debit card accounts that were first put up for sale on Sept. 18 in a credit card theft bazaar previously featured here called Joker’s Stash:
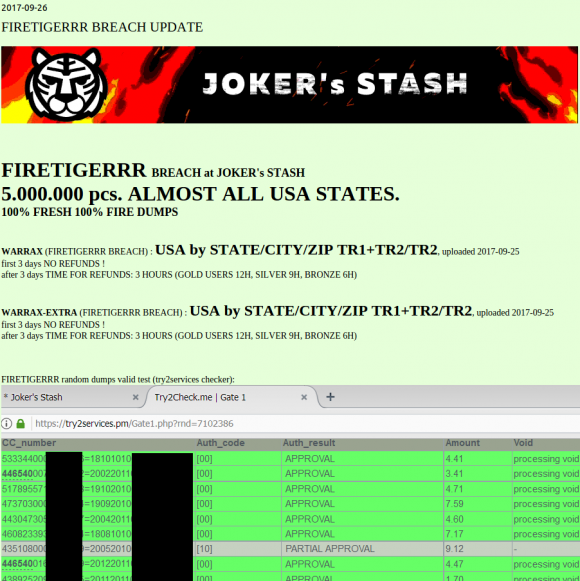
This batch of some five million cards put up for sale today (Sept. 26, 2017) on the popular carding site Joker’s Stash has been tied to a breach at Sonic Drive-In. The first batch of these cards appear to have been uploaded for sale on Sept. 15.
Sure enough, two sources who agreed to purchase a handful of cards from that batch of accounts on sale at Joker’s discovered they all had been recently used at Sonic locations.
Armed with this information, I phoned Sonic, which responded within an hour that it was indeed investigating “a potential incident” at some Sonic locations.
“Our credit card processor informed us last week of unusual activity regarding credit cards used at SONIC,” reads a statement the company issued to KrebsOnSecurity. “The security of our guests’ information is very important to SONIC. We are working to understand the nature and scope of this issue, as we know how important this is to our guests. We immediately engaged third-party forensic experts and law enforcement when we heard from our processor. While law enforcement limits the information we can share, we will communicate additional information as we are able.”
Christi Woodworth, vice president of public relations at Sonic, said the investigation is still in its early stages, and the company does not yet know how many or which of its stores may be impacted.
The accounts apparently stolen from Sonic are part of a batch of cards that Joker’s Stash is calling “Firetigerrr,” and they are indexed by city, state and ZIP code. This geographic specificity allows potential buyers to purchase only cards that were stolen from Sonic customers who live near them, thus avoiding a common anti-fraud defense in which a financial institution might block out-of-state transactions from a known compromised card.
Malicious hackers typically steal credit card data from organizations that accept cards by hacking into point-of-sale systems remotely and seeding those systems with malicious software that can copy account data stored on a card’s magnetic stripe. Thieves can use that data to clone the cards and then use the counterfeits to buy high-priced merchandise from electronics stores and big box retailers.
Prices for the cards advertised in the Firetigerr batch are somewhat higher than for cards stolen in other breaches, likely because this batch is extremely fresh and unlikely to have been canceled by card-issuing banks yet.
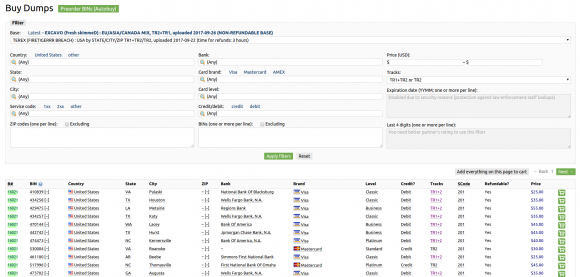
Dumps available for sale on Joker’s Stash from the “FireTigerrr” base, which has been linked to a breach at Sonic Drive-In. Click image to enlarge.
Most of the cards range in price from $25 to $50, and the price is influenced by a number of factors, including: the type of card issued (Amex, Visa, MasterCard, etc); the card’s level (classic, standard, signature, platinum, etc.); whether the card is debit or credit; and the issuing bank.
I should note that it remains unclear whether Sonic is the only company whose customers’ cards are being sold in this particular batch of five million cards at Joker’s Stash. There are some (as yet unconfirmed) indications that perhaps Sonic customer cards are being mixed in with those stolen from other eatery brands that may be compromised by the same attackers.
The last known major card breach involving a large nationwide fast-food chain impacted more than a thousand Wendy’s locations and persisted for almost nine months after it was first disclosed here. The Wendy’s breach was extremely costly for card-issuing banks and credit unions, which were forced to continuously re-issue customer cards that kept getting re-compromised every time their customers went back to eat at another Wendy’s.
Part of the reason Wendy’s corporate offices had trouble getting a handle on the situation was that most of the breached locations were not corporate-owned but instead independently-owned franchises whose payment card systems were managed by third-party point-of-sale vendors.
According to Sonic’s Wikipedia page, roughly 90 percent of Sonic locations across America are franchised.
Dan Berger, president and CEO of the National Association of Federally Insured Credit Unions, said he’s not looking forward to the prospect of another Wendy’s-like fiasco.
“It’s going to be the financial institution that makes them whole, that pays off the charges or replaces money in the customer’s checking account, or reissues the cards, and all those costs fall back on the financial institutions,” Berger said. “These big card breaches are going to continue until there’s a national standard that holds retailers and merchants accountable.”
Financial institutions also bear some of the blame for the current state of affairs. The United States is embarrassingly the last of the G20 nations to make the shift to more secure chip-based cards, which are far more expensive and difficult for criminals to counterfeit. But many financial institutions still haven’t gotten around to replacing traditional magnetic stripe cards with chip-based cards. According to Visa, 58 percent of the more than 421 million Visa cards issued by U.S. financial institutions were chip-based as of March 2017.
Likewise, retailers that accept chip cards may present a less attractive target to hackers than those that don’t. In March 2017, Visa said the number of chip-enabled merchant locations in the country reached two million, representing 44 percent of stores that accept Visa.




this is no surprise to me . i was at a sonic drive in the other day and looking at the menu i see a credit card reader to purchase your food on each stall . it would be extremely easy for someone to not look suspect while rigging up a skimmer to the reader. the first thing that came to mind so i waited for the carhop to bring me my go food to pay and i thought they would use the POS inside but she simply slide my card right there i was like if i wanted to use this public access POS i would slide the card myself as i explained my concerns she seemed not interested in what i had to say..
yes that is concerning – especially once PINs start getting used more often (giving access to cash machine exploit)…however this large scale breach would have been a centralized system (connected to all traffic flowing out for processing), 5 million cards points to a system compromise vs. skimming at individual POS devices. That said, it sound like the security culture isn’t very strict.
Security culture seems lax pretty much everywhere. Security doesn’t make money I guess.
Agreed security doesn’t make money. But it can save a company millions.
I’m 100% sure you don’t understand what happened. They could have installed hundreds of credit card skimmers and it wouldn’t have mattered. This hack involves getting into a database, which is the aggregation of all of the credit cards. A person who is using a skimmer wouldn’t have these kinds of skills.
How do we know this breach was of a database and not at point-of-sale?
The number of cards collected would likely require a huge number of compromised POS or for it to have run for a very long time without being spotted. Not impossible, but unlikely.
Database would certainly explain it better.
Who said it was a breach of a database? I wrote that these things usually are the result of malware installed on the point-of-sale.
I really wish we could get more detailed info about what OS’s are running. where in the network/environment the hack/breach/malware was…
Something to help the IT Security world to help better protect the data and customer…
Even understanding if the environment had P2PE would help.
If you got that info, I’d be interested too. I remain convinced that no one cares about breaches and card fraud. When my card was hacked/breached/whatever, I tried to get help from the police both where I lived and Ohio, where the fake card was used. Ohio wouldn’t help me even though they had the guy on video using a created card. The entire attitude about this has to change from “victimless crime” to “real crime”.
US total population today is 325 million. Can any adult claim not to have had a credit card or social security number stolen?
The solution to all of this is just use cash or gift cards at restaurants or retail
Who the hell trusts any of their Point-of-Sale systems anymore? Even EMV can be compromised
And please don’t be lazy and say its not convenient to have cash in your wallet
Using a gift card would be even worse. Most are just amex numbers that are limited and if they take the money off a gift card, you don’t get anything back.
At least with a credit card, you’re protected.
I’m not talking gift cards with high balances
enough for you purchase $20-25
You use it, you’re done, there would be nothing to steal
Yeah, but now you’re typing your CC number into a website. I don’t think it matters much if you lose your CC number on the net or POS if the payment processor is the same.
It does reduce your risk to a single failure point, instead of every single place you use your card.
Gift cards are an incredibly expensive way to spend money. And they are ridiculously difficult to get all of your money off of them at the end. I can’t imagine going through all that headache for 20-25$.
They’re not expensive if you use something like SCRIP cards. You’re getting exactly the amount you ask for and your CC information is in one location. As someone earlier pointed out, reducing your exploit point to one.
They’re really not expensive, look at the Rewards Credit Card churnning community, they live by manufactured spending buying up giftcards to maximize their rewards points
Can someone enlighten me why restaurants/fast-food chains like Sonic store credit/debit card information long after the original transaction? What is the purpose of this? If it is to protect themselves from fraud, why not only save a portion of the information?
They may not be storing it. The bad guy just gets into their system somewhere, either at POS or centrally, and makes a copy of each CC number as the transactions occur. As far as Sonic is concerned, they aren’t storing it.
Think of it like overhearing someone give out their CC info over the phone. Except in this case someone is electronically bugging the POS machines with their own card reader.
What is the purpose of restaurants and fast food chains holding card information from transactions longer than what it takes to complete the transaction? Am I missing something? If it’s for fraud protection purposes, wouldn’t they be fine with only holding a portion of the information (last 4 digits, name on card, zip code?)
Its to process any tips
I don’t believe most of these breaches are from post-auth storing of cardholder data. The malware on the POS will scrap memory looking for credit card numbers. Many merchants encrypt this information, but then have to decrypt it briefly so they can encrypt it using the private key from the processor or bank.
This is why many are moving to solutions that provide end-to-end encryption. With these solutions, the private key is injected into the payment terminal and the merchant has no way to decrypt the data.
Sonic problem is they use wifi to connect the customer terminal with their in store terminal. I am sure they do not encrypt the card at the end point. With a directional antenna and line of sight you could probably skim the numbers over the air over a mile away.
The next to last paragraph is a little misleading. In most instances, it doesn’t matter if the card is chip-enabled or not. If Sonic only has mag stripe readers (which I know the ones close to where I live only have mag stripe), it doesn’t really matter if the card was or was not chip-enabled. Plus, there is all the talk about liability shift but the liability shift only really matters where the actual fraud occurs, not where the “compromise” happened. In truth, the merchant that has the compromise should most definitely be held accountable especially if they do NOT have chip readers!
You can always tell the comments left by the banks.
Heather, you obviously know that the banks and retailers have been playing the blame game for years. The banks have held off issuing chip cards because not enough stores had chip-enabled readers that were ready to go, and meanwhile it would cost them more to reissue chip-based cards. So they waited. And the stores said, well look, not many banks are issuing these chip cards, so why should we rush to implement chip-capable readers?
My point is that both sides share blame for this embarrassing situation in the United States that we’re still in, and it’s unfair to say that it’s all the retail industry’s fault. Hell, I didn’t get a chip card from a big three bank until the end of last year. Kinda thought that might happen sooner, but it didn’t.
I’ve always felt you have had an ever so slight bias in favor of the banks. I’m glad to see this comment from you – I agree, blame is shared on both sides – all too often I feel its squarely levied on the merchant – whereas the payment brands (some are banks) hold the keys to fixing all of this.
If merchants were as secure as financial institutions and held to as high of a standard, we wouldn’t have the same level of these issues. I still see a lot of Mom-and-Pop merchants’ terminals taped with a sign saying, “No Chip, Ever” (to paraphrase).
Granted, as outdated as this technology is, crooks are finding ways to exploit it and there will still be fraud. Online card-not-present fraud isn’t covered in any of this chip technology debacle. Verified by Visa is being used by crooks because it requires a highly optional registration on the part of the consumer (what genius thought that was a good idea?).
Anytime that Europay, MasterCard, and Visa sneeze and make rulings, they become darn near law, and that’s a dangerous (but all to common) occurrence in American Capitalism that slows down innovation and harms everyone. EMV don’t want to drive off their customers, the merchants, so they cave every time that the merchants demand compliance delays or don’t want to purchase new terminals.
FI’s might have not been fans of having to spend money to make chip technology happen, but were ultimately glad to shift to it once fraud kicked up and definitely willing after EMV FINALLY made a halfway-decent liability shift.
If the larger national banks did some under-the-table garbage to make this situation worse, I really wish someone would blow that whistle.
The debit PIN block has been secured with 3DES encryption end to end dating back into the 20th century. Ignoring physical attacks (overlays, covert cameras, etc) – an electronic compromise of the PIN block by way of a merchant hack/breach has never occurred. The extremely late push to introduce EMV to the US was absolutely the wrong move – what should have occurred instead is the end to end encryption of the PAN just like the PIN block in debit today. The plumbing is already in place and its time tested – never compromised.
This stops the madness of FI’s like your own moaning and whining about how the dog groomer/dry cleaner/local mom and pop gas station/etc/etc aren’t running IT security like a bank. Secure the dang sensitive data from end to end instead of holding on to a pipe dream of every business person in America suddenly running bank grade IT systems.
As the owner of a company that manufactures Kiosks much like what is used at Sonic I can tell you that the ordeal of getting EMV installed is still extremely difficult. Most every project we do runs into issues when getting a processor to approve hardware. I’ve run into this with Fortune 100 companies who have literally spent more than a year getting a processor to finally select hardware they are willing to support for Kiosks. And it’s hardware from reputable companies like Ingenico and Verifone.
Whatever happened to the liability shift? I thought at some point it was going to be that the merchant had to eat all fraud if the bank’s card was chip enabled but the merchant only had swipe?
Alternatively, if the merchant was chip enabled, but the bank only had a magstrip, the bank had to eat the fraud.
The problem is that the liability goes to the wrong merchant.
It goes to the one who accepts the cloned card (because it doesn’t have a Chip reader), instead of the merchant where the card was cloned.
Visa says the liability shift was Oct 1, 2015:
https://www.visa.com/chip/merchants/grow-your-business/payment-technologies/credit-card-chip/liability-shift.jsp
Gas stations (Automated Fuel Dispensers, AFD) was to be Oct 1, 2017 but moved to Oct 1, 2020:
https://usa.visa.com/visa-everywhere/security/emv-at-the-pump.html
Ah, a light just went off in my head about the “liability” part. It’s not about the breach liability, it’s about the liability of future transactions. So for future transactions using these stolen magstrip numbers, the merchants with magstrip reader-only POS are stuck with the liability of any fraud charges, but the banks still have to re-issue all their cards to get new magstrips out there. So the banks don’t have fraud charges to deal with because of Sonic, but they still have re-issuing costs. It seems that Sonic should have to pay for all re-issuing costs if this is traced back to them.
or banks can just put a ‘card watch’ flag on exposed cards and only let ‘safe’ transactions through…eventually they will naturally all reissue as part of the standard 4 year cycle (so if all new cards since 2015 ish are Chip, then the last batch of mag-only should be done in 2019)…each bank will do it’s own business case base on cost and customer impact.
Great. Fuel pumps are probably the number one source of stolen credit cards, due to their easily purchased master keys, cheap and available skimmers, distance and lack of visibility to the attendant, and 24/7 accessibility. AFDs should be the first to be required to upgrade to chip, not the last.
As the manager of issuing and acquiring portfolios I see both sides of the dilemma. Yes, merchants and banks are to blame, but the entities in the best position to enforce the EMV transition are the card networks , and the have been woefully slow in their push. Take for instance their delay in the liability shift for automated fuel dispensers. I also know the routing provision for the Durbin Amendment caused programming delays for both sides.
There are lots of fingers to point. Issuers bear the burden of the fraud losses of these breaches, so they scream the loudest.
“the liability shift only really matters where the actual fraud occurs” That’s totally false! Credit card merchants currently experience charge backs (typically $25-30 fee, plus the actual charge amount) simply because the card holder protested the transaction, I know Heather because I have paid those charge backs. I have even called the bank, volunteered to provide a signed credit card slip, video of the customer eating there meal and video of the customer signing the slip. The banks response, it doesn’t matter if you didn’t read the chip on the card you lose and pay charge back fee plus lose the actual amount of the charge. It is NOT based on fraud at all. It’s banks and issuers stealing my money because they can. I even had a charge back that came from someone I know, in fact a good friend, when I asked them “why did you protest the charge?” they said they had not ever called there credit card issuer to dispute the charge. I then called my processor and demanded they provide proof that someone actually protested the charge in question, that proof never came. Fraud, that’s a joke, it’s a license to steal!
+1
nothing new,thats daily like that. hacking and those kind things,…not even news, try to write about something more interesting tyhamnks.
question? what can you do with those cards? security is so high, i think cant do much really
Magstripe data has been captured, so anyone buying this information online will most likely be creating counterfeit cards. As merchants in the US are predominately still accepting magstripe transactions, they will have a field day. This is on top of the fact they are buying card data which matches the area where the fraudster resides – avoiding financial institutions mitigation method of blocking ‘out-of-state’ transactions on compromised cards.
At what point will financial institution refuse to provide service to retailers and merchants who are don’t take the needed steps to secure and monitor their payment network?
If I was a financial institution, there are many merchants I would refuse to provide service until they better secured their payment system and used chip-enabled terminals.
One of my cards has had a chip for a couple years now. Another of my cards JUST got a chip this past summer. But the problem is that many retailers (like Sonic) still only do magnetic swipe. Many stores have card terminals with the chip slot, but there’s a paper tag inserted, instructing customers it’s not enabled yet, so they still have to do a magnetic swipe.
If card companies REALLY cared, they’d start issuing cards with the chip only, and get rid of the magnetic stripe altogether. That may be what it actually takes to force retailers to upgrade their equipment or remove those paper tags and FINALLY enable their dormant chip readers.
Peter, If banks did away with the magnetic stripes on cards, it would cost them multi-millions in transaction revenue during the period of time it would take to get all merchants up to snuff with EMV enabled readers. I don’t see bank doing away with msr until that potential lost revenue is minimized.
I just left sonic a few minutes ago! I had cash but not enough, so I had to use my card. This has pushed me to go with my gut…when I travel I use cash for gas and food..Why? I don’t trust the machine or the server taking my card. Now even locally I will do the same, I just finished freezing my credit because of Equifax, now this. When will this ever end???
Decades ago (before ATM cards) I drove from LA to SF with my mom. We stopped in some Podunk town to buy gas – paying in cash.
Many miles down the highway we realized that the cashier shortchanged us by quite a bit. We speculated that she probably did this intentionally and made a healthy living that way.
Where there is money there is fraud. it doesn’t matter what form the money is in.
Sounds like a life lesson. Maybe the cashier was just bad at math? Look at the pump to see how much the total was, do the simple subtraction math, and check the change you are given.
Does anyone have the dates effected by the Sonic breach? And is this breach a nationwide breach or by location? I am a bank and needing to determine if this is going to effect cardholders in Oklahoma. I suspect probably yes.
This will be nationwide I would suggest. All locations that use the affected POS system – so no state will be ‘untouched’.
As a bank, why not be better safe than sorry? ESPECIALLY when their headquarters is as close as it is to you. As a customer, I’d happily accept the “we just want to make sure you’re safe” line.
It is unfortunate how slow the U.S. has been adopting the chip cards. I was talking with folks from the U.K. at a security conference and they have already moved beyond the chips to cards with Tap ‘n Pay technology like what some hotel cards here have. They were so confused as to why we are still using mag strip.
Long live Samsung Pay (or ApplePay, if you must). Cardless, token based payment is the future.
Samsung has the technical edge on this tech, as the MST technology allows for use in many places where merchants haven’t upgraded to tap capability, but Apple has market dominance (for now).
Even the chip cards are easy to duplicate, if the reader errors out three times on the chip (if it cant read the chip), most systems will default back to just a swipe. Walgreens is one that I have seen that happen at.
That’s still a duplication of the mag stripe – just onto a chipped blank. “Chip cards are easy to duplicate” is hugely misleading, as easily verified by searching for counterfeit chip cases out in the wild. You’re right about the fallback transactions, but that’s down to implementation: the merchant can choose not to accept them (in some territories it’s not even a choice), and the card issuer can choose to block them (we do where I work and counterfeit cards are a non-issue for us).
No one should be swiping a mag card in this day image for purchase of anything
anywhere. It is the least secured way to process the transfer of money. The US is so far behind in this issue. Stop swiping your card. Call your bank. Demand a chip card. If you can’t manage that, use cash.
re: “some five million credit and debit card accounts that were first put up for sale”. Why do people use debit cards like credit cards thus exposing their checking account? If a person’s credit rating is not good enough to get a credit card then use cash until such time when a low limit credit card can be obtained. Plus never get a combined debit/credit card.
Oh also, PCI requirements say you can’t store PINs, so wtf is the difference
Because not all of us like to pay for stuff with someone else’s money.
“Thus exposing their checking account” – false
That’s… not what a credit card is for. If you’re using a credit card to pay for things that you don’t have cash for, you’re doing it wrong. Using a credit card does not equal going into debt.
And yes, debit cards are linked to checking accounts.
How can I get help as a victim of this incident. I used my American express at Sonic in Abbeville. 2 days later my balance was over $758!!!
Just contact your credit card company, mention this breach and where you used your card. They should perform an audit of the transactions.
Typically they want you to highlight all the charges you did not make and sign a document attesting to this. It’s not hard if the charges are done in a far off geographic. It’s much harder to do if they are from within your normal geographic and at common places like Wal-Mart, etc.
The whole idea behind the chip card was two factor ID, and you also needed a PIN to go with the card. American credit card companies diluted it to single factor, a credit card number (and a possibly forged signature). Security theatre. The chip as implemented is useless.
No. The PIN is mostly theater.
What matters is that the Chip performs a digital signature using a private key and retains a transaction log.
What is provided by the Chip during a transaction is not sufficient to produce a clone of the card.
The PIN is what stops someone going crazy on a lost/stolen card – hardly ‘theatre’. It’s the ‘something you know’ that increases the security of the ‘something you have’ – more secure than a signature that’s conveniently on the card (and rarely checked), and vastly more secure than having no other factor and just assuming that the person presenting the card is the rightful cardholder.
What’s the over-under on how much this will cost Sonic?
Just a bystander in CC security with a question, maybe obvious to you guys.
If these readers were chip readers and not swipe readers, would this breach be as serious as it sounds?
I’m still a little unclear on the swipe vs chip with regards to counterfeiting and theft. I mean swiping is worse, but is chip really counterfeit proof ??
I try to go to places who has Android pay, but alas it’s not everywhere. I’ve had a growing fear everyday I swipe my debit/credit cards.
This is one of my favorite places to eat and I have noticed how the card readers are outside so easy for anyone to place in skimmer. The other day I got Costco gas and saw their machines had a tape on them. If anybody were to try and install a skimmer, they’ll know about it immediately.
Brian,
Do you think there is any linkage between this breach and what happened with Oracle last year? Looks like Sonic was in the process of updating all their POS systems to the Oracle MICROS platform.
How can we find a list of zip codes affected without actually going to the Joker’s Stash site?
I have many credit cards and some of them I just use once a year only (to show some activity and keep from closure, I collect cards for points and miles and cashbacks). Few months ago I gave such a card to a sonic drive-trough window and next day it was drained in the nearby grocery store. Since there was no other activity on the card it became clear to me that Sonic employee duplicated it. They take the card out of your sight and can potentially swipe it wherever. I talked to a supervisor and explained it but I think he wouldn’t care much. IMHO the commonality of the stolen cards being previously used in Sonic is just because they take the card out of your sight. Another high risk POS is any full service gas station.
Have the at risk dates been given yet for the Sonic Drive In data breach? I did not come across them yet in my search. Are there initial suspected dates at this point?
Is there a way to find out if you’re on this list without going to a dirty website? lol
My CC companies “cant” or “wont” give me any information on this and so far I see no activity that identifies it but I was LITERALLY sitting at Sonic having JUST stuck my card (a chip card) into the stupid swiping thingie like 3 minutes prior when this hit my feed. I was like….great.
I am going to just have to change to “if they don’t take ApplePay” I am only paying with cash for my payment.
They run Micros terminals which were compromised last year, it’s possible the bad guys still have an entry point/back door.
They also installed new POS terminals which started to roll out earlier this yesr – http://www.nrn.com/technology/sonic-team-helps-operators-reap-benefits-new-pos-system
I believe we should go back to a cash society. Pay cash for your local transactions and mail checks for bills.
Here’s a bit about how MLM rolled out info of the alleged impact of the Sonic breach on their retailer debit cards. What a joke.
https://theprietopattern.com/
I would love some info on this, so I can get any impacted cards blocked. CAMS where are you?
How can I learn if my card was compromised at Sonic?