Companies around the globe are scrambling to comply with new European privacy regulations that take effect a little more than three months from now. But many security experts are worried that the changes being ushered in by the rush to adhere to the law may make it more difficult to track down cybercriminals and less likely that organizations will be willing to share data about new online threats.
On May 25, 2018, the General Data Protection Regulation (GDPR) takes effect. The law, enacted by the European Parliament, requires technology companies to get affirmative consent for any information they collect on people within the European Union. Organizations that violate the GDPR could face fines of up to four percent of global annual revenues.

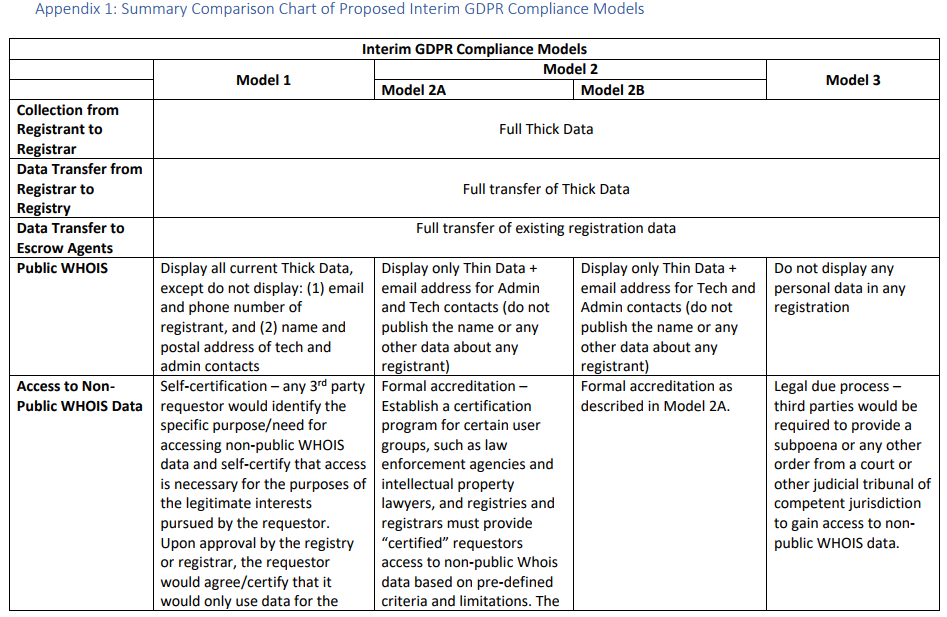
In response, the Internet Corporation for Assigned Names and Numbers (ICANN) — the nonprofit entity that manages the global domain name system — is poised to propose changes to the rules governing how much personal information Web site name registrars can collect and who should have access to the data.
Specifically, ICANN has been seeking feedback on a range of proposals to redact information provided in WHOIS, the system for querying databases that store the registered users of domain names and blocks of Internet address ranges (IP addresses).
Under current ICANN rules, domain name registrars should collect and display a variety of data points when someone performs a WHOIS lookup on a given domain, such as the registrant’s name, address, email address and phone number. (Most registrars offer a privacy protection service that shields this information from public WHOIS lookups; some registrars charge a nominal fee for this service, while others offer it for free).
In a bid to help domain registrars comply with the GDPR regulations, ICANN has floated several proposals, all of which would redact some of the registrant data from WHOIS records. Its mildest proposal would remove the registrant’s name, email, and phone number, while allowing self-certified 3rd parties to request access to said data at the approval of a higher authority — such as the registrar used to register the domain name.
The most restrictive proposal would remove all registrant data from public WHOIS records, and would require legal due process (such as a subpoena or court order) to reveal any information supplied by the domain registrant.
The full text of ICANN’s latest proposed models (from which the screenshot above was taken) can be found here (PDF). A diverse ICANN working group made up of privacy activists, technologists, lawyers, trademark holders and security experts has been arguing about these details since 2016. For the curious and/or intrepid, the entire archive of those debates up to the current day is available at this link.
WHAT IS THE WHOIS DEBATE?
To drastically simplify the discussions into two sides, those in the privacy camp say WHOIS records are being routinely plundered and abused by all manner of ne’er-do-wells, including spammers, scammers, phishers and stalkers. In short, their view seems to be that the availability of registrant data in the WHOIS records causes more problems than it is designed to solve.
Meanwhile, security experts are arguing that the data in WHOIS records has been indispensable in tracking down and bringing to justice those who seek to perpetrate said scams, spams, phishes and….er….stalks.
Many privacy advocates seem to take a dim view of any ICANN system by which third parties (and not just law enforcement officials) might be vetted or accredited to look at a domain registrant’s name, address, phone number, email address, etc. This sentiment is captured in public comments made by the Electronic Frontier Foundation‘s Jeremy Malcolm, who argued that — even if such information were only limited to anti-abuse professionals — this also wouldn’t work.
“There would be nothing to stop malicious actors from identifying as anti-abuse professionals – neither would want to have a system to ‘vet’ anti-abuse professionals, because that would be even more problematic,” Malcolm wrote in October 2017. “There is no added value in collecting personal information – after all, criminals are not going to provide correct information anyway, and if a domain has been compromised then the personal information of the original registrant isn’t going to help much, and its availability in the wild could cause significant harm to the registrant.”
Anti-abuse and security experts counter that there are endless examples of people involved in spam, phishing, malware attacks and other forms of cybercrime who include details in WHOIS records that are extremely useful for tracking down the perpetrators, disrupting their operations, or building reputation-based systems (such as anti-spam and anti-malware services) that seek to filter or block such activity.
Moreover, they point out that the overwhelming majority of phishing is performed with the help of compromised domains, and that the primary method for cleaning up those compromises is using WHOIS data to contact the victim and/or their hosting provider.
Many commentators observed that, in the end, ICANN is likely to proceed in a way that covers its own backside, and that of its primary constituency — domain registrars. Registrars pay a fee to ICANN for each domain a customer registers, although revenue from those fees has been falling of late, forcing ICANN to make significant budget cuts.
Some critics of the WHOIS privacy effort have voiced the opinion that the registrars generally view public WHOIS data as a nuisance issue for their domain registrant customers and an unwelcome cost-center (from being short-staffed to field a constant stream of abuse complaints from security experts, researchers and others in the anti-abuse community).
“Much of the registrar market is a race to the bottom, and the ability of ICANN to police the contractual relationships in that market effectively has not been well-demonstrated over time,” commenter Andrew Sullivan observed.
In any case, sources close to the debate tell KrebsOnSecurity that ICANN is poised to recommend a WHOIS model loosely based on Model 1 in the chart above.
Specifically, the system that ICANN is planning to recommend, according to sources, would ask registrars and registries to display just the domain name, city, state/province and country of the registrant in each record; the public email addresses would be replaced by a form or message relay link that allows users to contact the registrant. The source also said ICANN plans to leave it up to the registries/registrars to apply these changes globally or only to natural persons living in the European Economic Area (EEA).
In addition, sources say non-public WHOIS data would be accessible via a credentialing system to identify law enforcement agencies and intellectual property rights holders. However, it’s unlikely that such a system would be built and approved before the May 25, 2018 effectiveness date for the GDPR, so the rumor is that ICANN intends to propose a self-certification model in the meantime.
ICANN spokesman Brad White declined to confirm or deny any of the above, referring me instead to a blog post published Tuesday evening by ICANN CEO Göran Marby. That post does not, however, clarify which way ICANN may be leaning on the matter.
“Our conversations and work are on-going and not yet final,” White wrote in a statement shared with KrebsOnSecurity. “We are converging on a final interim model as we continue to engage, review and assess the input we receive from our stakeholders and Data Protection Authorities (PDAs).”
But with the GDPR compliance deadline looming, some registrars are moving forward with their own plans on WHOIS privacy. GoDaddy, one of the world’s largest domain registrars, recently began redacting most registrant data from WHOIS records for domains that are queried via third-party tools. And it seems likely that other registrars will follow GoDaddy’s lead.
ANALYSIS
For my part, I can say without hesitation that few resources are as critical to what I do here at KrebsOnSecurity than the data available in the public WHOIS records. WHOIS records are incredibly useful signposts for tracking cybercrime, and they frequently allow KrebsOnSecurity to break important stories about the connections between and identities behind various cybercriminal operations and the individuals/networks actively supporting or enabling those activities. I also very often rely on WHOIS records to locate contact information for potential sources or cybercrime victims who may not yet be aware of their victimization.
In a great many cases, I have found that clues about the identities of those who perpetrate cybercrime can be found by following a trail of information in WHOIS records that predates their cybercriminal careers. Also, even in cases where online abusers provide intentionally misleading or false information in WHOIS records, that information is still extremely useful in mapping the extent of their malware, phishing and scamming operations.
Anyone looking for copious examples of both need only to search this Web site for the term “WHOIS,” which yields dozens of stories and investigations that simply would not have been possible without the data currently available in the global WHOIS records.
Many privacy activists involved in to the WHOIS debate have argued that other data related to domain and Internet address registrations — such as name servers, Internet (IP) addresses and registration dates — should also be considered private information. My chief concern if this belief becomes more widely held is that security companies might stop sharing such information for fear of violating the GDPR, thus hampering the important work of anti-abuse and security professionals.
This is hardly a theoretical concern. Last month I heard from a security firm based in the European Union regarding a new Internet of Things (IoT) botnet they’d discovered that was unusually complex and advanced. Their outreach piqued my curiosity because I had already been working with a researcher here in the United States who was investigating a similar-sounding IoT botnet, and I wanted to know if my source and the security company were looking at the same thing.
But when I asked the security firm to share a list of Internet addresses related to their discovery, they told me they could not do so because IP addresses could be considered private data — even after I assured them I did not intend to publish the data.
“According to many forums, IPs should be considered personal data as it enters the scope of ‘online identifiers’,” the researcher wrote in an email to KrebsOnSecurity, declining to answer questions about whether their concern was related to provisions in the GDPR specifically. “Either way, it’s IP addresses belonging to people with vulnerable/infected devices and sharing them may be perceived as bad practice on our end. We consider the list of IPs with infected victims to be private information at this point.”
Certainly as the Internet matures and big companies develop ever more intrusive ways to hoover up data on consumers, we also need to rein in the most egregious practices while giving Internet users more robust tools to protect and preserve their privacy. In the context of Internet security and the privacy principles envisioned in the GDPR, however, I’m worried that cybercriminals may end up being the biggest beneficiaries of this new law.




Could be yet another example of regulations with unintended consequences.
What happens when the negative externalities of your industry are vastly larger than the value of your entire industry put together? It’s a question that should be considered for the domain registration industry.
The domain registration industry has long refused to reduce the massive volumes of criminality they enable, with their cheap domain sales, and highly obfuscated or nonfunctional processes for anti-abuse domain takedowns. They profit from crime!
I applaud improved privacy for the purchase of many different online services, but domains have been abused so much that it’s time for the pendulum to swing the other way. If you purchase a domain, you are playing in the same sandbox that China uses to phish trade secrets, and the same sandbox that Russia uses to install extremist puppets in Western democracies. Don’t be surprised if you receive scrutiny!
WHOIS is one of the last remaining tools network operators have before they say “fuck it”, and block everything outside of a whitelist.
If you want to own a domain with total privacy. Get a free subdomain. Get a .onion domain. Get ANYTHING ELSE. Don’t purchase the exact same type of product that is being used to conduct cyberwar.
As a european living in america I can see the european look at things: “We live in a pretty safe world and there is no reason to sacrifice civil liberties and descend into american-style paranoia.” Having lived in both places, I would agree.
I seem to remember a certain France election spearphishing campaign where WHOIS was crucial to discovering it before they could do to Macron what they did to Hillary.
Are you saying you’re okay with that operation succeeding if it means domain owners get additional privacy?
Bad things happen in Europe too. Turning this into some way to pretend you’re better than Americans is pretty foolish.
Brian, I’m a security researcher and a fan of yours but I’ll have to disagree with you on this one. I have always opted to pay registrars the extra dollar or so for WHOIS privacy. Seven months ago I registered a domain from my phone and missed the WHOIS privacy checkbox. Since then, I’ve been inundated with phone calls and emails from scammers.
My number is on every do not call list I could find. I used to get maybe one robocall per month or two, now I receive calls daily. I currently get more calls from scammers than I do from people I know. I used to report each call to the FCC, but it’s too time consuming to fill out their form several times per week.
WHOIS information is being abused. I’m sorry that restricting it will make your job harder, but the WHOIS records for my domain contain more information about me than most data breaches I’ve been in. This information shouldn’t be publicly available.
I agree. If I’m trying to reach a domain owner, I don’t really need their full name, home address and phone number. I have no problem with the plan to provide a web form that will forward a message to the domain owner.
I completely agree, I also love your research but not putting privacy first with this age of cyber security could put many individuals, family’s and businesses at risk from violence to loosing money and eventually everything, once one is ignored out of the three, it’s only a matter of time, there is no reason that they can’t cover any infrastructure. When registering with the Whois Database, personnel information should be registered but names and address should be kept private from the network with anyone, individual, business’s or government and only be made available to the registrar or government when needed. We get the cyber criminals and our privacy at the same time.
I disagree. You skipped a step in registration that you know you should have enabled, but didn’t.
Of those nuisance calls and emails you received, how many of them were from spoofed sources? If the number is zero, then you may have a point, otherwise I hope you reported all of them to the appropriate authorities. BTW, how did you know who to report the emails to? Probably WHOIS. If you used some other method, please let us know what that method is.
It’s almost as if the security and privacy people are talking past each other.
The security people seem willing to reach a compromise that doesn’t completely obliterate the usefulness of data in the whois database, while the privacy people seem to think we should just get rid of any data on the registrant, full stop.
Those who don’t see the security implications here tend to forget that without security there is no privacy.
People who say, “without security there is no privacy” live in a fantasy land where an omnipotent/omnicient benevolent government will always save everyone from all evil in the world. In the real world we live in, letting any government invade all privacy to “save” us creates a monster that crushes its subjects. Just look at all the dictatorships in the world for evidence of this. In effect, you actually have, “without privacy there is no security”
Pulling the mailing address and email address would pretty much kill one of the biggest scammers dead: Domain Registry of America.
Well I know whois helped me a couple times. Was just talking about it yesterday when I would complain to verizon about why they would send me over the pond to Germany before connecting to the west coast.
Residential said they would only help up to a certain amount of hops, i forget how many maybe 5 or 6. But the hop right after was the one redirecting me overseas. They said it was not a verizon server because the whois information said it was not theirs. But I found out that the whois information was oudated and wrong and I proved to them that Verizon had bought that server and I had the date and documents and linked it to them. It was right online.
Then they admitted that it was indeed their server but that it was the business department and they couldn’t help me. I started blowing up their forums with threads. Started posting on dslreports.com Many people had issues to the same game were responding. Long story short eventually a Level 3 verizon technician kept calling me at my house. And he started to try telling me the same thing about the hops i was seeing going to Germany and then back though Canada to Washington to get through to the west coast, were wrong and not accurate. That I was probably not going overseas. I eventually got him to admit that I probably was lol. And he said all he could do was shoot an email to the German server admin, which was the server causing me high latency, and he gave me the email address ass well which was diff then one I would see online with whois or icann.
Of course I never got a reply back from the German admin, but the issue was fixed.
SO to be honest I don’t know how reliable the whois stuff is, and I consider most security researchers just as bad as criminals and stalkers themselves sometimes. But I guess for someone like me doing trace routes, I will also be left in the dark now also.
It bothers me that I still get routed across the pond to get to the west coast from NY, or even sometimes to atlanta. Evident now in another game I’m playing. I get more stable connections playing on France and German servers then on California ones!! I always wonder if it has to do with what Snowden said about the 5 eyes and US government avoiding collecting information illegally on people from within the country. They let Germany do it for them.
Just wanted to share one of my own whois experiences…It definitely helped me and some other consumers because of it.
But I think as time goes on, its becoming less reliable anyways.
The DE-CIX extension located inside NYC has been legally very convenient for FISA exempted listening nodes for a number of years. People involved with TOR frequently find their traffic crossing a virtual piece of the german BGP IP ranges that for court room purposes will look like the traffic was ‘legitimately’ collected outside the border.
It is typically European to pay off extortionists and turn a blind eye to criminals until they cause somebody important a problem.
There needs to be a solution which is more nuanced than can be handled by the text of any law.
Have you looked at the law in question? It’s incredibly nuanced, for a privacy regulation. The text describing reasoning and scenarios for implementation are longer than the controls and extremely helpful for understanding the intent, which, almost uniquely for a regulatory framework, seems to *actually be aimed at trying to solve the problem*.
Brian’s way off the mark on this one, at the very least in regarding this as a major flaw in the regulation. At most, this is a small price to a very large good.
Please take the time to read the GDPR text. Your remark doesn’t add any value to the discussion. And be respectful to others.
I own about 30 domain names and most of them are merely parked or used for niche marketing… nonetheless, I have always exposed my normal email to the public / WHOIS rather than obscure it and as a result I receive a lot of unsolicited emails including blind solicitations and many phishing emails. I have nothing to hide and no reason to hide – the email volume is somewhat bothersome, but not unmanageable with spam filters and a decent firewall. Leave the information public IMHO.
GDPR looks like surfing fun so long as you are not in the EU, eurocrap eurocrats fixing things that aint broke since….
https://www.businessinsider.com/gdpr-europe-privacy-law-advantage-to-us-tech-companies-2018-2?IR=T
I register my domains without domain privacy. Have been doing so since the 1990s, and never have seen it as a problem. I don’t think I’m a target of phishing attempts any more than anyone else.
This idea of hiding nameservers is interesting. Do these “privacy experts” know how the internet works? The nameservers absolutely need to be public information so that a DNS can look up the IP address being requested.
If I can’t lookup the nameserver with “whois google.com”, I’ll look it up with “dig ns google.com @a.gtld-servers.net”. It’s not likely to change.
GDPR can grant exceptions for data collection in the interest of security. This could be information that is tracked, but not displayed on the website. Then is only provided with a request. The information is supposed to be provided in an electronic format so the turnaround time should be minimal.
Doesn’t seem like a big issue, but I’ll keep my eye on this.
1. “But with the GDPR compliance deadline looming, some registrars are moving forward with their own plans on WHOIS privacy. GoDaddy, one of the world’s largest domain registrars, recently began redacting most registrant data from WHOIS records for domains that are queried via third-party tools. And it seems likely that other registrars will follow GoDaddy’s lead.”
Seems like not following ICANN rules, a violation.
In a non-GDPR jurisdiction, I could see that heading to judicial case.
2. Flip the model 3 proposal: “Legal due process” — registrants would be required to provide legal documentation proving who they are…following a process to prevent fraudulent sign-ups. Create all the privacy AND a judicial apparatus of penalties for registrant violations.
When I’m doxing people I always use whois first. It has ruined very many family lives 🙂
A large portion of the benefit provided by what we can currently see in WHOIS will remain there even under the GDPR. Companies wishing to protect their brand will still grant permission to show their un-redacted data so visitors place the appropriate level of trust in their domain. To me, it seems the largest impact of the GDPR is that paid privacy protect services will be unnecessary for legitimate registrations.
I make extensive use of WHOIS in both my private and professional life, and I still see little impact from redacting personal contact information, especially if we are provided with an alternative method for comparing apples to apples (as some privacy/security conscious registries already provide).
If the current practice of keeping the address and the phone number of thevperson that registers a domain in the whois record ensures security why didn’t we use this information to close down all illegal hacker forums , Viagra vendors, typo squatting sites and so on by going to this address and taking the guy we find there to prison?
My guess is that the information in the whois record tends to be only honest if the website is legal and the owner would have a right for protection.
But some times the whois info is interesting, I have to admit. And there seems to be a bit of security: for my own website one day they sent me a letter to see if the address I have provided is real.
Anyone got any figures for the percentage of online crime etc that is originated from within the e.u/eea ?
Seems that a tiny minority of supposed smart people want to continue with what is an obviously broken/abusable system rather than design/implement a new,far more secure and useful one.
Whois may be useful sometimes for back tracking a few peoples past history,but then their the amatuers who dont think long term or are stupid/lazy,any true pro is not going to leave you clues like that..
Gpdr will help secure almost a billion peoples data and give them some kind of control over THEIR data,many of you seem to be arguing about a scenario that involves possibly catching a tiny number of idiots,most of whom never face any kind of legal action even after being exposed,so which is better,improved security for a billion,or ability to find a few amatuer baddies ?
As a contributing member of EFF I *strongly* support privacy for Internet users. But when you set up a domain, server and presence on the net I think you need to be accountable. A business needs a business license and often other permits that must be publicly accessible. How is this different? In both cases one is voluntarily revealing oneself to the public. It’s similar for broadcasters and publishers.
Political and cultural dissidents are a thorny problem. I think they have to find someone to shelter them much like Google did for Krebs.
Recently I registered and implemented a domain for personal email use. Afterwards I received one (1) spam concerning it.
But you are accountable. Law enforcement can and will have access to the whois data, just like they can and will have access to customer data at an ISP.
Via an edict, or any other means, determined in the legal framework of that jurisdiction.
Hi Brian, this line is confusing: “Under current ICANN rules, domain name registrars should collect and display a variety of data points when someone performs a WHOIS lookup on a given domain, such as the registrant’s name, address, email address and phone number.”
– There are rules for gTLDs, new gTLDs, ccTLDS, … and those rules are not the same.
– You have ICANN accredited registrars and other registrars.
– Should and must are not the same thing.
“…requires technology companies to get affirmative consent for any information they collect….”
This is inaccurate and misleading. Consent is a last resort if there are no other legitimate bases for processing.
This is indeed inaccurate and misleading.
Furthermore, “for any information they collect on people within the European Union” is also incorrect. It’s all about private data; information that, directly or indirectly, can identify a private person.
This is indeed inaccurate ands misleading.
Furthermore, “for any information they collect on people within the European Union” also is incorrect.
It concerns private data only; all information that, directly or indirectly, can identify a private person.
I think they are not being creative. They could anonymize data while still publishing “the hash” which would make it recognizable.
The actual data is not important, being able to recognize it is.
Some data is not PII, like “city” and “country”. It would still help in identifying patterns.
This is completely brain-dead. Any site at all that is accessible to the public (and one that is not doesn’t need its own domain) is already *required* to publish easily-accessible information WRT who’s responsible for that site. Getting that info from some web site, as opposed to the registrar’s data, is child’s play for somebody who would otherwise have to circumvent the registrar’s CAPTCHA.
I think Brian is wrong on this one. ICANN should be dissolved and let the UN handle this.
Can law enforcement officials not get the private Whois data from the registrars? The registrars won’t be getting rid of that data. What this is stopping is the average Joe from snooping through Whois data. If they’ve a legitimate reason to get the data then make an official request.
GDPR is stopping companies from displaying it publically to every Tom, Dick & Harry.
How many people submit real information on their Whois records anyway? I doubt that criminals are typing in their real name, address and phone numbers so it’s not the major blow to crime fighting that is suggested in the article.
I normal agree with Brian but not in this case. I’m in Europe and involved in our GDPR project. It’s a pain in the hole for business but a good step for privacy for citizens.
I don’t have much of an opinion on whois privacy; I believe CIRA (the .ca TLD authority) requires registrars to offer and enable privacy by default, and I’m fine with that, but I’m not unsympathetic to the utility of the information to network security research and action: indeed, I’ve often been stymied in attempts to alert legitimate operators of compromized mail accounts sending spam.
I love how the copyright lobby is able to secure outsized power for itself, though. From the article:
“In addition, sources say non-public WHOIS data would be accessible via a credentialing system to identify law enforcement agencies and intellectual property rights holders.”
This might sound reasonable-ish, until you realize that most people who have any interest in DNS (and many who don’t) own some sort of intellectual property. Where do you draw the line? It could be argued that Disney’s copyrights are worth more than mine, but does that make mine unworthy of access to whois data? Do Mr. Krebs’ rights to his copyrighted works clear the bar?
I too have forgotten to check the box for additional privacy — one time — and I went from almost no calls to daily calls in a very short time. It didn’t even matter that I realized my mistake less than a day afterwards. Too late.
Spam isn’t a problem. I pay for an excellent filtering service. It occasionally blocks things it shouldn’t, but it get’s better as I take a little time every week to “train” it.
But calls. . . . especially when caller ID is spoofed–One time, my number was calling me–are much harder to filter.
On the flip side, even criminals sometimes make stupid mistakes–using the same email address or the same password. So, even though they may use fake or stolen information, sometimes using the same bit in one place that was used in another can allow for dots to be effectively connected.
The current system is most definitely abused. I am not sure what I would propose, since I have conflicting interests. If I had to choose right now, I would say something more than self-certification and something less than law-enforcement only. . . Perhaps something similar to getting a personal digital certificate (like the ACES required by the GSA). But this is just an example.
I just did WHOIS on Krebsonsecurity!! There some info there. It seems Brian is using privacy providers…… hmmmm……
Ahhh…. Brian????
Contact Information
Registrant Contact
Name: Contact Privacy Inc. Customer 0122383209
Organization: Contact Privacy Inc. Customer 0122383209
Mailing Address: 96 Mowat Ave, Toronto ON M6K 3M1 CA
Phone: +1.4165385457
Ext:
Fax:
Fax Ext:
Email:krebsonsecurity.com@contactprivacy.com
Admin Contact
Name: Contact Privacy Inc. Customer 0122383209
Organization: Contact Privacy Inc. Customer 0122383209
Mailing Address: 96 Mowat Ave, Toronto ON M6K 3M1 CA
Phone: +1.4165385457
Ext:
Fax:
Fax Ext:
Email:krebsonsecurity.com@contactprivacy.com
Tech Contact
Name: Contact Privacy Inc. Customer 0122383209
Organization: Contact Privacy Inc. Customer 0122383209
Mailing Address: 96 Mowat Ave, Toronto ON M6K 3M1 CA
Phone: +1.4165385457
Ext:
Fax:
Fax Ext:
Email:krebsonsecurity.com@contactprivacy.com
Congratulations. What’s your point?
You are advertising for transparency while practicing privacy.
These things need not be mutually exclusive. I note in the story that most registrars offer whois privacy for free, or for a very small added fee. I’ve chosen to take advantage of that; most don’t, and then moan about getting spammed and blame it all on WHOIS. In reality, there are 1,001 different places that are leaking your email address daily or have just lost it in breaches a hundred times over.
“In reality, there are 1,001 different places that are leaking your email address daily-”
Starting with: Pretty Much Every Time You’ve Ever Sent or Received an Email.
Having read over the GDPR fairly extensively I can’t help but feel a lot of it- while it’s well-meaning- is inescapably Pie-in-the-Sky kind of thinking. “Wouldn’t it be great if everyone could be forgotten?”
Not saying it isn’t a worthy goal, mind you. I’m just saying that building that bridge out of paper might not be the most efficient way to make progress towards it.
Brian, I like your articles and research, but it would have been better if you would have disclosed that you use privacy protection.
Now I disagree with your point of view even more since you yourself do not appear to have faith in WHOIS to house your information.
As I said in the story, most registrars make this available for free or for a nominal fee. Hence, there is no need for a law that that calls for the removal of all public WHOIS info.
It’s not about faith: If you were threatened and harassed enough as I am, you would do the same. The point is, there are options available, although most people ignore this and give away their information unnecessarily here and there and then wonder why they have no privacy. For better or worse, if you wish to achieve and maintain privacy online, you have to work at it, and that means taking active steps to do so — and it especially means not expecting someone else or something else to do it for you, because in all likelihood they won’t (or they’ll try and fail).
I totally see your point where you get harassed and threaten by foreign actors in some cases. I did take that into consideration in my previous comments, but a little disclosure would be nice none the less.
Well, enough about that. by the way, can you make a mobile site of your page? It is hard to read your page on a small screen with a phone.
Also, move away from WordPress sites. I mean, you’re in technology for crying out loud. 🙂
Brian – I see your point since you are harassed and attacked often even by foreign actors. I did consider this in my previous point. But, a little disclosure would be nice none the less.
Well, enough about that. Now, can you make a mobile version of your site? It is pretty difficult to read your site on a small device.
Also, get away from WordPress! You are in technology for crying out loud! 🙂
James, you should probably refrain from making blanket statements like that about WordPress unless you have some stats handy to back it up. There’s nothing inherently insecure about WordPress vis-a-vis other CMS platforms; it’s one of the most popular, which means it’s also going to have more than its fair share of users who have no idea how to run a secure site.
Also, in my experience many, many sites — including WP sites — get hacked because they are running outdated, unsupported or backdoored plugins, or they just fail to install WP security updates in a timely manner.
Brian, I do! When I was learning PHP, I found cookies from WordPress that were extremely well hidden and hard to get rid off. I never used PHP again. But if you like them, you like them so that’s that.
What about a mobile site?
I always felt it strange we as internet users see very little problem with social sites having a lot of private information about us. But we clearly take the opposite opinion of government and law enforcement having access to protect us. The EU seems to trust nobody and insist in being the self proclaimed protector of everyone’s privacy. It’s probably not been thought out very well, and could come back to bite them in the future. These blanket policies never address the potential side effects of making such laws.
The EU is clearly not a “self proclaimed protector”. It’s quite the contrary. Instead of having some entity decide what to do with your personal information, GDPR grants you the right to “freely consent” and ensures you know how your info would be used should you want to provide it.
The good old I claim the right to do whatever so you all don’t have the right of privacy.
Let’s face it. Bad guys rarely use their real name or address to register a domain. In fact, anybody not wanting to disclose their own private data can easily fake their identity or use a lucrative privacy service.
The problem is not privacy, but less information being available for public researchers.
If security researchers cared so much about private data then they should have put more effort in enforcing that information being correct and verified before any registry accepted it as whois data. And as such there would not be any privacy service and less fake private data.
However, like Krebs, many researchers who love to have a peek at any private data are pretty fond of hiding their own data from the public.
“Let’s face it. Bad guys rarely use their real name or address to register a domain. In fact, anybody not wanting to disclose their own private data can easily fake their identity or use a lucrative privacy service.”
That doesn’t really change the value of the information. How many times have you seen Brian track the movements of one criminal or another through multiple layers of aliases?
Just as you can be assured people won’t use their real names if they mean to be up to shady things, you can be assured a lot of people are considerably less clever at OpSec than they think they are.
I dunno what the “I claim the right to do whatever” gambit is, but I’m firmly in the camp of people that believes that- if you want a public-facing resource that is to be trusted by that same public- you need to identify yourself in some meaningful fashion. The internet in general suffers from far too much ‘muddying’ of the chain of responsibility already.
Additionally, having looked at the GDPR (in particular it’s “Right to be Forgotten” mentality), I’m somewhat inclined to feel the people who came up with it lack some pretty fundamental understanding of how the Internet works.
+1.
I see a lot of people reasoning that criminals won’t use real information. That is beside the point. If you’ve ever done an investigation that starts with an email address provided in a domain registration and works backwards from there (reverse whois search, eg.) you’ll know that there are usually telling patterns that emerge even when crooks are providing patently false or misleading info.
Imagine if you are a scammer who’s in the habit of registering hundreds of domains for phishing scams and spams each week: Are you going to use different details and email addresses for each one? Nope. Honestly, I think most people commenting on this aspect of WHOIS just have never observed this dynamic in action.
As Skunkwerks said, the vasty majority of cybercriminals simply are not that good or invested in hiding their tracks or identities, and even the few who are get sloppy. And very often those mistakes show up in WHOIS records.
This whole line of argument seems inconsistent. Or rather, the new EU laws are a red herring in this entire debate. Let’s break it down.
1. De-identified domain registration is already available, either for free or a small charge, depending on the registrar used.
2. Law enforcement can subpoena the actual records even if they are publicly de-identified.
3. “Security researchers” (AKA private citizens with a greater interest but no greater rights to the underlying data) make use of mistakes made by sloppy scammers who fail to use de-identified registrations.
4. As I understand it, the new EU laws are more or less mandating the equivalent de-identification that is already optionally available (point 1).
It’s hard to view this blog post as much more than a complaint that the EU laws will make your job more difficult, yet really what you are doing is exploiting sloppiness on the part of scammers.
It’s a kind of competency arbitrage. You exploit it as long as you can but you don’t have any particular “right” to it.
Don’t get me wrong, you and others like you perform a useful service but really this just means the whole model is wrong, since it can be undermined simply by scammers getting a bit wiser.
Isn’t the takeaway here that the function performed by private security researchers would be better performed by adequately resourced law enforcement agencies? The idea of formally or informally “deputizing” private entities to undertake what is ultimately the state’s responsibility seems flawed – and differs only from private militia and vigilantism by the promise that it will be used for good instead of evil!
“…since it can be undermined simply by scammers getting a bit wiser.”
One could argue much of Information Security could benefit from the same seemingly Common Sense strategem.
And yet the stories we hear- in any decade- constantly uncover gross negligence.
Sloppiness, in other words.
In other words, I’m suggesting this is perhaps less of a “unique” set of circumstances than you’re making it out to be here. This seems to be the normative modus operandi for people on BOTH sides of the line.
“…since it can be undermined simply by scammers getting a bit wiser.”
One could make an argument suggesting that people on the Whitehat side of that fence could greatly benefit from this seemingly simplistic posture towards information security as well.
In any decade of the craft, the news is absolutely saturated with stories- not of “things no one- even with the most advanced understanding of the field- could have seen coming”, but with tales of gross negligence at the most basic levels.
Indeed the most successful hacks usually leverage the most simplistic- the most LOW tech- innovations one can imagine.
So what then do we make of the argument that “hackers and criminals could circumvent your methods by just being smarter”?
The fact of the matter is people on both sides of the line- and at ALL levels of (presumed) expertise- continually fail at pretty basic OpSec.
That being the case, it doesn’t seem like a troublesome approach at all to count on that kind of “sloppiness”.
Sure, but at that point we have to weigh up the net benefit to society of improved privacy for everybody, vs the impact on society (through hampering the work of “security researchers”) of that “everybody” including scammers.
I was reaching a bit with my final paragraph above, but it’s interesting to think about. What other area of crime detection and prevention relies so heavily on non-state actors? What is it about internet fraud and associated scams that causes so much responsibility for evidence gathering to fall on private citizens (or companies, such as google, microsoft etc) with an interest and ability to do so? It would be interesting to know just how much of this gets shut down without any law enforcement involvement at all.
The cynical answer might be that regular law enforcement is grossly under-equipped and under-resourced to do it.
More nuanced is possibly the trans-national nature of most of these acts.
And then pragmatically it’s also the fact that online privacy is such a shambles that things like WHOIS non-privacy makes it possible for private sleuths to have a significant impact.
“Sure, but at that point we have to weigh up the net benefit to society of improved privacy for everybody, vs the impact on society (through hampering the work of “security researchers”) of that “everybody” including scammers.”
It’s possibly this is through no intention of your own, but as Brian pointed out (and myself again), this is a false choice.
Or maybe the more apt thing to say is: the choice has already been made- whether you know it or not, and not even by the parties you think have made the choice for you here.
The bare minimum of information used in domain name registry is ROUTINELY leaked by lots of organizations and systems you implicitly trust every day (re: sloppiness; also: misunderstood expectations of security).
This is so common that- if you’re not assuming these are common knowledge by DEFAULT- you’re being foolish.
And herein lies my problem with the precepts of the GDPR that seem to be driving this debate- they are absolutely RIFE with this kind of foolishness.
So
It is not besides the point we public security researchers claim a right to investigate based on (private) data even if most bad guys do not use their own private data. Yes we researchers like to use any data, but what right do we have to deny others their privacy? If we wanted such rights we should have turned these claim in to law. We failed to do so. As sucht we fail to secure. Now we researchers are wining a large group of people is claiming a stronger enforcment of their existing rights of privacy by law in Europe while we did effectively nothing in the past to mitigate our dependency.
Indeed the world is bigger than Europe. However, in Europe privacy is already a right part of some constitutions in Europe. World wide over 150 national constitutions mention the right to privacy. The GDPR is merly a stronger enforcement regarding existing rights in Europe. The rights of 516 milion people.
Complaining law makers do not understand how the internet works by defining stronger regulations to enforce already existing rights such as a right to be forgotten is imho a miserable interpretation by ignore why laws exist in the first place.
Like Jan Peeters mentioned, there are also already many different policies. Many tld’s have privacy by default, only some forbid privacy and many organisations do not enforce any of these rules for sake of easy trade. Even while privacy laws were already in place in many countries the operators are based in. I consider it luck we all are able to be able to access data publicly. We fail to secure our information position by complaining.
“Those who would give up essential Liberty, to purchase a little temporary Safety, deserve neither Liberty nor Safety.”
-Ben Franklin
Almost every time government gets involved, it makes things worse. Although I like the concept of privacy, having a government come up with the rules is certain a bad idea.
Those that are talking about Liberty vs Security, you actually have a CHOICE right now whether you want to pay for the increased security (i.e. privacy), or go the cheaper route and have your information public. THAT is the Liberty option. Having a government force everyone into privacy REMOVES the choice. I think many people are missing that fact…
So basically I agree with Brian, but not because it helps track down “bad actors”. I agree with keeping us all more free, by not allowing a government body to create yet more rules that we must follow.
The good old it is the government to blame.
I hope anybody in the security community in the future starts getting involved in defining laws instead of complaining when the are defined. It is way to easy to blame the government instead of blaming our self to fail to secure a position. Reading the article of Krebs and many responders I can not ignore the fact many are ill informed, dont care about issues if there is no problem yet and have their own agenda to complain.
GDPR does not remove choice. It just enforces it. If you want someone to have your info, you can consent and hand it over.
The idea that privacy should be a product has always been a bad one.
In its agreement with Registrars (Godaddy, Network Solutions, eNom, etc.) ICANN makes a provision to profit off the whois database:
““In the event that ICANN determines, following analysis of economic data by an economist(s) retained by ICANN (which data has been made available to Registrar), that an individual or entity is able to exercise market power with respect to registrations or with respect to registration data used for development of value-added products and services by third parties, Registrar shall provide third-party bulk access to the data subject to public access under Subsection 3.3.1 under the following terms and conditions:
3.3.6.1 Registrar shall make a complete electronic copy of the data available at least one (1) time per week for download by third parties who have entered into a bulk access agreement with Registrar.
3.3.6.2 Registrar may charge an annual fee, not to exceed US$10,000, for such bulk access to the data.”
– https://www.icann.org/resources/pages/approved-with-specs-2013-09-17-en
To that end, Godaddy’s terms to Registrants (you, me, Brian, anyone who registers a domain name) state:
“By providing your telephone or mobile number, you consent to receive marketing telephone calls from or on behalf of GoDaddy that may be initiated by an automatic telephone dialing system and/or use an artificial or prerecorded voice.”
And:
“By providing your mobile number, you consent to receive marketing text messages from or on behalf of GoDaddy that may be sent by an automatic telephone dialing system.”
Here is the kicker:
“Message and data rates may apply.”
– https://www.godaddy.com/legal-agreements.aspx