Back in April 2015, I tweeted about receiving a letter via snail mail suggesting the search engine rankings for a domain registered in my name would suffer if I didn’t pay a bill for some kind of dubious-looking service I’d never heard of. But it wasn’t until the past week that it become clear how many organizations — including towns, cities and political campaigns — actually have fallen for this brazen scam.
The letter I tweeted about was from a company called Web Listings Inc., and it said I should pay a $85 charge for an “annual web site search engine” service.
The first clue that this was probably a scam was the letter said halfway down in capital letters “THIS IS NOT A BILL,” although it sure was made to look like one. Also, the domain it referenced was “fuckbriankrebs.com,” which was indeed registered using my street address but certainly not by me.
The sad truth is plenty of organizations *are* paying the people behind this charade, which is probably why Web Listings has been running it continuously for more than a decade. Most likely that’s because some percentage of recipients confuse this notice with a warning about a domain name they own that is about to expire and needs to be renewed.
We know plenty of people are getting snookered thanks to searchable online records filed by a range of political campaigns, towns, cities and municipalities — all of which are required to publicly report how they spend their money (or at least that of their constituents).
According to a statement filed with the Federal Election Commission, one of the earliest public records involving a payment to Web Listings dates back to 2008 and comes from none other than the the 2008 Hillary Clinton for President fund.
The documents unearthed in this story all came compliments of Ron Guilmette, a most dogged and intrepid researcher who usually spends his time tracking down and suing spammers. Guilmette said most of the public references he found regarding payments to Web Services Inc. are from political campaigns and small towns.
“Which naturally raises the question: Should we really be trusting these people with our money?” Guilmette said. “What kind of people or organizations are most likely to pay a bill that is utterly phony baloney, and that actually isn’t due and payable? The answer is people and organizations that are not spending their own money.”
Also paying $85 (PDF) to Web Listings was the 2015 campaign for Democrat Jim Kenney, the current mayor of Philadelphia.
A fund for the New York City Council campaign of Zead Ramadan (D) forked over $85 to Web Listings in 2013.
Also in 2013, the Committee to Elect Judge Victor Heutsche (D) paid $85 to keep his Web site in good standing with Web Listings. Paul T. Davis, a former Democratic state representative from Kansas handed $85 (PDF) to Web Listings in 2012.
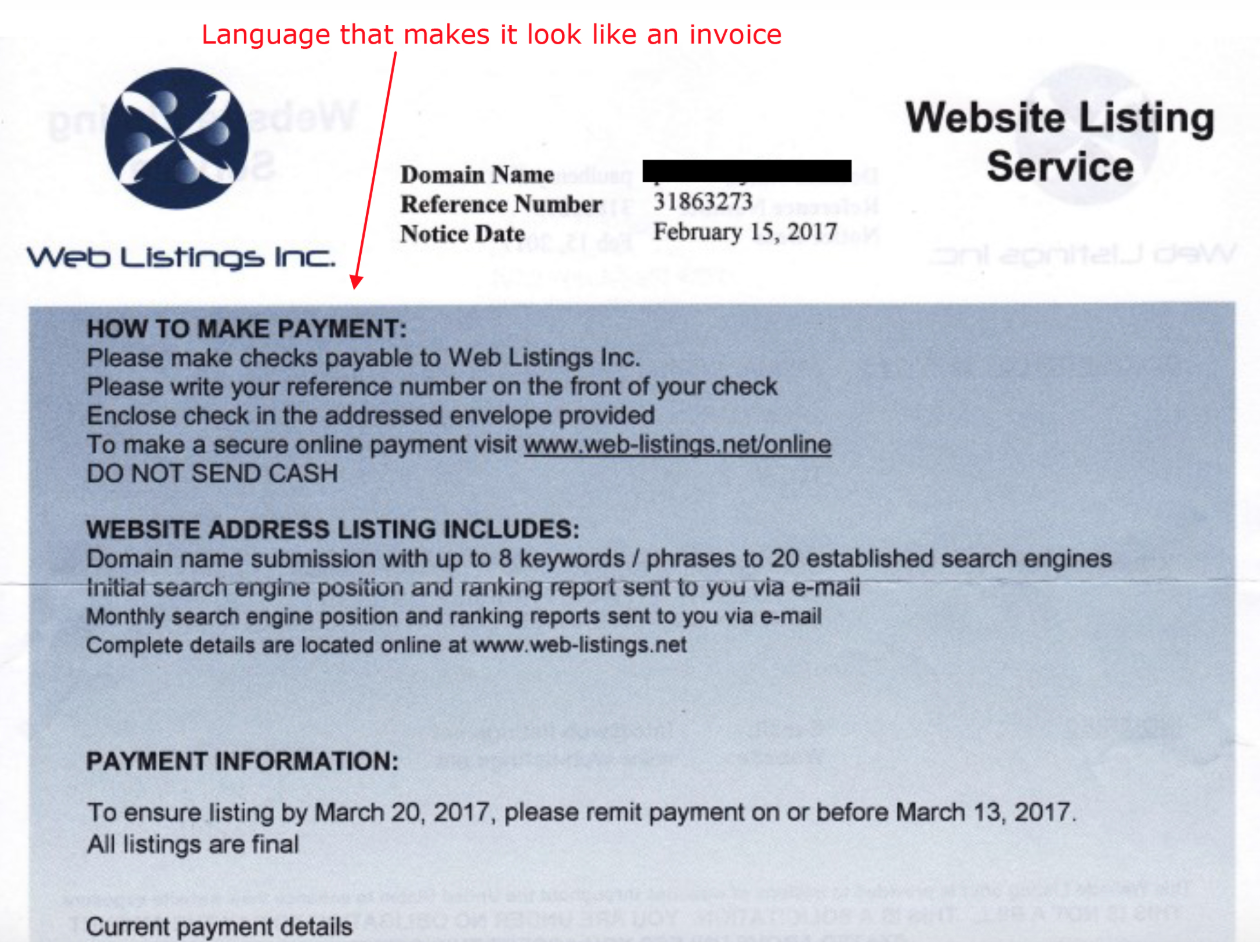
Image: Better Business Bureau.
Lest anyone think that somehow Democratic candidates for office are more susceptible to these types of schemes, a review of the publicly-searchable campaign payments to Web Listings Inc. uncovered by Guilmette shows a majority of them were for Web sites supporting Republican candidates.
The Friends of Mike Turzai committee spent $65 in 2010 on the GOP Representative from Pennsylvania.
The fundraising committee for Republican Dick Black‘s 2012 campaign for the Virginia Senate also paid Web Listings Inc. $85. The campaign to elect Ben Chafin as a Republican delegate in Virginia in 2013 also paid out.
Robert Montgomery, a former GOP state representative in Kansas, paid $85 (PDF) to Web Listings in 2012.
Those in charge of the purse strings for the “Friends of GOP New York State Senator Tom Croci” fund paid $65 in 2011 to keep his political Web site full of search engine goodness.
Paying $85 each to Web Listings in 2012 were the judicial campaigns for Louisiana GOP Judge John Slattery, and Lynn Donald Stewart, who successfully got re-elected to the Nevada state assembly that year.
Perhaps the most reliable customers of Web Listings’ dubious services have been cities, towns and municipalities across the United States. Somehow, the people in charge of the purse strings for Simpson County, Kentucky paid $85 notices from Web Listings Inc. three years in a row (2016, 2017 and 2018).
Other state and local governments that paid Web Listings for their imaginary services include El Paso County in Texas; the city council of Watertown, S.D.; the City of Cudahy, Wisconsin; the Village of Bedford Park in Cook County, Illinois; the city council in Osawatomie, Kansas; the board of supervisors in Clarke County, Iowa; Lake County, Colorado; the Morenci Areas Schools in Morenci, Michigan.
Guilmette even found a number of bankruptcy cases where a creditor named “Web Listings, Inc.” was listed, with an amount owed being either the old price of $65.00 or else the new price of $85.00, including a creditor in the University General Health System, Inc. et. al. bankruptcy (PDF); Blue Ridge Wood Products Inc.; and an organization called Advanced Solids Control LLC (PDF).
A review of the complaints about Web Listings Inc. left over the past few years at the Better Business Bureau suggests that many recipients of this scam are confusing the mailer with a late payment notice from their domain registrar. As such, it’s likely this phony company has scammed a ridiculous number of consumers over the years, Guilmette observed.
“I’m sure they’ve conned a zillion other people who were spending their own money,” he said. “These are only the ones for which public records are available online.”
Stay tuned for Part Two of this story, which will look at some clues about who may be responsible for this long-running racket.





This is a tricky one. It clearly says it isn’t a bill. They offer to submit your URL to a number of search engines. If they do that (a standard script) then they deliver the service. It might not do a lot for you, but that’s the offer.
As for the monthly reports – their site has a FAQ about why I haven’t got my reports – clearly a frequent enough question to feature. Their response: “Since the email address provided to us may have been written by hand, it’s possible that we couldn’t recognize your address, or that your email box had problems at the time we tried to contact you. To correct this issue please send us an email with your reference number and a request to resend your login information.” … and that’s how they can identify people that actually want the reports enough to follow up. Again, a script would make that relatively easy.
On this basis it would be hard to prosecute, and hard to make this operation go away. It’s arguable that it’s just a not very worthwhile but technically legal activity – if they do the submission and provide reports when you follow up and actually ask. Annoying though.
I think there are two key details:
1) While they may actually provide the service that they’re hawking, that service doesn’t actually have any value – it’s the digital equivalent of selling swampland in Florida (of course, that’s true of SEOs in general).
2) They market that service by attempting to mimic domain name renewal/expiration notices – in other words, selling a worthless service by trying to deliberately make it look like a different, legitimate. And it’s highly unlikely that anyone would pay for that service, if they weren’t deceived into doing so.
That said, I agree that it will be difficult to get anything done about it. The best solution I can think of would probably cross the line into grey-hat territory: deliberately make payments to them, and the immediately contest the charges so they get hit with charge-backs, which will cost them money and/or get them sh*tcanned by the payment processors. Not I ever do such a thing, or advocate for anyone else to do it – I certainly wouldn’t want anyone to get that idea. Nosiree.
I would so like to see if my employer ever paid them. I keep having to intercept their “bills” before the accounting folks pay them because marketing loses their mind over this “bill” every goddamn year. Of course every year its someone new falling for the exact same thing their predecessor fell for (might be why there’s a lot of turnover in marketing). I have a sneaking suspicion that before I came on board they were just getting paid.
I heard of/read similar blog entries on other security sites. They gather the information to send snail mail to you from DNS records (whois).
If you spend more money when extending the domains using higher privacy protection mechanism you will never get these snail mails.
Of course that depends how many domains you have and whether you can afford the extra dollars for the privacy protection …
If this is a one man show the person only needs to “sell” three of these a day for maybe 5 hours work per week day and have a reasonable income …
Im a bit confused by the two images. They seem to be identical. What am I missing?
Thanks, fixed that. Had the same image twice. Replaced it with the backside of the letter.
Noted.
I remember getting letters like this after registering a domain years ago (around 2003 I think and when SEO was just starting to be a thing more people were hearing about)
well researched article.. I am a regular reader of your site.. do you provide SEO related articles ??
I’ve been seeing this stuff regularly, off/and on for the last 2-3 years. I actually managed to get about a dozen domain names used by these scammers (or similar groups) shut down because they were stupid enough to use to use .NET domains – and using registrant/admin addresses via mail.com, who will (eventually…) shut down accounts, allowing me to file complaints with ICANN that the domains had invalid registration info. Though that’s now impossible thanks to the fecal theatre that is the GDPR (thanks for that EU!).
Last year, I started reporting them a bit more aggressively (as in manually de-obfuscating the redirects they hide behind), and doing a bit more digging into to see if I could spot anything interesting. One detail I noticed is that they all seem be using the domain name clickinject[dot]com, though hiding it behind redirects to evade spam filters, etc.
I also did some digging to see what payment processors they’re using. Almost all of them appear to be using either fthpay.com (which appears to be a fairly sketchy payment processor in Hong Kong/China), and surprisingly, Paypal. Or at least the fact that they were using Paypal WAS surprising, until I tried to report it to them & realized just how hopelessly incompetent Paypal is at dealing with the use of their service for fraud (at BEST – and at worst, they’re knowingly facilitating fraud while ALSO profiting from it).
I’ve reported it to Paypal back in April 2018, and over 8 months later, they still haven’t done ANYTHING to address it: there are two main Paypal accounts being used (the scammers are lazy/inept enough that you can find the EMail for the Paypal account in the source of their checkout page), and both are still active & still being actively being used to scam people. I tried reporting it to Paypal via Spamcop, but it turns out that they refuse to accept Spamcop reports. I tried report it on their support forum, it took them ages to reply – and the replies they did send were largely useless evasions, or telling me that I needed to jump through a bunch of hoops for an issue that’s their responsibility (referencing specific pages on their site, then being too lazy/inept to actually to them) – or whining that I had included “personal information,” AKA the EMail addresses of the scammer Paypal accounts. And when I tried to contact them about it on Twitter, I got the exact same run-around, pathetic excuses about how they “couldn’t receive [that] type of complaint via Twitter”… and more whinging about “personal information.” So it appears that Paypal is VERY concerned about protecting the throwaway freemail addresses used by scammers, while evidently being perfectly happy to allow the use of their service to defraud people.
I’ve made sure to save the details – I’d be happy to provide them if you’re interested.
routing@paypal.com ? It’s listed for abuse by ARIN.
Thanks, I’ll give the routing@ address a try – amusingly (but completely unsurprisingly), that address doesn’t appear to be listed ANYWHERE on Paypal’s website… or at least I get no results when googl’ing:
“routing@paypal.com” site:paypal.com
Send BK a tip.
Click on “About the author,” at the top/right of this page.
I went back and checked some of the EMails I’ve received for these, and it looks like there’s actually (at least) two separate groups running a similar scam. The ones with links that ultimately redirect to clickinject.com seem to have started more recently, they’re the ones using fthpay.com as their payment processor.
The other group appears to be piggybacking off legitimate sites that were compromised/hacked – at least, judging from the fact that the scam pages are all in a “/domain/” sub-directory & the sites themselves appear to be completely unrelated, E.g.
http://withvogue.com.au/domain/
http://harshproperties.com/domain/
https://divyashaktipeeth.org/domain/
https://autoklen.com/domain/
Those are the ones that are all using Paypal. Aside from the identical scam pages on all of them, they’re all using one of two Paypal EMails – so they’re clearly connected. The scammer accounts are:
exaltka@gmail.com
info@internetbirodalom.hu
One other detail I noticed is that almost all of the sites appear to be for companies based in either India or Australia – and I’ve had a curiously consistent lack of response when I’ve contacted the site owners about the issue. That leads me to question whether the sites were actually hacked, or whether the site owners were paid off to allow the scam pages to be hosted on their sites – or scammed themselves. E.g. it wouldn’t surprise me in the least if those are all sites that hired sketchy Indian SEO providers, who then turned around & exploiting sites they’d been given access to in order to run their scam.
In some ways, I’d see the latter possibility as the best-case, especially if it lead to “don’t hire Indian SEO spammers, or your website will be hijacked by scammers.” Maybe not entirely accurate, but I’m A-OK with anything that helps choke off the revenue stream for those worthless parasites.
http://www.paypal.com/us/smarthelp/contact-us “Email Us” at bottom.
I run spam IPs through (such as):
https://fortiguard.com/learnmore#as (to see if I need to forward)
http://www.sophos.com/en-us/labs.aspx (to see if I need to forward)
http://ipremoval.sms.symantec.com/lookup (to see if I need to forward)
http://www.dnsbl.info (to check barracuda to see if I should forward to ironport)
I’ve contacted Paypal about it numerous times – via Spamcop reports (before they started refusing to accept those), their contact pages, their labyrinthine abuse reporting process, and via Twitter. And they’ve done nothing about it in the 7-8 months since, so I get a fairly strong impression that they simply don’t care & are perfectly to happy to knowingly allow it to continue.
It’s pretty clear that these are solicitations, not invoices or bills.
Many of our leaders are idiots, apparently.
Are you exposing yourself as anti-democratic? You could turn more than 50% of this country against your bigoted website.
I suppose you could not obtain an republican payment details as they are anti-transparent and definitely not democratic.
The author gave examples of Democrats and Republicans being idiots. The website isn’t bigoted.
Oh, you’re a jackhole.
Not sure how you came to this conclusion, as there are at least five paragraphs in the story dedicated to discussion GOP campaigns that fell for the scam.
Shades of Brandon Gray Internet Services.
https://en.wikipedia.org/wiki/Brandon_Gray_Internet_Services
This sort of scam’s been going on a looooooooooooong time.