Two of the most disruptive and widely-received spam email campaigns over the past few months — including an ongoing sextortion email scam and a bomb threat hoax that shut down dozens of schools, businesses and government buildings late last year — were made possible thanks to an authentication weakness at GoDaddy.com, the world’s largest domain name registrar, KrebsOnSecurity has learned.
Perhaps more worryingly, experts warn this same weakness that let spammers hijack domains tied to GoDaddy also affects a great many other major Internet service providers, and is actively being abused to launch phishing and malware attacks which leverage dormant Web site names currently owned and controlled by some of the world’s most trusted corporate names and brands.

In July 2018, email users around the world began complaining of receiving spam which began with a password the recipient used at some point in the past and threatened to release embarrassing videos of the recipient unless a bitcoin ransom was paid. On December 13, 2018, a similarly large spam campaign was blasted out, threatening that someone had planted bombs within the recipient’s building that would be detonated unless a hefty bitcoin ransom was paid by the end of the business day.
Experts at Cisco Talos and other security firms quickly drew parallels between the two mass spam campaigns, pointing to a significant overlap in Russia-based Internet addresses used to send the junk emails. Yet one aspect of these seemingly related campaigns that has been largely overlooked is the degree to which each achieved an unusually high rate of delivery to recipients.
Large-scale spam campaigns often are conducted using newly-registered or hacked email addresses, and/or throwaway domains. The trouble is, spam sent from these assets is trivial to block because anti-spam and security systems tend to discard or mark as spam any messages that appear to come from addresses which have no known history or reputation attached to them.
However, in both the sextortion and bomb threat spam campaigns, the vast majority of the email was being sent through Web site names that had already existed for some time, and indeed even had a trusted reputation. Not only that, new research shows many of these domains were registered long ago and are still owned by dozens of Fortune 500 and Fortune 1000 companies.
That’s according to Ron Guilmette, a dogged anti-spam researcher. Researching the history and reputation of thousands of Web site names used in each of the extortionist spam campaigns, Guilmette made a startling discovery: Virtually all of them had at one time received service from GoDaddy.com, a Scottsdale, Ariz. based domain name registrar and hosting provider.
Guilmette told KrebsOnSecurity he initially considered the possibility that GoDaddy had been hacked, or that thousands of the registrar’s customers perhaps had their GoDaddy usernames and passwords stolen.
But as he began digging deeper, Guilmette came to the conclusion that the spammers were exploiting an obscure — albeit widespread — weakness among hosting companies, cloud providers and domain registrars that was first publicly detailed in 2016.
EARLY WARNING SIGNS
In August 2016, security researcher Matthew Bryant wrote about a weakness that could be used to hijack email service for 20,000 established domain names at a U.S. based hosting provider. A few months later, Bryant warned that the same technique could be leveraged to send spam from more than 120,000 trusted domains across multiple providers. And Guilmette says he now believes the attack method detailed by Bryant also explains what’s going on in the more recent sextortion and bomb threat spams.
Grasping the true breadth of Bryant’s prescient discovery requires a brief and simplified primer on how Web sites work. Your Web browser knows how to find a Web site name like example.com thanks to the global Domain Name System (DNS), which serves as a kind of phone book for the Internet by translating human-friendly Web site names (example.com) into numeric Internet address that are easier for computers to manage.
When someone wants to register a domain at a registrar like GoDaddy, the registrar will typically provide two sets of DNS records that the customer then needs to assign to his domain. Those records are crucial because they allow Web browsers to figure out the Internet address of the hosting provider that’s serving that Web site domain. Like many other registrars, GoDaddy lets new customers use their managed DNS services for free for a period of time (in GoDaddy’s case it’s 30 days), after which time customers must pay for the service.
The crux of Bryant’s discovery was that the spammers in those 2016 campaigns learned that countless hosting firms and registrars would allow anyone to add a domain to their account without ever validating that the person requesting the change actually owned the domain. Here’s what Bryant wrote about the threat back in 2016:
“In addition to the hijacked domains often having past history and a long age, they also have WHOIS information which points to real people unrelated to the person carrying out the attack. Now if an attacker launches a malware campaign using these domains, it will be harder to pinpoint who/what is carrying out the attack since the domains would all appear to be just regular domains with no observable pattern other than the fact that they all use cloud DNS. It’s an attacker’s dream, troublesome attribution and an endless number of names to use for malicious campaigns.”
SAY WHAT?
For a more concrete example of what’s going on here, we’ll look at just one of the 4,000+ domains that Guilmette found were used in the Dec. 13, 2018 bomb threat hoax. Virtualfirefox.com is a domain registered via GoDaddy in 2013 and currently owned by The Mozilla Corporation, a wholly owned subsidiary of the Mozilla Foundation — the makers of the popular Firefox Web browser.
The domain’s registration has been renewed each year since its inception, but the domain itself has sat dormant for some time. When it was initially set up, it took advantage of two managed DNS servers assigned to it by GoDaddy — ns17.domaincontrol.com, and ns18.domaincontrol.com.
GoDaddy is a massive hosting provider, and it has more than 100 such DNS servers to serve the needs of its clients. To hijack this domain, the attackers in the December 2018 spam campaign needed only to have created a free account at GoDaddy that was assigned the exact same DNS servers handed out to Virtualfirefox.com (ns17.domaincontrol.com and ns18.domaincontrol.com). After that, the attackers simply claim ownership over the domain, and tell GoDaddy to allow the sending of email with that domain from an Internet address they control.
Mozilla spokesperson Ellen Canale said Mozilla took ownership of virtualfirefox.com in September 2017 after a trademark dispute, but that the DNS nameserver for the record was not reset until January of 2019.
“This oversight created a state where the DNS pointed to a server controlled by a third party, leaving it vulnerable to misuse,” Canale said. “We’ve reviewed the configuration of both our registrar and nameservers and have found no indication of misuse. In addition to addressing the immediate problem, we have reviewed the entire catalog of properties we own to ensure they are properly configured.”
According to both Guilmette and Bryant, this type of hijack is possible because GoDaddy — like many other managed DNS providers — does little to check whether someone with an existing account (free or otherwise) who is claiming ownership over a given domain actually controls that domain name.
Contacted by KrebsOnSecurity, GoDaddy acknowledged the authentication weakness documented by Guilmette.
“After investigating the matter, our team confirmed that a threat actor(s) abused our DNS setup process,” the company said in an emailed statement.
“We’ve identified a fix and are taking corrective action immediately,” the statement continued. “While those responsible were able to create DNS entries on dormant domains, at no time did account ownership change nor was customer information exposed.”
SPAMMY BEAR
Guilmette has dubbed the criminals responsible as “Spammy Bear” because the majority of the hijacked domains used in the spam campaigns traced back to Internet addresses in Russia.
In the case of Mozilla’s Virtualfirefox.com domain, historic DNS records archived by Farsight Security show that indeed on Dec. 13, 2018 — the very same day that spammers began blasting out their bomb threat demands — the Internet address in the domain’s DNS records at GoDaddy were changed to 194.58.58[.]70, a server in the Russian Federation owned by a hosting company there called Reg.ru.
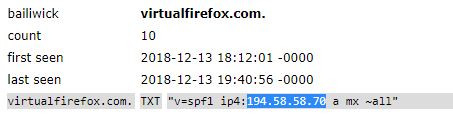
The record above, indexed by Farsight Security, shows the DNS entries for virtualfirefox.com were changed to allow sending of email from an ISP in Russia on Dec. 13, 2018, the same day spammers used this domain and thousands of others for a mass emailed bomb threat.
In fact, Guilmette found that that at least 3,500 of the commandeered domains traced back to Reg.ru and to a handful of other hosting firms in Russia. The next largest collection of fraudulently altered Internet addresses were assigned to hosting providers in the United States (456), although some of those providers (e.g. Webzilla/WZ Communications) have strong ties to Russia. The full list of Internet providers is available here.
Guilmette’s sleuthing on the 4,000+ domains abused in both 2018 spam campaigns, combined with data from Farsight, suggest the spammers hijacked domains belonging to a staggering number of recognizable corporations who used GoDaddy for DNS, including but not limited to:
Abbott Laboratories; Ancestry.com; Autodesk; Capital One; CVS Pharmacy; SSL provider Digicert; Dow Chemical; credit card processors Elavon and Electronic Merchant Systems; Fair Isaac Corp.; Facebook; Gap (Apparel) Inc; Fifth Third Bancorp; Hearst Communications; Hilton Interntional; ING Bank; the Massachusetts Institute of Technology (MIT); McDonalds Corp.; NBC Universal Media; NRG Energy; Oath, Inc (a.k.a Yahoo + AOL); Oracle; Tesla Motors; Time Warner; US Bank; US Steel Corp.; National Association; Viacom International; and Walgreens.

In an interview with KrebsOnSecurity, Bryant said the hijacking technique can be a powerful tool in the hands of spammers and scammers, who can use domains associated with these companies not only to get their missives past junk and malware filters, but also to make phishing and malware lures far more believable and effective.
“This is extremely advantageous to attackers because they don’t have to pay any money to set it all up, and there’s a strong reputation attached to the domain they’re sending from,” Bryant said. “A lot of services will flag email from unknown domains as high risk, but the domains being hijacked by these guys have a good history and reputation behind them. This method also probably greatly complicates any sort of investigatory efforts after the spam campaign is over.”
WHAT CAN BE DONE?
Guilmette said managed DNS providers can add an extra layer of validation to DNS change requests, checking to see if a given domain already has DNS servers assigned to the domain before processing the request. Providers could nullify the threat by simply choosing a different pair of DNS servers to assign to the request. The same validation process would work similarly at other managed DNS providers.
“As long as they’re different, that ruins this attack for the spammers,” Guilmette said. “The spammers want the DNS servers to be the same ones that were already there when the domain was first set up, because without that they can’t pull of this hack. All GoDaddy has to do is see if this particularly odd set of circumstances apply in each request.”
Bryant said after he published his initial research in 2016, a number of managed DNS providers mentioned in his blog posts said they’d taken steps to blunt the threat, including Amazon Web Services (AWS), hosting provider Digital Ocean, and Google Cloud. But he suspects this is still a “fairly common” weakness among hosting providers and registrars, and many providers simply aren’t convinced of the need to add this extra precaution.
“A lot of the providers are of the opinion that it’s down to a user mistake and not a vulnerability they should have to fix,” he said. “But it’s clearly still a big problem.”
Update, 10:38 p.m.: An earlier version of this story stated that Guilmette had identified more than 5,000 domains associated with the Spammy Bear campaigns. The true number is closer to 4,000. The discrepancy was my mistake and due to a formatting error in a spreadsheet. Also added text to clarify that not all of the domains were registered through Godaddy, but that all of them at one point at least received managed DNS service from the company.




I am a former godaddy user that got sextortion email. The password was something I recall was suggested for me. I haven’t used words in passwords for years, but did a decade ago.
The sextortion email was stupid. It claimed my email password was changed, which of course means if so I couldn’t read my email. Norman coordinate.
I researched the bitcoin address and it had two recent payments. Sad!
I got such a mail with an empty password 😉
The sextortion mail I got sent me an empty password claiming that I used this one 😉
Hi there, I have a domain parked at Godaddy. Its basically (my personal name) dot com. I have no email services from them, will I be affected?
Is bluehost.com affected too?
Since circa July 2018, I receive on the average 2 sextortion emails/day, across 3 different domain email addresses I’ve had since 1996 or so (same domain). The initial ones showed passwords, which were at least 10+ years old. Over time, and fast forwarding to today (01-22-2019), they are not even including a password, and the format (as such) is ever changing, lol. They are quick to note “I sent it from YOUR email address”, lol !
The original ones claimed to have embedded a ‘tiny pixel’ such that as soon as I read the email, they would know … via the ‘beacon’ concept I suppose. I looked at the source of the very first one of these I received, I could not see anything the equated to a graphic image (return) path.
But from that point on … in the Outlook folders I have that these (spam) emails come into, I do go into Offline Mode just in case … and just delete most of the, although I do save some in a special folder.
= = =
It would seem that Anonymous or a similar greyhat group could use such tactics to turn around and bombard the (ignorant?) enablers of the bad guys with endless spam. One would speculate that reg.ru would set up some type of automatic blocking on their end if everyone with an @reg.ru email address starting receiving spam from their own domain. Then perhaps such automated blocking would help prevent similar attacks directed at the general public. If reg.ru was monitoring their network, wouldn’t they see the large increase in activity and realize something is amiss? If they did and didn’t care to stop being the tool of the scammer spammers, then Anonymous might want to punish them.
So much spam ties back to Godaddy and Namecheap and their automated processes that involve zero human oversight.
(Phony restaurant websites, too).
In the physical world, if I rent out office space and a mailbox to people I know or should’ve known are scammers, I’d be liable.
The same principle should apply to domain registrars who fail to investigate customers before transferring existing domains or creating new domains.
It’s the automated, instant process that needs to be interrupted, if it’s to have any effect on reducing spam and scams. If I were Emperor, I’d (1) require a waiting period for any new domain or transfer, and (2) require payments be made by bank cashier check.
Yeah, I have to say I agree with this analysis. There is just no required rigor for who gets a domain, or how.
I’d make a joke about checking pulses, but I think the bar is even lower than that here.
One promising development is a recent change to Canada’s anti-spam laws, to hold providers liable if they fail to take action to prevent spamming from their systems – or fail to take action when it’s reported to them.
I’m getting ready to file a CASL-violation complaint against LinkedIn on those grounds, after they allowed some idiot Indian SEO/web dev spammer to repeatedly send me invitations (to an obvious honeypot address, no less), even after I clicked unsubscribe for each one.
I always report the bitcoin address on https://bitcoinwhoswhodotcom/scams lately I get two or three a week
Also here
https://www.bitcoinabuse.com/reports/create
godaddy is sketchy. Every good site I search for with their tools gets’ registered the NEXT DAY if I don’t register it. They obviously have an internal auction site for “unclaimed” domains.
Well, since GoDaddy has to pay ICANN $0.10/yr for each domain, you should continue to search for crappy, garbage domains and cause DOLLARS and DOLLARS of costs to GoDaddy! :3
On a more serious note, Network Solutions was doing that very thing about a decade ago… perhaps they still are.
This practice is called “Front Running” or “Domain Name Front Running”.
I do not expect GoDaddy is front running, but if you have examples, I’d love to dig into it further. To note, often times, the domain name is already registered (for many years) and GoDaddy may return an “Available” message in error. It also sells domains already owned by somebody and this message can come across as “Available For Purchase”, meaning from the current owner and not just to register an “available” domain.
I have observed this before many years ago, but in my case I found that the corporate server egress point seemed to be monitored by… someone. Or perhaps at the whois they were monitoring who was inquiring, figuring a major corporation making a name inquiry meant big bucks. Using my home internet connection did not result in front running.
I’ve dealt with GoDaddy.com, regarding spam abuse for many years, almost on a weekly basis
Extortion Criminals USing what payment method?
Bitcoins?? and Where this money Goes??
this money end Up Where?
It would appear that for the few last rounds of the sextortion scam the perpetrators had bought themselves an address list that included something to the tune of 40,000 of my spamtrap addresses (https://www.bsdly.net/~peter/traplist_ethics.shtml) – a log extract for part of the period is at https://www.bsdly.net/~peter/anonymous-hacked.bare.log.
I’m happy to report that we kept them hanging around for a long time (typically 371 seconds (6 min 11 sec) per message. Only a few for aliases fairly early in the alphabet got through, apparently sent from previously unused hosts.
I’ll be sitting on the data for a little while to see whether an analysis will show up anything useful.
Thanks, Peter!
Have these attacks negatively impacted the reputation of the domains used?
“The full list of Internet addresses is available here.”
Unless I’m missing an area of the spreadsheet, there are no Internet addresses. It lists the “tophosts” of Internet addresses.
Yes, that was fixed earlier. You may want to refresh the page. The list of domains impacted is linked further up in the story.
https://docs.google.com/spreadsheets/d/1p_Eq_LW2zjNopntTGipzn9mOLMeyBqYLA4J0WEM8yVc/edit?usp=sharing
Quote:
Large-scale spam campaigns often are conducted using newly-registered or hacked email addresses, and/or throwaway domains. The trouble is, spam sent from these assets is trivial to block because anti-spam and security systems tend to discard or mark as spam any messages that appear to come from addresses which have no known history or reputation attached to them.
However, in both the sextortion and bomb threat spam campaigns, the vast majority of the email was being sent through Web site names that had already existed for some time, and indeed even had a trusted reputation.
UNQUOTE
That’s domain name reputation. No mention was made of Internet address reputation. The one provided spam source IP address 194.58.58[.]70 has a poor reputation with certain blocklists, currently, and could be blocked by IP address reputation.
I’ve logged just over 350 instances of this scam/spam. Mostly what I saw was IPs out of Southeast Asia, Eastern Europe, and Central America. Some Russian, but not the vast majority.
Only very rarely did they attempt to mask their origin in any way, and out of all that I only found a single instance of GoDaddy being used. Nothing for Bluehost, or Digital Ocean (which are common enablers as others have noted on other scores).
I also noticed a pattern. At first it started with passwords, and then it sort of morphed, at times whatever automated mechanism they were using to insert the password seemed to have broken, either supplying only part of, or none of the expected password.
Eventually it just devolved into a wildly-swerving missive with no passwords, and just the ranting/raving manifesto of a “MASTER HAXX0RZ” type script kiddy with a lot of “ripped-from-the-headlines”-type claims (I hijacked your webcam), to some old tried-and-true panic/freak-out tactics (I found child-porn on your hard drive) peppered in for good measure.
I feel like, at some level, this campaign was self-selecting. As in: it was aiming for the sort of audience that frequently reuses passwords, not very tech-savvy (but maybe half-reads a lot of tech news), and is therefore easily spooked.
Am I understanding that GoDaddy allows “new” customers to make changes to someone else’s domain records? That seems incredulous. How can they take control of the domain records before transferring the domain to their “new” account?
That’s what’s going on, yes. It allows them to add an SPF record for the domain to allow sending mail from an IP they control. Or, at least until GoDaddy implements whatever mitigations it says it’s going to implement.
Like “basic ethics” or “common sense”, maybe?
😉
Brian, reg the comment “A lot of the providers are of the opinion that it’s down to a user mistake and not a vulnerability they should have to fix,”:
How can this possibly be a user mistake? If anyone else than me makes any change whatsoever in a DNS zone I’ve bought (without authenticating as me) it’s indisputably the provider’s fault —an authorization failure.
Are we missing something here?
The problem is the way dns works. It’s a very distributed process.
Registrars enable users to populate WHOIS records which points to DNS servers
DNS servers allow one to populate DNS entries which point to IP addresses
Hosting providers offer computers which have IP addresses.
CAs issue certificates to entities based on proof of control of DNS records or the computers that DNS records point to.
This problem is that there isn’t really a way for a DNS operator to know that an account doesn’t belong to a given holder.
Even if at time (a) user (b) held the WHOIS for a given domain (c), a year later, that domain could have been transferred to user (d). So, it isn’t unreasonable for a DNS host to accept requests at time (e) by user (f) to provide DNS records for that same domain.
From where I’m sitting, I think DNS operators would basically have to provide a randomly generated value and require people to add that to WHOIS records in order to establish trust.
That’s similar to what CAs force DNS/server operators to do to establish trust.
Brian, is it correct to say that this attack was possible when there is NO currently registered DNS server for the given domain? (e.g., doing “dig ns noirecardcapitaloneventure.com” returns no results).
If so, then to the others… there is no reasonable way that a DNS provider could verify ownership of the domain, as one cannot use the usual Domain-, Web- or Email-based verification. There’s no NS record, so the domain is essentially unreachable.
If the domain was actulally registered with the provider (the company is both a DNS hoster, and a DNS registrar) then verification is easy. But what it looks like they’re doing is “No NS records? Okay, we’ll just believe you and publish to the DNS system that we contril the domain on your behalf.)
However, certainly much more can be done. E.g., “okay, you want to host your domain with us? Set up the records you want, then tell the registrar to add these two NS records to the “stub domain” and then we can act as an authority for that domain.
There may also be a fault in the automation for registration… There’s a backend protocol being used between the registrars and the DNS root servers for publishing stub records… If the root servers don’t verify that a registrar actually registered the domain it is publishing for, then this would enable this exact kind of attack.
No, the problem is that WHOIS actually pointed to GoDaddy and the new customer set up an account, checked to see if the account gave them access to the same servers (or more likely looked through the WHOIS for all the domains to see if it matched any of them).
Any DNS server can have records for any domain.
But a given end user computer won’t ask that DNS server about that domain.
Instead, a computer will generally speaking eventually get information from a DNS server associated w/ the WHOIS records for the domain. (There’s a certain amount of recursion here and potentially lots of caching, the computer talks to its DNS recursor which may talk to further DNS recursors who may talk to the TLD DNS server for the given TLD which has info based on the WHOIS records, and then it bubbles up to talk to the DNS server based on the WHOIS records.)
I’m wondering about whether GoDaddy would only accept new DNS settings if they didn’t have an active account for that domain (which is probably the question you were trying to ask), my guess is yes.
The method to stop the ‘beacon’ from working is simply to set your email application whether, Gmail or some other app, so that it asks before displaying external images. If the external image isn’t displayed, nothing gets sent back to the malicious server.
If disable external image display, as indicated above, you’ll see that images have these long character sequences attached to their URLs. That character sequence is a code that is assigned to the email address it was sent to, indicating that the email was opened. Asking for that image will guarantee more spam into your inbox.
Yepp I got one of those email on Jan 21 …sorry for anyone that falls for it.
Wouldn’t implementing DMARC serve as a protection for this?
Haven’t used it myself. Seemingly trusted sources, explanations and my hands-off understanding of it say yes.
http://www.google.com/search?hl=en&lr=lang_en&num=100&safe=active&q=will%20demarc%20prevent%20phishing
I got similar mail. The password they send me was used at only one place, at the website of sigma aldrich.