For almost the past month, key computer systems serving the government of Baltimore, Md. have been held hostage by a ransomware strain known as “Robbinhood.” Media publications have cited sources saying the Robbinhood version that hit Baltimore city computers was powered by “Eternal Blue,” a hacking tool developed by the U.S. National Security Agency (NSA) and leaked online in 2017. But new analysis suggests that while Eternal Blue could have been used to spread the infection, the Robbinhood malware itself contains no traces of it.
On May 25, The New York Times cited unnamed security experts briefed on the attack who blamed the ransomware’s spread on the Eternal Blue exploit, which was linked to the global WannaCry ransomware outbreak in May 2017.
That story prompted a denial from the NSA that Eternal Blue was somehow used in the Baltimore attack. It also moved Baltimore City Council President Brandon Scott to write the Maryland governor asking for federal disaster assistance and reimbursement as a result.
But according to Joe Stewart, a seasoned malware analyst now consulting with security firm Armor, the malicious software used in the Baltimore attack does not contain any Eternal Blue exploit code. Stewart said he obtained a sample of the malware that he was able to confirm was connected to the Baltimore incident.
“We took a look at it and found a pretty vanilla ransomware binary,” Stewart said. “It doesn’t even have any means of spreading across networks on its own.”
Stewart said while it’s still possible that the Eternal Blue exploit was somehow used to propagate the Robbinhood ransomware, it’s not terribly likely. Stewart said in a typical breach that leads to a ransomware outbreak, the intruders will attempt to leverage a single infection and use it as a jumping-off point to compromise critical systems on the breached network that would allow the malware to be installed on a large number of systems simultaneously.
“It certainly wouldn’t be the go-to exploit if your objective was to identify critical systems and then only when you’re ready launch the attack so you can do it all at once,” Stewart said. “At this point, Eternal Blue is probably going to be detected by internal [security] systems, or the target might already be patched for it.”
It is not known who is behind the Baltimore ransomware attack, but Armor said it was confident that the bad actor(s) in this case were the same individual(s) using the now-suspended twitter account @Robihkjn (Robbinhood). Until it was suspended at around 3:00 p.m. ET today (June 3), the @Robihkjn account had been taunting the mayor of Baltimore and city council members, who have refused to pay the ransom demand of 13 bitcoin — approximately $100,000.
In several of those tweets, the Twitter account could be seen posting links to documents allegedly stolen from Baltimore city government systems, ostensibly to both prove that those behind the Twitter account were responsible for the attack, and possibly to suggest what may happen to more of those documents if the city refuses to pay up by the payment deadline set by the extortionists — currently June 7, 2019 (the attackers postponed that deadline once already).
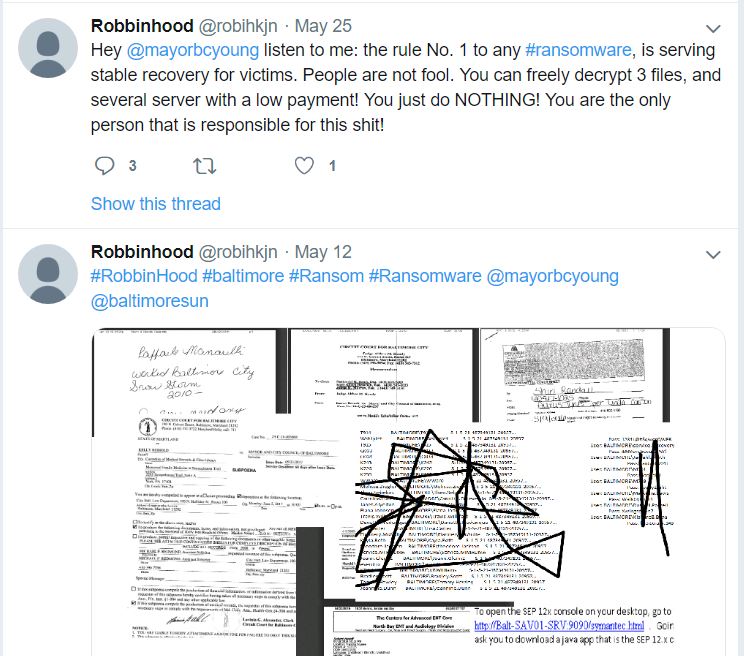
Some of @robihkjn’s tweets taunting Baltimore city leaders over non-payment of the $100,000 ransomware demand. The tweets included links to images of documents allegedly stolen by the intruders.
Over the past few days, however, the tweets from @Robinhkjn have grown more frequent and profanity-laced, directed at Baltimore’s leaders. The account also began tagging dozens of reporters and news organizations on Twitter.
Stewart said the @Robinhkjn Twitter account may be part of an ongoing campaign by the attackers to promote their own Robbinhood ransomware-as-a-service offering. According to Armor’s analysis, Robbinhood comes with multiple HTML templates that can be used to substitute different variables of the ransom demand, such as the ransom amount and the .onion address that victims can use to negotiate with the extortionists or pay a ransom demand.
“We’ve come to the conclusion Robbinhood was set up to be a multi-tenant ransomware-as-a-service offering,” Stewart said. “And we’re wondering if maybe this is all an effort to raise the name recognition of the malware so the authors can then go on the Dark Web and advertise it.”
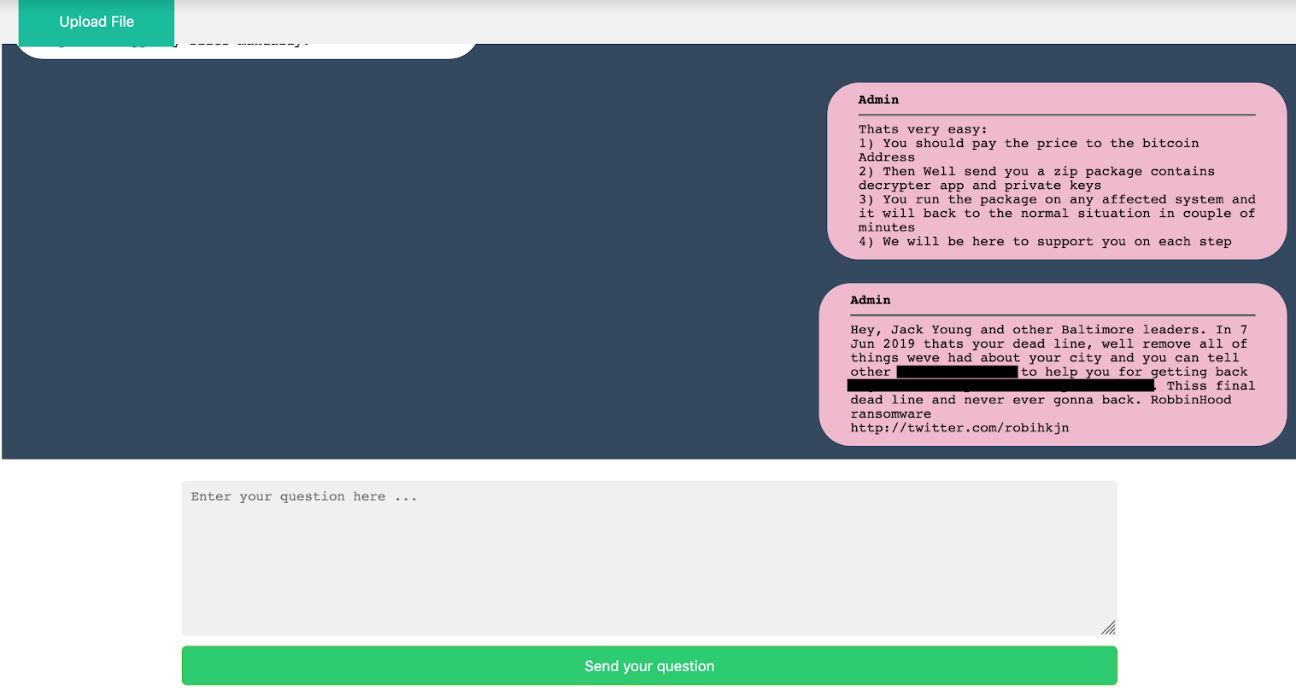
This redacted message is present on the Dark Web panel set up by the extortionists to accept payment for the Baltimore ransomware incident and to field inquiries or pleas from them. The message repeats the last tweet from the @robihkjn Twitter account and conclusively ties that account to the attackers. Image: Armor.
There was one other potential — albeit likely intentional — clue that Stewart said he found in his analysis of the malware: Its code included the text string “Valery.” While this detail by itself is not particularly interesting, Stewart said an earlier version of the GandCrab ransomware strain would place a photo of a Russian man named Valery Sinyaev in every existing folder where it would encrypt files. PCRisk.com, the company that blogged about this connection to the GandCrab variant, asserts Mr. Sinyaev is a respectable finance professional who has nothing to do with GandCrab.
The timing of the GandCrab connection is notable because just last week, the creators of GandCrab announced they were shutting down their ransomware-as-a-service product, allegedly after earning more than $2 billion in ransom payments.
Finally, since we’re on the subject of major ransomware attacks and scary exploits, it’s a good time to remind readers about the importance of applying the latest security updates from Microsoft, which last month took the unusual step of releasing security updates for unsupported but still widely-used Windows operating systems like XP and Windows 2003. Microsoft did this to head off another WannaCry-like outbreak from mass-exploitation of a newly discovered flaw that Redmond called imminently “wormable.”
That vulnerability exists in Windows XP, Windows 2003, Windows 7, Windows Server 2008 R2, and Windows Server 2008. In a reminder about the urgency of patching this bug, Microsoft on May 30 published a post saying while it hasn’t seen any widespread exploitation of the flaw yet, it took about two months after Microsoft released a fix for the Eternal Blue exploit in March 2017 for WannaCry to surface.
“Almost two months passed between the release of fixes for the EternalBlue vulnerability and when ransomware attacks began,” Microsoft warned. “Despite having nearly 60 days to patch their systems, many customers had not. A significant number of these customers were infected by the ransomware.”




How unsurprising that an incompetent, affirmative-action government would try to shift the blame.
Agreed. Just be careful saying that!
Your thinly veiled racism has no place in this discussion, or any discussion.
All: A quick google search reveals that Mr Digger has a habit of making racist and homophobic comments online. His “affirmative action” swipe is consistent with this pattern.
Someone has to monitor this total stranger’s behavior.
Thank goodness you stepped up, Jim.
Could you please explain where is the thinly veiled racism in that sentence?
Does that mean you think Baltimore’s city leadership is competent? Or just that only a “racist” could be against affirmative action?
A label is not an argument. “Racist” is a label.
Children, this website has always been a source of Brian’s straightforward, unbiased information and analysis. One of its added virtues has been the absence of irrelevant injections of petty politics and other non-constructive comments that undermine serious discussion.
Let’s try to keep it this way… and Brian, I hope you’ll feel free to exercise your right (as owner of this site) to delete posts that add nothing to the more serious exchanges that most of us have tried to have.
?
Agreed
Of course, Mr. Krebs doesn’t need our permission to moderate his own site, but I hope he will free free to delete ALL name-calling messages.
I agree. Some posts exists just to incite and troll whenever the word government is included in an article.
Politics are only “petty” when the power establishment happens to be on your side. No power minority regards its efforts to alter the frame of reference for a discussion as “petty.”
And there is no such thing as a news item that is apolitical. The only question is whether the politics of the story, as presented, comport with your own so completely that they become invisible to you. People tend not to complain about propaganda that they agree with. Most of them can’t even see it.
Wasc, nicely said.
I have never understood how people can become outraged by comments in an online forum. We are living in an infantile age.
Excellent blog site I learned a lot later in the article. Thanks for sharing
I didn’t see a mention of how Baltimore’s system got infected in the first place. I don’t remember reading about the attack vector in Brian’s earlier article. Did I miss it? What was the attack vector?
This twitter guy seems upset. There’s a good chance he’ll make a mistake because of that and he’ll get caught. Just wait.
After reading this, the paragraph that stands out the most to me is the last one about failure to apply updates in a timely manner.
Unfortunately, no one can patch an exploit that only the hackers have discovered. In this case, it was a “pretty vanilla ransomware binary” that would have been blocked by the use of an Execution Control technology using a default-deny paradigm.
The ransomware was only the payload. The article said something similar to “Eternal Blue” as the attack vector.
“Stewart said while it’s still possible that the Eternal Blue exploit was somehow used to propagate the Robbinhood ransomware, it’s not terribly likely.”
I didn’t see any mention that this was classified as a “zero-day” exploit, and just wondering if the initial attack should’ve been stopped by routine, up-to-date, security devices. Wondering if there was a lack of diligence here.
Usually these things start with phishing campaigns.
All it takes is one person to be off their game for them to get in with limited privileges.
Agreed, that is almost always the case, but that would only put it on an end-user station. How did it travel through the network to access the main infrastructure? What CVE did it expose?
Once again, another simple example of an attack that would have been thwarted by the use of an Execution Control technology.
Or just, like, having backups.
Blame first, get defensive when people ask questions later…sounds right.
If the hacker had access to documents, Then the hacker had remote code execution. Probably ran the ransomware after he pwned the system?
That doesn’t necessarily follow. It can be possible to exfiltrate data without being able to execute code.
Isn’t the cause/blame pretty easy? They are using Windows XP and Windows 2003. Neither should be in use. But the city government like many companies, don’t spend money to secure and maintain their network.
They should just force the previous mayor (Pugh) to pay the $100,000. She was the one that had all kinds of insider-like deals with the book supposedly she wrote (which someone else largely wrote).
Baltimore is a mess and unfortunately the citizens continually pay the price. And yes, race is a big problem.
I was thinking on the same line: What version of MS Windows are they (City of Baltimore) using?
Brian raises a good learning point – Always update with the latest patches (and/or upgrade accordingly.) This supports our call for good cyber hygiene.
While it certainly could be unpatched Windows machines, this is not being attributed to Eternal Blue nor to the recently reported RDP vulnerability.
So at this point, what’s known is an attacker installed software, and the software encrypted files, and wants a ransom for the key.
You can’t even necessarily blame the backup policy here.
Until you’ve got the point of entry identified, sealed off, and cans of paint in front of your windows (so to speak), the ninja can just come back the next night.
And so you want to identify how they came in, and when – for how long. You cannot trust any backup until you’ve done so, and the attacker can let you think you’ve won for a week, month, w/e – and then re-engage. Depends on how smart the attacker is.
Most attackers I get are just abusing Return-Path in email.
Yeah, no bias here.
Patching? as if
Is it not possible for the city of Baltimore to do wipe the system clean, do all the necessary security patches, educate all the staff of phishing emails, etc, and start over with back-up of the files?
Perhaps the cost exceeds the 100k, but then your not giving into criminals and have the opportunity to educate the City staff.
If they have good backups. Given their other failures, I would not count on it.
From what I understand, in the typical case, the ransomware will live in a system for several days or weeks before the villain gives the signal to encrypt everything.
As a result, the recent backups will likely be infected, thus they’re useless.
Victims may have months-old backups that predate the attack. Restoring from such backups is a huge expense, as a lot of labor will be involved in manually reentering data, forms, scanning paperwork, updating accounts, etc.
Often it’s cheaper to just pay a ransom, depending on the villain’s reputation and the labor costs.
Again, this is my understanding, and welcome correction.
This is some serious money: “GandCrab … earning more than $2 billion in ransom payments”
If any government entity or business thinks it’s OK to run outdated and unpatched systems with an internet connection, it should be no surprise if they find themselves contributing to the above earnings.
BCIT CIO signed on for a $250,000 a year, above what the mayor, police commissioner, and state attorney make. Then the mayor stated when swearing him in “I need somebody that’s a visionary who understands that the future is technology”
Oh he’s got the future covered. Two successful Ransomware attacks on his watch. Most CIO’s would be out on the first one.
Well see if there are any major changes or if they will continue to be a target.
Having 5 CIOs in 7 years might indicate a problem that is above the CIO level. If they fire the current CIO, will they lucky with number 6?
I don’t know anything about the CIO, or CISO if they have one, but it takes a loooooong time to get the budget moving in government. And cyber security is an overhead cost. Add to that the obscenely long time to hire and clear government vetted personnel and the dearth of cyber experts. This raises the costs of bringing in outside contractors to actually do the work. Firing the CIO just means bringing in another CIO who will face the same hurdles. Meanwhile you lose time and knowledge.
Couple of things: the Mayor stating he needs a visionary that understand the future of technology – yes, every organization wishes to have that.
Besides the $250k for the CIO salary; what has been the city’s IT budget for the past few years?
I totally agree that changing the CIO isn’t the best option. But having two ransomware attacks in a little over a year doesn’t bold well for ones leadership.
If this happened anywhere other than Governmental side, the CIO would be long gone by now.
The Mayor and the Controller didn’t want to talk a bit about why or how this happened. Which leads me to believe there was a failure to plan on their side.
I am super interested to see what they say was the reason for the ransomware to take hold of the city like this. They spent $1 million dollars to stand up a “known good” network and domain. That means they are going to have the infected infrastructure accessible for forensics sake.
Also I read somewhere that the city looked at some type of ransomware insurance. But didn’t pull the trigger because it wasn’t in the budget. I don’t want to be the Monday morning quarterback, but that line item may be worth it’s weight right now.
http://openbudget.baltimorecity.gov/#!/year/2018/operating/0/service/High+Performing+Government/0/department/M-R:+Office+of+Information+Technology/0/program/Enterprise+IT+Delivery+Services/0/description
Only $600,000 for Security, for a city that has a $2 Billion plus budget.
Then this was said on their webpage about their IT budget “BCIT compared the City of Baltimore’s IT budget against industry benchmarks for similar sized State & Local Government (SLG) entities. The results show that the City of Baltimore invests proportionally less on IT than most of its peers”
I question if the savings on IT budget really worth it?
Not receiving email notifications ?
Criminals have a lot bitcoins.
They Got it from Everywhere
Ransom funds are in crypto.
Offcourse You Can’t Buy food with your bitcoins…
Solution is:
Institutional investors like fidelity Will Invest a lot money into bitcoins.
Criminals Will earn 10x profit… And all the bitcoins becomes worthless.
Criminals Will sell their coins to big instututions.
Somebody Will Get very Rich soon.
Btc price Will hit 50k or over!
i wont deny the fact that this ransomware might look like something coming from Russia especially linking to “valery”. The tweet with grammatical errors like “people are not fool” can confirm the fact
city, county and other government organisations need to invest in cyber security. Hire more security analyst including CISO. Train Train Train, do patches regularly etc
Ms Krebs, love your site.
Please can I have a verdict: Was it a fish or eternal blue that hacked these guys?
Dang, more info please!!!!
Great site my friend.
Unless Baltimore had significant security instrumentation on their network (and there’s no indication of that), then there’s no way to say for sure whether EternalBlue was used.
— Jake Williams
“Finally, since we’re on the subject of major ransomware attacks and scary exploits, it’s a good time to remind readers about the importance of applying the latest security updates from Microsoft…” The experts at AskWoody would beg to differ:
https://www.askwoody.com/ms-defcon-system/
Am fafawally working at Marriott hotel city centre Doha
As a loss of prevention an safety and security
Ransomware can be harmless if you have an effective and secure backup system and methods in place. This shows how Baltimore city staff is incompetent and needs reshuffling.
It is unfortunate. many government agencies and critical sector organizations does not have robust pre-defined and solid position on dealing with ransomware.
Your post is awesome this will be definitely help us thanks
The first thing that should happen at any organization that is victimized by ransomware is that the CISO should be fired.
Why were these systems not properly backed up so that they could be restored without paying a ransom? This is basic, people.
The infection can lay dormant for weeks or months. Few places have a budget large enough to support complete backups going back that far.
It’s hardly fair to blame someone other than the criminals for practical limitations.
https://www.networkworld.com/article/2927212/new-sleeper-locker-ransomware-laid-dormant-on-infected-pcs-until-this-week-report-says.html
Thank you for the auspicious writeup. It in fact was a entertainment account it.
Look complicated to far brought agreeable from you!
However, how can we communicate?