As if the scourge of ransomware wasn’t bad enough already: Several prominent purveyors of ransomware have signaled they plan to start publishing data stolen from victims who refuse to pay up. To make matters worse, one ransomware gang has now created a public Web site identifying recent victim companies that have chosen to rebuild their operations instead of quietly acquiescing to their tormentors.

The message displayed at the top of the Maze Ransomware public shaming site.
Less than 48 hours ago, the cybercriminals behind the Maze Ransomware strain erected a Web site on the public Internet, and it currently lists the company names and corresponding Web sites for eight victims of their malware that have declined to pay a ransom demand.
“Represented here companies dont wish to cooperate with us, and trying to hide our successful attack on their resources,” the site explains in broken English. “Wait for their databases and private papers here. Follow the news!”
KrebsOnSecurity was able to verify that at least one of the companies listed on the site indeed recently suffered from a Maze ransomware infestation that has not yet been reported in the news media.
The information disclosed for each Maze victim includes the initial date of infection, several stolen Microsoft Office, text and PDF files, the total volume of files allegedly exfiltrated from victims (measured in Gigabytes), as well as the IP addresses and machine names of the servers infected by Maze.
As shocking as this new development may be to some, it’s not like the bad guys haven’t warned us this was coming.
“For years, ransomware developers and affiliates have been telling victims that they must pay the ransom or stolen data would be publicly released,” said Lawrence Abrams, founder of the computer security blog and victim assistance site BleepingComputer.com. “While it has been a well-known secret that ransomware actors snoop through victim’s data, and in many cases steal it before the data is encrypted, they never actually carried out their threats of releasing it.”
Abrams said that changed at the end of last month, when the crooks behind Maze Ransomware threatened Allied Universal that if they did not pay the ransom, they would release their files. When they did not receive a payment, they released 700MB worth of data on a hacking forum.
“Ransomware attacks are now data breaches,” Abrams said. “During ransomware attacks, some threat actors have told companies that they are familiar with internal company secrets after reading the company’s files. Even though this should be considered a data breach, many ransomware victims simply swept it under the rug in the hopes that nobody would ever find out. Now that ransomware operators are releasing victim’s data, this will need to change and companies will have to treat these attacks like data breaches.”
The move by Maze Ransomware comes just days after the cybercriminals responsible for managing the “Sodinokibi/rEvil” ransomware empire posted on a popular dark Web forum that they also plan to start using stolen files and data as public leverage to get victims to pay ransoms.
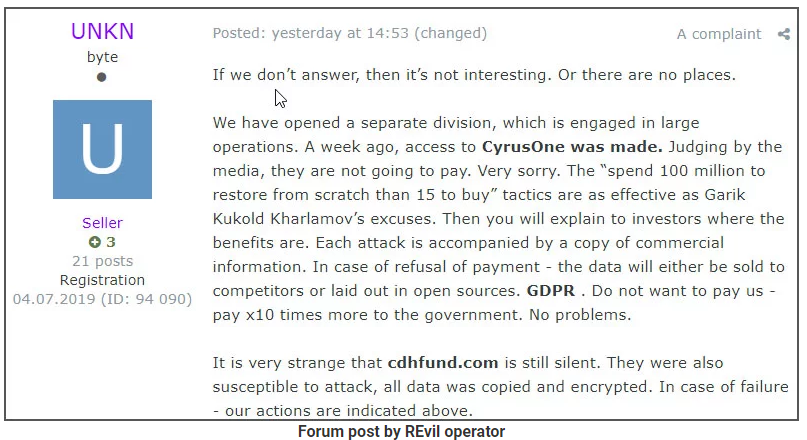
The leader of the Sodinokibi/rEvil ransomware gang promising to name and shame victims publicly in a recent cybercrime forum post. Image: BleepingComputer.
This is especially ghastly news for companies that may already face steep fines and other penalties for failing to report breaches and safeguard their customers’ data. For example, healthcare providers are required to report ransomware incidents to the U.S. Department of Health and Human Services, which often documents breaches involving lost or stolen healthcare data on its own site.
While these victims may be able to avoid reporting ransomware incidents if they can show forensic evidence demonstrating that patient data was never taken or accessed, sites like the one that Maze Ransomware has now erected could soon dramatically complicate these incidents.




It’s a Maffia like 90 was racketeering Now It’s trough i tech
Look like Bitcoin price will Go Up coz there will be demand for that and demand will be to pay ransome.
That has been the case for the entire life of bitcoin. A significant demand for cryptocurrency, bitcoin included, has always been criminal activity… to include ransom payers.
Joe, stop talking out of your posterior. “A significant demand for cryptocurrency, bitcoin included, has always been criminal activity”. This is patently false. It’s the equivalent of saying that the demand for US Treasury dollars has always been for narcotics.
Try not to lump a technology, just because you know absolutely nothing about it, into a category to attempt to scare everyone. I know nothing about rockets, but I’m not telling everyone that they’re being used to shuttle the rich people off to Mars.
Get a clue Philly Boy. Maybe Joe has read some articles on this situation while you haven’t taken the time to bolster your (false) claim by reasearching the subject yourself. We can ask Brian to look into Joe’s statement and can do some research ourselves.
https://blog.emsisoft.com/en/33977/is-ransomware-driving-up-the-price-of-bitcoin/
https://coinagereport.com/2019/10/21/ransomware-driving-up-bitcoin-prices/
https://www.blockchainbeach.com/how-ransomware-attacks-can-increase-the-price-of-bitcoin/
“By making companies want to buy Bitcoin, ransomware is actually driving up the value of the cryptocurrency. This fact leaves a lot of room for speculation”
https://thebitcoinnews.com/could-ransomware-be-driving-up-bitcoin-prices/
“We know a considerable number of companies hoard bitcoin in case they are hit with ransomware and need to pay a demand. It would seem to make sense that the bigger the demands come and the more high-profile cases there are, the more companies will start to buy. We suspect that that is what is driving the increase in prices, rather than the actual ransom demands themselves.”
https://www.nbcnews.com/storyline/hacking-of-america/companies-stockpiling-bitcoin-anticipation-ransomware-attacks-n761316
“A diverse group of British companies were asked whether they stockpiled digital currency in case of a ransomware attack. A third admitted that they did…”
I don’t think Joe is that far off the mark.
From Forbes in November of 2018:
“According to a study conducted earlier this year, approximately one-quarter of Bitcoin users and one-half of Bitcoin transactions are associated with illicit activity. Around $72 billion of unlawful activity per year involves Bitcoin, which is close to the scale of the U.S. and European markets for illegal drugs.”
https://www.forbes.com/sites/rachelwolfson/2018/11/26/tracing-illegal-activity-through-the-bitcoin-blockchain-to-combat-cryptocurrency-related-crimes/#7e179bd33a9a
As per the American Institue of Economic Research:
“…more than a third of all US currency in circulation is used by criminals and tax cheats.”
Link: https://www.aier.org/article/how-much-cash-is-used-by-criminals-and-tax-cheats/
I wasn’t even aware that ransomware actors even had any data from the computer systems they encrypted; I thought they just had the key.
It makes sense, though.
The German publisher heise was target of an malware attack. Seems like if they find a target that looks it is worth it they don’t just run the standard encryption but manually inspect the victim’s network including finding backups, ways to spread to other networks, installing persistent backdoors… …heise now besides the ordinary news (that today include a link to this article) sells hands-on knowledge they gained through that experience.
Using Ransomware as cover for a successful breach is a tactic I’ve been worried about. It looks like we now have evidence that is is actually happening. I’m now wondering if having Ransomware can be considered a “breach” as far as mandatory reporting laws as concerned. The most interesting thing to me is that many of these attacks are still using the same ETERNALBLUE vulnerability that was patched in 2017 and can also be remediated by completely disabling SMBv1. It’s astonishing that the vulnerability is still so widely spread.
Don’t be surprised SMBv1 is still around. Mission critical apps the company won’t spend money on to upgrade (despite being repeatedly warned, in writing) and only work on older OSs. Now add the ancient system (which doesn’t support more modern protocols) has to talk to more modern systems, now those need SMBv1 turned on.
Now add some more in that even when they migrate off said ancient app, they don’t want to spend the money to migrate historical data, but still want/need access to that data. So the old system has to be kept running even longer. […sigh…]
It seems to me that ransomware is simply a symptom of the breach. If they are in that deep, you should already be reporting it, in my opinion.
Screw them.
It’s a crime that targets mostly male victims, who must first overcome severe social barriers to obtain any sympathy at all in the role of victim, because men are typically perceived (by cops, lawyers, judges, potential jurors, etc.) as perpetrators rather than potential victims of crimes of a sexual nature.
In that regard it goes along with the usual panalopy of rape accusations, sexual harassment claims, civil restraining orders, protective orders, no-trespass orders, etc. which are commonly “served” on men who may be thus be marginalized as either registered or accused sex offenders or guilty of other violent or perceived violent crimes against women.
The element of demands for money in that context is commonly justified as being necessary to close a perceived gender pay gap at work, and if the monetary extortion is successful, the victim is further accused of paying “hush money” to women.
A female or feminist face is presented on the whole racket, and the role of the [usually] male crime bosses is carefully concealed.
The scheme is very effective, very profitable, and almost 100% foolproof, especially when family, friends, co-workers and associates are misinformed and “turned against” the targeted individual.
Wrong article… the sextortion article is just above this one.
Anyone convicted of using Malware for ransom should be put to death.
The natural progression of this battle will be for companies to place anti-malware malware on their sites to blow up the thief’s system should data transfer take place.
I’m male. I watch porn naturally. How’s that going to blackmail me?
Losers
From what I’ve gleaned, exfiltration appears to be happening prior to encryption. However, I wonder if uploading already-encrypted files might bypass some types of DLP that scan files for known patterns of sensitive data as well as IDS rules that look for this type of data in network flows.
getting around DLP isn’t that hard. once they are in they can easily setup an encrypted vpn..and exfiltrate everything they want to. Then let the encryption begin.
The natural progression of this battle will be for companies to place anti-malware malware on their sites to blow up the thief’s system should data transfer take place.