The criminal group behind the REvil ransomware enterprise has begun auctioning off sensitive data stolen from companies hit by its malicious software. The move marks an escalation in tactics aimed at coercing victims to pay up — and publicly shaming those who don’t. But it may also signal that ransomware purveyors are searching for new ways to profit from their crimes as victim businesses struggle just to keep the lights on during the unprecedented economic slowdown caused by the COVID-19 pandemic.
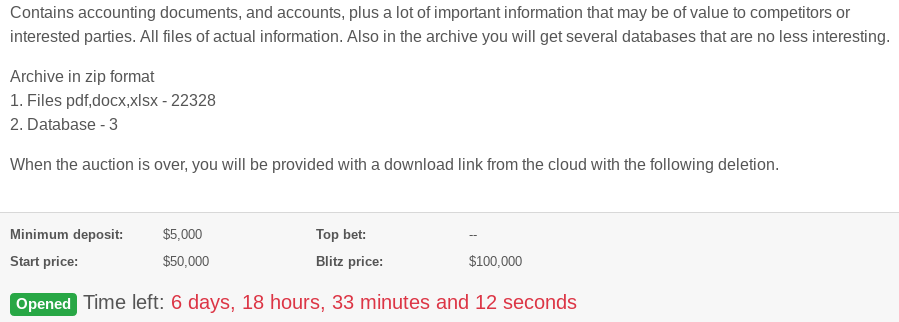
Over the past 24 hours, the crooks responsible for spreading the ransom malware “REvil” (a.k.a. “Sodin” and “Sodinokibi“) used their Dark Web “Happy Blog” to announce its first ever stolen data auction, allegedly selling files taken from a Canadian agricultural production company that REvil says has so far declined its extortion demands.
The victim firm’s auction page says a successful bidder will get three databases and more than 22,000 files stolen from the agricultural company. It sets the minimum deposit at $5,000 in virtual currency, with the starting price of $50,000.
Prior to this auction, REvil — like many other ransomware gangs — has sought to pressure victim companies into paying up mainly by publishing a handful of sensitive files stolen from their extortion targets, and threatening to release more data unless and until the ransom demand is met.
Experts say the auction is a sign that ransomware groups may be feeling the financial pinch from the current economic crisis, and are looking for new ways to extract value from victims who are now less likely or able to pay a ransom demand.
Lawrence Abrams, editor of the computer help and news Web site BleepingComputer, said while some ransomware groups have a history of selling victim data on cybercrime forums, this latest move by REvil may be just another tactic used by criminals to force victims to negotiate a ransom payment.
“The problem is a lot of victim companies just don’t have the money [to pay ransom demands] right now,” Abrams said. “Others have gotten the message about the need for good backups, and probably don’t need to pay. But maybe if the victim is seeing their data being actively bid on, they may be more inclined to pay the ransom.”
There is some evidence to suggest that the recent economic downturn wrought by COVID-19 has had a measurable impact on ransomware payouts. A report published in mid-April by cryptocurrency research firm Chainalysis found that ransomware payments “have decreased significantly since the COVID-19 crisis intensified in the U.S. and Europe in early March.”
Abrams said other ransomware groups have settled on different methods to increase victim payouts, noting that one prominent gang is now doubly extorting targets — demanding one payment amount in return for a digital key that can unlock files scrambled by the malware, and another payment in exchange for a promise to permanently delete data stolen from the victim.
The implied threat is that victims who pay to recover their files but don’t bite on the deletion payment can expect to see their private data traded, published or sold on the Dark Web.
“Some of these [extortion groups] have said if they don’t get paid they’re going to sell the victim’s data on the Dark Web, in order to recoup their costs,” Abrams said. “Others are now charging a few not only for the ransomware decryptor, but also a fee to delete the victim’s data. So it’s a double vig.”
The FBI and multiple security firms have advised victims not to pay any ransom demands, as doing so just encourages the attackers and in any case may not result in actually regaining access to encrypted files. In practice, however, many cybersecurity consulting firms are quietly urging their customers that paying up is the fastest route back to business-as-usual.
Here are a few tips that can help reduce the likelihood that you or your organization will fall victim to a ransomware attack:
-Patch, early and often: Many ransomware attacks leverage known security flaws in servers and desktops.
-Disable RDP: Short for Remote Desktop Protocol, this feature of Windows allows a system to be remotely administered over the Internet. A ridiculous number of businesses — particularly healthcare providers — get hit with ransomware because they leave RDP open to the Internet and secured with easy-to-guess passwords. And there are a number of criminal services that sell access to brute-forced RDP installations.
-Filter all email: Invest in security systems that can block executable files at the email gateway.
-Isolate mission-critical systems and data: This can be harder than it sounds. It may be worth hiring a competent security firm to make sure this is done right.
-Backup key files and databases: Bear in mind that ransomware can encrypt any network or cloud-based files or folders that are mapped and have been assigned a drive letter. Backing up to a secondary system that is not assigned a drive letter or is disconnected when it’s not backing up data is key. The old “3-2-1” backup rule comes into play here: Wherever possible, keep three backups of your data, on two different storage types, with at least one backup offsite.
-Disable macros in Microsoft Office: Block external content in Office files. Educate users that ransomware very often succeeds only when a user opens Office file attachment sent via email and manually enables Macros.
-Enable controlled folder access: Create rules to disallow the running of executable files in Windows from local user profile folders (App Data, Local App Data, ProgramData, Temp, etc.)
Sites like nomoreransom.org distribute free decryptor tools that can help some ransomware victims recover files without paying a ransom demand.




You forgot another very important tip. Don’t run Windows.
Or Mac OS, or Linux.
ALL of them are susceptible to ransomware.
There’s a valid reason to run windows. Roblox or other games (and you don’t want to Hackintosh or get a mac)
Yeah MattK, you really know your stuff.
You should consult for the Europeans and convince them not to run Windows on their supercomputers. How else would they get infected, right?
https://www.bbc.com/news/technology-52709660
…additional tip – train users not to open attachments they did not expect or that promise something “too good to be true”…
REvil’s favorite vector of compromise is CVE-2019-11510. Please patch your VPN servers.
the “create rules” link goes to a Microsoft 404 page
As a workaround, Wayback has it.
Remember to step upir users through new-school security awareness training as another control. “Your humans are the new endpoint.”
Agreed. I was going to suggest the same thing. Educate users, and test them.
Educating, testing and informing users is essential. Too often organizations treat their employees like cogs in a wheel. Employees know, by routine, not to do this, but then that happens, they need be more respected and invited in to the process in a reasonable way.
Here’s a REAL solution — REWARD those that CONVICT or PUNISH the bad guys.
— Post a GoFUNDme that posts/commits ALL malware demands as a REWARD, caught and proven DEAD or ALIVE to any proven source or accomplice. Seems that those employed by, or partners of those with this brand of morality,l eventually will not be able to resist the mounting rewards available to them, just by ratting out their “loyal partners”.
Which would create fun new spam claiming to be from guys who turned in their bosses and demanding rewards.
@Shiny Bright Ideas
Reading too many Western novels.
Among the problems with your idea:
1) If you aren’t law enforcement, you don’t have the capability to demand data from intermediary companies ranging from web site and server hosting to email.
2) Attribution of online attackers is really hard
3) Cross border issues even if LE
4) There is so much economic crime that most of these won’t even get written up – unless it is particularly big (i.e. over $10m) or has a serious national security (or political) angle.
5) The criminals make more than enough money to counter-fund. Ransomware alone is a multi-billion dollar plus annual business.
I do weekly deferential backups for 7 weeks and one main backup in the first week, in a two month cycle. I then do the cycle again for the next two months. So you have 6 main backups and 42 differentials in a one year period to cut down on storage size on a external hard drive .
I also do weekly registry backups . Furthermore, I do daily browser data backups in case it gets hijacked and or damaged
This is how you defeat ransomware, by having a regular backup routine.
Couldn’t agree with you more. Once you have a sound back-up and recovery strategy you end-up focusing on time-to-detection which seems to be the only real way to reduce impact and contain.
Well – ordinarily logic would dictate the victim company at least enter in the auction to buy back the data base; but of course, there is no guarantee it is the only copy, so scratch that.
Who really cares about private data anyway – every since the Equifax breach, the crooks have everything they want to know about everyone anyway. A constant stream of breaches just refreshes the information anyway. Other than the fact that it is medical data, there is no reason to play whack-a-mole with these turds!
I do like the suggesting of a Go Fund Me for a price on the head of a major bad actor in these major ransomware attacks; but it would take a very high end expert to validate who needs to be targeted – I’m sure the three letter agencies are not going to share data with bounty hunters.
Has anyone noticed that the story from two-to-three weeks ago involving REvil’s $42 million ransom has all but disappeared? Do a Google search and you’ll find that the most recent article is from two weeks ago. Even this article doesn’t specifically mention it. What happened to this story?
Ransomware encrypted it all; (just kidding) 😀
Try DuckDuckGo instead of Google.
Once an entity or enduser experiences their first ransomware incident they then understand, basic recovery strategies, how to mitigate known vulnerabilities and improve overall security awareness much like you mentioned. In the last 24 months more and more of my clients that have either dealt with ransomware or have advanced their recovery capabilities are now pivoting into maturing detection capabilities by way of understanding block change within their back-up. Some are using off the shelf products, others are writing custom ML workflows to quickly identify a change state in data block. With variants changing daily end users are opting focus on time-to-detection once they have a sound recovery strategy in place.
If at this stage in the game your organization still hasn’t implemented 6 out of those 7 steps (isolation is the hardest) you might want to consider another organization, as it is just a matter of time before they become the next bunny…