Cyber cops in Ukraine carried out an arrest and several raids last week in connection with the author of a U-Admin, a software package used to administer what’s being called “one of the world’s largest phishing services.” The operation was carried out in coordination with the FBI and authorities in Australia, which was particularly hard hit by phishing scams perpetrated by U-Admin customers.
The Ukrainian attorney general’s office said it worked with the nation’s police force to identify a 39-year-old man from the Ternopil region who developed a phishing package and special administrative panel for the product.
“According to the analysis of foreign law enforcement agencies, more than 50% of all phishing attacks in 2019 in Australia were carried out thanks to the development of the Ternopil hacker,” the attorney general’s office said, noting that investigators had identified hundreds of U-Admin customers.
Brad Marden, superintendent of cybercrime operations for the Australian Federal Police (AFP), said their investigation into who was behind U-Admin began in late 2018, after Australian citizens began getting deluged with phishing attacks via mobile text messages that leveraged the software.
“It was rampant,” Marden said, noting that the AFP identified the suspect and referred the case to the Ukrainians for prosecution. “At one stage in 2019 we had a couple of hundred SMS phishing campaigns tied to just this particular actor. Pretty much every Australian received a half dozen of these phishing attempts.”
U-Admin, a.k.a. “Universal Admin,” is crimeware platform that first surfaced in 2016. U-Admin was sold by an individual who used the hacker handle “Kaktys” on multiple cybercrime forums.
According to this comprehensive breakdown of the phishing toolkit, the U-Admin control panel isn’t sold on its own, but rather it is included when customers contact the developer and purchase a set of phishing pages designed to mimic a specific brand — such as a bank website or social media platform.
Cybersecurity threat intelligence firm Intel 471 describes U-Admin as an information stealing framework that uses several plug-ins in one location to help users pilfer victim credentials more efficiently. Those plug-ins include a phishing page generator, a victim tracker, and even a component to help manage money mules (for automatic transfers from victim accounts to people who were hired in advance to receive and launder stolen funds).
Perhaps the biggest selling point for U-Admin is a module that helps phishers intercept multi-factor authentication codes. This core functionality is what’s known as a “web inject,” because it allows phishers to inject content into the phishing page that prompts the victim to enter additional information. The video below, produced by the U-Admin developer, shows a few examples (click to enlarge).
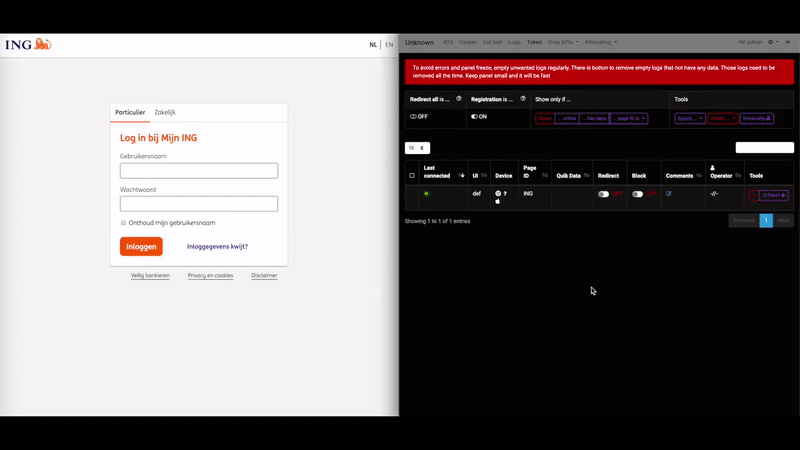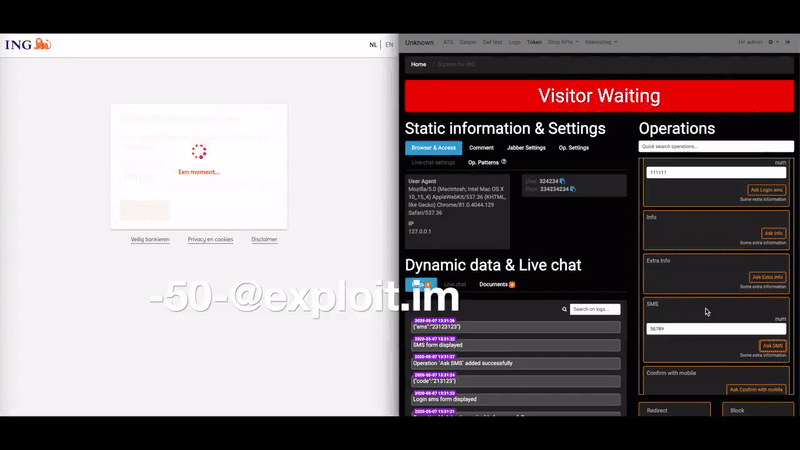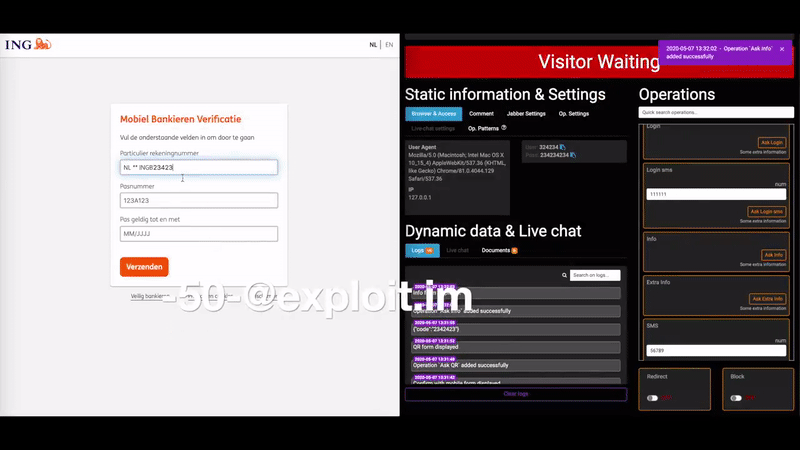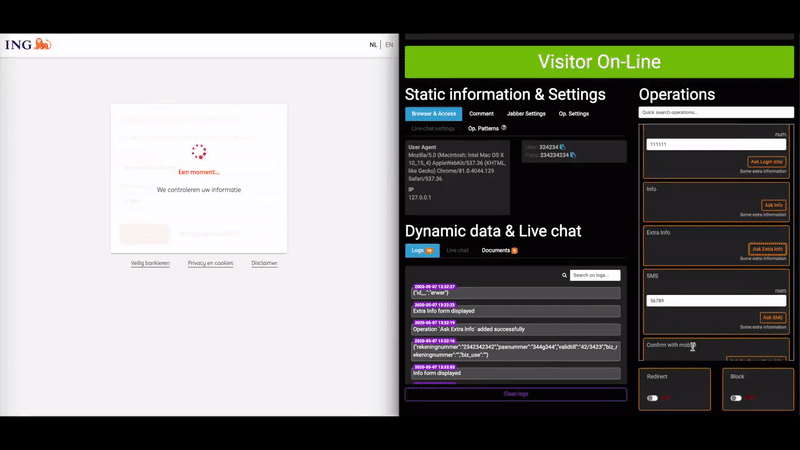
A demonstration video showing the real-time web injection capabilities of the U-Admin phishing kit. Credit: blog.bushidotoken.net
There are multiple recent reports that U-Admin has been used in conjunction with malware — particularly Qakbot (a.k.a. Qbot) — to harvest one-time codes needed for multi-factor authentication.
“Paired with [U-Admin’s 2FA harvesting functionality], a threat actor can remotely connect to the Qakbot-infected device, enter the stolen credentials plus the 2FA token, and begin initiating transactions,” explains this Nov. 2020 blog post on an ongoing Qakbot campaign that was first documented three months earlier by Check Point Research.
In the days following the Ukrainian law enforcement action, several U-Admin customers on the forums where Kaktys was most active began discussing whether the product was still safe to use following the administrator’s arrest.
The AFP’s Marden hinted that the suspicions raised by U-Admin’s customer base might be warranted.
“I wouldn’t be unhappy with the crooks continuing to use that piece of kit, without saying anything more on that front,” Marden said.
While Kaktys’s customers may be primarily concerned about the risks of using a product supported by a guy who just got busted, perhaps they should be more worried about other crooks [or perhaps the victim banks themselves] moving in on their turf: It appears the U-Admin package being sold in the underground has long included a weakness that could allow anyone to view or alter data that was phished with the help of this kit.
The security flaw was briefly alluded to in a 2018 writeup on U-Admin by the SANS Internet Storm Center.
“Looking at the professionality of the code, the layout and the functionality I’m giving this control panel 3 out of 5 stars,” joked SANS guest author Remco Verhoef. “We wanted to give them 4 stars, but we gave one star less because of an SQL injection vulnerability” [link added].
That vulnerability was documented in more detail at exploit archive Packet Storm Security in March 2020 and indexed by Check Point Software in May 2020, suggesting it still persists in current versions of the product.
The best advice to sidestep phishing scams is to avoid clicking on links that arrive unbidden in emails, text messages and other mediums. This advice is the same whether you’re using a mobile or desktop device. In fact, this phishing framework specialized in lures specifically designed to be loaded on mobile devices.
Most phishing scams invoke a temporal element that warns of dire consequences should you fail to respond or act quickly. If you’re unsure whether the message is legitimate, take a deep breath and visit the site or service in question manually — ideally, using a browser bookmark so as to avoid potential typosquatting sites.
Further reading:
uAdmin Show & Tell
Gathering Intelligence on the Qakbot banking Trojan




We need more information on the raids and ultimately all the arrests.
Worried?
Nope
Front guys just to be used by Higher level.
The real organisators you never catch.
Not true.
Higher level guys just take a bit longer. That is why the lower level guys get prosecuted to the fullest extent… so they can plea bargain for lower sentences, by rolling over on the higher level.
Eventually, the bosses do go down. Retirement is a very rare occurrence. Most often, they get arrested but it doesn’t make the news.
Actually the jokers stash closes tomorow February 15,2021 their bowing out after making over a billion since 2014. Just Google it and there’s plenty stories. That’s actually how I got here lol
Jokers stash = card/data market
There is a story about it here: https://krebsonsecurity.com/2021/01/jokers-stash-carding-market-to-call-it-quits/
Yes, rule one, if it smells like phish and swims like a phish – it’s time to manually pay a browser visit to your service – and see it there are actually messages for you and of, course assess if the site works
…you’ve already won, call now, have your credit ready, operators are standing by…
…or at least the equivalent in email…
…wow, people are still gullible…
Nice write up, Brian.
When scammers like this are found AND found guilty, they should be placed in solitary confinement WITHOUT access to any internet device for at 5 years!
Those scammers im sure somewhere spain relaxing on yacts or monte carlo or st tropez.
They got lawyers never go in jail in ukraine money talks only
Extradition is no joke. Even in corrupt countries… it won’t matter. International criminals won’t escape justice since they can and will be extradited to either the US or Australia.
Over the years we’ve seen notices about “major” spam/phishing networks being taken out but almost no corresponding significant reduction in spam/phishing.
Why?
Because the 2nd ranking product then becomes the top ranking product, after a brief interlude…
Thanks Brian
As yet no Australian news source has published this information
I’m a bit late to this post.
To quote security vet above
“wow, people are still gullible”
How come this stuff still works? I do some verification on Phishtank and am amazed. It never stops: all day every day. Sometimes I take a break for a few days.
Don’t have any reliable stats but are people still putting their hands in a fire to check if it still burns? Am I the only one who thinks that maybe these victims asked for it and maybe deserved a burned hand?