On Aug. 13, 2020, someone uploaded a suspected malicious file to VirusTotal, a service that scans submitted files against more than five dozen antivirus and security products. Last month, Microsoft and FireEye identified that file as a newly-discovered fourth malware backdoor used in the sprawling SolarWinds supply chain hack. An analysis of the malicious file and other submissions by the same VirusTotal user suggest the account that initially flagged the backdoor as suspicious belongs to IT personnel at the National Telecommunications and Information Administration (NTIA), a division of the U.S. Commerce Department that handles telecommunications and Internet policy.

Both Microsoft and FireEye published blog posts on Mar. 4 concerning a new backdoor found on high-value targets that were compromised by the SolarWinds attackers. FireEye refers to the backdoor as “Sunshuttle,” whereas Microsoft calls it “GoldMax.” FireEye says the Sunshuttle backdoor was named “Lexicon.exe,” and had the unique file signatures or “hashes” of “9466c865f7498a35e4e1a8f48ef1dffd” (MD5) and b9a2c986b6ad1eb4cfb0303baede906936fe96396f3cf490b0984a4798d741d8 (SHA-1).
“In August 2020, a U.S.-based entity uploaded a new backdoor that we have named SUNSHUTTLE to a public malware repository,” FireEye wrote.
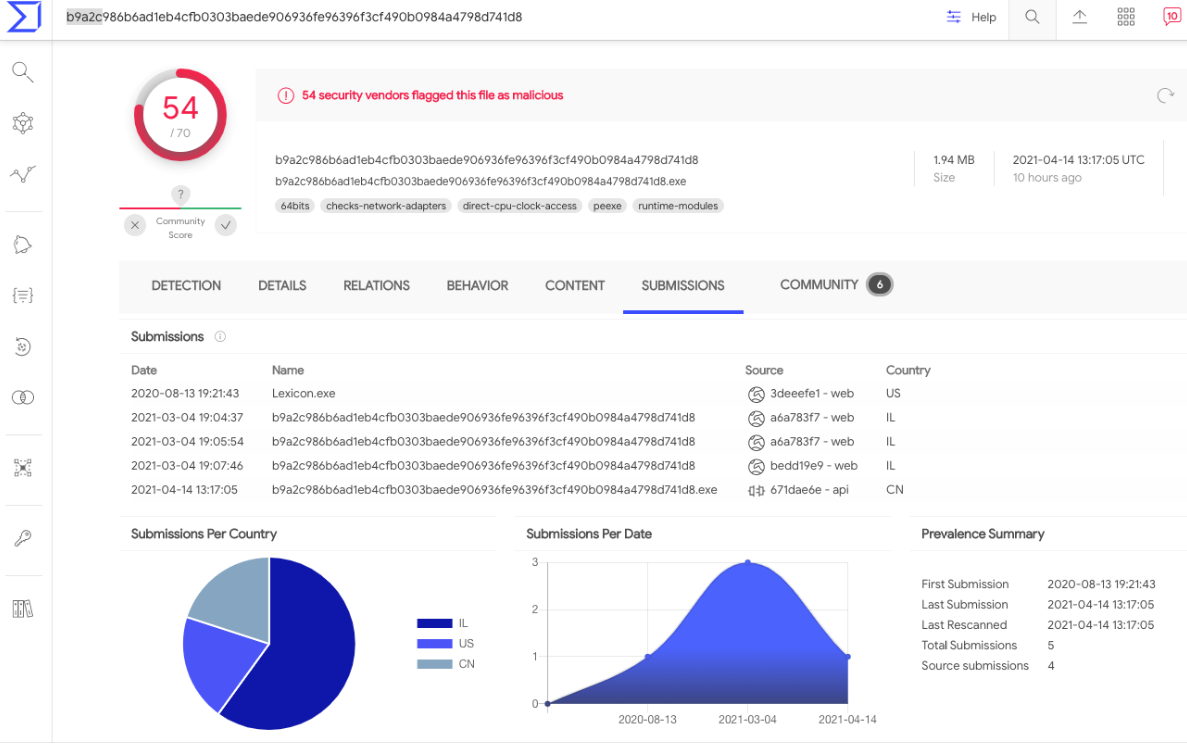
The “Sunshuttle” or “GoldMax” backdoor, as identified by FireEye and Microsoft, respectively. Image: VirusTotal.com.
A search in VirusTotal’s malware repository shows that on Aug. 13, 2020 someone uploaded a file with that same name and file hashes. It’s often not hard to look through VirusTotal and find files submitted by specific users over time, and several of those submitted by the same user over nearly two years include messages and files sent to email addresses for people currently working in NTIA’s information technology department.
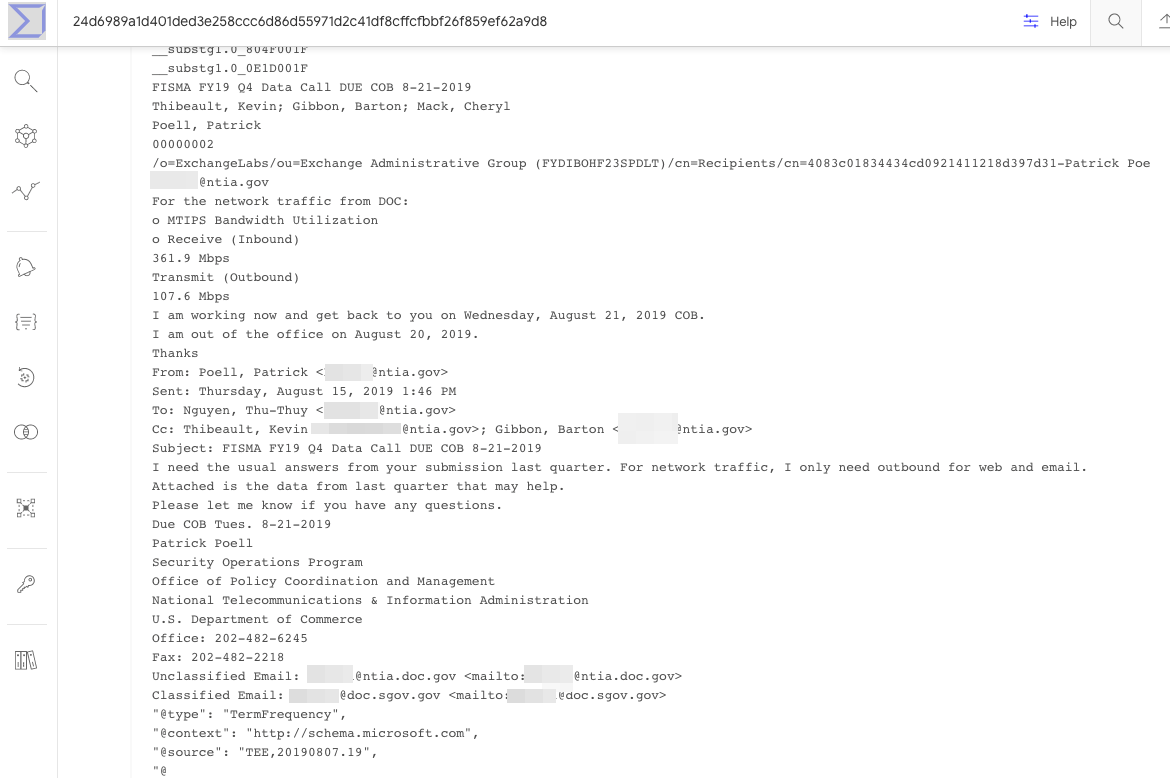
An apparently internal email that got uploaded to VirusTotal in Feb. 2020 by the same account that uploaded the Sunshuttle backdoor malware to VirusTotal in August 2020.
The NTIA did not respond to requests for comment. But in December 2020, The Wall Street Journal reported the NTIA was among multiple federal agencies that had email and files plundered by the SolarWinds attackers. “The hackers broke into about three dozen email accounts since June at the NTIA, including accounts belonging to the agency’s senior leadership, according to a U.S. official familiar with the matter,” The Journal wrote.
It’s unclear what, if anything, NTIA’s IT staff did in response to scanning the backdoor file back in Aug. 2020. But the world would not find out about the SolarWinds debacle until early December 2020, when FireEye first disclosed the extent of its own compromise from the SolarWinds malware and published details about the tools and techniques used by the perpetrators.
The SolarWinds attack involved malicious code being surreptitiously inserted into updates shipped by SolarWinds for some 18,000 users of its Orion network management software. Beginning in March 2020, the attackers then used the access afforded by the compromised SolarWinds software to push additional backdoors and tools to targets when they wanted deeper access to email and network communications.
U.S. intelligence agencies have attributed the SolarWinds hack to an arm of the Russian state intelligence known as the SVR, which also was determined to have been involved in the hacking of the Democratic National Committee six years ago. On Thursday, the White House issued long-expected sanctions against Russia in response to the SolarWinds attack and other malicious cyber activity, leveling economic sanctions against 32 entities and individuals for disinformation efforts and for carrying out the Russian government’s interference in the 2020 presidential election.
The U.S. Treasury Department (which also was hit with second-stage malware that let the SolarWinds attackers read Treasury email communications) has posted a full list of those targeted, including six Russian companies for providing support to the cyber activities of the Russian intelligence service.
Also on Thursday, the FBI, National Security Agency (NSA), and the Cybersecurity Infrastructure Security Administration (CISA) issued a joint advisory on several vulnerabilities in widely-used software products that the same Russian intelligence units have been attacking to further their exploits in the SolarWinds hack. Among those is CVE-2020-4006, a security hole in VMWare Workspace One Access that VMware patched in December 2020 after hearing about it from the NSA.
On December 18, VMWare saw its stock price dip 5.5 percent after KrebsOnSecurity published a report linking the flaw to NSA reports about the Russian cyberspies behind the SolarWinds attack. At the time, VMWare was saying it had received “no notification or indication that CVE-2020-4006 was used in conjunction with the SolarWinds supply chain compromise.” As a result, a number of readers responded that making this connection was tenuous, circumstantial and speculative.
But the joint advisory makes clear the VMWare flaw was in fact used by SolarWinds attackers to further their exploits.
“Recent Russian SVR activities include compromising SolarWinds Orion software updates, targeting COVID-19 research facilities through deploying WellMess malware, and leveraging a VMware vulnerability that was a zero-day at the time for follow-on Security Assertion Markup Language (SAML) authentication abuse,” the NSA’s advisory (PDF) reads. “SVR cyber actors also used authentication abuse tactics following SolarWinds-based breaches.”
Officials within the Biden administration have told media outlets that a portion of the United States’ response to the SolarWinds hack would not be discussed publicly. But some security experts are concerned that Russian intelligence officials may still have access to networks that ran the backdoored SolarWinds software, and that the Russians could use that access to affect a destructive or disruptive network response of their own, The New York Times reports.
“Inside American intelligence agencies, there have been warnings that the SolarWinds attack — which enabled the SVR to place ‘back doors’ in the computer networks — could give Russia a pathway for malicious activity against government agencies and corporations,” The Times observed.




It mentioned that the NTIA emails were hacked in June. Perhaps the attackers obtained VirusTotal credentials as well and uploaded it via those hacked credentials. That way, it cannot be traced to them
Why would they upload their own virus to VirusTotal to be scanned?
The Six Dumbest Ideas in Computer Security
#2) Enumerating Badness
http://www.ranum.com/security/computer_security/editorials/dumb/
Wow brother, that is a good read! They should teach this as IT 101…
IT 101 would be better served if they taught Kerckhoff’s Principle
https://en.wikipedia.org/wiki/Kerckhoffs%27s_principle
1) Kerckhoff’s Principle is what the Federal Government uses regardless of who is “running the Census”. The key idea to “differential privacy” is that hacks of information from separate sources can not be normalized.
2) Uncle Sam knows well how to hack. For The Battle of Midway in WWII he was the hacker. Fun Fact: All Zip Codes west of Hawaii are identical so had Uncle Sam bought hacked address lists from Facebook, LinkedIn, etc. they could never have “discovered” the Japanese Code for Midway Island. “AH” as I recall.
This was 15 years ago, and Hacking is not gone and no longer dumb. LOL
To see if it can be picked up by the scanners. It’s often done
Most experienced malware writers or those who buy their code will know to test against services similar to Virustotal that check against the various AV’s but do not report anything back or save any details.
These services are made specifically to keep your newly crypted nasty away from those who will examine it and flag it.
They would naturally try to maximize the leverage they gained by the exploit to target detection abilities for ongoing and future attacks. So it doesn’t follow a detection by VT would be a good thing for them from that perspective.
The upload was indeed legit. It just wasn’t enough to trigger an early response of the kind needed to stop the infil unfortunately.
I make more then $12,000 a month online. It’s enough to comfortably replace my old jobs income, especially considering I only work about 11 to 12 hours a week from home. I was amazed how easy it was after I tried it…GOOD LUCK..===))> http://Www.Workapp2.Com
Not following you here…. why would they do that?
A long time ago, around 1970, I read a book called “Up The Organization”
The only part I still remember is “You will rise to your level of incompetence.”
Sounds like that happens at most of these departments of government
Love that book.
My favorite quote is about the strategy of data over-collection.
(Exxon was the largest Corporation in the world at the time)
The comment was: “Exxon didn’t get to be Exxon doing things the way Exxon does them now.”
…”rise to your level of incompetence” has been known since the 1969 book The Peter Principal by Peter Drucker…
…the vast majority of supervisors / managers exhibit that…
Up the Organization is a good book, and it does mention that as a ‘viable theory” (if I recall correctly—my copy got so well used it fell apart and I tossed it), but the originator of the theory was Dr. Peter, a B-school prof. and published in his books and writing. https://en.wikipedia.org/wiki/Peter_principle
…possibly older and grumpier, that’s me…
Indeed, one can trace this concept’s thread back [at least] to Shepherd Mead’s 1952 book, “How to Succeed in Business Without Really Trying: The Dastard’s Guide to Fame and Fortune” — which was was the basis for the highly successful 1961 Broadway musical “How to Succeed in Business Without Really Trying” (with music by Frank Loesser and book by Abe Burrows, Jack Weinstock, and Willie Gilbert), followed by a 1967 film. The original stage production won seven Tony Awards, the New York Drama Critics’ Circle award, and the 1962 Pulitzer Prize for Drama. (Today, one either becomes president or goes to prison — which are not necessarily mutually exclusive…)
Kudos — again — Brian!
The same goes for private industry too.
Based on my years in corporate management, I developed my own corollary to the Peter Principle: “You rise to one level above your level of incompetence, and then you stay THERE.”
Great analysis and writing as usual Brian.
The joint advisory is also a clear-cut vindication of your reporter’s instincts as to the potential link between the VMWare flaw and the NSA report about Russia/SolarWinds. The readers who called your writing “tenuous”, “circumstantial” or “speculative” back in December were way off the mark. Seems they didn’t bother to consider the depth of research and careful consideration that you apply to your writing, before they posted their opinions. Personally, I appreciate your no-nonsense reports.
Looking forward to your virtual event on April 22nd.
Regards
Fabian
I am confused by your second sentence in the first paragraph above; that begins with “An analysis…”
Does it mean to say someone at the NTIA uploaded malware?
VirusTotal is a place where you can upload suspect files and see whether they have been identified as malware by well-known security vendors. So, yes, it appears someone at NITA found the backdoor, found it suspicious, and uploaded it to VirusTotal to see if it was a known malicious file.
The NITA employee did the right thing. You’re supposed to upload malware to VirusTotal. They didn’t upload the malware any place that would have furthered any infections.
This is a good reminder that whatever you submit to virus total will not be private.
The way I use virus total is I feed it links in spam. If there is a suspicious attachment, I just delete the email. I don’t even chance doing the download.
Often the link isn’t deemed malware. However it is possible the file isn’t known to be malware yet. If it is detected as malware, only two or three out of the hundred of service will deem it malware in my experience.
My point here, after that long wind up, is submitting something to virus total doesn’t mean you had a clue it was malware at all.
Yes, whatever you submit can be shared but VirusTotal is upfront about its policy. This is what it states on the link where you upload the file you want scanned by the service: “By submitting data below, you are agreeing to our Terms of Service and Privacy Policy, and to the sharing of your Sample submission with the security community. Please do not submit any personal information; VirusTotal is not responsible for the contents of your submission. Learn more.”
I use VirusTotal often, not only for scanning files attached to emails but also URL links. It’s not infallible (both false positives and negatives) but it’s a good tool for checking.
And apps, of course, even from trusted sites.
URLs and Files are treated differently by VirusTotal.
Submitting to VT can be very useful for both.
For files, it runs the sample in a sandbox that has multiple AV vendors running inside. Although there are lots of ways to evade sandbox detection. And these AV engines also run signature based detection for known malware.
0day files might not get a hit on VT, but after a few days, it often will start getting hits.
Links are generally reputation based. I think VT will also visit the URL, and see what resources (libraries, javascript, etc) are loaded, and run those hashes too.
All in all… VirusTotal is a great resource for security depts that can’t run their own sandbox, with multiple AntiVirus solutions. It isn’t perfect, and it won’t detect the latest and greatest of malware. But when a sample becomes known, it is pretty good.
You just like to input your own output.
Thanks, I actually read both books. Mainly just remember the phrase.
I had a concrete construction co. in S. Cal. & several of my employees reached that level. I gave them a choice go back to being what they were before the promotion or get laid off. Most chose to go back.
Nice to be vindicated, eh Brian? 🙂
I was inclined to believe it was there might be a connection, but mostly because that agreed with my political priors.
I’m not sure I see this as a demonstration of incompetence by anyone in government. Someone found a dubious file, likely got rid of it from their own systems, and shipped it off to VirusTotal. As Gary said, finding a dubious file doesn’t necessarily indicate malware. This stuff was pretty well obfuscated. It’s hardly evidence of incompetence that they didn’t look at this file and come to the realization it was part of was a high level compromise of the US government. I doubt I…or anyone else here. would have done any better.
“could use that access to AFFECT a destructive or disruptive network response”
Shouldn’t that be “effect” ?
No.
Lexicon.exe was the name of the most popular text editor in Russia in the 90s. Very nice nod.
It looks like the same MD5 and SHA1 hashes were found on binaries run/tested on some public 32-bit Win 7 VM’s on app [dot] any [dot] run on March 4 and March 5.
They didn’t execute but have the same hashes. For anyone interested:
https://app.any.run/tasks/bf7ff03c-5357-4845-a0bd-56f87207af99/
March 4/5 2021.
Maybe even earlier than August:
https://www.npr.org/2021/04/16/985439655/a-worst-nightmare-cyberattack-the-untold-story-of-the-solarwinds-hack?utm_campaign=storyshare&utm_source=facebook.com&utm_medium=social&fbclid=IwAR08w-FnVGx2chlpTDANjZXpZLVplRZ2n1G2OGfF2kKQUVbLvKoQaOcCMDs
…just to set the record straight, or at least illuminate history…
…virus total is just a later instantiation of the room at NCSA/ICSA labs where all the a/v vendors of the day looked at the daily hauls from the news groups that we affectionately called “porn hauler” circa mid 90’s…
…ok, time for my nap…
Maybe I missed it but when this was first loaded (8/13/2000) what were the results?
I’m assuming (yeah, sorry) that if it was a “new” technique various virus scanners may not have reported anything negative and the end user assumed it was ok?
Not all virus tools are signature based but depending on how this malware worked, it may have evaded many/most of the scanners?
Gotta love the continued spread of the BlueAnon Russian Disinfo theories here. Lol