The Federal Bureau of Investigation (FBI) confirmed today that its fbi.gov domain name and Internet address were used to blast out thousands of fake emails about a cybercrime investigation. According to an interview with the person who claimed responsibility for the hoax, the spam messages were sent by abusing insecure code in an FBI online portal designed to share information with state and local law enforcement authorities.
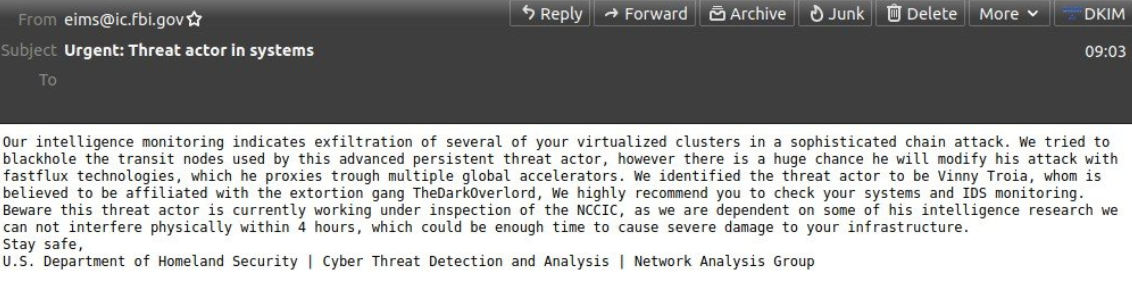
The phony message sent late Thursday evening via the FBI’s email system. Image: Spamhaus.org
Late in the evening on Nov. 12 ET, tens of thousands of emails began flooding out from the FBI address eims@ic.fbi.gov, warning about fake cyberattacks. Around that time, KrebsOnSecurity received a message from the same email address.
“Hi its pompompurin,” read the missive. “Check headers of this email it’s actually coming from FBI server. I am contacting you today because we located a botnet being hosted on your forehead, please take immediate action thanks.”
A review of the email’s message headers indicated it had indeed been sent by the FBI, and from the agency’s own Internet address. The domain in the “from:” portion of the email I received — eims@ic.fbi.gov — corresponds to the FBI’s Criminal Justice Information Services division (CJIS).
According to the Department of Justice, “CJIS manages and operates several national crime information systems used by the public safety community for both criminal and civil purposes. CJIS systems are available to the criminal justice community, including law enforcement, jails, prosecutors, courts, as well as probation and pretrial services.”
In response to a request for comment, the FBI confirmed the unauthorized messages, but declined to offer further information.
“The FBI and CISA [the Cybersecurity and Infrastructure Security Agency] are aware of the incident this morning involving fake emails from an @ic.fbi.gov email account,” reads the FBI statement. “This is an ongoing situation and we are not able to provide any additional information at this time. The impacted hardware was taken offline quickly upon discovery of the issue. We continue to encourage the public to be cautious of unknown senders and urge you to report suspicious activity to www.ic3.gov or www.cisa.gov.”
In an interview with KrebsOnSecurity, Pompompurin said the hack was done to point out a glaring vulnerability in the FBI’s system.
“I could’ve 1000% used this to send more legit looking emails, trick companies into handing over data etc.,” Pompompurin said. “And this would’ve never been found by anyone who would responsibly disclose, due to the notice the feds have on their website.”
Pompompurin says the illicit access to the FBI’s email system began with an exploration of its Law Enforcement Enterprise Portal (LEEP), which the bureau describes as “a gateway providing law enforcement agencies, intelligence groups, and criminal justice entities access to beneficial resources.”
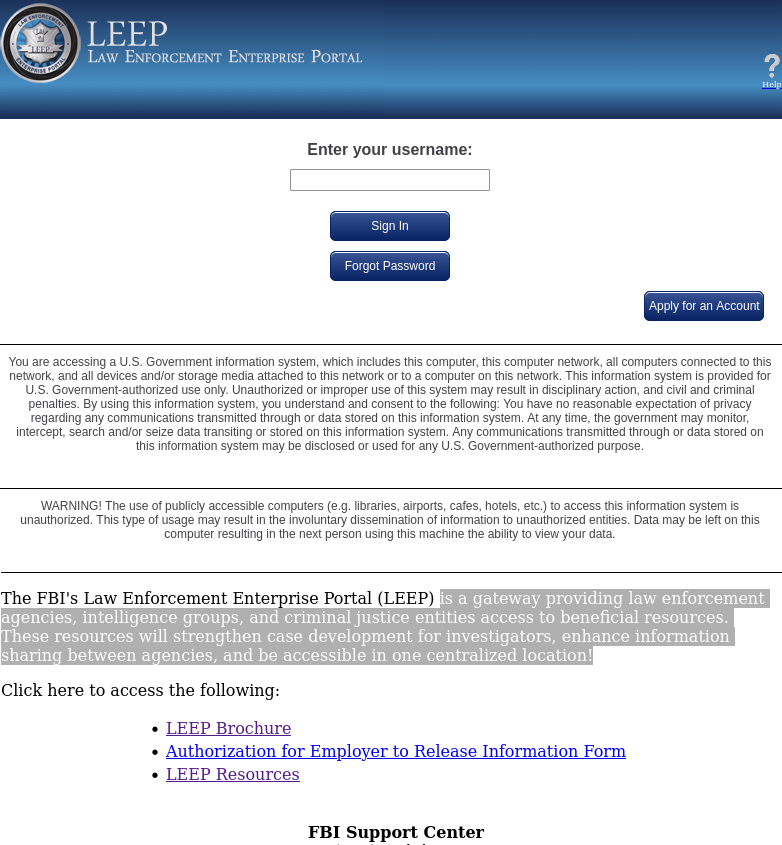
The FBI’s Law Enforcement Enterprise Portal (LEEP).
“These resources will strengthen case development for investigators, enhance information sharing between agencies, and be accessible in one centralized location!,” the FBI’s site enthuses.
Until sometime this morning, the LEEP portal allowed anyone to apply for an account. Helpfully, step-by-step instructions for registering a new account on the LEEP portal also are available from the DOJ’s website. [It should be noted that “Step 1” in those instructions is to visit the site in Microsoft’s Internet Explorer, an outdated web browser that even Microsoft no longer encourages people to use for security reasons.]
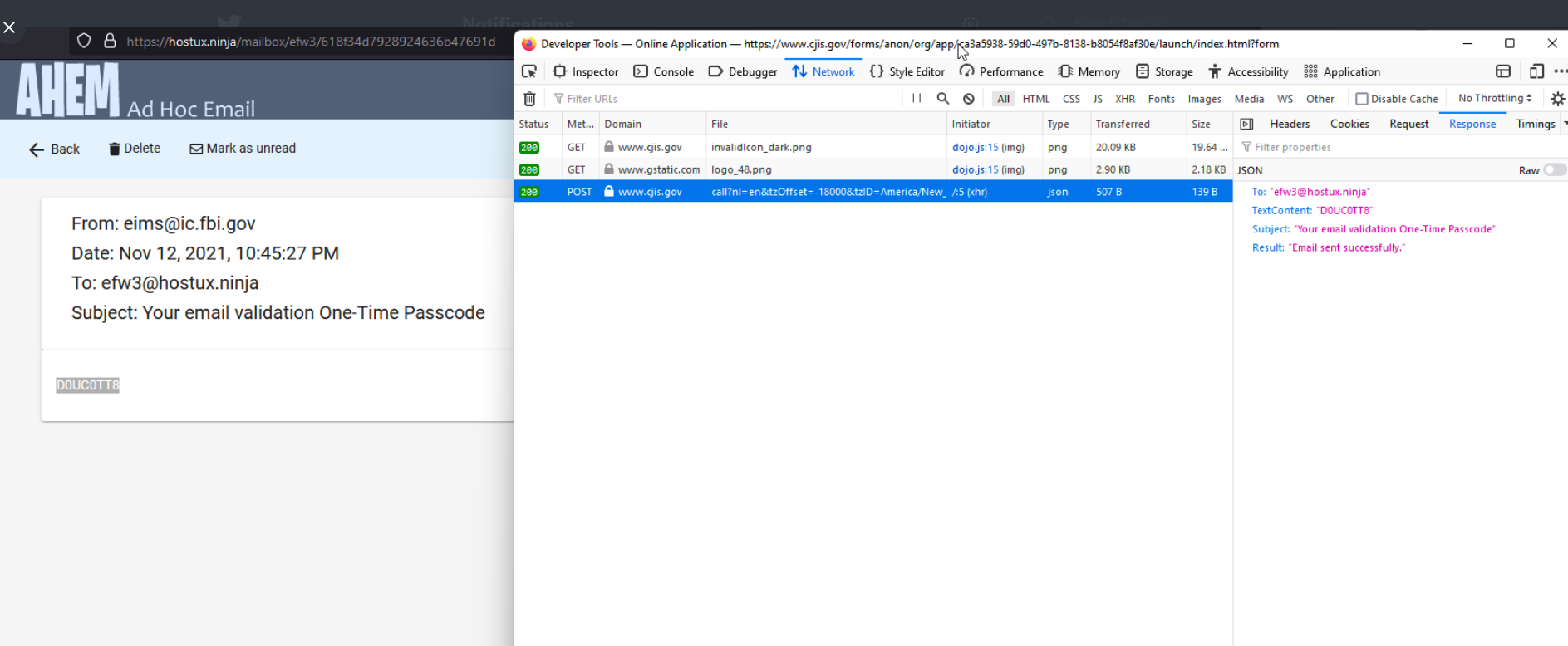
Much of that process involves filling out forms with the applicant’s personal and contact information, and that of their organization. A critical step in that process says applicants will receive an email confirmation from eims@ic.fbi.gov with a one-time passcode — ostensibly to validate that the applicant can receive email at the domain in question.
But according to Pompompurin, the FBI’s own website leaked that one-time passcode in the HTML code of the web page.
Pompompurin said they were able to send themselves an email from eims@ic.fbi.gov by editing the request sent to their browser and changing the text in the message’s “Subject” field and “Text Content” fields.
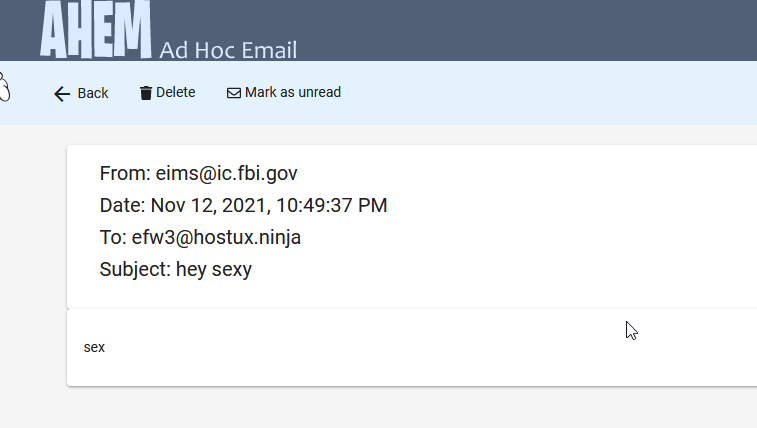
A test email using the FBI’s communications system that Pompompurin said they sent to a disposable address.
“Basically, when you requested the confirmation code [it] was generated client-side, then sent to you via a POST Request,” Pompompurin said. “This post request includes the parameters for the email subject and body content.”
Pompompurin said a simple script replaced those parameters with his own message subject and body, and automated the sending of the hoax message to thousands of email addresses.
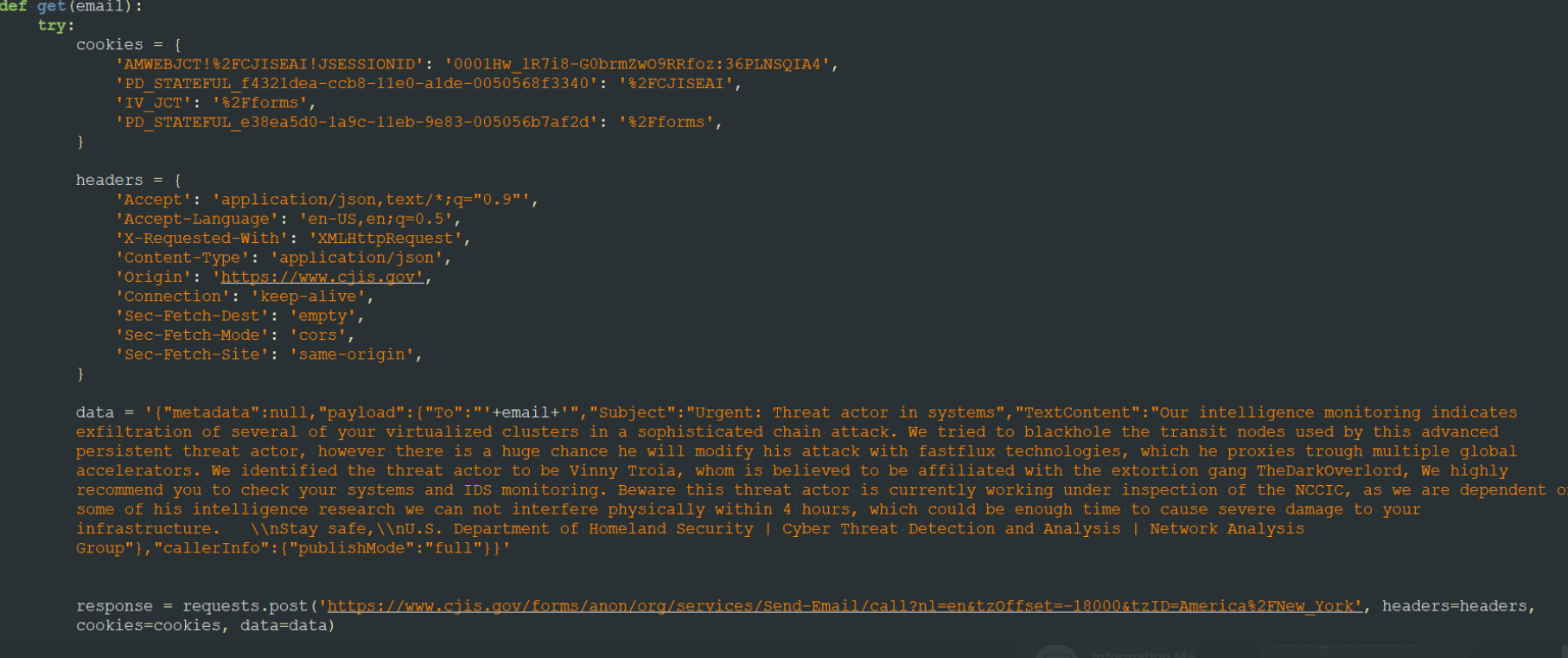
A screenshot shared by Pompompurin, who says it shows how he was able to abuse the FBI’s email system to send a hoax message.
“Needless to say, this is a horrible thing to be seeing on any website,” Pompompurin said. “I’ve seen it a few times before, but never on a government website, let alone one managed by the FBI.”
As we can see from the first screenshot at the top of this story, Pompompurin’s hoax message is an attempt to smear the name of Vinny Troia, the founder of the dark web intelligence companies NightLion and Shadowbyte.
“Members of the RaidForums hacking community have a long standing feud with Troia, and commonly deface websites and perform minor hacks where they blame it on the security researcher,” Ionut Illascu wrote for BleepingComputer. “Tweeting about this spam campaign, Vinny Troia hinted at someone known as ‘pompompurin,’ as the likely author of the attack. Troia says the individual has been associated in the past with incidents aimed at damaging the security researcher’s reputation.”
Troia’s work as a security researcher was the subject of a 2018 article here titled, “When Security Researchers Pose as Cybercrooks, Who Can Tell the Difference?” No doubt this hoax was another effort at blurring that distinction.
Update, Nov. 14, 11:31 a.m. ET: The FBI has issued an updated statement:
“The FBI is aware of a software misconfiguration that temporarily allowed an actor to leverage the Law Enforcement Enterprise Portal (LEEP) to send fake emails. LEEP is FBI IT infrastructure used to communicate with our state and local law enforcement partners. While the illegitimate email originated from an FBI operated server, that server was dedicated to pushing notifications for LEEP and was not part of the FBI’s corporate email service. No actor was able to access or compromise any data or PII on FBI’s network. Once we learned of the incident we quickly remediated the software vulnerability, warned partners to disregard the fake emails, and confirmed the integrity of our networks.”




generating the message client side…. i can’t even believe this would even be a thing
That’s what happens when systems are built by the lowest bidder!
Abusing a formmail CGI script like this is something that goes back to the early days of the web, when they were bundled with web servers and things like cPanel. It’s not something I thought I’d see these days.
You know, with this being a government website, it might still be running code from those early days, judging by that IE recommendation
It’s a TRAP!!!
#Deniability..
#Deniability
wrong.. lol
the entire internet is one giant honeypot
and if the CCP gets it way..
Xinny the pooh will own all the honey.
Why? Why generate the magic number client side? I’m baffled. Is it just laziness, because it’s easier?
It isn’t clear to me that the code is actually generated on the client. Much more likely is that it was created on the server and simply sent to the client, possibly because the account creation server has no ability to send emails. As a stateless protocol, HTTP is an absolutely terrible thing to be using for these sorts of transactional processes, especially if we’re looking for security. It’s a real shame that the web has become the lowest common denominator for most people on the Internet.
Well, I used HMAC in the past and now JWT with HTTP and it works fine. By the time you cracked the JWS, it has become invalid. And still on top of that sucky HTTP ^^
What baffle me more are people still sending password in clear text then telling you that it is OK, because it’s HTTPS… So, people who can’t make the difference between a secure channel and a secure message.
And on the web, both are equally important as infrastructure is shape shifting. Yet, 99% of website don’t use any mean to secure passwords sent from client.
For those who don’t understand: even with HTTPS, the client should send his password hashed. The salt is to be considered public (yep, it’s not private!) and the client has to generate a unique nonce and use timestamp from the server. The server can do the double hash tacking into account the salt, nonce and timestamp. So the attacker can’t change any of those parts and it forbid replay attacks AND rainbow tables! Salt has to be unique to each user.
See that the hash stored server side is NEVER exposed outside client or endpoint server.
Then, on top of that comes TLS (https).
It’s important because the infrastructure can have a load balancer handling the TLS layer then communicating in plain text with the server inside the network. There, a compromised machine can sniff and do replay attacks or just save the password for later use. With proper hashing, that compromised node sees gibberish!
I was filling out the internet tip form about a month or two ago and when it sent something flashed really quick like it would if it was diverting or was intercepting something so I checked the digital certificate for the site and it came back to a strange godaddy issuer which I would not think the FBI would be using a godaddy authority if they didn’t have their own it would be identrust or the like so I called to let them know that it appeared someone was spoofing the tip line site. At the time and still to this day my communication is diverted so I thought it was the person doing it to me but if they could spoof a govt site that well then I thought it needed to be brought to their attention. The agent pretty much told me to F MYSLEF and hung up. Much like they just did when I saw this and called to report it again that there was a spoofed domain operating under the ic3.fbi.gov name .
FBI recommendation, “We continue to encourage the public to be cautious of unknown senders…”
But the sender wasn’t unknown, it was you!
That’s because it is not providing a valid S/mime end point for a real person
That’s what happens when our Government is financially strained by all the government giveaways in the name is social justice.
Learn English to make stuff up for Breitbart effectively, comrade!
Brainwashed fool. Just parrot those Fox talking points and obey!
Correction: “This is what happens when government IT efforts are farmed out to the lowest bid from perpetual government IT contractors. This has nothing to do with any other efforts the U.S. Federal government has to take care of at all. ”
You’d know this if you ever worked on a government IT contract. Stop being a right-wing misinformation sheep.
You’re trying to sound smart, but this isn’t even a “lowest bidder” scenario. Maybe if you understood the article, perhaps some night classes at the local community college would help, this is a fundamental misunderstanding of POST.
it seems to me that you’re the one that needs to go back to school you have an extreme lack of reading and comprehension skills that need to be corrected be you you should be allowed back on the internet.
To be fair, you both did it to x degree.
Let’s all be less dumb going forward.
I’ll start.
It seems like this Pom guy either didn’t want to go up against the FBI or had good intentions by doing an obvious hoax. Maybe both. As for the political stuff, both sides seem to think the other is a bunch of sheep. Politicians are really good at dividing us and distracting us while they spend our money. If you look at what they do you see that none of them care about anything except for getting re-elected. There are very very few that actually are there to make a good difference.
+1 Choose from “column A” or “column B” just so as you keep eating at the same crappy restaurant. The populace doesn’t know anymore what good food really is so they settle for this garbage “takeout” served from DC.
That’s what happens when anti-government politicians attack the FBI and defund important government functions.
This is rather unfortunate since DOJ was on a roll smashing ransomware bandits and stealing back their money.
Script Kiddy Pompouspurin has just poked a stick into a massive nest of angry hornets. He’s going to get badly stung for what was a pointless zero revenue activity.
Hopefully he gets away with it, it’s not worth going to to jail over teh epic lolz
One correction: “request sent to their browser” should be “request sent from their browser”. No HTTP requests are sent to a browser.
Eh eh eh, websockets!
Just kidding, I understood what you meant.
Minor critique: the one time code wasn’t leaked in the HTML code of the page it was leaked in the network traffic.
This is ridiculously insecure though. Web security 101 is that you don’t trust any data sent from the client.
What a complete waste. Must have been a 13 year old surely. He could have easily leveraged that sort of access/capability for internal spear phishing and furthered his foothold, among other things.
Just as stupid as those dumb kids that got into Twitter earlier this year and completely wasted their access.
Best comment.
ohhh..you mean the kids who ate tide balls as a challenge? or the kids who lick food in grocery store and post it on social engineering sites? or maybe your talking about the smart kids who do work for free but then call it crowd sourcing then wonder why they have no monay!!!
LOL.. we all stupid kids but just waiting to see what the next gen does and what they will be called.. oomers, gloomers… doomers? Lol remember the phrase.. “Boomer remover?”..
well whos fearing for their future now… i guess the youth isn’t as smart as they think.
Gray hat. They do exist.
The FBI spends too much time testing security programs and software for the government to use. meanwhile the hackers create new exploits and programs, every day, every minute, every hour..while the complacent agents just use the old tools and wait for approval from ASCLAD and other approval agencies.
[It should be noted that “Step 1” in those instructions is to visit the site in Microsoft’s Internet Explorer, an outdated web browser that even Microsoft no longer encourages people to use for security reasons.]
Any idea how long this vulnerability existed, and could the vuln have been previously exploited to gain further access?
I’m not adding any new information with this comment, just helping myself visualize the attack. Maybe this will be useful for others.
Score points for creativity. Let’s way I’m an attacker. I fill out the form to sign up for the LEEP website. LEEP tells me it will send a code to my email and when I respond, then LEEP knows I’m me. So far, pretty standard stuff.
But for some reason, maybe intuition, I sniff the conversation between LEEP and me and I find the HTML POST command to tell LEEP to use the fields I provided to generate that confirmation email. But that POST does more than just tell LEEP to send *the* confirmation email. It also has the subject line and body of the message. Right there in my browser client. Which means, I can put in any subject, message body, and recipient email address and viola, I can use the FBI’s own systems to impersonate it.
Pompompurin indeed did us a left-handed favor. He could have generated much more damaging content and sent the FBI and a whole bunch of people chasing their tails. Instead, he did an obvious hoax. And now the world knows about the dangers of generating confirmation email content from a browser client. What I don’t get is, if he really wanted to make Vinny Troia look bad, why brag about his exploit to Brian Krebs?
…because he’s an insider with an agenda against one vinny…
Don’t you mean back-handed favour?
As a lefty, I take exception to your misuse of that term
…as a tennis player I take exception to your misuse of that term…
This is all too common. I once found keys for millions of users exposed, on a public website. My career was destroyed and I was blacklisted in my community for publicly reporting it. I applaud this man for doing what he did and sacrificing like he has. My experience caused me to change career paths, its not about the money I went from engineer to tow truck driver and I’m ok knowing I helped people…not ok knowing I can’t help them again.
FBI outsourcing their IT development work to India?
Close. Indiana.
Wrong how about Alabama….the secret service operates their national forensic cyber crime training facility in Hoover Al. On the Shelby county side of Birmingham/Jefferson co. Significant because Shelby is the infamous Shelby in Shelby v Holder that gutted the voting rights act and has had so far one officer commit suicide in his cruiser, one officer murder his wife after they gave him his service pistol back that they took because he shot her with it. And one officer fired for putting a Black Lives Matter protestor in crosshairs on his Facebook page, and had a news reporter found dead of apparent suicide after moving back from Arizona to Hoover when he was receiving death threats and being harassed and cyber bullied for writing a book that didn’t exactly paint the FBI in a favorable light. And had no previous history of mental illness…but I’m sure they just threw that one on the clintons and walked away .
DoJ is too busy indicting innocent grandmas instead of investing in their own security. The DoJ has become an almost a terrorist organization filled with highly paid incompetents that can’t catch 17 years old kids without paying astronomical amounts to third party’s but in their pursuit to get high conviction rates they get only the low hanging fruits then bankrupt & torture people to accept the cr4p they call plea agreement while propagandizing the public how great they are to get more federal funding. They should really feel ashamed of themselves!
Innocent grandmas! Lol, why aren’t you in prison then, fabulist-nanna?
So lemme get this straight, they were generating the entire email via a client side script, which would then submit it to their server via POST, and the server was sending out whatever the client script told it to send?
Good lord this could’ve been a million times worse.
I have seen much worse: SQL sent from client side ^^
When I asked the guys what they thought about it, they replied that it is back-end, so not accessible from the public.
Another one had SQL injections everywhere because he didn’t knew about prepared statements, neither escaping. I even had to rewrite this myself to be sure it’s done the right way.
Even when I reported to management, I got the “to this date, we didn’t had any issues”, then (ironically) a grey hat sent use an email proposing his services (stating he found vulnerabilities and that we can pay him to have details). I made management pay (it was quite cheap) and the guy started finding stuff left and right ^^ Almost every-time “should I pay ?” to which I had to say “Yes, of course”.
We even had someone abuse SMS to get multiple coupons and triggering charge back.
Another one was abusing support by making two small transactions then telling he did one big transaction that did not appear…confusing the support who proceeded to… a refund.
Crzy stuff!
for most of us unschooled in these fine points, and I mean the great unwashed majority, 80-90% of people, where is the handbook on proper web and email practice. I would challenge all of you savvy and honorable experts, who have taken the hard road and the high road in becoming professionals, to point to a concise guide for the layman, on what is proper and responsible online practice. I think most are mystified.
I know very little. Most of my family and people I work with, know even less and deliberately avoid learning how the web works. I did get the sense back in the early 2000’s that there were a million ways to manipulate the very complex interactions of the web for those who have studied it and do not want to do the right thing. The problem is, how to do everything properly and safely has not been codified or put into a handy guide, for those who are not computer engineers or programmers.
I do know it is a terribly complex system and a constantly moving target. But what can those of us do, who do not have degrees or know programming ? Someone needs to come up with a guide for best standard practice in plain English. Perhaps that is too simplistic or a bridge too far. We need a Bible for the internet.
Ok maybe but the FBI should not need “internet for dummies”
Such guides have long been available, but the masses don’t care to read them. Form mail exploits have been a known problem for decades; no new education should be necessary. The Biblical “commandment” for this particular issue is “Never trust the client/Always sanitize your inputs”. This would be basic knowledge to anyone competent in the field, including the managers overseeing the development. In truth, there are no less than 10 people in the FBI who could have and should have stopped this exploit before it ever went live. Odds are pretty good that at least 2 of those people are so incompetent that they never should have been hired in the first place. This sort of thing always points to larger organizational issues like that, and simply having documented best practices doesn’t mean there still isn’t some MBA out there that thinks they can just ignore it, try to get away with cutting corners, and thus end up making the world an increasingly worse place.
Ok – you asked and I’ll respond with a self-serving web link with exactly what you asked for. Just click on my name right above this comment and that should take you to www dot dgregscott dot com.
Seriously – I write novels with a cybersecurity theme and I put all kinds of easy-to-digest information on my website. Feel free to explore while you’re there. Book marketing for a bald guy from Minnesota, don’t ‘cha know.
Anyway, go to my website, click the big red button, fill out the form with your name and email address, and I have automation that will send you a dozen or so emails, each with one cybersafety tip and maybe a couple of colorful war stories. I’m not going to spam you, I won’t sell your name to anyone, but I’ll probably email you when my next book is ready, or other times when I think I have something worth emailing.
And if you’re so-inclined, I’d appreciate it if you’d consider buying one of my books for yourself and everyone in your family. As long as I’m asking, maybe consider buying a book for everyone on your Christmas shopping list.
But the cybersafety email tips come with no strings attached.
– Greg
I am curious where the list of target emails came from? I got this and it was not an ARIN contact email as some sources have suggested?
…he was an insider with email addresses…
…doh…
And FBI’s using computers similar to those in War Games.
Nitpick but there’s no “The” in front of most gov’t agencies or administrations. FBI, FDA, FTC, FCC, etc. Sounds weird for sure.
I wonder if he had sent emails stating the equivalent of ‘Stop. We have you surrounded. Turn yourself in and no one would get hurt.’, if any pending cases would have been solved.
i was abusing this for years before this skid found it and made it public i made so much money ransoming people with this so a big middle finger to pom
How about that …my posts were removed …hmmmm why would they not be relevant considering I again tried to contact them like I did almost 2 months ago to inform them the site I was on for them was listed under a go daddy certificate instead of their usual entrust and I didn’t think the FBI would be using a security certificate from a rogue godaddy site but was told to mind my own business in their own way and was promptly hung up on …thanks US FED GOVT …
Where do I send my resume? Just learned there’s a systems manager opening at the feds.
Internet Explorer!? c’mon man my 10 yeard old niece knows better not to use that browser. HR departments everywhere are to blame for hiring IT people based on certificates and not experience. You can see all the job ads applicants with certain certificates have an advantage of being hired. Most ads do not put emphasize on actual experience.
..
The FBI and I go way back – just click on my name right above this comment for a taste from an outsider for how the FBI operates. That may help explain why the FBI built this website with such obvious issues.
– Greg